Role of Mobile Agents in the Layered Architecture of Mobile Ad-hoc Networks
Автор: Bindiya Bhatia, M.K.Soni, Parul Tomar
Журнал: International Journal of Computer Network and Information Security(IJCNIS) @ijcnis
Статья в выпуске: 11 vol.7, 2015 года.
Бесплатный доступ
In today's world mobile agents and mobile ad-hoc networks are the two technologies that are contributing towards better connectivity and communicability. When the two technologies used jointly, the interest is increased. Due to the properties like self-configuration and infrastructure-less, the mobile ad-hoc networks provide various remarkable features. But the various challenges are also associated with mobile ad-hoc networks like dynamic topology, mobility, energy constraint etc. Mobile agent provides solution to these challenges. A mobile agent is a new way of computer interactions and provides better options for the developers to create applications based on connectivity. Mobile agents move around the ad-hoc networks in a different and better way than the other widespread client server architecture based applications. Due to their mobility and autonomy these agents can perform various functions in mobile ad-hoc networks like topology discovery, routing, key management, congestion control etc. The paper reviews the role of the mobile agents in the mobile ad-hoc networks, and emphasizes its application on the various layers of a layered architecture of mobile ad-hoc networks and concludes its merits as compared to other conventional approaches.
Mobile ad-hoc networks, mobile agents, routing, key management, topology discovery
Короткий адрес: https://sciup.org/15011471
IDR: 15011471
Текст научной статьи Role of Mobile Agents in the Layered Architecture of Mobile Ad-hoc Networks
Published Online October 2015 in MECS DOI: 10.5815/ijcnis.2015.11.04
In recent times, mobile computing becomes admired in favor of mobiles, notebooks, and personal digital assistant (PDAs) computers. Sometimes it happens that many computing devices gather at the same site such as any conference site or a classroom. Exchanging information among these moveable computing devices without any centralized managing entity is not an easy task. The ad -hoc network is the solution for these communications. The ad-hoc network is created on demand to make possible the communications among the moveable computers [15]. The computing devices are integrated into various systems, such as phones, homes, sensors, vehicles, military equipment etc. Due to this the inclination is moving towards the self-configuring and infrastructure-less wireless networks, such as mobile ad hoc networks (MANETs) [12]. While MANETs bring many striking features for communications there are various challenges associated with it:
-
> Dynamic network topology
-
> Mobility of nodes
-
> Scalability
-
> Battery constraints
-
> Location aware routing
A lot of work has been done to meet these challenges. New routing protocols are introduced and new technologies are introduced at the different layers of networks. With the advent of time research is going on to optimize these algorithms and protocols used at different layers. To optimize these algorithms and protocols, one of the technologies used is Mobile agent. Mobile agents are small programs which can move themselves from node to node autonomously, and also interact with the environment. Mobile agents and mobile ad-hoc networks are the two competitive technologies to provide better communication and connection. By using jointly, high dimensions can be given to communication. A mobile agent is a new way of computer interactions and provides better options for the developers to create applications based on connectivity. They roam around ad-hoc networks in a more graceful way than the other clientserver based applications.
This paper represents the frontward shift behind mobile ad hoc networks and presents the technology solutions based on mobile agents at various layers of the ad-hoc network. Due to the extensive literature on Mobile ad-hoc Network we try to present the main research areas in which mobile agents can be applied. The next section of the paper is discussing Mobile ad-hoc networks and mobile agents. Further the third section describes the implementation of mobile agents in various technologies used in different layers of MANET and the fourth section presents the comparison of mobile agent approach over other traditional approaches used in different layers of MANET. Section five concludes the paper.
-
II. Mobile Ad-Hoc Networks And Mobile Agents
We are living in a world of Ubiquitous Computing in which a user gets all the necessary information whenever and wherever needed through the electronic devices. A user can use his mobile phone to check e-mail, browse the internet; tourists can use Global Positioning System (GPS) installed in rental cars to locate driving maps, travelers with their handy computers can browse the internet anywhere [11]. This can happen through the interconnection of the wireless devices. Presently, the connectivity can be achieved by fixed infrastructure based service provider or private network. But to set up the required infrastructure, high cost and time is needed. And sometimes in a given geographical area, networking connections are not available, and it becomes a real challenge to provide the needed connectivity and network services in these situations.
Mobile Ad Hoc Network is the solution for this. Mobile Ad Hoc Network is comprised of movable nodes which communicate over a wireless link without any central control [22]. In mobile ad-hoc networks, the ad hoc connection is established between the mobile devices through automatic configuration within a transmission range. Through this mobile devices become able to communicate with each other and can exchange information.
During last twelve year, MANET is one of the hot research topics. As the advancement is going on in wireless technologies and mobile devices, Mobile ad hoc network is playing a vital role in enabling current and upcoming communication.
Mobile nodes create the mobile ad-hoc network by interconnecting each other through a wireless medium. The network is formed without any centralized entity and current infrastructure viz base station etc. That’s why the network is called the infrastructure-less network. The movement of the mobile node is random, due to this there can be fast and sudden change in the topology. Such networks are also called as the multi-hop wireless network because the routes between the two nodes may include multiple hops. The communication between the two nodes can be direct if the nodes are in the transmission range. The nodes which are residing outside the transmission range, the communication can be done through intermediate nodes by relaying the message hop by hop. Fig. 1 is depicting the infrastructure less mobile ad-hoc network.
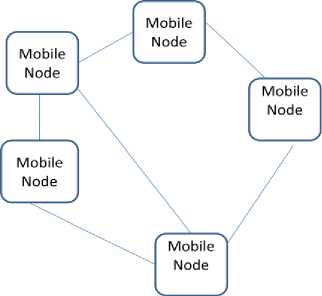
Fig.1. Mobile Ad-hoc Networks
MANET exhibits various characteristics which are mentioned below:
-
1) Self-organization and self-administration: There is no requirement for any central entity to control the operations of the network. The nodes in the network are self-organizing and cooperate with each other. Whenever there is a requirement for specific functions such as routing, each node can act as relay.
-
2) Multi-hop routing: One or more intermediate nodes can be required to forward the packet if the node is out of the communication range.
-
3) Autonomous and infrastructure less: MANET does not rely on any fixed infrastructure and each node can independently act as router.
-
4) Dynamic network topology: Due to the mobility of the nodes, the network topology may change randomly. At that time, the nodes in the MANET dynamically create a route.
-
5) Battery constrained devices: Generally, the nodes in MANET are mobile with limited power and storage.
-
6) Network Scalability: In MANET, the network can grow to several thousand of nodes. The mobility of the network makes the scalability easy.
Due to these characteristics MANET can be used to areas where sometimes we cannot apply conventional networking for e.g.
-
• Military Areas: In battlefield communication is needed for situational awareness. MANET is useful in this case due to its infrastructure less property.
-
• Disaster Prone Areas: MANET can be used for rescue operations in case of disasters like earthquake, flood etc. Due to damaged communication infrastructure in disaster, a rapid deployment of the network for communication is much required.
-
• Ad hoc conferencing: MANET can be formed to communicate in a conference, seminar or meeting etc.
Although mobile ad hoc networks have flexibility and convenience, but there are problems associated with the network due to wireless communication and mobility [11]:
o The wireless medium has not readily observable boundaries.
o The channel is unprotected from outside signals.
o Reliability of a wireless medium is less as compared to wired media.
o There is a problem of Hidden-terminal and exposed -terminal.
o Addressing is another issue as the position of the node doesn’t matter in case of addressing the mobile node in MANET.
Besides these problems, there are other issues that are associated with MANETs
-
• Bandwidth Constrained – The links in the wireless network have the lower capacity as compared to the wired connection.
-
• Energy Conservation –The moveable nodes in the network are battery operated. Due to the limited battery life the conservation of the energy is the major issue in MANET.
-
• Dynamic Topology- The topology in the network changes dynamically due to the movement of the nodes. So, every time updated topology needs to be communicated to the nodes in the network.
-
• Routing – Because of the constant change in the topology, the routing is a big challenge in MANET. The routing table needs to be updated due to the unpredictable variation in the topology. Multi-hop routing is even more complex.
-
• Security – Due to the mobility of the node the network is at higher security risks. The wireless network is vulnerable to eavesdropping & numerous other security risks.
-
• Scalability – According to the need the network grows. The mobile nodes must be capable of providing services even in a large network.
-
• Network Management & Configuration – Configuring and managing the network is also a major issue because of the dynamic connection.
-
• Fault Management – In MANET every node is capable of communicating with other nodes in the network through multi-hop. Also, the nodes are moving. So, it is difficult to identify & manage faults.
Extensive research is done to overcome these issues. A mobile agent is the latest approach that is used to conquer the problems associated with MANET.
Mobile agents are small programs which can roam from node to node. They can interrupt their execution on one node and resume where they halt on the previous node. While moving from node to node, mobile agents can collect information from the node, and also mobile agents can gain experience from user’s behavior by some advanced artificial intelligence means [2].
Client and server are tightly coupled in client- server approach. Continuous bandwidth availability is required while communication in this approach. But if we talk about mobile computing, low bandwidth is there and the devices are resource constrained. Mobile agents are solutions to this because of its inherent properties like mobility and autonomy. The connection time between the mobile devices can be optimized by agent’s mobility. Due to the autonomy, the agent can perform the task at the remote site without the connection. After completion of the task, the agent waits for the user to reconnect and then the agent give the result. The information retrieval and filtering is done by the agent at the server side and the agent return to the client only with the significant information.
Mobile agents are not restricted to the device where it is initiated. It has the capability to take itself from one device to another device around the network. With this capability, a mobile agent can move to a device where the object is lying with which the agent wants to interact.
Mobile agents are intelligent, autonomous application programs. They can themselves decide what will be their next destination and what they will do. They can move from one device to another device in a network, to complete a specific task, which means mobile agents are also goal oriented. Mobile agents are having a feature that not only its code is mobile, but the state of the agent is also mobile. This means that mobile agents can stop their execution anywhere on one host and can resume its execution on the next host from where it has stopped execution on the previous node. It is able to carry the incomplete transaction or calculation with them when they migrate from one device to another device and can complete that transaction on next device where it will be migrated [23].
A mobile agent is a somewhat young technology that has only existed for some years. Though, lots of programming environments are designed to allow programmers designing mobile agents in a simple way [2]. With the prevalent acceptance of Java, it increases people’s interest in mobile agents.
Fig. 2 shows the difference between the mobile agent approach and client-server approach.
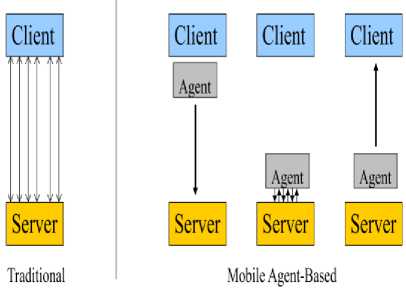
Fig.2. Concept of Mobile Agents
The mobile agents have three properties mentioned below that makes them different from the client-server approach:
-
i. Mobility: The mobile agents can move around the network with their code and data. The mobile agents can also move their executable state with them from a host to host. To move code, data & state it needs a channel which can be FTP, WWW or TCP/IP, UDP. FTP is little slow channel whereas WWW is fairly fast & fastest is TCP/IP & UDP.
-
ii. Executable: The mobile agent can carry their executable states with them from one node to another node. With this ability, it is able to suspend its execution on one node and can resume its execution on another node.
-
iii. Autonomy: An autonomous thing can act on its own without any outside control. A mobile agent encapsulates the code, data & state into one unit. The program states have its variables & binding to resources. With this encapsulated unit, the mobile agent possess the autonomy and can respond, react or developed independently of the environment.
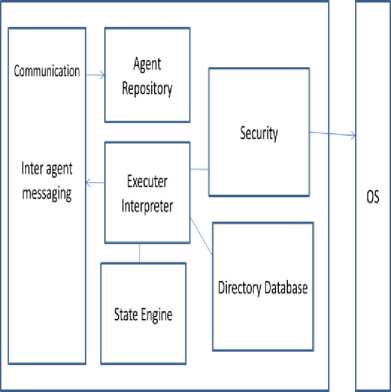
Fig.3. Mobile Agent System Architecture
The execution module is responsible for the execution of the mobile agent. The current state of the agency is contained in state engine and also some kind of rule or inference engine to decide what to do with the agents. It also handles local inter – agent communication. The directory or database is there to store or retrieve the date by agents. The security module keeps the track of what the agents are allowed to do. The monitoring of the agency is also done by security module [34].
Mobile agents are well suited for mobile computing due to its various features such as autonomy, mobility, intelligent, goal driven, learning, corporation, reactivity. In order for a mobile agent to collect information from the remote site, it doesn’t need to transfer the multiple request and responses across the low bandwidth. The mobile agent can use the resources of remote site efficiently and for this purpose it doesn’t require the connection. All the tasks can be performed by the agent even if the connection is disconnected. So the loss of connection during the process will not affect the agent.
Mobile agents have the skill to cover the communication channel and show the computation logic. With this skill of the mobile agent, the development, testing and implementation of distributed applications can be simplified. They can act as client and server depend on their goal and can dispense themselves throughout the network. The scalability of the application can be increased due to the ability of the mobile agent to relocate the work to appropriate location.
-
III. Implementation of Mobile Agents on Different Layers of Manet
Problems are associated with each layer of mobile ad hoc networks. Various solutions were proposed to overcome these problems. However mobile agents, one of the emerging technology could be much more adaptive than others conventional approaches in such environment. Mobile agents are intrinsically linked to these issues and often proposed as a solution. The paper reviews the application of mobile agents, according to the layered approach of ad-hoc networks as mentioned in Fig. 4. Following layers are considered:
-
> Data Link Layer
-
> Network Layer
-
> Transport Layer
-
> Application Layer
-
> Cross-Layer
Application Layer

Key management, Security______


Congestion
Management
Routing, Service discovery, cluster management
Topology discovery
Cross Layer
Transport Layer
Network
Layer
Data Link
Layer
Fig.4. Layered Design of MANET
-
A. Data Link Layer
T opology discovery is the major issue in manet. Due to the mobility of mobile hosts the dynamics of the mobile ad-hoc network create a number of problems while topology discovery.
Chpudhury et al. [20] proposed a method for discovery of the topology using mobile agents in wireless ad-hoc networks. A Multi-agent based protocol is designed to make the nodes in the network topology aware. In the proposed approach, mobile agents gather all topology related information from every node of the network and then distribute the updated information to other nodes periodically.
Adnan Ahmed, Behrouz Far [35] present a combination of reactive and proactive system i.e. “NONANT” mobile agent based topology discovery system. The agent mobility is a reaction to network change. Whenever a new node joins the existing network, a beacon is sent by the new node of its existence to all the existing nodes. Then the mobile agent who was residing on the existing node travels to the new node. Thus, the agent movement starts whenever there is a change in the network, which is a reactive mechanism.
-
B. Network Layer
Although various solutions are there to overcome the issues related to networking in MANET. Still problems exist with the current approaches:
-
■ Proactive on demand routing protocol generates large volumes of control traffic for discovering the topology, and the actual data traffic is delayed due to this.
-
■ Route discovery latency and end to end delay are there in present routing protocols. Common distant vector routing algorithms prove not to be efficient where wireless networks are continuously changing.
Extensive research is reported to make the routing algorithms decentralized by dispatching agents traveling through the network.
Few years earlier, the proposal of use of mobile agents for the purpose of routing in mobile ad-hoc networks has been explored in MIT Media Lab [16] with few limitations.
Further Nikos, William, Kelvin [14] worked on the problem of delay in the route discovery and introduced the concept of mobile agents to find the best path. In their work, the Mobile agents can roam around the ad-hoc network independently and collect information from static agents. Then the information collected through the mobile agents can be used to execute required calculations in order to find the best path to route the network traffic.
Mobile agent based Ant-AODV technique was introduced in [25], which forms a hybrid of both antbased routing and AODV routing protocols. In this technique, routing information is gathered by mobile agents and the routing table of every node is revised according to the information collected. With this hybrid technique node connectivity can be enhanced and end-to-end delay and route discovery latency can be decreased.
Based on the mobile agent, a routing algorithm with multiple constraints is proposed by CHEN et al. [31] for the ad doc network. Mobile agents are used to gathering the information of all mobile nodes. With this information, the delay in the network and the operating cost of control messages for routing can be reduced. According to the authors, in this algorithm link failure probability is low because the algorithm selects links with large link expiration time when the route is created.
-
C. Transport Layer
Problems are also there on the transport layer even after the existence of various solutions. Whenever severe congestion is there, it is preferable to use a new route. In on-demand routing protocol due to processing and communication effort to discover a new route, there is a problem of delay. If multipath routing is used, though an alternate route is readily found, the high overhead is there to maintain multiple paths. So some improved mechanism was required to control the congestion.
-
V. Sharma, S. Bhadauria [28] proposed an approach based on mobile agents that travel through the network, to pick a neighbor node as its next hop which is less loaded. The routing table is updated by the mobile agents according to the node’s congestion status. Mobile agents make aware the nodes about the dynamic network topology in time.
-
D. Application Layer
In the present security mechanism for MANET, there is a drawback that the requirement for a trusted entity that initializes the very first k trusted nodes. With the use of mobile agents, this drawback can be overcome.
Zhang Yi, Zhu Lina and Feng Li [30] based on the (t, n) threshold cryptography, introduced a technique in which mobile agents are used to exchanging the private key and information about the network topology information with nodes in the network. In this method, a centralized certification authority is avoided for distributing the public keys and certificates. Due to this security can be enhanced.
Based on a combination of techniques such as hierarchical clustering, partially distributed key management, offline certification authority, and a mobile agent, a new composite key management scheme is introduced in [19]. The technique hierarchically structured the network into clusters according to the trust value of the node. The mobile agents exchange the information about node revocation and PKG service among the nodes. There is a cluster head which will maintain member’s public keys. Here each node maintains public key of another node. So the storage problem in PKI is overcome. Also, the centralized CA can be avoided to generate keys, thus security is increased.
Hijazi [1] proposed three designed for intrusion detection system in MANET using mobile agents. The first design is called local intrusion detection system (LIDS). In this architecture, the mobile agents are residing on different nodes. The architecture takes the advantages of SNMB. But the requests are sent to remote hosts through mobile agents instead of sending through unreliable UDP. The second design is based on the static stationery database. The system consists of two parts. The first part is mobile IDS agents that execute on every node in a network and the second part is the stationary secure database which contains global signatures of known misuse attacks. Patterns of each user’s normal activity in a non-hostile environment are also saved in the database. Intrusions are found by the IDS agents based on local audit data. It participates in cooperative algorithms with other IDS agents to decide on attacks. On the other hand, the secure database acts as a repository for nodes which is secure and trusted. This repository is used by the mobile nodes to find out the information about the latest misuse signature and the latest patterns of normal user activity. The third design is Distributed intrusion detection system using mobile agents. In this system, lightweight mobile agents are there with certain functionality. The total network load can be reduced by dividing the functional tasks into categories and dedicating an agent to a specific purpose.
A cluster-based distributed hierarchical intrusion detection system [38] is designed to secure the MANET using mobile agents. The proposed solution has used cluster based routing protocol. In this two layers are considered: cluster member layer and cluster head layer. Several mobile agents are used and specific tasks are given to the agents. There is intrusion detection agent which detects the intrusion and also tries to spot the possible attacks. Then the agent informs the members of the cluster regarding the intrusion. There is one another agent i.e. Network response agent which informs the other cluster heads regarding the intrusion. All the responses use piggybacking, so there is no communication head.
Secure Wireless Agent Testbed (SWAT) is a technique introduced in [26] which implements secure communication in wireless ad hoc networks by employing autonomous mobile agents.
-
E. Cross Layer
There are research areas that may affect all layers of mobile ad hoc networks for e.g. energy conservation, quality of services etc.
Since most of the mobile hosts operate on battery power that is why Energy saving is a critical issue for MANET. A cross-layer coordinated framework for energy saving was proposed. 4 new strategies were discussed in the framework to save the energy. Mobile agent and periodic beacon-based topology discovery is one of the strategies to conserve the energy [32].
An energy efficient routing protocol is discussed in [36]. Span protocol is used in the algorithm which switches off nodes for as long as possible and hence maximizes the lifetime of the wireless ad-hoc network. In combination with this, ants (mobile agents) are used to save the energy. In the algorithm, coordinators are chosen in a network which regularly awake and implements the multi-hop packet routing within the network. The rest of the nodes can go to sleep mode. A coordinator can withdraw itself any time if its neighbors are able to talk with each other, either directly or through any other coordinator. Two types of control packets are used for routing table modification i.e. forward ants and backward ants. These two packets share the information regarding the traffic load in the network. The job of the forward ant is to find the new routes on demand in the network. And backward ant’s job is to carry the data packets. It also estimates the quality of the new routes. There are substantially less number of control packets. Due to this the algorithm is energy saving.
The owner can verify the data against temperament when the agent comes back. The node sends the agent to its entire neighboring node to collect the resource information. After receiving the information, the election starts. A vote agent is initiated to collect votes of the neighbor node and according to the nodes the leader node is selected.
A Multi-Constrained QoS Routing Algorithm based on mobile agents is discussed in [33]. The algorithm considers two QoS factor energy and bandwidth resource in MANET. The algorithm effectively provides reliable network performance by expanding the network load and increasing the utilization ratio of the network resource.
Mobile agents are used in this technique to gather the information of all mobile nodes and reduce the delay in the network and the operating cost of control messages for routing.
The multipath strategy of the algorithm reduces the time consumption of rerouting. QoS requirements are met in order to extend the survival time of network by utilizing the best path to perform the data transmission. Also, it improves the network resource utilization.
-
IV. Comparison of Using Mobile agents over Traditional Approach in Manet
A comparison can be made against the mobile agent approach and other conventional approaches used in MANET over various parameters like topology discovery, network latency, congestion control, key management etc. Generally the tools used by the network administrator, use PING, trace route, SNMP queries for topology discovery. These all are based on the client-server approach.
Such approaches consume more bandwidth and more power as compared to the use of a mobile agent for topology discovery in MANET. The mobile agents can run remotely and don’t need bandwidth and connection to run on a remote host. This reduces the network traffic and hence improves the network latency. In highly dynamic networks such as MANETs, there is a requirement for frequent dissemination of the information regarding the topology change. In DSDV routing protocols, the network capacity for actual data communication is reduced due to these frequent updating. Also, in on-demand, reactive routing schemes like AODV and
Dynamic Source Routing (DSR) the actual transmission of the data is delayed until the route is discovered. This delay is not acceptable in real-time data communication. Whereas if we use a mobile agent for routing, it updates the routing table periodically while migrating to the host and thus reduce the end to end delay and provide fast rerouting and a best path selection. In MANET, the normal TCP congestion control is not very efficient. In a mobile agent approach, the mobile agents propagate the status of the congestion to every node so that the node will be able to select the path with less congestion. Also by using Mobile agent approach the security is enhanced because there is no need for the centralized entity for distributing the public keys and certificates.
The table 1 is showing the merits of mobile agent approach over other traditional approaches that we use in various layers of MANET for topology discovery, route discovery, congestion control, and key management.
Table 1. Comparison Between the Mobile Agent Approach and Traditional Approach in MANET
|
Parameters |
Using Mobile Agents |
Other Conventional approaches |
|
Data link Layer |
||
|
Bandwidth Conservation |
More Efficient |
Less efficient |
|
Dynamic Topology Discovery |
consume less bandwidth and power |
consume more power and bandwidth |
|
Network Layer |
||
|
Network Latency |
Low |
High |
|
Network Traffic |
Less |
More |
|
Updating Routing table |
End to end delay is less |
End to end delay is high |
|
Finding best path |
Fast |
Slow |
|
Rerouting |
Fast |
Slow |
|
Transport Layer |
||
|
Congestion Control |
More Efficient |
Less Efficient |
|
Application Layer |
||
|
Key Management |
More Efficient |
Less efficient Due to the requirement of a central entity |
|
Cross-Layer |
||
|
Energy Conservation |
More Efficient |
Less efficient |
-
V. Conclusion
The paper studies the current research and technologies to review the role of a mobile agent in various areas of a layered architecture of a mobile ad-hoc network. The study convinces us that mobile agents are a novel and feasible approach to overcoming the issues related to ad-hoc wireless networks. With the use of mobile agents, we can achieve various advantages like:
-
> Fast topology discovery
-
> Fast updating of routing table
-
> Energy conservation
> Bandwidth conservation.
-
> Efficient Key management
-
> Efficient congestion control
Although mobile agents play a vital role to give the new dimensions to various services of MANET, still mobile agents are also at security risks and vulnerable to attacks. And the focus of our future work is to encounter the problem of securing mobile agents.
Список литературы Role of Mobile Agents in the Layered Architecture of Mobile Ad-hoc Networks
- Abdulrahman Hijazi, "Using Mobile Agents for Intrusion Detection in Wireless Ad Hoc Networks", Wireless and Optical Communications Networks, 2005. WOCN 2005, Second IFIP International Conference on March 6 - 8, 2005.
- Alexandre Manguer, "Mobile agents in ad hoc networks", thesis, April 2003.
- B. Askwith, M. Merabti, Q. Shi and K. Whiteley, "Achieving User Privacy in Mobile Networks," Proceedings of the 13th Annual Computer Security Applications Conference, San Diego, 1997, pp. 108-116.
- Borselius,N." Mobile agent security" The Electronics & Communication Engineering Journal Vol 5, pp. 211–218 (2002).
- Chandreyee Chowdhury, Sarmistha Neogy, "Securing Mobile Agents in MANET against attacks using Trust", International Journal of Network Security & Its Applications (IJNSA), Vol.3, No.6, November 2011.
- Chaum, "Security without Identification: Transaction Systems to Make Big Brother Obsolete" Communications of ACM, Vol. 28, No. 10, 1985, pp. 1030-1044, doi: 10.1145/4372.4373.
- F.Hohl, "Time Limited Black box Security: Protecting Mobile Agents from Malicious Hosts," To appear in Mobile Agents and Security Book edited by Giovanni Vigna, published by Springer Verlag 1998.
- G. C. Necula and P. Lee, "Research on proof-carrying code on mobile-code security," 1997.
- G.Geetha, C.Jayakumar, "Trust Enhanced Data Security in Free Roaming Mobile agents Using Symmetric Key cryptography", International Journal of Network Security & Its applications (IJNSA), Vol.3, No.5, Sep 2011.
- Haghighat, R., Yarahmadi, H.: A New Approach for Mobile Agent Security. In: The Proc. of the World Acadamy of Science, Engineering and Technology, vol. 32, 2008.
- Imrich Chlamtac, Marco Conti, Jennifer J.-N. Liu, "Mobile ad hoc networking: imperatives and challenges", Ad Hoc Networks Vol 1, pp. 13–64, doi: 10.1016/S1570-8705(03)00013-1
- Karlsson, Jonny; Dooley, Laurence S. and Pulkkis, Goran, "Routing Security in Mobile Ad-hoc Networks", Issues in Informing Science and Information Technology, volume 9, 2012, pp 369 – 383.
- L. D'Anna, B. Matt, A. Reisse, T. Van Vleck, S. Schwab, and P. LeBlanc, "Self- Protecting Mobile Agents Obfuscation Report," Report #03-015, Network Associates Laboratories, June 2003.
- Nikos Migas, William J.Buchanan, and Kevin A. McArteny, "Mobile Agents for Routing, Topology Discovery, and Automatic Network Reconfiguration in Ad-Hoc Networks", in proceeding of 10th IEEE International Conference and Workshop on the Engineering of Computer-Based Systems (ECBS'03).
- N Kawaguchi, K Toyama, Y Inagaki, "MAGNET: ad hoc network system based on mobile agents", computer communication, volume 23, issue 8, April 2000, pages 705-782, doi: 10.1016/S0140-3664(99)00236-4.
- N. Minar, K.H. Kramer, and P. Maes, "Cooperating Mobile Agents for Dynamic Network Routing", MIT Media Lab, http://xenia.media.mit.edu/~nelson/research/ routes-book chapter/minar.pdf, Software Agents for Future Communication Systems, 1999, ISBN: 978-3-642-63584-7 (Print) 978-3-642-58418-3 (Online), pp 287-304, doi: 10.1007/978-3-642-58418-3_12.
- Rajesh Shrivastava, Pooja Mehta (Gahoi), "Analysis of Secure Mobile Agent System", International Journal of Soft Computing and Engineering (IJSCE) ISSN: 2231-2307, Volume-2, Issue-1, March 2012.
- Rizvi, S.M.S.I., Sultana, Z., Bo, S., Islam, M.W.," Security of Mobile Agent in Ad hoc Network using Threshold Cryptography". In: The Proc. of the International Conference on Cryptography, Coding and Information Security (2010).
- R. Pushpa Lakshmi, Dr. A. Vincent Antony Kumar, "Cluster Based Composite Key Management in Mobile Ad Hoc Networks", International Journal of Computer Applications (0975 – 8887), Volume 4 – No.7, July 2010.
- R.R. Chpudhury, S. Bandyopadhyay, and K. Paul, "A distributed mechanism for topology discovery in ad hoc wireless networks using mobile agents", In Proceedings of First Annual Workshop on Mobile Ad Hoc Networking Computing, MobiHOC Mobile Ad Hoc Networking and Computing, August 11, 2000, doi:10.1109/MOBHOC.2000.869229.
- R. Wahbe, S. Lucco, T. E. Anderson, and S. L. Graham, "Efficient software-based fault isolation," In Proceedings of the 14th ACM Symposium on Operating Systems Principles, pages 203--216, Dec. 1993, doi:10.1145/168619.168635.
- Saleh Ali K.Al-Omari1, Putra Sumari2, "An overview of mobile ad-hoc networks for the existing protocol and applications", International journal of application of graph theory in wireless ad-hoc networks and sensor networks, vol 2, No. 1, March 2010.
- Samuel Lee, "Mobile Agents", A tutorial report, Agent based software engineering.
- Sathish Alampalayam Kumar, "Classification and Review of Security Schemes in Mobile Computing", Wireless Sensor Network, 2010, vol 2, pp 419-440.
- Shivanajay Marwaha, Chen Khong Tham, Dipti Srinivasan, "Mobile Agents based Routing Protocol for Mobile Ad Hoc Networks", Global Telecommunications Conference, 2002. GLOBECOM '02. IEEE volume 3, pp 17-21, Nov 2002.
- Sultanik, E., "Secure Mobile Agents on Ad Hoc Wireless Networks." The Fifteenth Innovative Applications of Artificial Intelligence Conference Acapulco, Mexico, 2003.
- Tarig, M.A.: Using secure-image mechanism to protect mobile agent against malicious host. In: Proc. of World Academy and Science, Engineering and Technology, pp. 439–444 (2009).
- Vishnu Kumar Sharma, Dr. Sarita Singh Bhadauria, "Agent based Congestion Control Performance in Mobile ad-hoc Network:A Survey paper", (IJACSA) International Journal of Advanced Computer Science and Applications, Special Issue on Wireless & Mobile Networks,2012
- W. M. Farmer, J. D. Guttman, and V. Swarup, "Security for mobile agents: Authentication and state appraisal," in Proceedings of the European Symposium on Research in Computer Security (ESORICS'96), ser. Lecture Notes in Computer Science, E. Bertino, H. Kurth, G. Martella, and E. Montolivo, Eds., vol. 1146. Rome, Italy: Springer, September 1996, pp. 118–130.
- Zhang Yi, Zhu Lina and Feng Li, "Key Management and Authentication in Ad Hoc Network based on Mobile Agent", Journal of Networks, Vol. 4, No. 6, August 2009, doi:10.4304/jnw.4.6.487-494.
- CHEN Wei and ZHANG Yi, "A Multiconstrained Routing Algorithm based on Mobile Agent for MANET Networks", International Joint Conference on Artificial Intelligence. IEEE 2009.
- Xu Li, Zheng Baoyu, "Cross-Layer Coordinated Energy Saving Strategy in MANET", Vol.20 No.6 Journal of Electronics (China) Nov. 2003.
- Bindhu.R, "Mobile Agent Based Routing Protocol with Security for MANET", International Journal of Applied Engineering Research, Dindigul Volume 1, No1, 2010.
- Mats Person, "Mobile Agent Architectures", Scientific Report, Dec 2000, Defence Research Establishment, ISSN 1104-9154.
- Ahmed, A.; Far, B., "Performance of Mobile Agent Based Network Topology Discovery," Electrical and Computer Engineering, 2007. CCECE 2007. Canadian Conference on, vol., no., pp.66-69, 22-26 April 2007, doi: 10.1109/CCECE.2007.24.
- Annapurna Patil, Saunhita Sapre," Intelligent Energy Efficient Routing Protocol based on Biological Agents for MANETS", International Journal of Emerging Technology and Advanced Engineering, (ISSN 2250-2459, ISO 9001:2008 Certified Journal, Volume 4, Issue 7, July 2014.
- M. Darji, B.Trivedi, "Secure Leader Election Algorithm Optimized for Power Saving", Proceedings of international conference on Recent Trends in Computer Networks and Distributed Systems Security, Trivandrum, India, October 11-12, 2012, DOI 10.1007/978-3-642-34135-9.
- B. Pahlevanzadeh, S.A. Hosseini Seno, T.C. Wan, R. Budiarto, Mohammed M. Kadhum, "A Cluster-Based Distributed Hierarchical IDS for MANETs", International Conference on Network Applications, Protocols and Services 2008.
- Neogy, R.; Chowdhury, C.; Neogy, S., "A reliable service discovery protocol using mobile agents in MANET," Reliability and Maintainability Symposium (RAMS), 2012 Proceedings - Annual, vol., no., pp.1,7, 23-26 Jan, 2012, doi: 10.1109/RAMS.2012.6175451.
- Hamad, H., "Distributed Mobile Agents for reliable cluster management in MANETs," International Journal of Interactive Mobile Technologies (iJIM), Issue 2, vol. 2, Apr. 2008, pp. 11-17.


