The Rating Mechanism for the Trusted Relationship Establishment for the Security of the Distributed Computer Systems
Автор: Vadym Mukhin
Журнал: International Journal of Computer Network and Information Security(IJCNIS) @ijcnis
Статья в выпуске: 6 vol.6, 2014 года.
Бесплатный доступ
There is suggested a method for the trust level establishment to the nodes of distributed computer systems (DCS) taken into account the dynamics of the information value changing and with the in-time records of the security incidents from the nodes. The proposed method of the DCS nodes rating establishment allows adaptively and during the DCS functioning to determine a safety configuration of resources (nodes) for the information processing in the DCS. Also, there is described the specifics of the implementation of the mechanisms for the nodes trust level establishment.
Distributed Computer Systems, Security, Nodes, Trust Level
Короткий адрес: https://sciup.org/15011312
IDR: 15011312
Текст научной статьи The Rating Mechanism for the Trusted Relationship Establishment for the Security of the Distributed Computer Systems
Published Online May 2014 in MECS
The information security mechanisms for the distributed computer systems should solve the following three main problems [1,2]:
-
• the integration of the developed security mechanisms into the existing computer systems;
-
• the interoperability of the security mechanisms with the different software platforms and environments (J2EE,. NET, Linux-server, etc.);
-
• the trusted relationship establishment between the interacting DCS nodes.
In view of the fact, that the DCS security mechanisms cover many domains in the system, the trust relationships between them play the special role. The trust between the DCS domains and nodes may be conjectural, be based on the topological features, either be explicit, specified with the formal policies and support the mandates exchange. The trust establishment is performing separately for each session, or dynamically on demand [3-8]. Due to the fact that in the DCS domains there are used the different technologies (computer network authentication protocol k erberos , public-key infrastructure - pki, etc.) during the trust establishment mechanisms implementation should be taken into consideration the specifics of the security mechanisms.
The problem of trusted relationship establishment is actual due to the need to support the dynamic and controlled launching of services, which are initiates to perform the certain tasks [3-8]. For example, in a distributed data processing system the temporary services are creating for data retrieving from a remote repository, as well as for the synthesis of results.
The process of the trusted relationships establishment is based on the following aspects [9 -11]:
-
• authorization: it is required to determine exactly which subject is the initiator of service launching;
-
• policies establishment: subjects should be able to create their own policies, in particular , to determine the subjects, that can get access to the services and the corresponding allowable actions, and the subject’s local policy must comply with the DCS security policy;
-
• the level of node reliability: before the tasks initiation the subject may request evaluation of the nodes reliability, which includes the following criteria: the antivirus protection, the the firewalls implementation, the Virtual Privat Network (VPN) mode for data exchange within the DCS, etc. To perform this evaluation the accreditation mechanism is commonly used, where the level of node reliability is determined on the basis of the independed experts review;
-
• complex formation of the policies: security policies for DCS services are created dynamically taken into consideration the several factors: the owner of the resource, the initiator of the service launch, the specifics of the virtual system, which is realized the services, etc;
-
• access rights delegation: in some cases, the temporary services perform the actions on behalf of the subject that has created them, for example, some computational process may requests data in the different DCS domains. In this case, between the domains, which run the services and the one that the request performs, can not be established directly the trusted relationships, then the service must be able to perform actions with the rights of its subject-initiator. This requirement, in turn, raises a number of issues, including: the principle of providing the partial access rights of the subject to the service, a mechanism for resolving situations when the validity of delegated access rights will be over before the service will be complete its actions [9].
One of the possible approach to solve this problem is to implement the controlled access to DCS resources and services. The Global Grid Forum (GGF), currently named Open Grid Forum (OGF), has developed Open Grid Standards Architecture (OGSA) for the Grid systems, and the most important element of the standard is Grid Security Infrastructure (GSI), which describes the main challenges and requirements for safety ensuring for the Grid systems.
In this paper are described the mechanism for the trust level establishment between the nodes of the distributed computer system. There is suggested an approach to form the trust level of the DCS nodes on the basis of the analysis of the dynamics of the processed information value changing. Also these is proposed the method for the dcs nodes rating establishment considering the dynamics of the information value changing and is described the specifics of the implementation of the security mechanisms for the distributed computer systems based on the trust level establishment.
-
II. The mechanism for the trust level
ESTABLISHMENT BETWEEN THE DCS NODES
To improve the security of the distributed computer systems there is proposed the mechanism for the resources protection on the basis of the trust level to DCS nodes with the dynamic changing of the information value.
The suggested approach is the follow. During the DCS scaling each new node or domain are initially assigned with the initial minimal (possibly zero) trust level, because the behavior of this new added node in the DCS is not defined due to the absence of the any relevant statistical information.
Thus, a new added node in the initial period of its operation in the DCS structure has not sufficient trust level to operate with the confidential information and, hence, it will receive the open data only. When the node is functioned in DCS structure, the parameters of its operation and the data transmitted from this node to the DCS are monitored continuously. The need for continuos monitoring of the transmitted data from the nodes, is in particular due to the possibile situation, when a node with a low trust level is acting as an agent of the intrusions, and, for example, performs the unathorized access to DCS resources [9-11].
By default, the new added node is automatically accept the pre-installed security policy in the system. In the general, it is assumed that the new node trusts, at least, a node or domain of the safety administrator, supporting the basic security functions of DCS. Further, during the node is functioned in DCS structure the trust level to it is dynamically changed, and there is forming index of the node rating based on relevant statistical information.
To form the nodes ratings (the trust level) there are used the mechanisms for nodes parameters monitoring, as well as statistical data, received from the nodes with high level of trust, that are previously integrated into the system ( Fig. 1) [3,9].
We suggest an approach to form the trust level of the DCS nodes on the basis of the analysis of the dynamics of the processed information value changing. Let us descibe it below.
Taken into account the processed infomation value, the trust level Tni(t) to the i-th node is:
I СГгУ1е1 N lim I I
Tn i ( t ) = Tn0 Л ( ) g l N i ( t )+1 JJ (1)
where: Tn0 – initial trust level to the node; C(t) - the function of the information value parameter for the time interval (0, t), Ni(t) - the number of safety incidents initiated by or associated with the i-th node on a time interval (0 , t), Nlim – the critical number of the incidents at the same time interval .
The parameter of the information value is presented as the discrete levels, for example, from 1 to 5, depending on the current requirements for the information safety, and is changing dynamically.
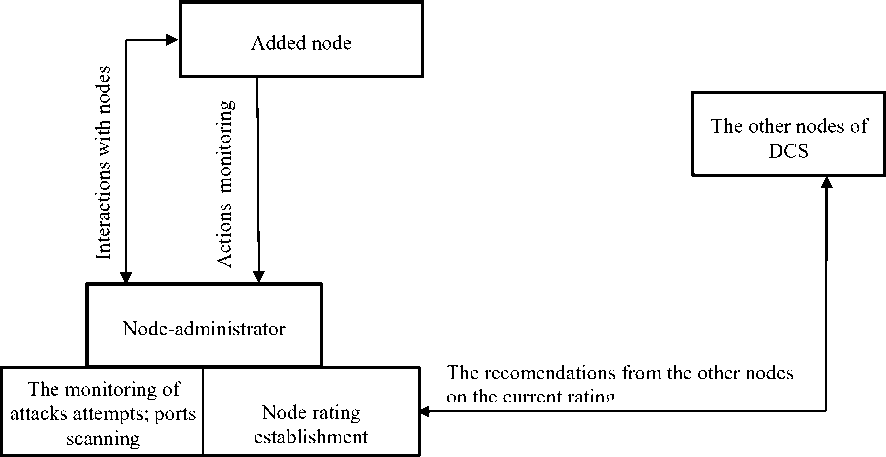
Fig 1: The mechanism for the establishment of the DCS nodes ratings (the trust level)
Security incidents in the DCS are divided into intentional and unintentional actions of the subjects. In general, the DCS subjects, and accordingly, the nodes from which they interact with DCS, can occasionally make unintentional mistakes, that are formally associated with the attempt to get unauthorized access. So, the changing of the parameter N lim , which in fact, defines the maximum allowable number of security incidents caused by accidental actions of the subjects, allows to settled down this problem.
In general, the trust level
Tni
to the
i
-th node during its functioning in DCS structure can be increased, reduced or remain constant. Thus, if the number of security incidents
N
i
(t)
, associated with the
i
-th node on the interval
(0, t)
exceeds the critical parameter
N
lim
(N
i
(t)> N
lim
),
then the trust level to the node is decreased, in the other case
(N
i
(t)
We propose to normalize the node rating on the interval (0, ..., 1). To do this, we define the maximum possible turst level Tnmax to nodes in a certain DCS with a with a fixed initial trust level:
( C max *lg ( N lim ) )
Tn max( t ) = Tn о fx * e (2)
where Tn0 f ix - the initial trust level to the node, Cmax -the maximum level of the informa-tion value on the time interval (0, t).
Further, to norm the trust level the parameter Tn i is divided by Tn max .
The period when the node is functioned in DCS structure (0, t) we present as the finite observation intervals (t k , t l ), and, depending on the results of the node behaviour in these intervals the trust level to it is reduced or increased. As a result, the changing of the trust level Tni to the i - th node is a piece-wise function.
Fig. 2 shows the possible variants of the normalized nodes ratings during its functioned in DCS structure with the dynamically changed index of the information value on the observation intervals.
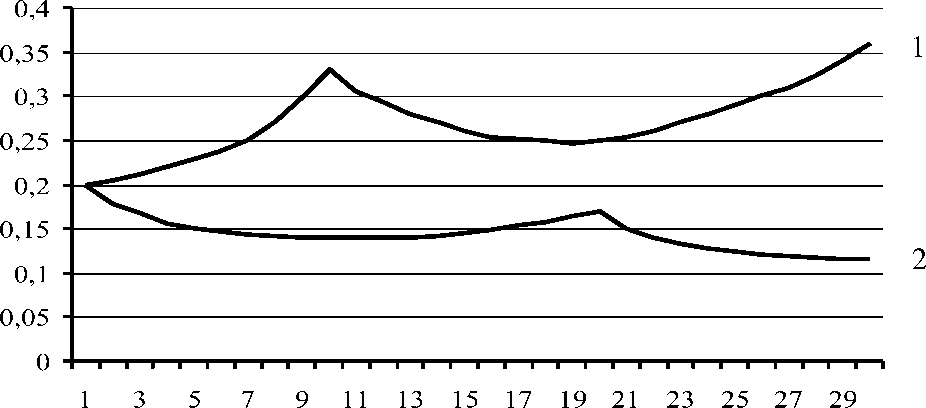
Fig 2: The DCS nodes rating with the dynamically changed index of the information value
In the first case (the dependance 1) on the first interval the trust level to the node is increasing, on the second -- is decreasing and on the third interval is increasing again, that is determined by two factors:
-
• the number of security incidents associated with the node (respectively, on the first and third interval the number of incidents is less than the critical level, on the second is above of it)
-
• the dynamics of the processed information value.
With the increasing of the trust level also there is increased the degree of the information value, which can be sent to this node for processing, that, in turn, in accordance with (1), further increases the trust level to the node. In the case if the node is initiated the security incidents, the trust level to it is reduced and therefore this node will receive the information with a lower value, down to the open information only. In general, the dependence 1 shows the general trend of the DCS node rating increasing, thus it should be noted that the node rating is changed gradually (continuously), but not as the jump at the end of the observation interval.
The dependence 2 is described the second case, when due to a large number of security incidents from the node the trust level to it is reduced, however, as in the previous case, on the certain observation intervals there is some local increasing of the trust level.
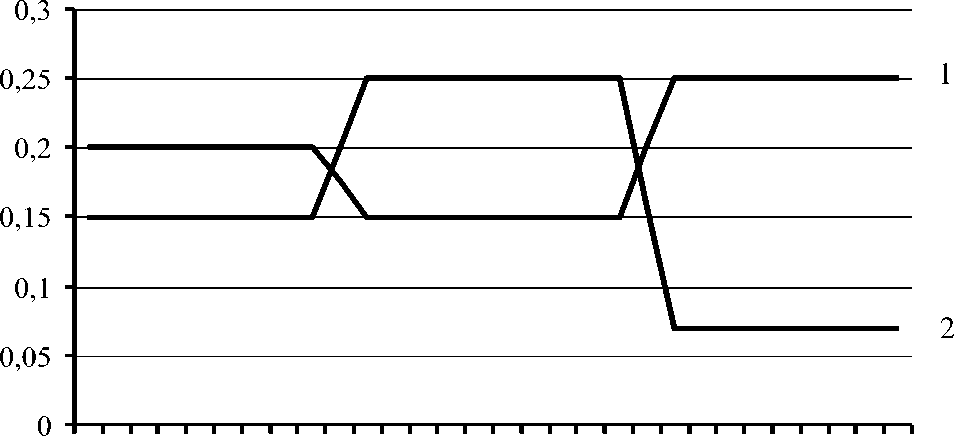
Fig. 3 shows the variants of nodes rating changing in case, when the number of security incidents on the corresponded observation intervals (tk, tl) is the same as in the first and second cases discussed above, but the index of the processed information value is constant. In fact, this situation is typical when the differentiation of information by its value is not performed.
As it shows Fig. 3, in this case the main trend of the DCS node trust level changing remains the same as in the case of dynamic changes of the information value, but the index of the trust level is varying discretely (discontinuously) at the end of the observation interval, so, it does not provide the in-time adaptation to current safety requirements to DCS.
It should be noted, that in general the DCS combines a big number of nodes and, as a consequence, the centralized forming of the trust level to the each nodes in the system is rather time-consuming task, requiring the considerable time. The trust management architecture used in the XenoServer Open Platform - XenoTrust system solves this problem by limiting the number of nodes, which send the information to change the trust level. However, in this case it is necessary to define the correct criteria for the nodes selection, which will be send information on the trust level, and to perform continuous monitoring of the received data from this node, because if the node trust level is low, the data are used to modify the trust level can be unreliable.
1 3 5 7 9 11 13 15 17 19 21 23 25 27 29
Fig 3: The rating of DCS nodes with the constant index of the information value
To solve this problem, we propose the next approach. In general, the DCS structure contains the several domains within which the nodes are located in a limited area, and are related to the the united organizational structure, so they are forming the mutual trust level based on the functioning within its local domain.
To improve the correctness of the trust level establishment procedure and to reduce the needed time for it there is sugessted to perform the average rating assessment, taking into account the mutual trust level between the nodes within the local domain. To implement this approach we propose to introduce the server with trust metrics, which, depending on the current trust level to the DCS nodes, generates the complex assessment of the nodes trust level. So, the complex trust level Tncx i to the DCS node is:
n
Tnsi + 2 Tnji * Tns,
Tncx i =------------ j =4----------- (3)
n +1
where Tns i - the trust level to the i -th node on the server with trust metrics, Tn ji – trust level of the j - th node to the i -th node (mutual trust), n – the number of nodes in the system.
Initially, the trust level for the i -th node on the server with trust metrics is set to an initial value Tns0i, although, if necessary, for the certain nodes there the different from the initial Tns0i trust level can be set. Further, according to the results of the node functioning in the DCS structure as part of its domain, with (1) we receive the trust levels Tnsi and Tn j i , and then we form the complex trust level Tncx i .
To correct the trust level in a new added node with the initial trust level Tncurr0 we proposed to launch the so-called test parcels, i.e. to generate data that imitatite the information with a high index values, then transfer it to the node, and to analyse the node reaction to it. In case if the node will perform the unauthorized actions to these data, the trust level to it will be decreased. Such adjustments are particularly relevant in those cases, when all the DCS nodes are processed of the confidential information and there is the critical trust level, which can not be reduced during the information processing.
-
III. The method for the dcs nodes rating
ESTABLISHMENT CONSIDERING THE DYNAMICS OF THE INFORMATION VALUE CHANGING
Let us formulate the suggested method for the DCS nodes rating establishment considering the dynamics of the information value changing.
-
1. To perform the ranking of information by its value, then to form a functional dependence of the information value C(t) in time. To each information unit (data, tasks, etc.) is assigned the appropriate level of its value.
-
2. To calculate with (1) the trust level to the nodes from the server with trust metrics (Tnsi) and the mutual trust level between the nodes within the local domain (Tnji).
-
3. To calculate the current rating Tncxi of the DCS nodes with (3).
-
4. To correct the trust level to the new added nodes with the special test mechanism.
-
5. To perform the test of the possibility to send the information to the certain node before launch any transactions by comparing the current complex trust level Tncxi to this node and the required critical trust level Tnmin, that is defined by the safety administrator. The transaction is permitted in the case only if the current trust level to the node is greater than or equal to the required trust level (Tncxi ≥ Tnmin).
The suggested method for the DCS nodes rating establishment allows adaptively and during the system functioning to determine the most secured configuration of resources (nodes) for the information processing taking into account the dynamics of the information value changing, so the method allows to improve the effectiveness of the security systems in DCS. The implementation of security mechanisms, based on the proposed method allows to reach the sufficient level of security for the system, even in case when the new node is added during the scaling of the distributed system, what is especially important in the real practice.
-
IV. The implementation of the security
MECHANISMS FOR THE DCS BASED ON THE TRUST LEVEL ESTABLISHMENT
In accordance with the recommendations of the OGF, the security mechanims are implemented in the DCS as the additional tools to the already existing hardware and software mechanisms which support the distributed computing [12-16]. To implement the proposed method for the DCS nodes rating establishment we suggest the special structure of the safety mechanism, which includes the tools for the evaluation and analysis of the trust level to the nodes (Fig. 4). This structure is consistent with the basic requirements of OGF to the DCS security mechanisms: there are present the mechanisms for the network security, authorization and authentication, for the security of the transmitted messages, and it may be expanded to include additional mechanisms [17-19].
All the security mechanisms form an united system, but each mechanism is independent from the others. The one of the most important components is the security monitoring service, which also takes part in the formation of the trust level to the nodes. This service includes the tracking subsystem, affecting on the nodes trust level. Also, this service performs the monitoring of the all critical events in the DCS. In particular, it monitors the processes of the identification, authentication and the access authorization to the DCS resources [17-19].
The generated values of the nodes rating are transmitted to the service of the subjects access control, based on the trust level, that allows to establish a secure configuration of resources (nodes) for the information processing in DCS taking into account the dynamics of the information value changing. Also, the proposed structure includes several standard services that support the distributed computing environment, in particular, the protocol for data protection.
-
V. Conclusion
We suggest a method of the trust level establishment to the DCS nodes taken into account the dynamics of the information value changing and with the in-time records of the security incidents from the nodes. It is shown that the proposed method of the DCS nodes rating establishment allows adaptively and during the DCS functioning to determine a safety configuration of resources (nodes) for the information processing in the DCS, which improve the effectiveness of the security system. The implementation of the suggested method allows to support the required security level system for the DCS in case of the new nodes adding during the scaling of the distributed system.
Also, there is described the specifics of the implementation of the mechanisms for the nodes trust level establishment. It is shown that the suggested mechanisms are compliane with the main requirements for the security system for the DCS, and are expandable to include additional mechanisms.
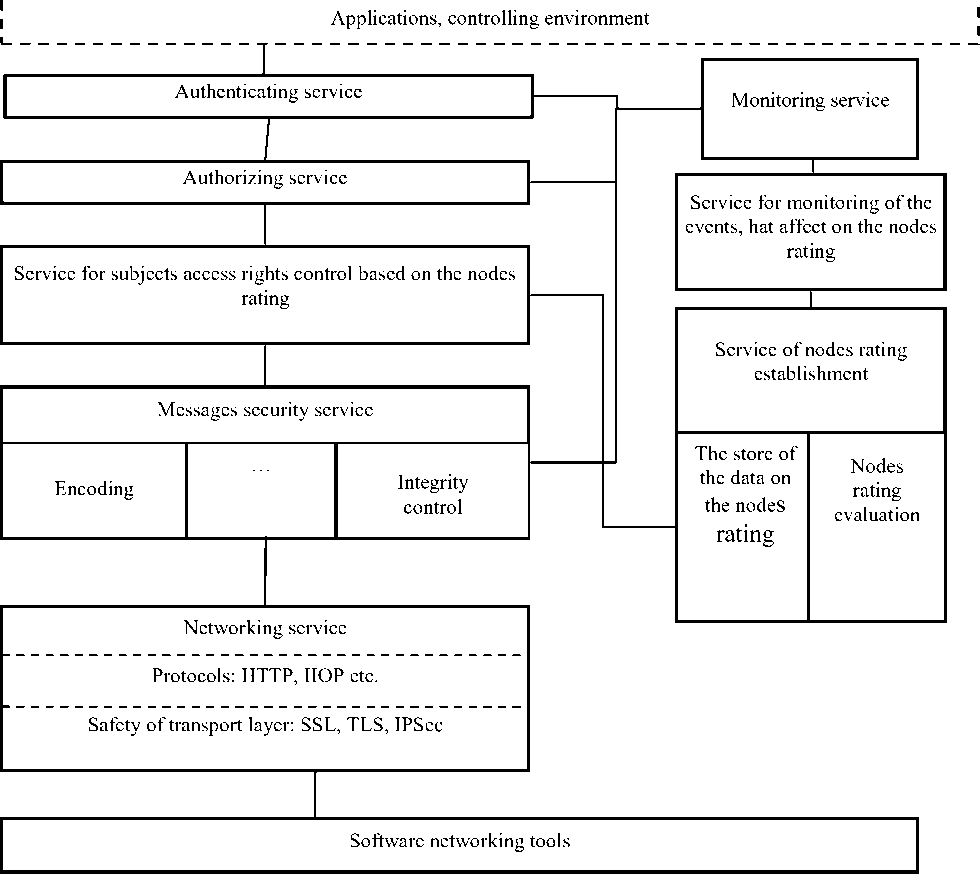
Fig. 4: Structure of the security mechanisms for DCS based on the nodes rating establishment
Список литературы The Rating Mechanism for the Trusted Relationship Establishment for the Security of the Distributed Computer Systems
- Nagaratnam N., Janson P., Dayka J., Nadalin A., Siebenlist F., Welch V., Foster I., Tuecke S.: The Security Architecture for Open Grid Services. Publisher: Global Grid Forum, http://www.scribd.com/doc/45082834/The-Security-Architecture-for-Open-Grid-Services. - 31 p.
- Mukhin V.Ye., Volokyta A.N. Integrated Safety Mechanisms Based on Security Risks Minimization for the Distributed Computer Systems. // International Journal of Computer Network and Information Security (IJCNIS), Volume 5, No. 2, February 2013. – pp. 21 – 28.
- Josang A., Ismail R., Boyd C.: A Survey of Trust and Reputation Systems for Online Service Provision // Decision Support Systems, 43(2), 2007. – p. 618-644.
- Grandison T., Sloman M. A survey of trust in Internet applications.// IEEE Communications Surveys, 3(4). – pp. 4-7, Oct.-Dec. 2000.
- Imamura T., Dillaway B., Simon E. XML encryption syntax and processing. W3C Recommendation, 2002. http://www.w3.org/TR/xmlenc-core.
- Gasser M., McDemott E. An architecture for practical delegation in a distributed system. // Proc. of IEEE Symposium on Research in Security and Privacy, IEEE Computer Society Press, Los Alamitos, CA, 1990.- pp. 20-30.
- Howell J., Kotz D. End-to-end authorization.// Proc. of 2000 Symposium on Operating Systems Design and Implementation. USENIX Association, 2000.
- Azzedin F., Maheswaran M. Integrating Trust into Grid Resource Mana-gement Systems // Proc. of First IEEE International Workshop on Security and Grid Computing, 2002.
- Luke T.W.T., Jennings N.R., Rogers, Luck M.: A Hierarchical Bayesian Trust Model based on Reputation and Group Behaviour // 6th European Workshop on Multi-Agent Systems, 18th-19th December, 2008, Bath, UK.
- Arenas A.E., Aziz B., Silaghi G.C.: Reputation Management in Grid-Based Virtual Organisations // Proc. International Conference on Security and Cryptography (SECRYPT 2008), Porto, Portugal, 26-29 Jul 2008, INSTICC.
- Kerschbaum F., et al: A trust-based reputation service for virtual organization formation. In Proceedings of the 4th International Conference on Trust Management, vol. 39(86) of Lecture Notes in Computer Science, pp. 193–205. Springer, 2006.
- Chakrabarti A.: Grid Computing Security. // International Workshop "Advanced Com-puting and Communications (ADCOM)", Ahmedabad, INDIA, December 2004. - 12 p.
- Adams C., Lloyd S. Understanding PKI. Concepts, Standards and Deploy-ment Consideration. Second Edition. Addison-Wesley, 2003.
- Abdul-Rahman A., Hailes S. Supporting trust in virtual communities// Proc. of the IEEE 33rd Hawaii Int. Conf. on System Sciences (HICSS '00), vol.6, 2000. - p. 607.
- Arenas A., Aziz B., Silaghi G.C. Reputation management in Grid-based virtual organizations. // Proc. of Intern. Conf. on Security and Cryptography (SECRYPT 2008), Porto, Portugal, 2008. - pp. 538-545.
- Kamvar S. D., Schlosser M. T., Garcia-Molina H. The eigentrust algo-rithm for reputation management in P2P networks //Proc. of the 12th international conference on World Wide Web, New York. NY: CM Press, 2003.
- Teo Y.M., Wang X.B.: ALiCE: A Scalable Runtime Infrastructure for High Performan-ce Grid Computing. // Proceedings of IFIP International Conference on Network and Parallel Computing, Springer Verlag, Wuhan, China, October 18-20, 2004. - pp. 101-109.
- McKnight D.H., Chervany N.L. The Meaning of Trust. Technical Report MISRC Working Paper Series 96-04. University of Minnesota. Management Information Systems Research Center, 1996.
- Luke T.W.T., Jennings N.R., Rogers A., Luck M. A Hierarchical Bayesian Trusl Model based on Repulalion and Group Behaviour // Proc. of 6th European Workshop on Multi-Agenl Systems, Bath. UK, 2008.


