Study on Challenges, Opportunities and Predictions in Cloud Computing
Автор: Jitendra Singh
Журнал: International Journal of Modern Education and Computer Science (IJMECS) @ijmecs
Статья в выпуске: 3 vol.9, 2017 года.
Бесплатный доступ
Cloud computing is transforming the way IT is owned and utilized in the present day business scenario. Several predictions by the researchers and analytical enterprises have predicted unprecedented growth for this emerging paradigm. This work is an attempt to analyze the cloud future based on the various reports and predictions published recently. We have explored the various opportunities that will drive the cloud growth. We have also highlighted the effect of cloud in Indian and US market. Significance of the study is validated by conducting the Strength, weakness, opportunity, and Threat (SWOT) analysis. Based on the findings, we have identified the intensity of challenges faced by the various types of cloud deployment model. Correspondingly, we have recommended the critical challenges that need to be addressed first, in order to facilitate the cloud in gaining further momentum.
Cloud challenges, cloud future, loud opportunity, cloud prediction, security challenges
Короткий адрес: https://sciup.org/15014951
IDR: 15014951
Текст научной статьи Study on Challenges, Opportunities and Predictions in Cloud Computing
Published Online March 2017 in MECS DOI: 10.5815/ijmecs.2017.03.03
In Legacy based system, resources are managed and maintained by the organizations themselves. Mainframe is the prominent paradigm used in legacy based system and prevailing for substantially longer time. However, maintaining the resources has led to huge investment, at the same time; hiring skilled manpower was cumbersome as well as expensive. Non-IT Organizations, specifically small and medium enterprises (SME’s) were searching for cheaper and reliable computing environment. To cater the need of such users, a new paradigm popularly known as cloud computing has emerged.
Cloud computing offers its services as a utility based model in which Information Technology(IT) capabilities are offered as a services, whereas users are paying as they go (Lin, Fu, Zhu, & Dasmalchi, 2009;
Various reports have been published by the research organizations including International data Corporation (IDC), Aberdeen, Gartner etc. reveal great cost saving due to the cloud usage. According to the General Service administration (GSA), they have saved around $2 million due to the cloud adoption in their mail services (Coleman, 2012). Saving is attributed by switching from their own maintained infrastructure (mail) ‘Lotus notes’ to the cloud. It is believed that switching to the cloud saves 35% to 50% in operation and infrastructure cost (Wilcox, 2011). In cloud, the major saving is resulted due to nonprocurement of IT infrastructures that need to be purchased upfront in legacy based system. The worst part is that the infrastructure undergoes replacement in every 5 years’ due to the change in technology, as per the Murphy’s Law. This law is still relevant for the hardware maintained.
Realizing the huge business potential, IT giants including Microsoft, Amazon, IBM etc. have already adopted the cloud business and offering wide variety of services through their cloud. This has led to stiff business competition among the small emerging and large organizations offering cloud services. IT Giants including Amazon, Microsoft, IBM etc. have captured the substantial market share and increasingly popular among the users for their brand value and services. Microsoft is offering its services with the nomenclature of Windows Azure, whereas the Amazon is offering its service with the nomenclature of Amazon web service (AWS). Services offered by the IT Giant are ranging from IaaS to SaaS. In addition, services such as management as a Service (MaaS), Security as a service (SecAAS), Hardware as a Service (HaaS) etc. have also emerged. New Services are continued to be developed in order to cater the varying need of the subscribers.
Objective of this manuscript is enumerated as follows:
-
a. To review the various cloud predictions
-
b. To categorize the various challenges in cloud paradigm.
-
c. To identify the various opportunities existing in cloud computing.
-
d. Discuss the case of cloud adoption in India and U.S.
-
e. To conduct the SWOT analysis.
Remainder of this manuscript has been organized as: Section 2 describes the usage of cloud paradigm in contemporary world. Section 3 describes the challenges that cloud paradigm is facing. Section 4, reviews the various predictions by the research majors including Gartner, Forrester, IDC etc. Finally, section 5 analyzes the predictions and future of the cloud computing after taking various challenges into account.
-
II. Usage Pattern of Cloud Computing
Private, Public cloud, Community cloud and Hybrid cloud are the popular cloud deployment models. Users are adopting the cloud model based on their requirement. To determine the satisfaction of the cloud subscribers, a survey was conducted by the Cloud security alliance (CSA), and Information Systems Audit and Control Association (ISACA) in 2012. Survey revealed that 2.8% users were unsatisfied with the SaaS. In the same survey, unsatisfied subscribers using the IaaS and PaaS were 6.7% and 12% respectively. Therefore, it can be inferred that the users utilizing the SaaS services were among the highly satisfied one.
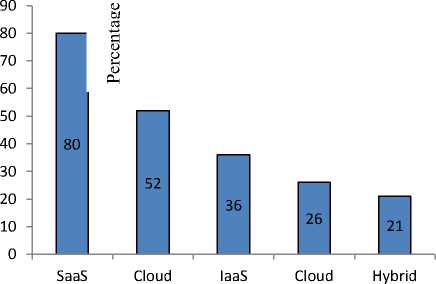
In a recent survey conducted by the research major Aberdeen group pertaining to public cloud usage, it is revealed that the public cloud has reasonable share in SME’s, and large enterprises. These enterprises are subscribing public cloud to cater for their varying needs that include SaaS services, cloud storage, IaaS, Cloud recovery etc. Share of these services have been illustrated in the figure 1.
storage recovery
Fig.1. Public cloud usage (Source: Aberdeen, 2013)
From the figure 1, it can be inferred that the SaaS and cloud storage are the widely subscribed services in the public cloud domain and enjoys 80 and 52 percent share respectively. SaaS services are widely subscribed by the small and medium enterprises. Cloud recovery and hybrid are the least subscribed services by the large organization. Correspondingly, cloud recovery and hybrid cloud enjoys with 26 percent and 21 percent share respectively. For the services mentioned in the figure 1, usage of services is governed by the size of an enterprises and same has been illustrated in the figure 2. Interpreting the figure 2, it is evident that the cloud services are becoming increasingly popular in small enterprises. In majority of the services SME’ are leading in subscription. SaaS and cloud storage is highly sought services by the SME’s.
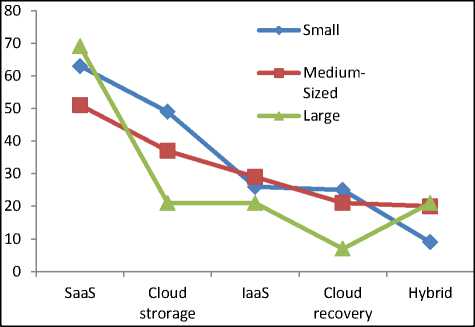
Fig.2 Public cloud services utilization by Small, medium-sized and large organization (Source: Aberdeen, 2013)
-
III. Challenges to Cloud Computing
Cloud computing is gaining support from wide variety of subscribers ranging from large organization to the individual business groups. Despite several favorable conditions, this emerging technology is facing various challenges from many fronts. Several reports published by the organizations such as Cloud security alliance (CSA), National institute of standard and technology (NIST) etc have also highlighted the same fact. Several significant reports are being discussed in the upcoming sub-section.
-
A. Reviewing Cloud challenges reports
Cloud computing has evolved from the legacy based system. Consequently, challenges applicable to the legacy based system are more or less are still applicable to the cloud computing. In addition, cloud specific challenges, driven by the virtualization, multi-tenancy, ubiquitous access etc. have also emerged. Assessing the criticality of the situation, many of the significant reports by the organizations including CSA, NIST, and European Union Agency for Network and Information Security (ENISA) etc. have been published to highlight the impact of aforementioned challenges. Reports published by these research major companies are based on their area of specializations, for instance, CSA published reports on the security challenges. These reports are highlighting the challenges that are applicable to the cloud computing and suggesting measures that need to be initiated in order to address the specified challenges at the appropriate level.
Existing security challenges are acting as deterrent and retarding the exponential growth in cloud paradigm. In addition, adversaries view the cloud as huge collection of resources in a single control. Consequently, they are exploiting the cloud functioning and evolving new methodologies for unauthorized data gathering and attacking the cloud. Reviewing the cloud reports and various publications, factors such as data security, loss of the data, availability of the services, performance etc. have been identified as the major challenges. In cloud paradigm, challenges for the expert subscribers are significantly different from non-expert users. .
Upon reviewing the literature, we have grouped the identified challenges in various categories that include security, availability, interoperability, performance etc as illustrated in the figure 3. Each of them has been further discussed in detail in subsequent sub-sections.
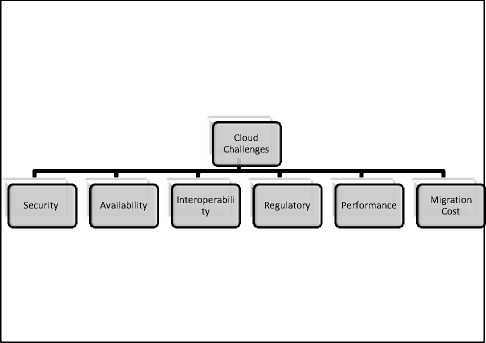
Fig.3. Cloud computing challenges
-
B. Security challenges
Security is the major challenge in the cloud computing and need to be managed at various levels. For instance, during transmission security is needed at the client side, security is also needed at storage time (Singh & Kumar, 2014; Singh, 2014). When the data is placed at cloud service provider, resources need to be protected from the unauthorized access from within and outside of the cloud provider’s scope. Cloud security alliance (CSA) and NIST are the leading groups publishing the various reports on security issues. Published reports are also suggesting the measures to be initiated in order to improve the security in the cloud paradigm.
A number of threats and challenges can be identified with the help of manuscript published in leading journals. For instance, Cloud security alliance (CSA) has published the document on security titling “Top ten threats in cloud computing V1.0” (CSA, 2010). In this document CSA has identified ‘Ten’ major threats prevailing in the various cloud deployment models and services. Publication highlighted the malicious insider, insecure interface and API’s, shared technologies issues etc as the major security threat (CSA, 2010). Cloud security group (CSA) has not restricted itself to this study, instead in its subsequent publication titling "The Notorious Nine: Cloud Computing Top Threats” published in 2013, document has extensively discussed the nine notorious threats (CSA, 2013). Beside identification of threats, significant examples of the major security breaches were also highlighted.
Physical security of cloud infrastructure is equally important. Cloud physical infrastructure is accessible to technical personnel involved in managing the resources, and security personnel involved in safeguarding the resources located in a specific data center. Enough care need to be exercised for the recruitment of personnel deployed at cloud infrastructure. Decision needs to be taken for the selection of appropriate personnel for the physical security of cloud resources in order to avoid any data theft and sabotage activities.
-
C. Availability challenges
In cloud computing, resources available at remote locations are accessed using internet. Availability challenges may arise at the client end or the service provider’s end. Correspondingly, it is significant that both the internet and resources at the cloud provider’s end should be available at all the time. Lack of availability at any one of them may lead to the disruption of the cloud services. Disruption of the cloud services is also known as cloud outages. Disruption of cloud services or cloud outages may lead to huge losses considering the types of business conducted by the specific organization. Impact of cloud outages can be determined by the study of International working group on cloud resilience (IWGCR). It reveals that a total of 548 hours of downtime in 13 major cloud services have caused a loss of more than $71.7 million since 2007( http://iwgcr.org ). Researchers are of the view that the outages may be more than the above stated facts as many more of the outages go unreported (Baston, 2012). Various cloud outages and losses incurred due to the cloud outages have also been highlighted by Singh and Kumar (2013). Authors have also suggested the broker based technique in order to improve the availability and reliability.
Consequently, it can be inferred that the availability remains the huge challenges even for the major cloud providers including Microsoft, Amazon, Go-grid etc. (Singh & Kumar, 2014). Although many of them are claiming for 99.999 % availability, however the fact of the matter is that the majority of them are hovering at around 99.9 percent availability only (Gite, 2008;
(SLA) need to be put in place so that in future cloud provider should not deviate from the responsibility of services to be delivered as agreed in the SLA.
-
D. Interoperability
Currently, cloud providers are using their own protocols and API’s for their interface. Correspondingly, data stored in one cloud may not be compatible with another type of cloud. Consequently, it may lead to lockin, which is undesired from the subscriber’s perspective, since data hosted by the subscriber is important for him. Lack of interoperability may lead to limited options of switching from one provider to the other provider. In addition, user may be aiming to subscribe multiple clouds based on their specialization (Singh & Kumar, 2014). For instance, cloud provider have established themselves in specific domain and enjoying great reputation, for example Salesforce for SaaS, Amazon EC2 for the IaaS, Windows Azure for PaaS, etc have already gathered the specialization in their respective area. Users aiming for SaaS services of Salesforce, IaaS of Amazon may face huge challenges in terms of service utilization of multi cloud provider. In all these clouds, adoptability, and interface is needed from one cloud provider to the other. Lack of cloud interoperability hinders the subscription of multiple clouds and migration from one cloud provider to the other one. Although, XML is widely used for the transferring of the data from one cloud provider to other; however it is inadequate to represent the information semantics (Joshi, et al, 2004).
To facilitate the interoperability in the cloud paradigm, serious discussion is already underway that is aiming to resolve the complexity in the interoperability. Various standards organizations have already been set up in order to arrive at the common standards. Although a lot has been done, yet a long distance is yet to be covered in order to realize the interoperability issue becomes a reality.
-
E. Regulatory issues
In cloud computing, Cloud providers are offering the resources through the data centers. Majority of the data centers are available in USA, countries of European Union, Singapore etc (Singh & Kumar, 2013). Consequently, it poses great regulatory challenges as the data is stored outside the user’s own country. In majority of the countries, prevailing regulatory acts does not permit to store and compute the data outside their own country, as it may lead to breach in privacy and security of the data. Acts like, Health Insurance Portability and Accountability Act (HIPPA), Gramm-Leach-Bliley Act (GLBA), Payment Card Industry Data Security Standard PCI-DSS, etc. are some of the prevailing regulatory acts and need to be abided by the cloud subscribers (Singh & Kumar, 2013). Majority of these regulatory acts are prevailing from the time of legacy based system, therefore need to be mapped with cloud requirement.
Cloud specific standard such as FedRAMP has also emerged; however, liability of security is still vested within the cloud subscriber. Considering the significance of regulatory compliances, many of the major cloud providers including Amazon, Microsoft, Gogrid, etc have got themselves certified for their compliance of regulatory acts. Details of the regulatory compliances for which they are certified are enumerated in their respective website.
-
F. Performance issues
Performance in the cloud computing is a sensitive issue and need to be managed in order to offer the similar feel as offered by the legacy system. Performance of the cloud is governed by:
-
• Infrastructure performance at the Data center.
-
• Resources utilized to access the cloud, such as internet etc.
-
G. Demand in network traffic
The other major challenge in cloud paradigm is related to the network bandwidth offered and the one available. Enterprises needing huge data transfers from ownpremises to cloud and vice versa are hesitant due to the limited upload speed. Delay in uploaded data has been measured and it has been discovered that an internet line of 10 Mbps need 12.5 days to transfer/Upload 1 TB of data whereas an internet line of 02 GB will require of around 02 hours (Profeeitt, 2012) in order to upload the data on the cloud resources. Consequently, much needed action is to be initiated at the earliest in order to improve the network speed that is needed.
Demand of cloud resources will witness unprecedented growth. Cloud index report projected the increase in workload in cloud data center to multi-fold. In Asia Pacific region itself, load to grow over 5 times by 2018 from the one handled in 2013 (Cisco, 2014). However, for Europe it is just to be double for the same period.
Middle East and Africa will witness the maximum growth in traffic. In these regions, traffic is set to grow from 31 Exabytes of 2013 to 262 Exabytes by 2018 (Cisco, 2014). By 2018, 78% of workloads will be processed by cloud data centers, 22% will be processed by traditional data center. Overall workloads will double by 2018. By 2018, 31% of cloud workload will be public cloud data center, 59% of workload will be SaaS based (Cisco, 2014).
-
H. Migration Cost
Migration cost represents the cost associated in switching from the existing system to the cloud based system. Adopting the cloud paradigm is relatively easier for the enterprises with no IT infrastructure. Since, there would be no loss in relinquishing the existing infrastructure. Migrating from the traditional system is costly since IT infrastructures are already maintained. Migrating from traditional system to cloud involved the financial overhead, due to the following reasons:
-
• Existing IT resources need to be relinquished that leads to the revenue loss from the existing resources.
-
• Recurring expense in order to subscribe the cloud resources and internet connection, whereas no expenditure is needed in own maintained network.
-
• Expenditure is also needed to transfer the existing data to the cloud.
Correspondingly, migration to the cloud may not be feasible for many of the enterprises who have greatly invested in establishing the IT resources.
-
IV. Predictions on Cloud Future
Despite of several challenges enumerated in the preceding sections, there are many studies which are predicting the great future for this promising new paradigm. These predictions are made by the research majors including the IDC, Gartner, Forrester, Aberdeen, etc and have been discussed in the following sub-sections.
-
A. Predictions by the IDC
As per the IDC, cloud services are set to grow from $47.4 billion in 2013 to $107 billion in 2017. SaaS will continue to remain the largest public IT service and by 2017 it will drive 59.7 % of cloud services revenue. Opportunity also exists in cloud computing due to the continued tariff cut by the public cloud providers.
-
B. Predictions by the Gartner
Gartner predicts in its symposium that the cloud will continue to grow up-to 2016(Gartner, 2013). Cloud analyst, participated in the cloud symposium have predicted that the major IT spending of an organization will be focused on the adoption of cloud paradigm. Cloud adoption trend will continue by the year 2016. That means that the budget of traditional based computing will
shrink tremendously. Similarly private cloud that is continued to be adopted by the larger organizations will give the way to the hybrid cloud in order to realized the benefit of public cloud. In addition, cost saving mantras adopted by the majority of the large organizations in the current economic recession that has shaken the many countries will further drive the cloud growth.
According to the Gartner prediction, spending on the cloud will consistently increase till 2016 in which it is predicted to reach around $210 billion, a phenomenal increase from the year 2010 when the spending was restricted to mere $77 billion. In the same period, IaaS will emerge as a major offering and same has been illustrated in the figure 4 (Gartner, 2013).
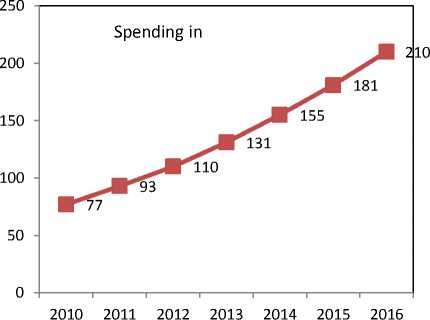
Fig.4. Public cloud spending 2011-2016 Source: Gartner (2013)
IaaS growth is primarily driven by the Murphy’s Law, SME’s, and adoption of cloud by the business firm. IaaS will be followed by the SaaS that is also has the huge potential for growth. In addition to PaaS and SaaS, share of other service such as paas is also set to grow, and same has been illustrated in the figure 5.
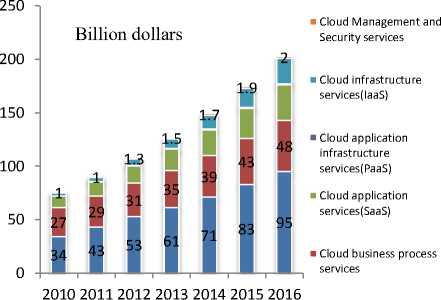
Fig.5. Public cloud services market segment 2010-2016 Source: Gartner (2013)
-
C. Predictions by the Forrester
Another research major enterprise, Forrester has published its reports to predict the cloud market. According to the Forrester, public cloud market to reach $191 billion by 2020. The forecast is 20% above its
previous forecast in the year 2011. Forrester prediction is illustrated in the figure 6.
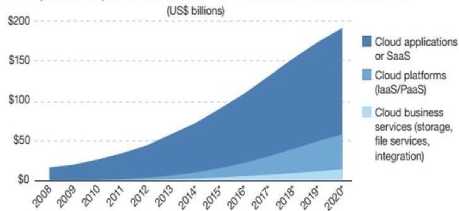
Fig.6. Public cloud prediction by Forrester
From the figure 6, it is apparent that the SaaS will have the major share in the public cloud domain. SaaS will be followed by IaaS/PaaS. Storage, file services will gain further momentum from the year 2015 and will have the substantial market share by 2020. On one hand cloud computing will able to gain the substantial market share, on the other hand, it has to face the major challenge from the security front. It is evident from the figure 7 that the security is the major threat in cloud paradigm, and SaaS model in particular.
"How concerned is your firm with the following potential issues around using software-as-a-service (SaaS)?1' (4 or 5 on a scale of 1 [not at all concerned) to 5 (very concerned])
■ Q4 2013 (N = 1.417)
■ Q4 2011 (N = 1.332)
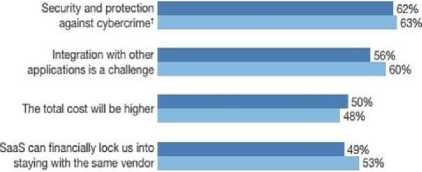
Fig.7. Issues in SaaS
-
D. Cloud predictions for India
India is considered as an IT giant specifically in application software. IDC estimates that Indian cloud market is set to grow around $3 billion by 2015. Interestingly, Gartner predicts that the 2/3 of the CIO will migrate to the cloud computing in next two years. Beside the existing cloud provider, many more companies will emerge in cloud domain and would be offering their cloud specific services. CIOReviews magazine have identified 20 most promising cloud computing companies that includes AppPoint software solutions, A2zapps.com, ciphercloud, Qualispace, Ramco etc that will gain the momentum soon.
Cloud major Amazon is eyeing on the $2 trillion cloud services opportunity by setting up the data center in India. However, existing regulations don’t allow to non-telecom companies to lease optical fiber cables, required for transmitting data. Unified access service license (UASL) is acting as the major barrier in this regard. IDC, another research major has predicted that the cloud market in
India would grow from $688 million in 2012 to around $3.5 billion by 2016. An IDC Survey of 473 respondents, out of which 200 were small organizations have demonstrated great willingness to adopt cloud computing. Potential for India is huge, since India is a home of around 47 million small businesses, yet only 1% is Microsoft an entrenched player in Indian market has to target this small business segment.
Aligning with the other parts of the world, Public cloud is set to emerge as top subscribed services and predicted to be around $83 million by the year end from $632 million in 2014. According to the Gartner, cloud market is poised to reach $1.9 billion by the end of 2018. Dell India is confident of great opportunities including metrocloud in India and set to replace SONIT, SDH with optical packet switches and WDM metro. Leveraging the cloud paradigm, SME’s are becoming more efficient and productive. SME’s are embracing the cloud to build, test, and to run critical application.
Cloud computing is set to pose huge challenges to the Indian IT firm which have outsource business acting as their major revenue generator. Indian IT firms are maintaining the on-premises servers maintained by the organizations where the less skilled personnel are available or the cost of human resources is high. In cloud services, servers are managed by the cloud provider who can employ the skilled personnel. Managing the cloud data center located at remote location is not costly since relatively fewer personnel are needed to manage the servers. Subscribing to the cloud paradigm will transform the way resources are maintained and used. Since, this service also falls under managed category of services; therefore overall staff needed for the cloud paradigm will be smaller relative to the traditional system.
-
V. Opportunities in Cloud Computing
Cloud computing has increasingly high opportunities for growth. By adopting the cloud services, users can improve their services, at the same time cloud provider can generate huge revenue. The upcoming section enumerates the various opportunities for the cloud computing.
-
A. Reducing Price of Cloud usage
With the passage of time, competitions among cloud providers have increased many folds. Increased competition among the cloud providers is benefitting the cloud users in the form of cost reduction. Various costs cutting in the offered services have been witnessed recently. Cost cutting is carried out by the companies including the cloud major Google, Amazon, etc.
-
B. Google cost cut
Google has also joined the cost cutting in cloud services. Google has cut the price in the range of 10 percent to 48 percent. Same can be evaluated with the help of table 1, enumerated as follows:
Table 1. Google cloud utilization
|
S.No. |
Services |
Percentage |
|
1. |
Google compute engine |
10% |
|
2. |
Google “Big query storage” |
23 % |
|
3. |
Persistent disk (SSD) |
48 % |
|
4. |
Large cloud SQL instance |
25% |
Google is also switching to various cloud services as enumerated in the aforementioned table.
-
i. Amazon
Amazon is the other leading cloud provider. It is also indulged in the price war. Recently, it has reduced the data transfer prices ranging from 6% to 43 %. To improve the user base, it has started few more services, for instance, Amazon aurora, a native RDBMS designed for cloud. In addition, a set of new services that include code deploy, code commit, code pipeline which are cloud native alternatives to traditional application lifecycle management products.
Cloud computing continues to reduce the complexity of managing and working on services by means of automation. It is evident from the recent development in Amazon that has launched AWS lambda. This is neither PaaS nor IaaS (CloudOM, 2014). This is an execution environment with minimal configuration. Unlike IaaS, subscribers do not need to provision and manage Virtual Machine (VM). At the same time, configuration details are minimal in PaaS.
-
ii. Cloud Adoption U.S. Federal Government
Since 2009, US federal government has initiated various efforts in order to shift from own managed data center to the cloud. Key motive behind this move is to leverage cloud paradigm. This is followed by a plan titling “A 25: point implementation plan to reform federal IT management” released by the U.S chief information officer (CIO) in Dec 2010. However, it has to face the challenges that include the heavy cost that will be incurred in maintaining the connectivity that was not applicable in their own managed infrastructure.
In September 2014, Government accountability office (GAO) reported that total number of cloud services deployed in various departments that include Agriculture, Health and human services, Homeland security, etc. have increased from 21 to 101. At the same time, cloud expenditure has increased from $307 million to $529 million. This signifies great shift in various departments from the traditional services towards the cloud services.
-
C. Existence of legacy based system
Cloud computing has the huge opportunities due to the presence of small and medium enterprises. Best-in class organizations are far ahead in the technology relative to the small and medium enterprises. This is primarily attributed to the following factors:
-
• Lack of funds with the small and medium enterprises.
-
• Scarcity of highly skilled personnel.
Existing legacy based system offers huge opportunity for the cloud computing to exploit and grow. It is also apparent from the recent study of the Aberdeen group that highlights that the data center’s resource aging is the major concern for the enterprises and same is illustrated in the figure 8. Once the logarithm trend-line has been drawn, it is apparent that it is not the cost instead aging of the resources is the major concern for the enterprises which are maintaining their own infrastructure. This is followed by the longtime in the deployment of services.
Both the above concerns can easily be addressed by subscribing to the cloud paradigm. By subscribing to the cloud paradigm, dealing with the aging will be the responsibility of the cloud provider, since lowering the services efficiency may lead to the reduction in cloud subscriber, therefore, they would like to constantly upgrade their infrastructure to avoid any customer’s shift.
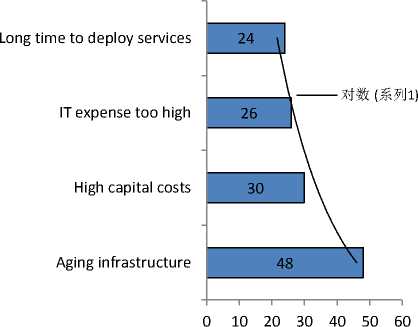
Fig.8. Top data center and IT infrastructure pressure (Source: Aberdeen, 2014)
-
D. Present small and medium enterprises
In its recent report, Aberdeen group has discovered that the best-in class organizations are three times ahead relative to SME’s in resource performance. Consequently, best-in class organizations can offer better services to their customers. With the emergence of prominent cloud players including Amazon, Microsoft, IBM etc. SME’s can also subscribe to the Best-in class and latest resources without managing the personnel and updating the infrastructure frequently.
Business continuity and disaster recovery is the other area that offers huge opportunity for the cloud computing. Downtime causes heavy losses to all types of organizations irrespective of their size. Same is revealed in the Aberdeen group report (Aberdeen, 2014) that reflects losses that are incurred to various types of organization.
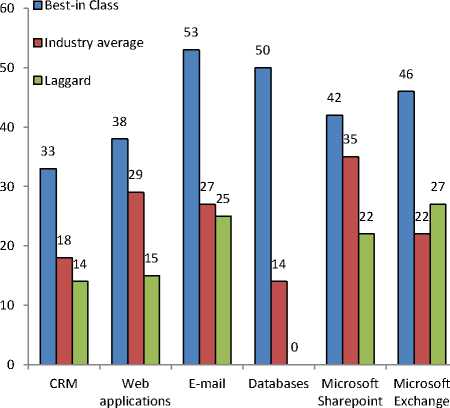
Fig.9. Workload deployed on next generation servers
Table 2. Downtime cost per hour
|
S. No. |
Companies |
Downtime cost |
|
1. |
All companies |
$163,674 |
|
2. |
Small companies |
$8,580 |
|
3. |
Medium companies |
$215,637 |
|
4. |
Large Companies |
$ 686,250 |
It is apparent from the above table that small and medium enterprises are unable to maintain the uptime from their resources for a longer time. As a result, huge losses are incurred to them directly in terms of money as well as indirectly in terms of services and goodwill. This is viewed as huge opportunity by the cloud providers claiming to offer 99.9 % of service availability. Consequently, uptime can be improved by subscribing to the cloud.
-
E. Application development cost and time
Application deployment time is the other major concern of the users. In the legacy based system, applications program need to be developed for the organizational specific requirement. Consequently, efforts are needed for software requirement analysis and specification, development and testing the software. As a result, it requires time and cost. In order to minimize the cost, many small enterprises have approached to less mature organization and incurred huge losses later. Software required is more or less is same, only the scale of information that need to be stored varies. The specific requirement can be met by way of customization of application program.
With the emergence of SaaS, enterprises irrespective of their size can subscribe to SaaS specific services in order to reduce the expenditure, at the same time would be able to leverage the best-in class application. Applications that are no longer needed can be relinquished immediately, since no upfront expenditure was involved in procurement of the application. To cater the emerging need, new needed applications can be demanded and consumed instantly.
-
F. Infrastructure space requirement and cost
To maintain the servers, routers and data center require huge investment in reality sector, personnel, power etc that results in great expenditure. If the usage is less, then the cost invested is unable to yield the optimum return. Coupled with the silo operation, servers were not utilized to their optimum level. According to Oracle, old data center were not designed for the load that is currently they need to handle. Even worst, additional resource requirement for fairly less time is acting as the hindrance for the legacy based system. Provisioning of additional resources require more space, electricity for operation as well as for cooling. Restructuring project was undertaken by oracle, revealed that space can be reduced by 66 percent and operating cost can be reduced by 30 percent, if used at the optimum level (Oracle, 2010). Study conducted by American power Corporation (APC) revealed that 30% of the data center power is utilized for the load and 33% for the chiller. Therefore, subscribing to the cloud data center may result in huge cost saving (APC, 2008). All the above limitations provide fair opportunities for cloud adoption.
-
G. Mobile based cloud services
Recently, we have witnessed unprecedented growth in tablet, iphones, Smartphone’s, etc. Portability, ease of usage, promising features offered, and cheap prices are the key drivers that led to the mobile growth. Mobile sell have surpassed the computers by 2 to 1 (Musungu, 2012). Variety of purpose can be fulfilled with the help of Smartphone including calling, gaming, emailing, social media etc, at the same time it offers great portability and computing power.
In SmartPhones, many apps are popular and simplifying the various task carried out by utilizing the cloud computing. Popular apps can easily be integrated with the available cloud platforms including Amazon web services(AWS), Windows Azure, Force.com, etc. 80% of developed apps are predicted to be integrated with social networking services including Facebook, Twitter, FourSquare, etc (Musungu, 2012). All these requirement offers fertile ground for the growth of cloud paradigm.
-
H. Trust in cloud provider
In a survey conducted by the Microsoft in US has revealed that 75% of SMB subscribed to cloud services have experienced improve in service availability. Out of the 96% SMB’s who have subscribed for the cloud services have confidence that their cloud provider can quickly and effectively restore services during an outage (Microsoft, 2013). Subscribers have great trust on the capabilities of the skilled personnel hired by the major cloud organization for managing the cloud resources for efficiency, security, availability etc. Due to less focus technological issues such as security, SMB’s can pursue new opportunities since security is managed by the cloud provider.
-
VI. SWOT Analysis
Based on numerous studies conducted earlier, we can measure the strength, weakness, threat and opportunities that are prevailing in this new emerging paradigm. Being a new paradigm, many potential cloud subscribers are in the state of wait and watch mode, in order to analyze the cloud performance and future. However, many of the proactive cloud subscribers have already migrated to the cloud and leveraging the cloud paradigm for their advantages.
As with the many of the prevailing paradigm, cloud computing do have its strength, weakness and potential to grow further. Considering, the fact and figures enumerated in the previous sections, we have attempted to conduct the Strength, weakness, opportunity and threat (SWOT) analysis in the contemporary cloud paradigm. Same has been depicted in the following table.
Table 3. SWOT analysis in contemporary cloud computing
|
Strength
provider. |
Weakness
resources.
country.
requirement. |
|
Opportunity
and medium enterprises with lack of funds.
prevailing in many countries compelling for the cost cutting in IT.
access.
outsourcing the specialized services to the specialist.
computing resources for the emerging big data.
|
Threat
securing the data during transfer, and storage.
heterogeneous providers such as cloud resource by cloud provider whereas Internet service by the Internet service provider.
regulatory standards that are specific to the subscriber’s country.
|
It is apparent from the table 3 that there are number of strength, weakness, opportunities and threats that are prevailing in the cloud paradigm. Current focus of cloud providers and cloud subscriber’s trend demonstrate that the positive side of the cloud is increasingly appealing to both the stakeholders, consequently, cloud is growing rapidly.
-
VII. Conclusion
Cloud computing is growing with a rapid rate. Cloud computing is the evolution from the traditional own managed computing. Being a new paradigm, it has to counter many challenges including security, performance, regulatory compliances, interoperability etc. These challenges are posing the huge business losses and retarding the cloud adoption. However, cloud predictions are highlighting the upward trend in cloud adoption. SWOT analysis conducted based on the review of challenges and prediction on the contemporary cloud highlighted many weaknesses and threat in cloud computing environment, yet the strength and opportunities are driving the cloud growth. These opportunities have outnumbered the threats and challenges. However, existing challenges need to be addressed as soon as possible in order to further gain the confidence of cloud subscribers.
Acknowledgement
Список литературы Study on Challenges, Opportunities and Predictions in Cloud Computing
- Barton, M. (2012). Cloud downtime's cost: $70M since 2007, give or take. Retrieved October 29,2012, from http://www.wired.com/insights/author/mikeburton.
- Bigo, D., Boulet, G., Bowden, C., Carrera, S., Jeandesboz, J, and Scherrer, A.(2012). Fighting cyber crime and protecting privacy in the cloud. DIRECTORATE GENERAL FOR INTERNAL POLICIES POLICY DEPARTMENT C: CITIZENS' RIGHTS AND CONSTITUTIONAL AFFAIRS. Available at http://www.europarl.europa.eu/RegData/etudes/etudes/join/2012/462509/IPOL-LIBE_ET(2012)462509_EN.pdf.
- Buyya, R., Yeo, C. S., Venugopal, S., Broberg, J. & Brandic, I. (2009), 'Cloud computing and emerging it platforms: Vision, hype, and reality for delivering computing as the 5th utility', Future Generation computer systems 25(6), 599–616.
- Coleman, C. (2012, September 25). Cloud conversion saves GSA millions. Retrieved from http://gsablogs.gsa.gov/ gsablog/2012/09/25/cloud-conversion-saves-gsa-millions/.
- CSA (2010). Top ten threats in cloud computing. Cloud Security Alliance, 2010.
- CSA (2013). The Notorious Nine: Cloud Computing Top Threats in 2013. Cloud Security Alliance, 2013.
- Cisco (2014). Forecast and Methodology, 2013–2018. Cisco Global Cloud Index
- American Power Conversion, Increasing Data Center Efficiency by Using Improved High Density Power
- Distribution (2008), www.apcmedia.com/salestools/NRAN-6CN8PK_R1_EN.pdf.
- Gartner (2013).Forecast Overview: Public Cloud Services, Worldwide, 2011-2016, 4Q1. Published: 8 February 2013.
- Gonzalez, N., Miers, C., Redigolo, F., Simplicio, M., Carvalho, T., Näslund, M. & Pourzandi, M. (2012), 'A quantitative analysis of current security concerns and solutions for cloud computing', Journal of Cloud Computing 1(1), 1–18.
- Gite, V. (2008). Explain: Five nines (99.999%) computer / network uptime concept. Available at http://www.cyberciti.biz/faq/computer-networkuptime-five-nines-999999/
- Hooper, Christopher and Martini, Ben and Choo, Kim-Kwang Raymond. Cloud Computing and Its Implications for Cybercrime Investigations in Australia (October 15, 2013), Computer Law and Security Review 29(2): 152-163, 2013.
- http://aws.amazon.com/blogs/aws/aws-data-transfer-price-reduction/
- http://googlecloudplatform.blogspot.in/2014/10/Announcing-across-the-board-price-cuts-on-Compute-Engine.html
- http://iwgr.org.
- JanakiramMSV(2014), "CloudTracker, Fourth-Quarter 2014", technical report, GIGAOM Research, Jan 2015.
- Joshi, J. B. D., Bhatti, R., Bertino, E., & Ghafoor, A. (2004). An access control language for multidomain environments. IEEE Internet Computing, 8(6), 40–50. doi:10.1109/MIC.2004.53
- Kwang, K., Choo, R.(2013).Trends & issues in crime and criminal justice. Australian Institute of criminology, No. 400 October 2010.
- Lin, G., Fu, D., Zhu, J., &Dasmalchi, G. (2009).Cloud computing: IT as a service [IEEE]. IT Professional, 11(2), 10–13. doi:10.1109/MITP.2009.22.
- Liu, Y., Sun, Y. L., Ryoo, J., Rizvi, S. & Vasilakos, A. V. (2015), 'A survey of security and privacy challenges in cloud computing: Solutions and future directions', Journal of Computing Science and Engineering 9(3), 119–133.
- Mell, P., & Grance, T. (2011). The NIST definition of cloud computing. Special publication 800-145, National Institute of Standards and Technology.Available at http://csrc.nist.gov/ publications/PubsSPs.html#800-145.
- Microsoft (2013). Small and midsize business cloud trust study. US study result, Jun 2013.
- Mel, P. & Grance, T. (2009), 'The nist definition of cloud computing. National institute of standards and technology', Information Technology Laboratory, Version 15(10.07), 2009.
- Mualla, K. & Jenkins, D. (2015), 'Evaluating cloud computing challenges for non-expert decision-makers', IJDIWC p. 285.
- Singh, H. P., Bhisikar, A. & Singh, J. (2013), 'Innovative ict through cloud computing', IUP Journal of Computer Sciences 7(1), 37.
- Singh, J and Kumar, V (2013).Implementation of User-End Broker Policy to Improve the Reliability of Cloud Services. International Journal of Cloud Applications and Computing, 3(4), 13-27, October-December 2013.
- Singh, J. (2014). Cloud Computing for Beginner to researcher. New York: CS an Amazon company.
- Singh, J. (2014a). Comprehensive Solution to Mitigate the Cyber-attacks in Cloud Computing . International Journal of Cyber-Security and Digital Forensics (IJCSDF), , Vol. 3, issue 2, pp. 84-92.ISSN: 2305-0012 .
- Singh, J. (2014). Data structure simpliefied: Implementation using C++. New York: CS an Amazon company.
- Singh, J. (2014b). Study on the response time in cloud computing . International journal of information engineering and electronic business, , Vol. 5, 36-43(ISSN: 2074-9023 (Print), ISSN: 2074-9031.
- Singh, J., & Kumar, V. (2011). Assessment of security risk in cloud computing environment. Asia Pacific Business review, Vol 7, 180-190.
- Singh, J., & Kumar, V. (2014). Multi-disciplinary research issues in cloud computing . Journal of information technology and research, Vol 7, No. 3, pp. 32-53, DOI: 10.4018/jitr.2014070103.
- Takabi et al. 2010Takabi, H., Joshi, J. B. & Ahn, G.-J. (2010), 'Security and privacy challenges in cloud computing environments', IEEE Security & Privacy (6), 24–31.
- Wei & Blake 2010Wei, Y. & Blake, M. B. (2010), 'Service-oriented computing and cloud computing: challenges and opportunities', IEEE Internet Computing 14(6), 72.
- Wilcox, J. (2011). Gartner: Most cios have their head in the cloud. Retrieved from http://betanews.com/2011/01/24/ gartner-most-cios-have-their-heads-in-theclouds/.
- Yeo, C. S., Buyya, R., Assuncao, M. D., Yu, J.,Sulistio, A., Venugopal, S., &Placek, M. (2007).Utility computing on global grids. In H. Bidgoli (Ed.), Handbook of computer networks.Hoboken,NJ
- Oracle(2010),"Strategies for Solving the Datacenter Space,Power, and Cooling Crunch: Sun Server and Storage Optimization Techniques", An Oracle White Paper March 2010.


