Wi-Fi Networks Security and Accessing Control
Автор: Tarek S. Sobh
Журнал: International Journal of Computer Network and Information Security(IJCNIS) @ijcnis
Статья в выпуске: 7 vol.5, 2013 года.
Бесплатный доступ
As wireless networks access gains popularity in corporate, private and personal networks, the nature of wireless networks opens up new possibilities for network attacks. This paper negotiating Wi-Fi security against scanning of rogue Wi-Fi networks and other related activities and considers the monitoring of Wi-Fi traffic effects. The unauthorized access point (AP) problem has raised more attention and resulted in obtaining wireless access without subscriber permission. This work assumes Wi-Fi AP under attack specially rogue AP and/or ad-hoc client. It provides a solution for detecting and preventing this attack. In addition, it provides the required user permissions to allow/block access of the files on the user of ad-hoc client. The experiments include the rogue AP attack are maintained and the effectiveness of the proposed solution are tested.
Mobile Internet Devices, WLAN Networks, Rogue Access Point, Wi-Fi 802.11
Короткий адрес: https://sciup.org/15011205
IDR: 15011205
Текст научной статьи Wi-Fi Networks Security and Accessing Control
Published Online June 2013 in MECS
and AP know the rules and appropriate responses for a successful authentication. The most popular EAP types are LEAP, PEAP, TTLS, and Cisco’s FAST [www. ] [23]. Each of these authentication methods has their own unique strengths and considerations, and choosing the correct method for underlying network can be one of the most important steps of the security design process [www. ]. Fig. 4 presents RADIUS mediated Authentication Process using EAP.
Table 3: EAP authentication types []
|
EAP Type |
Client Certificate? |
2 Way Authentication |
Susceptible to Dictionary Attack? |
|
MD5 |
Password |
No |
Yes |
|
LEAP |
Password |
Yes |
Yes |
|
TLS |
Yes |
Yes |
No |
|
PEAP |
No |
Yes |
No |
|
TTLS |
No |
Yes |
No |
|
FAST |
No |
Yes |
No |
MD5 – This is the weakest of the possible EAP methods and typically should not be employed in a WLAN inasmuch as it provides negligible benefits over WEP.
LEAP – It provides an easy way to get 2-way authentication without using certificates. The weakness is that it requires users to remember a user password, and is thus susceptible to dictionary attacks.
TLS – It provides a very secure solution, but requires the use of certificates on the client.
PEAP– It is very secure solution. Uses TLS to create a secure tunnel where a second authentication mechanism can be used. Does not require a
TTLS –
FAST –
certificate on the client, but will use a certificate on the server.
It is very secure solution. It is very similar to PEAP; it uses TLS to create a tunnel to avoid using certificates on the client.
It is very secure. Creates a secure tunnel, then uses AAA server to authenticate the server and client.
-
III. Rogue Problem
The problem of rogue APs has garnered more attention than any other security issue. A rogue AP defined as any AP in your network that was not intentionally deployed by your network staff (see Fig. 5). Rogue AP may be well-meaning employees who bring in devices from home, they can be devices used by hackers, or they can be neighboring devices that simply overlap with your WLAN. These devices can have many effects and none of them is good in terms of network security. In short, a rogue device is any untrusted or unknown device running in your WLAN.
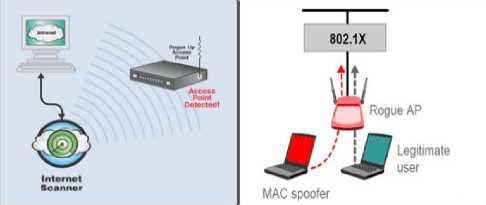
Figure 5: Unsecured Rogue Access Point Allows Anyone to Connect to the Network [17]
The well-known scenario of rogue AP is to plug it into a wired switch port and now rogue AP has wireless access to the larger wired network. Unfortunately, so does any Wi-Fi device within range of the AP including the wireless lurker in the parking lot. This provides a chance of unauthorized access to the entire enterprise network. An attacker could avoid organization security policy by planting a rogue device inside the building.
In such mobile environment, it is hard to trust any device completely. A wireless mobile device beaming signals into your network be either a harmless neighbor AP or an attacker-operated device trying to steal proprietary information from your WLAN [7, 9, 25]. Moreover, a poorly configured AP or a client can either open up access to outsiders or get associated with attacker. Fig. 6 illustrates some scenarios rogues AP attacks.
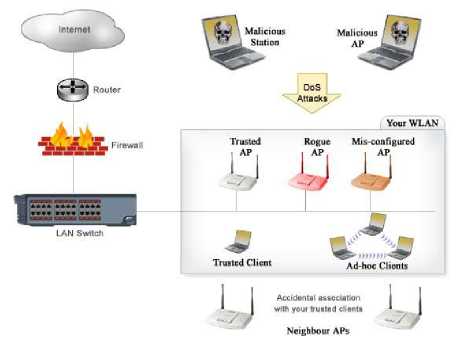
Figure 6: Malicious Rogue Devices and Associated Threats [25]
Though the term rogue is often referred to devices that are external to an organization, for clarity, in this work the term may refer to any unauthorized device irrespective of its real intent. The rogue threats are listed as follows:
-
3.1 Employee installed unauthorized Access Points
-
3.2 Misconfigured Access Points
-
3.3 Attacker Access Points
-
802.11 clients automatically choose the best available AP nearby and connect with them. Currently, Windows platforms connect automatically to the best connection possible in the vicinity. Due to this behavior, authorized clients of one organization can connect to Access points from the neighboring organization. Though the neighbors APs have not intentionally lured the client, these associations can expose sensitive data [27].
-
3.4 Unauthorized Access Points
Driven by the convenience of wireless home networking some employees plug grade access points to corporate LAN [26]. The cheap AP may not follow enterprise standard deployment procedures thus compromising security on the WLAN and wired network.
Users and visitors inside organization building (Wi-Fi network) and hackers outside organization building can connect to such unauthorized APs to steal network traffic, send objectionable content to others, retrieve private data, attack company assets, or use organization network to attack others.
Sometimes an authorized AP accidently turns into a rogue device due to configuration flaw [17]. Change in SSID, authentication settings, encryption settings etc., should be taken seriously as they could enable unauthorized associations if not configured properly. For example, in open mode authentication any wireless client device in state of unauthenticated and unassociated can send authentication requests to an AP and on successful authentication would move to state of authenticated but unassociated. If an AP does not validate the client properly, an attacker can send lot of such authentication requests, overflow the AP client access list, and make it reject access to other clients.
Ad-hoc devices are wireless clients that can communicate among themselves without requiring a
LAN bridging device such as Access Point [17]. Though such devices can essentially share data among themselves, they pose significant threat to the enterprise as they lack the necessary security measures such as 802.1x user authentication and the dynamic key encryption. As a result, ad-hoc networks risk-exposing data in the air. In addition, weak authentication may allow unauthorized devices to associate. If the ad-hoc mode clients are also connected to the wired network, the entire enterprise wired network is at risk.
WLANs are also becoming targets of a variety of attacks. One of the ways in which a WLAN can be attacked is by introducing one or more unauthorized fake Access Points (APs) in the network []. Unauthorized AP can be set up by a malicious attacker to masquerade as an authorized AP by spoofing the authorized AP’s MAC address.
Organizations can set security policies on what constitutes an authorized AP. The basic security policy depends on MAC addressed filtering. Organizations can pre-configure the list of authorized wireless devices [17, 27]. MAC and identification of any other device outside the MAC list will signify the presence of a rogue device. Also, if an organization standardizes on specific vendor APs then AP from any other vendor can be deemed rogue [23]. Similarly, enterprises can set various policies including SSID, Radio Media Type, and Channel. Whenever a new access point is discovered in the network that falls outside the pre configured authorized LIST, it can be assumed a rogue AP, as we will see in the proposed model.
-
3.5 Attacker operated Access Points
WLANs are prone to numerous attacks especially with freely available attacking tools. Attackers can install APs with the same ESSID as the authorized AP. Clients receiving stronger signal from the attacker operated AP would then attract legitimate clients to associate with it and launch a man-in-the-middle attack.
Table 4 presents a summary of the types of rogue APs and a number of possible scenarios [28].
Table 4: Rogue AP Taxonomy and Scenarios [28]
|
Rogue AP Class |
Possible Scenarios |
|
1. Improperly configured |
Insufficient security knowledge; Faulty driver; Physically defective; Multiple network cards |
|
2. Unauthorized |
Connected to internal LAN without permission; External neighborhood AP |
|
3. Phishing |
Fabricated by adversary |
|
4. Compromised |
Disclosure of security credentials |
-
IV. Related Works
Rogue AP security threats for corporate Wi-Fi networks are critical; detecting such rogue APs is one of the most important tasks of network security staff. Traditional rogue AP detection relies on network enumeration tools such as NetStumbler running on computer (laptop or other mobile device). This auditing approach is both time-consuming, unreliable and fails when a rogue AP is spoofed such as the MAC address and SSID of a legitimate AP.
Two online rogue AP detection algorithms are proposed in [29]. The basic idea of these two algorithms is the sequential hypothesis tests applied to packet-header data that are passively collected at a monitoring point. Algorithms use the properties of the 802.11 CSMA/CA and the half duplex of wireless channels to distinguish between wired and wireless connection. Once TCP ACKpairs are observed, prompt decisions are made with little computation and storage overhead.
A layer-3 rogue AP detection approach is proposed by Yin et al. [27]. It uses the both verifier and sniffers. A verifier is employed on the internal wired LAN to send test traffic towards wireless edge. If sniffers capture an AP relaying from the test packets, the AP is marked as rogue. In addition, binary hypothesis testing is used to improve the detection rogue AP.
Several commercial products have been developed to help automate scanning process and continuous monitoring. The main product in the market today is AirDefense [] and provides an IDS capability specifically for the Wi-Fi environment using an integrated system of sensors and a management console. It uses a combination of radio frequency sensors and an intrusion detection/protection server appliance to capture, process, and correlate network events. Also, AirDefense [www. ] stated that Security conscious enterprises are fortifying their wireless LANs with a layered approach to security that closely resembles the accepted security practices of wired networks. This layered approach addresses all network components by locking down the wireless LAN’s perimeter, security communication across the wireless LAN and monitoring network traffic. It provides the industry’s only enterprise level security appliance for wireless LANs to discover wireless LAN vulnerabilities, enforce security policies and detect then respond to intruders. It uses a distributed architecture of remote sensors and centralized server appliance to constantly monitor all wireless activity in real time allowing enterprises to control the wireless air space and define and enforce policy compliance [30]. Using it organizations can set policies for how all wireless LAN devices should be configured and then monitor all WLAN devices to identify when any device deviates from that policy.
Other products can provide the IDS portion incorporated in their Wireless network management tools like the ones provided by Air-Wave [] and AirMagnet []. Typically, these tools become network management tools that have the ability to provide: Wi-Fi security policy management, wireless intrusion detection, rogue AP detection, connection troubleshooting, trend analysis, reporting and capacity planning and may even assist in the site survey process.
-
V. The Proposed Model
-
5.1 Unauthorized AP Detection and Prevention
Detecting unauthorized access devices is the first step to efficiently defend your WLAN. Therefore, the solution to the issue such as rogue devices always begins with detection. Security staff needs to have complete visibility of all connected access points and clients in the network with deterministic rules that identify the devices that are authorized to be network member.
The proposed model consists of two basic sub models. First, sub model basic functions are WLAN detection and prevention of unauthorized AP. Second, sub model basic functions are protecting and preventing data leakage of ad hoc client's.
The more specific the wireless policy, the easier unauthorized access detection becomes. For example, if you know the MAC address of your devices, you can then easily identify rogues based on MAC address. In the same way, Rogues can also be identified based on other factors such as the hardware vendor, Channel, or SSID. All of this requires the ability to scan the airwaves and identify every device based on a variety of criteria, again illustrating the need for comprehensive wireless monitoring. As a closing note, it is important to think of rogue detection as part of the larger security policy and not the security policy itself. The response process of rogue device threat should ideally be broken to two steps: First step is suppression where the rogue device is immediately quarantined from the network. Second step is a removal where the rouge device is physically located by staff and potentially removed from the network.
WLAN unauthorized access detection and prevention is a continuous process. Fig. 7 presents the required process components. These components are:
-
1) Sensors are used to capture the wireless traffic and network behavior. Sensors we are used here RF scanning and AP scanning. RF scanning sensors will be quick to detect any wireless device operating in the area. However, the drawback of these sensors is the possibility of dead zones, which are not covered by the sensors. If unauthorized AP such as rogue AP finds its place in any of these dead zones, it will be unnoticed. AP scanning automatically discovers APs operating in the nearby area and exposes the data through its interface. Though it is a very useful, the ability of the AP to scan neighboring devices is limited to a very short range. Unauthorized APs operating outside this coverage area will go unnoticed.
-
2) A central monitoring and response engine to collect its inputs from available sensors.
-
3) A management component to identify the connection to unauthorized access according to authorized list database and take appropriate actions. The attack prevention here it means taking the appropriate action in order to avoid attacks such as blocking attack connection.
These actions are taken according to predefined organization policy and authorized access list as shown in Table 5. The objective from authorized access list is to find unique device characteristics that cannot be fabricated. Any newly detected AP that falls outside the authorized list would be flag as unauthorized or rogue AP. Management component use different authorized attributes values to populate the authorized list like SSID, MAC, BSSID, Media Type, Channel, and AP Vendor in addition to WLAN location used as comment attribute as shown in Table 5. Organizations would in most probably standardize on the authorized SSIDs and sometimes may want their APs to operate on select channels. The MAC you see in insider is the BSSID of the access point, a unique value per SSID that is being advertised by the AP. Generally for low cost access points that allow only a single SSID to be broadcast, it is common to see that the BSSID address is the Ethernet port +/- 1, i.e. 00-04-01-ad-cf-45 for Ethernet and 00-04-01-ad-cf-46 for BSSID. Sometimes we use certain standard on 802.11 a,b,g, or bg in our WLAN APs. This enables our toll to compare with our access list and to alert WLAN administrators whenever AP with different radio media type is detected.
Sometimes WLAN administrator wants his APs to operate on authorized select channels. This enables the proposed tool of our model to send alert whenever AP operating in a different authorized channel is detected.
These attribute values in Table 5 enable the proposed model to detection unauthorized AP and alert WLAN administrators whenever AP operating with a different value outside authorized list such as whenever AP operating in a different channel is detected. For example, when WLAN administrator staff detects rogue AP they can use the sensor to launch a network disassociation flooding attack of numerous packets against rogue AP. In addition, if the hacked AP linked to wired network a management component can identify the connected switch port and shutdown it. This would normally disconnect clients of the AP without dropping the connection and clients get associated to the nearest AP.
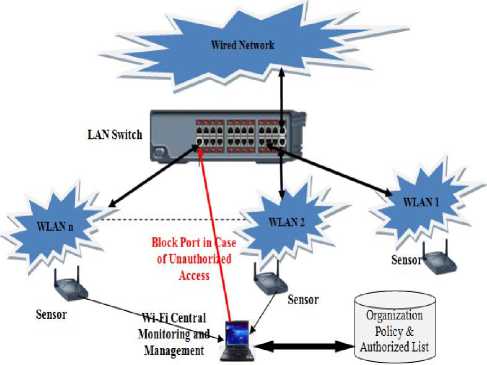
Figure 7: Wireless protection and prevention against unauthorized access
Authorized access list in Tables 5 shows AP of WLAN n not authorized due to unauthorized MAC then a management component will block its port in the LAN switch as shown in Fig. 7. However, today attackers can easily spoof MAC address and device driver characteristics are difficult to separate multiple devices with same device driver. Kohno et al. [30] used clock skew as a device fingerprint. In this work, we used clock skew too as a fingerprint to AP device in addition to attributes list in Table 5. We implemented clock skew like Jana et al. [31] did but the details of this part outside the scope of this paper (see [30, 31, 32]).
Table 5: Authorized Access List
|
SSID |
MAC |
BSSI D |
Type |
C h |
Vend er |
Locati on |
|
WLA N1 |
00230fc4 5b |
802.11b \g |
6 |
Proxi m |
Financ e Office Buldin g1 |
|
|
WLA N2 |
00230fc4 7b |
1 |
Cisco |
Accou nt Buldin g2 |
||
|
00230fc4 3b |
1 1 |
|||||
|
00230fc4 4b |
||||||
|
WLA Nn |
00230fc4 6c |
Mgr Office Buldin g3 |
-
5.2 Secure Wi-Fi Ad Hoc Client
-
5.2.1 Traffic Sniffer Module (TSM)
While the focus thus far has been on access points, the same principles also apply to clients. A rogue client could indicate an unknown user trying to get unauthorized access to the network. On the other hand, it could be an unconfigured employee device searching randomly for any available connection. In either case, it represents an issue that requires immediate attention from technical staff. Fig. 8 provides the proposed wireless protection of ad-hoc client against the unauthorized access attack and data leakage as well.
The proposed model in Fig. 8 is consists of four main modules, Traffic Sniffer Module (TSM), Ad-Hoc Client Manager Module (ACMM), Traffic Filter Module (TFM), and Traffic Analysis Module (TAM).
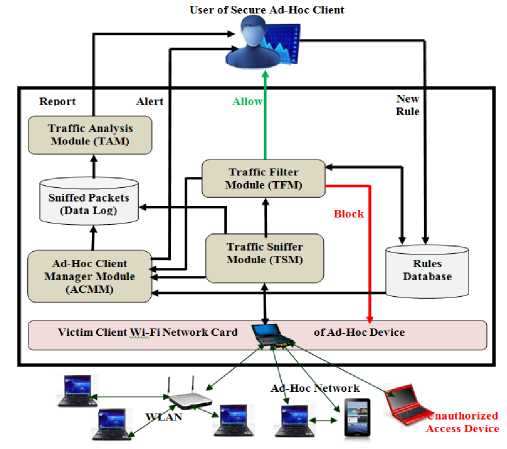
Figure 8: Ad-hoc client defense against unauthorized access
In Fig. 9, the ad-hoc client device traffics are captured by the TSM. TSM captures all the arrival Wi-Fi packets to the ad-hoc client and provides total information about it. At first user of ad-hoc client has to choose a network card then press start capture to begin sniffing the packets. Then user can choose to stop sniffing and drop the sniffed logged data packets into a “PCAP” file format as shown in Fig. 10. TSM identifies: Packet arrival time; Length; Source IP; Destination IP, used Protocol and Payload. It provides multi panes so that the user can select a specific packet in one pane to display its data content in another pane view.
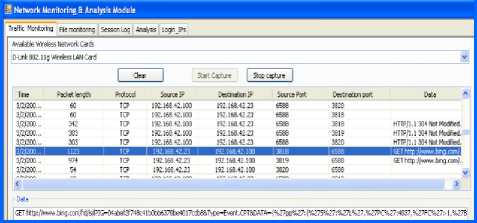
Figure 9: Ad Hoc Device Traffic Sniffer Log
Figure 10. Traffic Data Log in “PCAP” File Format
-
5.2.2 Ad-Hoc Client Manager Module (ACMM)
-
5.2.3 Traffic Filter Module (TFM)
ACMM provides information about the available wireless networks. Fig. 11 shows the available (given wireless card) details of specific ad-hoc device near to you to connect. The output will be displayed after scanning process with the following details: Network card type, Network name, MAC address, Signal quality, Security and Authentication. User can do “scan process” at any time to be informed with the available wireless networks and their data.
As shown in the Fig. 11, the SSID name called " HMF_WIRELESS " is displayed and its corresponding MAC address. Also, the signal quality for this detected network is displayed and secured WLAN status (see Fig. 11). The “Scan” option can be selected more and more to detect the additional Wi-Fi networks. In addition, ACMM arise alerts when policy violation detected. Such as a file/directory on the host machine is required to be illegal accessed by a network user.
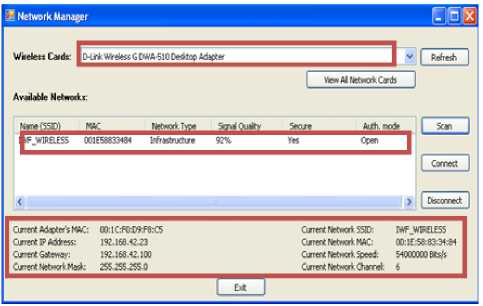
Figure 11: Available Details of Specific Device
TFM is ad-hoc client filter to allow/deny the connections to the ad-hoc client. It is different from windows firewall as it is designed to provide more options, which allow user to prevent the connections by all other network nodes on the same network from, connect to the user host. In addition, the user has an option to identify some legible machine IP(s) to allow them to connect to his secure ad-hoc client. So that, the user has the ability to connect to the network, while all other network nodes will be denied. TFM takes its decision to allow or block specific connection based on sniffing data from TSM and available rules in the database. TFM send its decision to both ACMM and user of secure ad-hoc client with alert message. Finally, TFM may update existing rule or add addition rule into rules database. Sometimes TFM leave this filtering decision to the user of secure ad-hoc client.
Once the user or TFM allowed this access, this allowed device can access the files in the secure ad-hoc client. With every try from the guest user to access a new file in the secure ad-hoc client the pop-up alert window will appear to the user with details about this new access and options to allow or block this access regardless previous decision.
If the user or TFM blocked this connection then TFM will drop all packets from blocked device (IP) to prevent this IP to access any files in the secure ad-hoc client. This IP will be added to a filtering rules database to prevent this IP from accessing or dealing with the user's machine. In all cases, the user can change the status of any IP from trusted IP to blocked IP and from blocked IP to allowed IP or the user can add a new IP to the trusted list or to the blocked list.
There are four level levels of security available in TFM as shown in Fig. 12:
-
• High: This level disables all packets to / from our secure ad-hoc client.
-
• Medium High: This level disables all input packet to our secure ad-hoc client, but you can send (connect to) other devices in your ad-hoc network.
-
• Medium: This level is custom level which allow you to connect with other devices in your ad-hoc network (send & receive packet) and reject the rest of devices in your ad-hoc network, this is level is preferable in case of using proxy on our secure ad-hoc client.
-
• Low: This level stops filtering operation of TFM and it is not recommended.
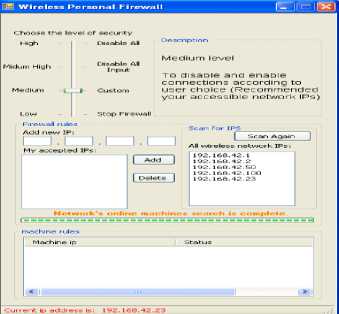
Figure 12: Wireless Packet Filtering in TFM
When discovering a new ad-hoc connect device appeared in the network an appropriate alert should be raised to our underlying secure ad-hoc client user. This alert should has some details appeared about the new device connects to the ad-hoc network; these details are device IP, device Mac address and the device name. The idea is that when a new device connects to the ad-hoc network it broadcasts ARP packets to all devices in the ad-hoc network because ARP is used as a simple announcement protocol. This is useful for updating other devices mapping of a hardware address when the sender's IP address or MAC address needs to be updated in all ad-hoc network devices. By detecting ARP packets according to ARP packet structure, we can reach to the user’s client.
If the details of this device already exist in the user’s database, it means it’s already known device. If not it means it’s a new device joined the ad-hoc network. The system will alert the user about this new connected device. System gives the following information about connected device: IP address, Mac address and device name then the user can know if this new connected device is trusted or it’s not trusted and he/she has to take action against it. The ACMM raised the alert message to user of our secure ad-hoc device client contains computer name, IP address, operating system and message say "This computer trying to access your machine", when policy violation detected as shown in Fig. 13. Without this alert, the user of secure ad-hoc client could not know that a new network device trying to access his machine. Now, the user of secure ad-hoc client should to decide whether to allow or deny this new connection through TFM.
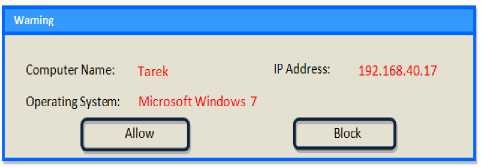
Figure 13: The Alert Message on Illegal Access Trial
This proposed model is a client-side filter to allow/deny the connections to our secure ad-hoc client. The secure ad-hoc client user can select either allow or block option as shown in Fig. 13. The secure ad-hoc client user reaction should be logged to be used by TAM.
-
5.2.4 Traffic Analysis Module (TAM)
TAM allows the user of secure ad-hoc client to get a reports, statistics, and analysis charts of network activities captured by the system. These charts can give the user information about the most active IPs with the user's machine in the last session, the most active source and destination ports, and the most active IPs through a specific period of time determined by the user as well.
The statistical analysis of the machine activities can be viewed by charts representing the most frequent used IPs. Fig. 14 shows an example of the machines traffic within a period of time (3 hours). Graph shows IPs 192.168.40.12 and 192.168.40.17 that have accessed the secured ad-hoc client machine in this period of time.
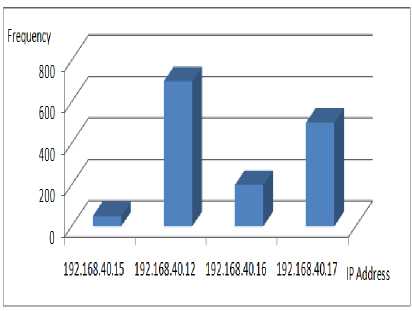
Figure 14: The frequency of the IP usage within 3 hours
Fig. 15 displays the output from traffic analysis module. It shows that 192.168.40.23 is the most active IP device connected to our ad-hoc device client.
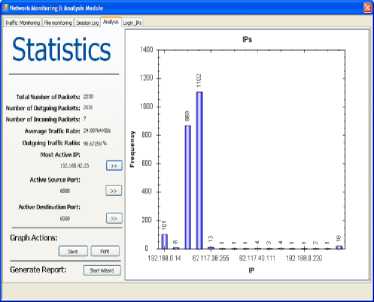
Figure 15: Most Active IP Connected Device
Fig. 16a and 16b is statistic result from analysis module. It displays both most active source port and destination port respectively.
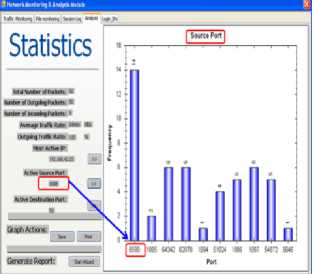
Figure 16a: Most Active Source Port
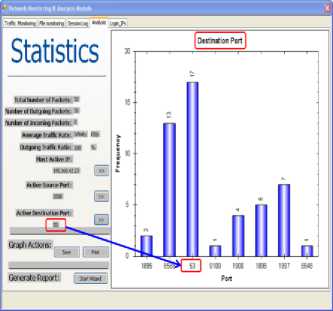
Figure 16b: Most Active Destination Port
-
6. Conclusions and Future Directions
Wireless connectivity is simple access to the network compared to traditional wired connectivity such as Ethernet. Wireless standards provided a comprehensive solution to the WLAN security but wireless security will have to continually evolve to keep up with the newest attacks. Current researches looking for authentication and encryption algorithms to ensure that defenses capabilities are in place to provide a complete security solution. Detecting unauthorized access devices is the first step to defend your AP and ad-hoc client.
This work presents two models. First model consists of these components: Sensors to capture the wireless traffic and network behavior, central monitoring and response engine to collect its inputs from available sensors, and a management component to identify the connection to unauthorized access according to authorized list database and take appropriate actions. In this model, we used the access list table in addition to clock skews for detecting unauthorized AP in WLAN. Second model presents a solution to protect ad-hoc clients. This model consists of four main modules, traffic sniffer, ad-hoc client manager, traffic filter, and traffic analysis.
The proposed solution faced the problem of detecting unauthorized APs and/or ad-hoc client, but the general problem of finding encryption-free method to detect spoofed MAC by any wireless client still remains open area of research.
Список литературы Wi-Fi Networks Security and Accessing Control
- LaRoche, P. and Zincir-Heywood, A.N., "Genetic Programming Based Wi-Fi Data Link Layer Attack Detection", "In Proceedings of the 4th Annual Communication Networks and Services Research Conference (CNSR 2006)", IEEE Press, May 24–25, 2006, pp. 8–15.
- Securing Wi-Fi Wireless Networks with today's Technologies, Wi-Fi Alliance. Available at: http://www.Wi-Fi.org/files/wp_4_Securing%20Wireless%20Networks_2-6-03.pdf [Accessed Nov. 2009].
- Balachandran, S., Dasgupta, D. and Wang, L., "A Hybrid Approach for Misbehavior Detection in Wireless Ad-Hoc Networks", "In Symposium on Information Assurance", New York, USA, June 14–15, 2006.
- M. E. Elhamahmy and Tarek S. Sobh, "Preventing Information Leakage Caused by War Driving Attacks in Wi-Fi Networks", Proceedings of the 14th International Conference on AEROSPACE SCIENCES & AVIATION TECHNOLOGY, ASAT–14, pp 09, May 24 – 26, 2011, Military Technical College, Kobry Elkobbah, Cairo, Egypt, 2011.
- S. Zanero, "Wireless malware propagation: A reality check," IEEE Security and Privacy, vol. 7, no. 5, pp. 70{74, September-October 2009.
- Tom Rowan, "Negotiating Wi-Fi security", Network Security, February 2010, pp: 8-12, 2010.
- Huajian Mao, Nong Xiao, Weisong Shi, and Yutong Lu, "Wukong: A cloud-oriented file service for mobile Internet devices", Journal of Parallel Distributed Computing, Vol. 72 (2012), pp: 171–184, 2012.
- Yung-Wei Kao, ChiaFeng Lin, Kuei-An Yang, and Shyan-Ming Yuan, "A Web-based, Offline-able, and Personalized Runtime Environment for executing applications on mobile devices", Computer Standards & Interfaces, Vol. 34 (2012), pp: 212–224, 2012.
- Reed M., P. Syverson and D. Goldschlag, Protocols using Anonymous Connections: Mobile Applications, 1997 Security Protocols Workshop.
- G. Perrucci, F. Fitzek, G. Sasso, W. Kellerer, J. Widmer, "On the impact of 2G and 3G network usage for mobile phones battery life", European Wireless, 2009.
- Lee Barken and Eric Bermel, "Wireless Hacking: Projects for Wi-Fi Enthusiasts", Chapter 10: Wireless 802.11 Hacks, Appendix A, pp 299-323, Published by Syngress
- A. Muthitacharoen, B. Chen, D. Mazieres, A low-bandwidth network file system, in: Proceedings of the eighteenth ACM symposium on Operating systems principles, ACM, 2001, pp. 174–187.
- Martin Beck and Eric Tews, "Practical Attacks against WPA, November 8 2008, http://dl.aircrack-ng.org/breakingwepandwpa.pdf
- T. Raman, "Cloud computing and equal access for all", in: Proceedings of the 2008 International Cross-disciplinary Conference on Web Accessibility (W4A), ACM, 2008, pp. 1–4.
- WPA™ Deployment Guidelines for Public Access Wi-Fi® Networks, Wi-Fi Alliance. Available at: http://www.Wi-Fi.org/files/wp_6_WPA%20Deployment%20for%20Public%20Access_10-28-04.pdf [Accessed 27 Nov. 2009].
- IEEE Std 802.11-1997 Information Technology- telecommunications And Information exchange Between Systems-Local and Metropolitan Area Networks specific Requirements-part 11: Wireless LAN Medium Access Control (MAC) And Physical Layer (PHY) Specifications, IEEE, 1997. http://ieeexplore.ieee.org/search/freesrchabstract.jsp?arnumber=654749&isnumber =14251&punu mber=5258&k2dockey=654749@ieeestds&query=%28802.11+1997%29%3Cin%3Emetadata&pos=0
- Gopinath K. N. and Hemant Chaskar, "A quick reference to Rogue AP security threat, Rogue AP detection and mitigation", AirTight Networks, 2009, www.AirTightNetworks.com
- Ter Kah Leng, "Wireless Internet regulation: Wireless Internet access and potential liabilities", Computer law & Security Report, Vol. 23 (2007), pp: 550 – 554.
- Reiter M. K. and Aviel D. Rubin. Crowds: Anonymity for Web Transactions. ACM Transactions on Information and Systems Security, (1)1, 66-92, June 1998.
- Mishra, A. and Arbaugh, W. A., "An Initial Security Analysis of the IEEE 802.1x Standard", University of Maryland, Tech. Rep. CS-TR-4328, 802.11, IEEE 802.11 Standard, 2005. Available at: http://grouper.ieee.org/groups/802/11/ [accessed 24 Mar, 2010]
- Borisov, N., Goldberg, I. and Wagner, D., "Intercepting Mobile Communications: the Insecurity of 802.11", "In 7th Annual International Conference on Mobile Computing and Networking", 2001.
- Fluhrer, S., Mantin, I. and Shamir, A. "Weaknesses in the Key Scheduling Algorithm of RC4", "In 8th Annual International Workshop on Selected Areas in Cryptography", 2001.
- Wireless LAN solution engine (WLSE), http://www.cisco.com.
- Siemens Enterprise Communications, "WLAN Security Today: Wireless more Secure than Wired", White Paper, July 2008.
- ManageEngine UK Distributor: Networks Unlimited, "Wireless Network Rogue Access Point Detection & Blocking", www.manageengine.co.uk [accessed 2005]
- Tarek S. Sobh, "Wired and Wireless Intrusion Detection System: Classifications, Good Characteristics and State-of-the-art", Computer Standards & Interfaces, volume 28/6, pp. 670-694, 2006,
- Yin, H., Chen, G., and wang, J., "Detecting protected layer-3 rogue APs," in IEEE BROADNETS '07: Fourth Annual International Conference on Broadband Networks, 2007.
- Liran Ma, Amin Y. Teymorian, and Xiuzhen Cheng, "A Hybrid Rogue Access Point Protection Framework for Commodity Wi-Fi Networks", IEEE Communications Society subject matter experts for publication in the IEEE INFOCOM 2008 proceedings, 2008.
- W. Wei, K. Suh, B. Wang, Y. Gu, J. Kurose, and D. Towsley, "Passive online rogue access point detection using sequential hypothesis testing with tcp ack-pairs," in IMC '07: Proceedings of the 7th ACM SIGCOMM conference on Internet measurement. New York, NY, USA: ACM, 2007, pp. 365–378.
- T. Kohno, A. Broido, and K. C. Claffy, "Remote physical device fingerprinting", IEEE Transaction on Dependable and Secure Computing, 2(2):93–108, 2005.
- Suman Jana and Sneha K. Kasera, " On Fast and Accurate Detection of Unauthorized Wireless Access Points Using Clock Skews", Proceedings of the MobiCom'08, September 14–19, 2008, San Francisco, California, USA.
- Kumari, L., Debbarma, S. and Shyam R., "Security Problems in Campus Network and Its Solutions", "International Journal of Advanced Engineering & Application", Vol. 1, Issue 1, pp. 98-101, Jan 2011.


