Secure and Dynamic Model for Book Searching on Cloud Computing as Mobile Augmented Reality
Автор: Adeel Rafiq, Bilal Ahsan
Журнал: International Journal of Modern Education and Computer Science (IJMECS) @ijmecs
Статья в выпуске: 1 vol.6, 2014 года.
Бесплатный доступ
Availability of internet on different devices like smart phones like android based, IOs based, windows based and PDA etc. has brought into the evolution of mobile cloud computing, which is a vast side of research nowadays. Internet connectivity has become very easy with the evolution of Wi-Fi, everyone can access the internet using wireless connectivity. A major issue in wireless connectivity is the low level of encryption and low security. This might be a security risk for the sensitive data available on the cloud. There are mobile augmented reality systems based on cloud computing, we want to propose a dynamic framework for the security of cloud and live update data on cloud.
Cloud, PMD, Image processing, Augmented reality, SMS, MMS, Wi-Fi, Urdu OCR
Короткий адрес: https://sciup.org/15014623
IDR: 15014623
Текст научной статьи Secure and Dynamic Model for Book Searching on Cloud Computing as Mobile Augmented Reality
Published Online January 2014 in MECS DOI: 10.5815/ijmecs.2014.01.08
Time is money and very precious thing in the world. Book shopping and searching of book in library is very hectic task and time consuming work. People go to shop or library and spend lot of time to select good books. There is many library management system available but not for people but for library and stores. Now with the passage of time advance developing of smart phone application developing, many augmented reality base application is developed [1]. Since last decade smart phone with internet make the world globe and people now have everything in their pocket. Combination of smart phone and remote server facilitate the developing the application of augmented reality. Augmented reality makes the virtual environments just like real world. Because combination of sound, graphics and even different kind of scent which is computer generated forget us that this is all is virtual. Example of augmented reality is the if we can manage the graphics in the air rather than in television, this is one example of augmented reality.
There is a rapid influence in industries infrastructure with emerging cloud computing technologies and their benefits. Industries are now transforming their conventional systems by making use of cloud computing service models (SaaS, PaaS and IaaS) and deployment models (private, public, community, and hybrid). Service models classify different types of services available on the cloud. Software as a Service (SaaS) is responsible for handling of applications on the cloud. These services can be accessed by users through some device (e.g. mobile). Platform as a Service (PaaS) is used for deploying clients newly created or purchased applications on the cloud. Infrastructure as a Service (IaaS) allows the clients to deploy random software’s including operating system; they are not allowed to manage the cloud
Infrastructure but they have some control over the deployed applications. Deployment models includes Private Cloud exclusive for specific organization, Community Cloud mutually used by many organizations, Public Cloud offered to public or group of industries, Hybrid Cloud is a collection of two or clouds thus sometimes solving portability issues.
With the evolution of cloud we can store and process almost all our data on cloud. Technology advancements have made the devices fast, so we can process a lot on the device and save the transmission cost, so that we don’t have to transmit huge amount of data on cloud.
We needed to send an image to the cloud to search for a book in the library and process this image on cloud; this consumed a lot of bandwidth. Now as we can process the images on the personal smart devices, using OCR techniques we can extract the features of the book like book name and author of name etc. send only this data to the cloud for searching purposes which can save a lot of transmission cost. This data is searched on the cloud and the cloud can tell all features regarding the book like rating of the book, similar books from different authors, price of the book and its availability.
The organization of the paper is as follow: Section-I is the introduction of the evolution of cloud. Section-II Literature review present. Section-III tells about the previously proposed model. Section-IV describes the newly proposed system. Section-V finally concludes the paper.
-
II. LITERATURE REVIEW
Mell and Grance [2] at NIST characterizes cloud computing as a blueprint that facilitates direct connection with networks, servers, storage devices , software applications and different services using service and deployment models provided. This would help in covering different social and technical issues faced by organizations. These issues might be related with cost, building and security of cloud computing and its impact on IT units.
Qi and Gani [3] proposed that there is a large increase in the cloud based software applications with the advancement in Mobile Cloud Computing (MCC). They proposed three optimal approaches for MCC. 1st: All data and associated tasks are placed on a virtual terminal and that virtual terminal is connected with cloud hence improving results. 2nd: Using single cable network is a superior approach as compared to wireless network resulting in better communication service. 3rd: Applications requiring large number of data and computational tasks which cannot be deployed on mobiles are divided into high and low computational tasks. Higher computational tasks are handled by the cloud and low computational tasks are performed by mobile devices.
Bahl and Han [4] when merging mobile and cloud computing proposed a research questionnaire that focus on designing cloud computing at enterprise level, what enhancements can be made to current cloud infrastructure and how enhancement can be made in present technologies. They further proposed that sections of human commotions and their underlying constraints can be transformed by providing different services through mobile cloud. The mobile users make use of cloud computing services to get various benefits without postponement of any work thus empowering them and ending their worries. They visualize that in future mobile cloud and computing apps will be on top of ecological unit.
Jain and Rani [5] explore benefits of using agile methodology with cloud computing. They suggested that organizations can strengthen their IT structure if they follow above techniques in combination. This provides better service availability by reducing organizations budget. It provides continuous process improvement, lessens the development time by 75% and making the system stable by reducing the workload. Since, this technique replaces the documents with whiteboards and other similar techniques the overall intervening time of working can be reduced.
Haung, lin and lee [6] developed a book searching system based on augmented reality in conjunction with cloud computing. The purpose of developing the system is to give users an ease in book searching. They use mobile along with the camera for confinement of book spine images and transferring the results to the cloud for high computational tasks. In the cloud the results are matched with the information already present in the database. The best matched results were then transferred back to the device and through augmented reality the results are rendered on to the display screen.
Das and Vaidya [7] proposed an agile cloud framework for Computer Science Corporation (CSC) an American multinational company. For their companies projects they defined a workflow that consist of: 1. Inception Phase which includes project initiation. 2. Elaboration Phase consist of sprint planning, meetings and reviews. 3. Construction Phase is done to bring the project to the final state for user acceptance. 4. Transition Phase allows the team to make changes to the project if any and closing the project.
The invent of mobile computing has opened many path ways of research for mobile users. Two of the main issues in the interaction of mobile users with the cloud server is the privacy and security of the data that is transferred between the two. To ensure secure transmission of data from the cloud server to the mobile user, the advantages of cloud computing should be known in advance. Secondly, the aspects of security are analyzed by observing the behaviors of mobile terminals, the underlying network and most importantly the cloud server used for computing purpose.
Hui Suo, Zhuohua Liu, Jiafu [8] Wan, in their paper, have highlighted the significant issues of security and privacy that occur frequently in cloud computing applications. The importance of cloud computing in today's world is analyzed and on the basis of this significance some of the major issues regarding security of client's data are represented. Based on the nature of the issues, some of the standard approaches including encryption, anti-malware, access control mechanisms etc are presented as the optimum solutions.
Mostly data in the libraries is in printed form. Searching among this data is a very difficult task. The evolution of digital libraries has made this task very easy. But huge amount of scanned documents cannot be searched easily. OCR systems have been very helpful for this problem. But OCR finds its limitations in different handwriting styles and degraded texts which are very difficult to recognize.
Urdu OCR [9] is a very difficult task due to the reason that Urdu characters have different appearance depending upon whether they are appearing in isolation, in the start, middle or end of the text. The segmentation of characters from a word is a very difficult task. This difficulty has increased due to the overlapping nature of Urdu. The proposed model works in two phases i.e. indexing and retrieval. The partial words are extracted by binary conversion. In the second phase PWs in the query word are compared with the PWs in the indexed document. The most difficult task is text segmentation. There are a lot of segmentation techniques but not efficiently applicable to Urdu. This issue has been resolved by not going for word segmentation rather PWs segmentation. These PWs are comprised of more basic Urdu characters which are actually used in word recognition.
-
III. PREVIOUS MODEL
Previous mobile augmented reality system was based on the client-server mode as shown in Fig.1. Processing work was distributed among the client and server side. Local processing was done on client side and huge processing database matching and algorithms were run on the cloud. User captures the image using built-in mobile camera. Image processing is done using embedded mobile processor to get the feature of the images. After collecting the information, it is sent to the cloud for massive computation. Information sent to the cloud is matched with similar data residing there and after matching, the best suitable results are sent back as information to the mobile with detailed information. After transmitting data the information is displayed as an augmented object.
This model is basically designed for finding the desired books from the cloud.
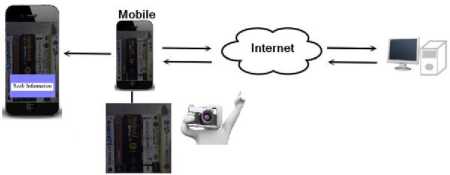
Figure 1: Original Model
The image taken by the embedded camera is passed through several steps. In first step the acquired image is normalized for the purpose of noise removal. After image acquisition a standardized algorithm is used for extracting the quality information. The data retrieval process should be highly reliable and efficient. This particular information is then transferred to the cloud server through underlying network.
The second step comprises of feature matching of transferred data with the existing data of cloud servers.
In the final step, an augmented authenticity component extracts the simulated information including book title, its ISBN number, author’s name etc. This extracted information is then finally displayed on the mobile screen. Flow chat of whole scenario is shown in Fig.2.
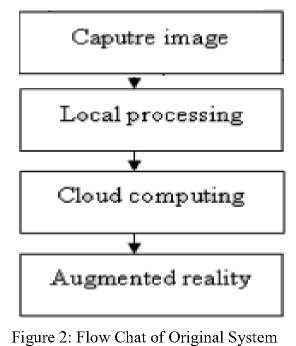
The basic aim of image processing is to retrieve desired characteristics from the server, which requires some preprocessing filtering mechanisms for noise removal and quality enhancement.
Due to bandwidth restrictions of the network, it is costly to send the captured snap using mobile internet to the cloud, so only the necessary information is transferred over the network.
Mobile Devices are limited in their physical resources having lower memory and computational capabilities, so for manipulating large databases cloud servers are exponentially utilized. Cloud servers can smoothly be extended as required.
While the desired information is detected and recognized, it is sent to the cloud and matched as a string arrangement. The best matched results are then passed on to the client’s PMD. The string storage and transfer method is less expensive and more efficient.
An alternative way of searching and comparison comprises of rendering required information to the next or right side of the book spine. This can be done by calculating the coordinates of the book spine. The density of the identified information is used for finding the exact location of the book. Another utilization of this step can be done in the matching process of cloud.
-
IV. PROPOSED MODEL
We will discuss briefly about the mobile cloud computing, the risks and threats involved and then a proposed solution, which is the aim of our paper.
Mobile cloud computing means the availability of different cloud services on different handheld devices like smart phones and tablet PCs over a mobile network. With the evolution of mobile cloud computing the storage and complex computations’ burden can be put on the cloud.
Data access has become easier; users can connect to the cloud through any wireless terminal and can gain access to their data. The architecture of cloud includes its basic infrastructure and the servers which are responsible for providing the IT services on user’s demand.
Coming towards the threats and issues involved in mobile computing there are two main concerned things i.e. mobile terminal and mobile network.
A mobile terminal has an open operating system which supports third party software and wireless access of internet.
This high availability of internet and openness of operating system is the weakness which is targeted by the attackers. There are some corrupt files also known as viruses which are automatically downloaded to the devices undetected. These viruses can get access to the personal information of the user and can cause an automatic pay which may result in economic damage. These viruses can be spread in variety of ways like SMS, MMS and Wi-Fi etc.
There are also some software drawbacks which need to be resolved. For example the username and password of a user are its very critical information, which while transferring using FTP are saved in clear text form in a file. This can cause unauthorized access to user’s personal information and thus leakage of information.
In some cases the bugs involved in the operating system are also used to hack the devices.
Now we will discuss briefly about the issues involved in the mobile network.
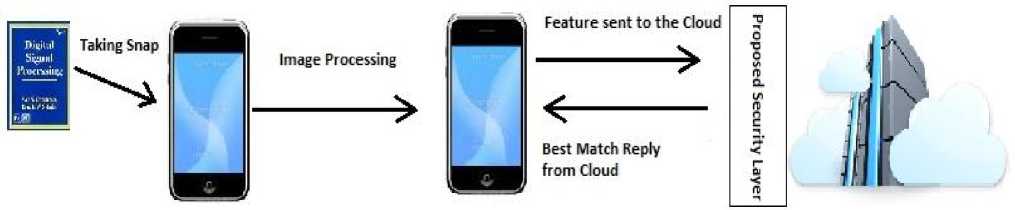
Figure 3: Proposed Model
Most devices use Wi-Fi to connect to the internet. Wi-Fi has weak encryption mechanism, which may result in information loss.
As we know that there is huge amount of information on the cloud so it is likely to be attacked by the attackers. So it must be reliable enough so that the users may put their information on the cloud without worrying about the loss. The DOS attack can close the service of the cloud resulting in no access to the user’s information. Another issue is that the information is scattered i.e. it is not stored in one place as there are a number of users. So the users must feel secure about their information.
Solution:
In the security layer two things should be implemented i.e. detection of viruses and prevention of viruses. There are many advanced software available for this purpose. Detection means finding the viruses or malware in the existing data and files and removing it. Prevention means that the virus should not be allowed to enter the device.
These softwares must be kept up to date because the types of malwares change rapidly so the anti-malware should be able to tackle all the new types of malwares.
Sometimes users’ bad actions also cause abnormal behavior of device resulting in creation of bugs which may cause loss of information. This should also be avoided.
A good approach is applying access control i.e. allocating attribute identifiers to users which specify that which user has what privileges.
Another attribute which must be implemented is authentication of user by user id and password which are transmitted by secure and advanced encryption methods.
Another feature which could be introduced is live update. If the user searches for some data on the cloud, for instance let’s say a book, and it is not already present on the cloud then its features are automatically uploaded to the cloud by the applications running on cloud. The features could include price of the book, author name and brief description about the book. This will help in keeping the database updated for the upcoming users. This data go through from security check layer and then update on cloud. The complete flow chart of proposed model is shown in Fig.4.
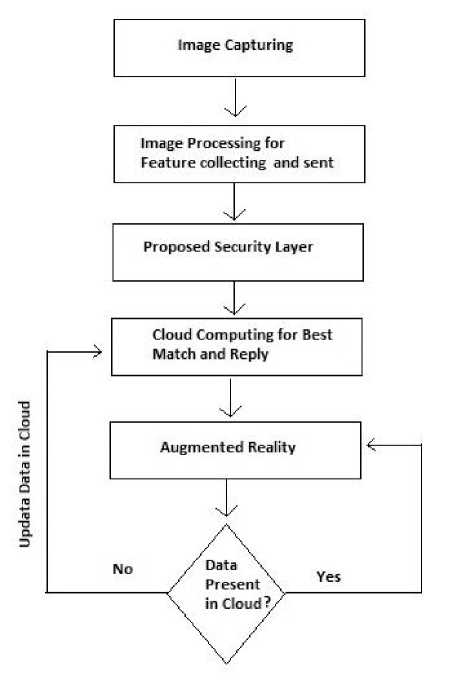
Figure 4: Proposed Flow Chart
-
V. CONCLUSION
In this paper a secure and dynamic framework for online book searching on cloud is presented as a mobile augmented reality. Images acquisition and processing is done on the mobile. These images are collected through OCR and then sent to the cloud for book searching. In the cloud, traversing is done for collecting best matched results and finally the results are transferred back to the mobile for display as an augmented data. A security has also been introduced in this model for protection of cloud sensitive data. If the required data is not found in the cloud server then it will be updated in the server with security checks applied properly.
In future more work distributed between mobile and cloud for more fast response, as server in cloud has latest and high performance resources for high processing speed as compare to mobile. Therefore more work should be shifted to the cloud. Urdu OCR also implemented for the country like Pakistan where many book are in Urdu language. SO that information related to Urdu literature book also can be store in cloud, as we know clouds are very flexible so that it can be extended according to our requirement.
Список литературы Secure and Dynamic Model for Book Searching on Cloud Computing as Mobile Augmented Reality
- Jae Hyuck Jang; Won Vien Park; Chang-Geun Song; Sun Jung Kim; Young-Woong Ko, "U-Sketchbook: Mobile augmented reality system using IR camera," Advanced Communication Technology (ICACT), 2011 13th International Conference.
- Peter Mell, Tim Grance, "The NIST Definition of Cloud Computing" under the Federal Information Security Management Act (FISMA) of 2002.
- Han Qi; Gani, A., "Research on mobile cloud computing: Review, trend and perspectives," Digital Information and Communication Technology and it's Applications (DICTAP), 2012 Second International Conference.
- Mahadev Satyanarayanan; Bahl, P.; Caceres, R.; Davies, N., "The Case for VM-Based Cloudlets in Mobile Computing," Pervasive Computing, IEEE , vol.8, no.4, pp.14,23, Oct.-Dec. 2009.
- Abhishek Jain, Reena Rani. Article: Analytical Study of Agile Methodology with Cloud Computing. IJCA Proceedings on National Workshop-Cum-Conference on Recent Trends in Mathematics and Computing 2011 RTMC (14):13-14, June 2012.
- Bai-Ruei Huang; Chang Hong Lin; Chia-Han Lee, Mobile augmented reality based on cloud computing," Anti-Counterfeiting, Security and Identification (ASID), 2012 International Conference on , vol., no., pp.1,5, 24-26 Aug. 2012.
- Kirti Vaidya "AN AGILE PROCESS FRAMEWORK FOR CLOUD APPLICATION DEVELOPMENT" Computer Sciences Corporation CSC Papers 2011.
- Suo, Hui; Liu, Zhuohua; Wan, Jiafu; Zhou, Keliang, "Security and privacy in mobile cloud computing," Wireless Communications and Mobile Computing Conference (IWCMC), 2013 9th International, vol., no.
- Abidi, A.; Siddiqi, I.; Khurshid, K., "Towards Searchable Digital Urdu Libraries - A Word Spotting Based Retrieval Approach," Document Analysis and Recognition (ICDAR), 2011 International Conference on.


