Virtual Examination Supervision System for Nigerian Universities
Автор: Akazue Maureen I., Ajenaghughrure Ighoyota Ben.
Журнал: International Journal of Modern Education and Computer Science (IJMECS) @ijmecs
Статья в выпуске: 9 vol.8, 2016 года.
Бесплатный доступ
Examination malpractice is a dishonest conduct by a candidate prior to examination and through the examination to attain success effortlessly. Examination malpractice is a plague that heralds severe menace for the nation and has constantly remained a bother in the Nigerian educational system. Supervising examination has been manual since the inception of examinations in Delta State University. Likewise, most of the State Universities and Federal Universities in Nigeria utilize manual supervision of examination though visit by examination supervisors. Thus, this research paper presents a virtual examination supervision system (VESS) that checks candidates who are writing examination. VESS is an information technology approach towards curbing the problem of cheating in examination hall, using computer vision motion detection technique on real-time IP-camera video stream from examination. The implementation and practical experiment of VESS was carried out in Delta State University and result analysis indicated shift in position by examinees during examination at every milliseconds, which is difficult for human eye to monitor accurately and other cases such as copying and impersonation. These further proved that VESS is a solution to mitigating examination malpractice of all kinds and protection of the invigilators. Furthermore, the stored result in VESS can be used as evidence to punish the culprit.
Examination, malpractice, virtual, IP-camera, Computer, Supervision
Короткий адрес: https://sciup.org/15014902
IDR: 15014902
Текст научной статьи Virtual Examination Supervision System for Nigerian Universities
Published Online September 2016 in MECS
Examination is the true test of knowledge attained in any educational institution, but the approach that is being used to manage the security of this test of knowledge has made it relatively uncertain that examination is a true test of knowledge [1]. Such examination gives, with sufficient details, a clear analysis about the student’s progress in different areas of concentration [2].
Application of computer to the organization of examination is necessary since computer usage in the management of day-to-day activities of individuals and establishments is on the increase [3, 4]. Adopting the accuracy and efficiency offered by the computer to the invigilation of examination will yield a clean sheet [5]. Thus, it is possible to acquire the true test and analysis of a student skill in an unbiased situation [6].
Since the Nigeria university examination invigilation/supervision has so many flaws due to inadequate staff and breach on the security and privacy of supervisors/invigilators, it leaves a computer based supervision system as the only way forward toward ensuring full security of examinations in Nigerian Universities. Virtual examination supervision system (VESS) is the use of IP-surveillance for the security of examinations against all kinds of cheatings such as an examinee replicating another’s write-up, use of unacceptable materials (cell phone, piece of papers), and forming alliance with examination supervisors to cheat.
This research evaluated the inefficiency and ineffectiveness of manual method of examination supervision in most Nigeria Universities and developed a virtual examination supervision system (VESS) to compliment the manual examination supervision system. The designed model proved the act of a student copying from another student and a student talking to another student during examination as an act examination malpractice, with digital evidence before the institution’s disciplinary committee.
The entire research paper is divided into six sections. The first section was an introduction, while the second section presents an overview of related works and a highlight of the manual system shortcomings. The third section presents the VESS architecture and its components description, while the fourth and fifth section was a data analysis and reported cases of examination malpractices detected during the VESS implementation. In addition, the sixth section comprises a brief discussion, based on the analysis from the fourth and fifth section. Finally, the seventh section concludes the paper, based on findings during the VESS implementation
-
II. Related Works
Several researchers have been on the forefront of discovering information technology solution for mitigating and eventually eradicating the menace of examination malpractices [2, 6, 7, and 8].
In [9], the use of wireless camera for online examination supervision was proposed. This is part of continuing effort to tackle examination malpractices in computer-administered test environment especially in areas of candidate authentication and activities during examination. Furthermore,[10] designed a real-time video analysis system that has the capability to detect suspicious human activities such as peeping, entry and exit during examination. In addition, [11] developed a similar system, which was developed by [10] to detect suspicious activities of students in a classroom during examination.
The excessive human involvement in examination management is responsible for the prevalence of examination malpractices, as suggested by [12]. Hence motivating [12] into proposing the use of Automated test taking, marking, and result printing system, as a solution for expunging examination malpractices from Africa. In addition, [13] proposed the design and implementation of an online examination security system based on presence detection using passive infrared sensors. This lacks the capability of identifying individuals. Also, [14] Investigated examination cheating in online examination, using cameras and the result clearly indicated blatant cheating by examinees participating in online examination.
To prevent the use of online resources by online test takers, [15, 16] proposed the integration of firewall into online examination system for monitoring of candidates systems packet, to prevent cheating through the use internet resources to source for solution during examination. This system only identifies candidates by their username and password, which will not always be true for all cases, where a user may be using another personal computer that ideally is not his/her own. In addition, an unknown person having a user credential could impersonate.
Candidate authenticity was the focus of the study conducted in [17], which proposed an embedded zigbee based communication system for verification and authenticating candidates before, granted access into examination halls, to prevent malpractices, using biometric fingerprint and webcam. This system could only prevent impersonation, but cannot be useful in other cases.
Examination data security in online examinations was studied by [18], which Proposed and designed a secured web based online examination system using cryptography to ensure the integrity of examinees interaction with the server with their system. Furthermore, [19] discussed the imminence of the need to employ ICT for examination security and integrity assurance, citing the overwhelming responsibilities on academic faculties in India universities, as a major reason for the ineffectiveness of the existing manual examination supervision system.
Hence, this justifies the need for VESS as a solution for ensuring the integrity of Nigerian university education, through efficient security of examination.
-
A. Problems of Existing Systems
Information gathered from the existing system (Delta State University) showed that the system has the following flaws:
-
> Inability to archive examination incidence and
playback electronically
-
> Inability of the human eye to be fixed on a
particular direction over a long period.
-
> Exposing supervisors of examination to risk, such as threat to life, since offenders know the reporting supervisor.
-
> Prone to compromise, due to relationship between lecturers and students
-
> Ineffective motion detection (movement) during examination.
-
III. Vess Architecture
Fig1 is the VESS architecture. The camera serves as the input device while the network infrastructure serves as the medium of transportation for the collected and encoded data from the camera to the viewing center. The viewing center is an information technology powered center with high-speed network bandwidth connectivity to stream real-time video feeds from the cameras through the network. Although, the network infrastructure in this research is a wireless network which links both the viewing center and the wireless IP cameras together wirelessly. The viewing center equipped with motion detection software that logs detected motions video frames with timestamp. The technique of timestamp motion analysis of the monitoring software introduces intelligence. This prevents the need to watch through entire examination video. Rather, just scanning through each frame with detected motion event will be the sole task of monitoring personnel.
-
A. Components of VESS.
The components of VESS are classified into three major groups amongst which include;
-
> Network infrastructure includes wireless antennas and radios that connect wireless IP cameras in examination halls. In addition, it connects the cameras to examination monitoring center. This is denoted by the mast structure in Fig1. Also included in the network infrastructures’ are the switch, router and network gateway modem are included in this group. These components of the network infrastructure provide modulation, demodulation and connectivity for data transfer at each layer of the system network infrastructure.
-
> Examination venue infrastructure includes the surveillance cameras, connection cables in cases of non-wireless cameras and power supply adapters that provide power supply to cameras placed in examination halls/centers. In addition,
the examinees participating in the examination is included.
-
> Examination monitoring center infrastructure includes components such as storage servers, intelligent video analysis software systems, and personal computers used by monitoring.
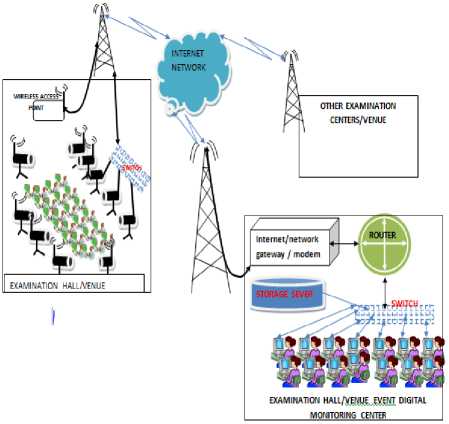
Fig.1. VESS Architecture
-
IV. Data Analysis
Delta State University used as a case study, currently runs a manual examination supervision method for all degree and entrance examinations. This method manages examination malpractice cases (both treated and awaiting cases) reported manually (pen and paper). In addition, evidence of reported cases and collection of examination malpractices cases are manual. Hence, students know the identity of examination malpractice task-force personnel reporting malpractice cases, and disciplinary committee members. This jeopardizes their safety and privacy. In addition, possibility of missing evidence and compromise are clear, due to the manual case collection, evidence storage, and reporting method. Therefore, this research combines motion detection on real-time IP-camera camera network to provide an ICT based solution for the impeding examination malpractice problem in Nigeria Universities. During the implementation of the research, data collected and analyzed using motion detected in video frames with time stamp.
-
A. Motions Detected
The archived video feeds from the cameras were analyzed using intelligent video analysis software known as ZP-player. The ZP-player received the video streams and analyze them base on motion detected using three parameters, which are the time of motion occurrence, the frame where motion was detected and a unique arbitrary value for identifying the frame.
The Table1 shows the analysis of time of occurrence, frame of occurrence of motion and the value of the motion detected for CSC417, MTH318 and MCB 312 examination analysis.
Table 1. Analysis of archived video from VESS implementation using the ZP-player
|
TIME |
FRAME |
VALUE |
|
00:00:00 |
27 |
50.0 |
|
00:00:02 |
80 |
74.0 |
|
00:0004 |
136 |
52.0 |
|
00:0006 |
205 |
52.0 |
|
00:00:08 |
257 |
70.0 |
|
00:0010 |
313 |
55.0 |
|
00:00:13 |
392 |
50 |
|
00:00:14 |
443 |
65.0 |
|
00:00:30 |
922 |
50.0 |
|
00:00:32 |
974 |
53.0 |
|
00:00:34 |
1032 |
67.0 |
|
00:00:36 |
1084 |
56.0 |
|
00:00:37 |
1139 |
55.0 |
|
00:00:45 |
1370 |
64 |
|
00..:0..0.:.50 |
.1.5..18.. |
.5. 3...0.. |
|
00:0052 |
1580 |
64.0 |
|
00:00:54 |
1640 |
126.0 |
|
00:00:56 |
1697 |
81.0 |
|
00:00:58 |
1750 |
86.0 |
|
00:01:00 |
1802 |
53.0 |
|
00:01:02 |
1883 |
72.0 |
|
00:01:04 |
1934 |
52 |
|
00:01:06 |
1985 |
64 |
|
00:01:08 |
2042 |
92.0 |
|
00:01:10 |
2124 |
63 |
|
00:01:12 |
2183 |
111.0 |
|
00:01:14 |
2240 |
108.0 |
|
00:01:16 |
2295 |
158.0 |
|
00..:0..1.:.30 |
.2.7..77.. |
.5. 6...0.. |
|
00:01:32 |
2866 |
70.0 |
|
00:01:34 |
2923 |
156 |
|
00:01:36 |
2986 |
130.0 |
|
00:01:37 |
3044 |
67.0 |
|
00:01:39 |
3097 |
55.0 |
|
00:01:53 |
3760 |
81.0 |
|
00:01:55 |
3812 |
69.0 |
|
00:01:57 |
3866 |
51.0 |
|
00:02:00 |
3921 |
56.0 |
|
03..:2..1.:.56 |
3.6.3.4. 8..5 |
.5. 4...0.. |
Further analysis of motion detected in the Table1, is presented graphically in Fig 2. From which we can infer that there is change in position (motion) by examinees in every one seconds (1ms) to three (3ms) seconds during examination, which is highly undetectable by human eye easily. This validates the need for an eagle eye such as a security camera deployment for efficient and consistent monitoring of examinees behavior during examination.
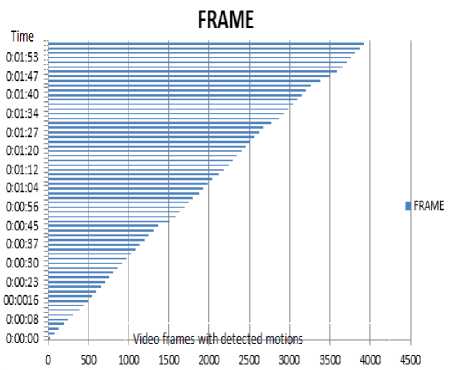
Fig.2. Graphical representation of motion detected during analysis
-
V. Cases Recorded
The cases recorded were copying from fellow students, moving from seat to another seat, talking/discussing during exam.
-
A. Results from scanned analysis of detected motions
From MCB318, Csc417 And MTH 318 examinations
During the scanning of MTH318 and CSC417 video frames with detected motions, as recorded table1 above, some of the following events were predominant as shown in Fig 3,4,5,6 and 7 respectively. Although copying was rampart in both examinations but only one case of impersonation was recorded in MTH318 examination. In addition, intentional copying was also predominant, for example, three students who sat together with the intention of copying from each other in order to pass the CSC417 examination undermining the presence of the examination supervisor, as shown in fig 3 and figure4. The impersonation case recorded, a hired impersonator was detected in the MTH318 examination, as well as copying from one another was not exempted. Finally, the MCB312 was another examination with massive intentional copying case recorded.
-
B. Copying
Copying was predominant during the VESS implementation due to the limitations of the manual examination supervision system. Such as the human eyes inability to focus on one direction for long time without blinking and clever students not copying word to word and thus, provide no tangible prove to that form of examination malpractice for disciplinary actions to be taken against the perpetrator at the disciplinary committee.

Fig.3. CSC417 Exam
The Fig3 shows three female friends who sat together with intention of copying from one another, undermining the sitting space arrangements employed by the manual system and was copying from each other. The same three students in CSC417 examination continued copying despite the presence invigilators in the examination hall, as depicted in fig.4. In addition, another two male students that sat together intentionally copied from each other in fig.3. The prevalence of copying in examination is owing to the fact that there is no substantial evidence to present before disciplinary committee.

Fig.4. CSC417 Exam
Furthermore, the same three friends continued to copy from one another until the end of the examination as shown in Fig5 without being caught by the invigilator or supervisor. This seriously undermines the quality and integrity of examination and educational values.

Fig.5. CSC417 Exam

Fig.6. MTH318 EXAM

Fig.8. MTH318 EXAM; the impersonator (guy) and his contractor (girl)
Similar to the copying in CSC417, a student is seen in Fig6 copying from another student in MTH318, undermining the supervisor behind him on blue shirt. The same student is seen in Fig7 raising his booklet for the girl behind him to copy.

Fig.7. MTH318 Exam

Fig.9. MTH318 Exam; the female student who hired an impersonator sitting idle, while her impersonator (boy) writes for her
Hence clearly reveals the weakness of the manual examination system capability to mitigate the menace of examination malpractice perpetuated by copying, and validating the deployment of VESS as a competent solution.
-
C. Impersonation
This is a purposeful act, where a person is hired by a student to come and seat for an examination for them to pass. Sometimes the hired person is more intelligent. During the VESS implementation, a case was recorded in MTH318 examination. The girl in the red circle hired the guy behind her to sit for the examination (see Fig8). She wrote only for a total of 15minutes and 45seconds in an examination that lasted for two hours 6minutes and 40 seconds. Thereafter, in Fig9, she folded her hands and was idle for about one hour (1Hr) forty minutes (40minutes), while the impersonator (boy) was writing for his contractor (girl). Latter, about seven minutes to the end of the examination (Fig10 to Fig12), she swapped her details with the guy on her question paper and waited for him to submit (Fig13), after which she submitted 3minutes latter.

Fig.10. MTH318 EXAM impersonator (boy) and his contractor (girl) prepares to swap details but involved the girl on the contractors seat to use her question paper for the contractor to write her details to the impersonator

Fig.11. MTH318 Exam; the contractor (girl) giving her details to her impersonator (boy)

Fig.12. MTH318 EXAM; impersonator (boy) gives his forged details to the contractor to enter into her own booklet

Fig.13. MTH318 EXAM’ impersonator (boy) summits his script while the contractor (girl) waits awhile
-
D. Movement from seat to seat (mth318)
Movement from one seat to another in attempt to copy from other students was also recorded, immediately after the impersonator had submitted in fig13. Unknowingly to the invigilator, another student moved from his seat to occupy the empty seat for assistance. He sat on the same row where the impersonator was originally seated as seen in Fig14.

Fig.14. MTH318 Exam; An examinee moving from seat to another seat to get assistance
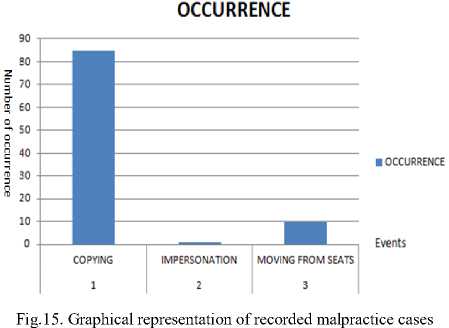
From the records in Table1 and Fig15, a summary table showing the numbers of recorded copying cases, impersonation cases, and seat change cases shown in Table2.
Table 2. Summary of recorded malpractice cases detected by VESS
|
S/N |
CASES |
OCCURRENCE |
|
1. |
Copying |
85 |
|
2. |
Impersonation |
1 |
|
3 |
Moving from seat |
3 |
-
VI. Discussion
Impersonation mostly caused where there are no familiarity between the students and their course level advisers and course lecturers. We can now infer that the manual examination supervision system requires familiarity between the students and lecturers in order to curtail the problem of impersonation. This is another flaw in the manual examination supervision system. Therefore, it will be advantageous if all level course advisers monitor their students during their examination as they could easily identify these impersonators and expunge them out of the hall to face panel.
Furthermore, since there will be no tangible evidence to persecute students who move about, they are warned and allowed to continue writing. Thus, VESS has contributed immensely to the prevalence of this form of examination malpractices.
-
VII. Conclussion
For the war against malpractices of all forms in Delta State University examinations to be won, there is need for an information technology approach towards curbing this menace while maintaining the security and privacy of all examination supervisors. The VESS is capable of mitigating over 90% of examination malpractices from Nigeria University examination system when implemented. Although, we continue further research into development of more intelligent video analytic computer vision system that automatically log and record each case of malpractices into an event database, to avoid the need for manual scanning of video frames with detected motion in future, for a more robust system with more coverage. It is therefore suggested that a digitalized examination surveillance system that keeps archive of tangible evidence for prosecuting perpetrators of this form of examination malpractice should be deployment.
Список литературы Virtual Examination Supervision System for Nigerian Universities
- Balongun E. A., (1995) "Negative impact of examination malpractices in Nigeria tertiary institution", Ahmadu Bello University, Zaria.
- Fagbemi, M.0.(1995) "Examination ma/practices in tertiary institutions: Ondo State College of Education", Ikere- Ekiti experience. A paper presented at the in-house Seminar on examination malpractices held at the Ondo State College of Education, Ikere-Ekiti (pp 26-27,).
- Amar E., Mohini S., "Importance of Information Technology in examination security", University of New Delhi, India. . (2009).
- Atabom S. "Effect of examination malpractice on nation building." University of Uyo, Uyo; Nigeria. (2008).
- Xingbao Li, Yunming Wu,( 2007) Design and Development of Online Examination and Evaluation System based on B/ S Structure, Proceedings of International Conference on Wireless Communications, Networking and Mobile Computing, IEEE,,PP 6223-6225
- Ojerinde, E. A "Overcoming examination malpractice challenges in the joint admission and matriculation board examination" available: www.vanguard.org.ng/News/jamb/malpracticesummit (retrieved 12th Dec. 2013)
- Ojikutu, D.E. (1987)"Administration of examination in Nigeria: Problems and solutions in University system – OAU experiment". A paper delivered at the WAEC monthly Seminar, University of Lagos, Lagos.
- Olaseinde - Williams, 0. "The need for instituting academic integrity climate in Nigerian Universities: A psychological perspective. (2004)" A paper presented at the 7th National Conference of National Association for Educational Researchers and Evaluators.
- Suman, M.C., Prathyusha, K. Wireless Camera based Online Examination Security, International Journal of Engineering Research and Applications (IJERA) Vol. 2, Issue 2, pp.1432-1435, 2012.
- Gowsikhaa D., Manjunath, Abirami S., Suspicious Human Activity Detection from Surveillance Videos (IJIDCS) International Journal on Internet and Distributed Computing Systems. Vol. 2, Issue 2, pp141-148, 2012.
- Sandhya Devi G., Prasad Reddy, Suvarna Kumar, Vijaya Chitnaya, Multiple View Surveillance using Image Registration, International Journal of Computer Applications , Vol. 93, Issue 2, pp 0975 – 8887, 2014.
- Atabong T. A. , Okpala M. C., Abondem A. L. and Essombe C. E., Eliminating Examination Malpractice in Africa with Automated Test Taking, Marking and Result Printing, Tropical Journal Of Biomedical And Allied Sciences Research Vol. 4, Issue1, pp452-469, 2010.
- Benilda E. V. Comendador, Dan Emille S. Molenilla, Glenn C. Sabales, Gabriel Angelo G. Suazo, and Jake R. Capangpangan Asynchronous Online Examination Security System Using Occupancy Detection Journal of Automation and Control Engineering Vol. 3, Issue 2, pp 141-145, April 2015.
- Simon, (2005) "Blatant cheating detected in an online examination, Educational integrity : values in teaching, learning and research: 2nd Asia-Pacific Educational Integrity Conference, University of Newcastle, Australia 2006 (ISBN: 1920701680)
- V.Selvi, R.Sankar, R.Umarani, The Design and Implementation of On-Line Examination Using Firewall security, IOSR Journal of Computer Engineering (IOSR-JCE), Vol.16, Issue 6, PP 20-24, 2014.
- N.Sendhil Kumar, Agarapu Raghavendra, Secure Online Examination Management System Using Firewall Settings SSRG International Journal of Computer Science and Engineering (SSRG-IJCSE), Vol. 2, issue 5, PP185-191, 2015.
- Babu Anumolu, N.Bharadwaj, An Online Examination System Using Wireless Security Application 1Madhu International Journal of Engineering Trends and Technology (IJETT) Vol. 4, Issue 9, pp 3885-3887, 2013.
- R. Sheshadri, T.Chalama Reddy and N.Ashok kumar, Web-Based-Secure Online Nonchoice –Based Examination System (WONES) using Cryptography,International Journal on Computer Science and Engineering (IJCSE) Vol. 3, Issue 10, PP3383-3393, 2011.
- Mohini Bhardwaja and Amar Jeet Singh Automated Integrated Examination System: A Security Concern, Information Security Journal: A Global Perspective, Vol. 20, Issue 3, pp 156-162, 2011.
- Adegboye, 0. Outoye, & J.0. Adetunberu (Eds.), "Issues on examination ma/practices in Nigeria: A book of readings" Ikere Ekiti: Ondo State College of Education, Ikere Ekliti, (pp. 195-201).
- Asagba, P. O. (2012) Software engineering lecture note, Department of Mathematics and computer science, Delta State Univerity Abraka. (pp 21-43).
- Chiemeke (2010) "System analysis and design", University of Benin, Benin city, Nigeria.
- Ekanem, B. (2005) "The rudiment of Information Technology, equipped for relevance in a global village", Essinet printing and publishing, Uyo, Nigeria.
- Ojobaro, A. (2012). "IP surveillance security system design and implementation training guide", Kitts Tech. Press, Lagos, Nigeria.
- Olaseinde, A.O. "Cheating in examinations in the University of Ilorin: Styles, causes and remedies. Nigerian Journal of Educational Foundations, Vol. 4, Issue 1, pp56-61, 1993
- Olumero, S.O. Crisis of examination misconduct in Nigeria secondary and tertiary institutions: Typologies, techniques and students collaborators. A paper presented at the National Workshop on Examination Malpractice held at the University of Benin, Benin-city. 1992.


