A Framework for Detecting Cloning Attacks in OSN Based on a Novel Social Graph Topology
Автор: Ali M. Meligy, Hani M. Ibrahim, Mohamed F. Torky
Журнал: International Journal of Intelligent Systems and Applications(IJISA) @ijisa
Статья в выпуске: 3 vol.7, 2015 года.
Бесплатный доступ
Online Social Networks (OSN) are considering one of the most popular internet applications which attract millions of users around the world to build several social relationships. Emerging the Web 2.0 technology allowed OSN users to create, share, or exchange types of contents in a popular fashion. The other hand, OSN are considering one of the most popular platforms for the intruders to spread several types of OSN attacks. Creating fake profiles for launching cloning attacks is one of the most risky attacks which target Users' profiles in Online Social Networks, the attacker seek to impersonate user's identity through duplicating user's online presence in the same or across several social networks, therefore, he can deceive OSN users into forming trusting social relations with his created fake profiles. These malicious profiles aim to harvest sensitive user's information or misuse the reputation of the legitimate profile's owner, as well as it may be used as a spy profiles for other criminal parties. Detecting these fake profiles still represent a major problem from OSN Security and Privacy point of view. In this paper we introduced a theoretical framework which depends on a novel topology of a social graph called Trusted Social Graph (TSG) which used to visualize trusted instances of social communications between OSN users. Another contribution is a proposed detection model that based on TSG topology as well as two techniques; Deterministic Finite Automaton (DFA) and Regular Expression. Our proposed detection model used to recognize the stranger instances of communications and social actions that performed using fake profiles in OSN.
Fake Profiles, Cloning Attack, Trusted Social Graph (TSG), Friend Pattern, Regular Expressions, and Deterministic Finite Automata (DFA)
Короткий адрес: https://sciup.org/15010663
IDR: 15010663
Текст научной статьи A Framework for Detecting Cloning Attacks in OSN Based on a Novel Social Graph Topology
Published Online February 2015 in MECS
Online Social Networks (OSN) are considering one of the most recent internet applications which attract millions of users to setup several types of social relationships such as friendships, business or common interests…etc. Emerging the web 2.0 technologies which present a new dynamic version of World Wide Web (WWW), allowed users across online social networks to share, exchange and create several types of contents [1]. Online Social Network services range from social interactions-centered platforms such as Facebook or MySpace, to information dissemination-centric platforms such as twitter or Google Buzz, to Social interaction feature added to existing platforms such as Flicker [2]. The other hand, enhancing security considerations and protecting the OSN privacy still represent a major bottleneck and considered challenge. From a security point of view online social networks have unique characteristics. First, information access and communication models are based on the trust between parties, such that, OSN users typically share vital amount of private and personal information with their friends. This information may be shared in public mode or dedicated private mode. If it is not public, access to it must be regulated by a network of trust, in this case, a user allows to his friends to access and view information regarding him. Second, unfortunately, Online Social Networks haven't strong authentication mechanisms for protecting users' profiles. This matter provides an easy way to impersonate user's identity and to steal in a user's network of trust [3]. In recent days, users' profiles and their personal and private information are representing a main target for many OSN attacks that can exploit the weaknesses of OSN security and privacy mechanisms. These attacks include Identity theft [4] by which the intruder able to convince anyone about the ownership of some particular OSN profile. Profile Hijacking [5], the goal of the adversary is to obtain control over some existing profiles within OSN platforms. Profiling attack [6], by which the intruder aims to gather information about OSN activities. Crawling and Harvesting attacks [5], the main goal of crawling attack is to aggregate publicly available information across multiple OSN profiles and applications in an automated way. Another attack by which the attacker crawls across different OSN platforms is called harvesting attack by which the harvested results are storing in large dataset with larger amount of private information about OSN users. Image Retrieval and Analysis Attack [5], is another attack which target multimedia data such as (images, videos, etc). This attack is followed by subsequent analysis via Reverse Social Engineering attack (RSE). RSE is a specific type of social Engineering attacks by which the adversary doesn't initiate contact with the victim, rather the victim is tricked into contacting with the attacker himself [7].Special type of impersonation attacks is the Cloning Attack by which the intruder creates some fake profiles for one or more users. These fake profiles are claiming the same identity as the genuine profiles in a given OSN. The cloning attack makes the fake profiles able to setup friendships with the victim's friends and eventually mounting malicious activities with them [8]. In other words, the intruder seeks to finds user's personal information such as (name, job, photo of his profile …etc) then forges user's identity and creates a similar profile as a fake profile in OSN. Finally, he sends friend requests to victim's friend list. As soon as these friend requests are accepted and confirmed, a new friend list network is built. Hence, the intruder become able to access friend's profiles of the victim and steal sensitive information or mount other malicious activities such as posting malicious photos or sending spam messages, etc [9].In response to this type of attacks, this paper introduces a novel framework for detecting fake profiles in OSN. This paper involves two contributions; first, we introduced a novel graph topology called Trusted Social Graph (TSG). TSG model used to visualizes the instances of trusted communications between OSN users in a novel way which facilitate detecting the un-trusted or fake communications between OSN users. Second, we present a detection model that depends on two terms: Regular Expressions and Deterministic Finite Automaton (DFA) for detecting fake profiles in Online Social Networks.
The rest of this paper is organized as follows; section II presents and discusses the literature review. Section III clears some of profile features that may be exploited by Cloning Attack. Section IV presents the major proposed definitions and concepts by which our methodology based on it. Section V presents the proposed theoretical framework which used for detecting cloning attacks through a proposed Social Graph Topology called a Trusted Social Graph (TSG) as well as, a proposed detection model for recognizing malicious social behaviors of fake profiles in Online Social Networks (ONS). Finally, section VI formulates the general conclusion and suggests how we can improve this framework in the future.
-
II. Related Work
Impersonations threats in Online Social Networks (OSN) such as creating Fake Profiles by which OSN hackers use to launch cloning attacks, are considering one of the hot topics from OSN security and privacy point of view. The intruder seeks to create fake profiles to setup fake relations with the victim's friends and to mount malicious activities such as misusing the reputations of OSN users. In Ref [9] profile cloning and identity theft attacks are introduced, and then, a framework for detecting suspicious identity is proposed. This approach is based on attribute similarity and friend network similarity measures. According to similarity measures which are computed in each step and by having predetermined threshold, it will be decided which profile is clone and which one is genuine. In [10] the authors proposed a methodology for detecting profile cloning in OSN, the study presents architectural design and implementation details of a prototype system that can be employed by users to investigate whether they have fallen victims to such an attack. The core idea behind this approach is to identify any information contained in the user's profile that uniquely identifies him. The experimental results from use of this prototype system prove its efficiency and simplicity. In [8] the authors introduced a new model aims to mitigate the threat of the fake profile attack, where an adversary tries to impersonate the victim on a specific OSN where the victim has no prior profile in place. The main idea behind this approach is to study the temporal evolution of OSN and characterize real user profiles where data can be collected and used to identify set of feature in dynamic mode of OSN. These features can be used to study the time evolution of a given test profile and detect any major deviations from expected behavior of a profile. In [11] the study showed how to use exclusive shared knowledge to allow users to take responsibility for identifying their own trusted friends in an OSN in a completely online way. The idea is, secret information shared only between a pair of OSN friends, then rules of " Bond Breaker Game" are applied which is a practical tool associated with public Key Infrastructure (PKI) for identifying friends in OSN. The results were presented through a study on Facebook, which showed that users who do share exclusive knowledge with their Facebook friends, the adversary are rarely able to know or guess that knowledge. M.Fire,G.Katz, and Y.Elovici in Paper [12] presented a novel methodology for detecting malicious profiles in OSN. The proposed methodology used a combination of graph theory algorithms and machine learning in order to detect these malicious profiles, the proposed algorithm had been evaluated on several social networks and was found to be effective in detecting various types of fake profiles. In [4] the authors investigated two automatic attacks: First, Identity Theft Attack within one OSN. The attack is simulated in an automated way for existing user profile and sending of friend requests to the friends of cloned victim. The hope of the intruder here is to gain the trust of these profiles. By establishing friendship relationships with the contacts of the victim, hence, the attacker becomes able to access the sensitive personal information of these contacts. The second attack is Cross-Site Profile Cloning Attack, which simulated in an automatic way by creating forged profiles in OSN in which the victim isn't belong to it but his friends are registered in it, and then connect to the victim's friends who are registered on both networks. The experimental results showed that these two simulated attacks are effective and feasible in practice. The author also introduced some suggestions for improving security and privacy of OSN in face of these two attacks. In a similar study [6] that present misusing OSN using automated profiling attack, the authors introduced a prototype system which simulates the fact that an attacker can query several OSNs to obtain registered e-mail addresses on a large scale. By automatically crawling and correlating these profiles that associated with the collected e-mails addresses, personal information about each user are gathered which used for automated profiling attack. The proposed prototype system is applied on the most popular OSN such as Facebook, MySpace, and Twitter. The results showed that the automated profiling attack executed in efficient way . in addition the results reflect that these social networks still have common weakness and still need for more security precautions to protect the vast amount of personal information stored on these networks. This study also introduced several mitigation strategies that can be used to limit the extent of this attack. One of the common risks of creating fake profiles is to use in launching spam messages [13]. The authors presented a design and real world evaluation of a novel social honeypot-based approach to social spam detection, the research goal is to investigate techniques and develop effective tools for automatically detecting and filtering spammers who target social systems. Another similar study for detecting spammers in Twitter-Social Network [14] introduced a spam detection prototype system to identify suspicious users on Twitter. Architectural social graph model is proposed to explain the "follower" and "friend" relationships among Twitter's users based on the spam policy of Twitter, a novel content-based and graph-based feature are proposed to simplify spam detection process. The author exploited classical classification algorithms to detect suspicious of spam accounts and developed a web crawler using Twitter API method to collect real data set from public available information on Twitter, finally, he analyzed the data set and evaluated the performance of his detection system. Also in [15], the authors discussed the functionality and the implementation of SocialNetworkingBot which is a proof of concept botnet that uses Twitter for command and control of individual bots.
-
III. Profile Features And Cloning Attacks
The intruders seek to create fake profiles in OSN for launching cloning attack that used to misuse user's profiles through main features of user's profile. We shed light on these features as follows:
-
A. Personal page
Personal page is considered one of the vital assets in user profile since this page contain personal information such as (name, gender, job, education, photos, ... etc). The default seating in OSN such as Facebook is that you able to access on the personal page of any user even he isn't in your friend list. Also, you can share any content without any access control, as well you can send message to any profile without any authenticated prove about the verification of identity of the sender. Although this may be seen as a flexible use in online social networks, but this may be a weakness from security and privacy point of view. Such that the fake profiles that created by OSN intruders able to setup trusted relationships with OSN user through exploiting access flexibility on users' personal page.
-
B. Home Page
Is the front end of user's profile in which all shared contents such as photos, texts, videos, or some commercial advertisements are appearing through it. The shared contents may be from your friends or may be from others. The OSN attacker may exploit the home page to share advertisement for a specific product or for a specific company through fake page in an attractive layout. Then he invites the victim to enroll to this page without any mechanism for recognizing the identity of this page.
-
C. Friend Requests List
Is a menu that includes all friend requests that requires choosing one of three options, confirming, ignoring, or delaying the request. Friend requests list is agglutinative contact which the attacker can use to send fake requests to users. As soon as accepting this request, the fake profile will added to your friend list. Hence the fake profile can exploit this permission to mount malicious activities with your friends in the friend list.
-
D. Messages List
Is a menu that involves all messages you sent to or received from other user in OSN. The other hand, messages list is another channel through which cloning attack can occur. The intruder may send spam message [1, 3] to specific user and this messages may contain malicious link to third party or may be a malicious link for running malicious software or deceive users to join to other malicious web sites. Since there is no an effective mechanism by which we can control in sending and receiving messages across OSNs, the users' profiles may be threaten with spam messages which are sent through fake profiles in OSN.
-
E. Friends and Close Friends Lists
Friend list is a menu that involves all friends whom user may contact with them through several instances of communications using synchronous or asynchronous messaging. The other side, Close Friend list is a derived menu from the friend list that involves the most important friends for you. The social service provider flags them with "yellow star" as a mark to distinguish them from other friends. In the opposite direction, OSN adversaries seek to obtain victim's friend list, then send fake friend request to them which will be accepted at the most. Such that most smart OSN attackers add some victim's friends to his close friend list to be common with the victim's close friends, this will make the fake profile more genuine and has more trust [9, 14].
-
IV. Basic Concepts For The Detection Framework
In this section we present some definitions and concepts by which our detection framework depends on them. We import some techniques, Principles, and methodologies that used in compiler when recognizes the language, but we correlated it to adapt with our problem that explains how to recognize and detect Fake Profiles in Online Social Networks.
Let x be a specific user in an OSN system, we define the profile of x as two tuples ( , ( ) ) where:-
-
1- is an attribute label in the form user's name and specific image by which user is digitally represented in specific OSN.
-
2- ( ) is a unique Friend Pattern (FP) of user that
used as a rule by which a set of trusted profiles (i.e. trusted users ) in the friend list of user can be recognized. In addition, each Friend Pattern (FP) is represented mathematically as a Regular Expression over specific Alphabet ∑.
From authentication point of view, we define the Friend List of user x in specific OSN as a Regular Set that includes some of Rules (R). Each rule is represented as two concatenated Friend Patterns in the form R. = FP . FP . Such that FP is the friend pattern i xy x of user x. and FP the Friend Pattern of user y.
R 1 = FP z . FP a

R 2 = FP z . FP b <-------------------
User Z

Friend A

Friend B

Friend C
R = FPz . FPc (
User Z in OSN
Authenticated Friend List of User Z
Fig. 1. a novel view for representing a user's Profile and the associated Friend List in OSN
Fig.1. Show an authenticated way by which a specific user in a specific OSN can set up social relations between him and his friend list. For example, the Rule/protocol which authenticate the social relation between User Z and his Friend A is; R = FPz . FP .Such FPzand FPa is the friend patterns of user Z and friend A respectively. In addition, each Friend Pattern is represented mathematically as a Regular Expression as we cleared in Definition 1.
Definition 3: ( Finite Automaton FA)
Is a mathematical model used as a recognizer for regular set of strings that derived from a specific Regular Expression . A Finite Automaton consists of five tuples:
Such that
Q is a non empty finite set of states , V q E Q, q is called state of Q .
∑ is an input alphabet such that the derived strings of specific Friend Pattern is from ∑ .
δ is a transition function that maps from state to another state in Q over input symbol of the alphabet ∑, such that, δ : Q×∑ → Q .
is the initial state of FA.
F is a finite set of final state of FA, F C Q, V q E F, q is called the final state.
As we see in Fig. 2. that presents an example of Finite Automata (FA) that can recognize all strings that derived from the Regular Expression: ∗ ∗, such as ( aabacc, aaabaccc, abacccc, aaaaabac, etc). Really, the Finite Automata (FA) doesn't be a novel concept, however, we defined it here since we use it as an effective tool for recognizing Friend patterns which represented as a Regular Expressions to accept or reject profiles' social actions in Online Social Networks.
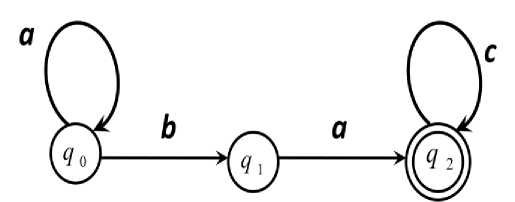
Fig. 2 . Finite Automata for recognizing all strings derived from the Friend Pattern: ∗ ∗ .
According to Definition 3 we have:
-
1- Q = ( q 0, q 1, q 2 ).
-
2- ∑= {a , b, c }.
-
3- δ can be defined as:
8 i ( q 0 , a ) = q 0 8 т ( q 0 , b ) = q 1
^ 3 ( q 1 , a ) = q т
84k q 2 , c ) = q г
-
4- The initial state is q
-
5- The set of final state is F = { q 2 }
Definition 4: (Genuine Profile)
A specific profile of user in OSN is said to be a Genuine Profile to user , if and only if , there exist a Deterministic Finite Automat (DFA) that associated with the profile of user x and able to recognize the authentication Rule/Protocol between user x and user y .
A specific profile of user in OSN is said to be a Fake Profile to user if and only if , the Deterministic Finite Automat (DFA) that associated with the profile of user x able not to recognize the authentication Rule/Protocol between user x and user y .
For visualizing our framework about detecting fake profiles in Online Social Network (OSN) , we need to define special type of graphs called DeBruijn Graph [16] on which our proposed social graph topology is based on it.
Definition 6: (DeBruijn Graph)
In graph theory, a graph of order k denoted by G ( k ) is said to be DeBruijn Graph if it was directed graph with 2 k vertices, each labeled with a unique k-bit string . Vertex a is joined to vertex b by an arc if a bit string of b is obtainable from bit string of a by either cyclic shift or DeBruijn shift . Additionally, each arc of G( k ) is designated as cyclic shift arc or debruijn arc . According to the shift operation, each arc is labeled by the first bit of the vertex at which it originates, followed by the label of the vertex at which it terminate.
Fig.3.depicts a Debruijn Graph of order 3 (i.e.
G (3) = 2 3 =8 vertices) and the bit-strings associated with these vertices are: 000, 100, 001, 010, 101, 110, 011, and 111.
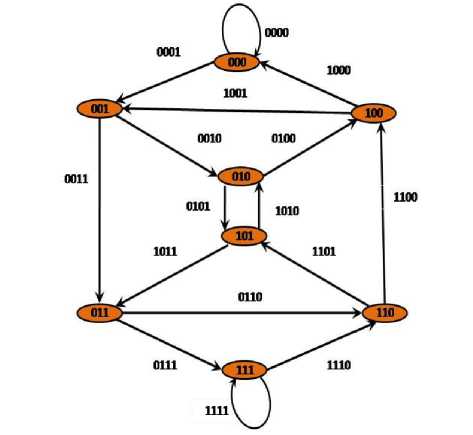
Fig. 3. An example of DeBruijn graph of order 3: G (3) =8 vertices.
-
V. The Proposed Detection Framework
We suggest that we can use the DeBruijn graph to derive a novel social graph topology called " Trusted Social Graph (TSG) ". The proposed graph topology can visualize social relations in an authenticated manner. Hence, detecting fake profiles and recognizing trusted friends in OSN became a possible issue through the proposed approach. Our new social graph (TSG) has common properties and features with DeBruijn graph, but it also has proposed properties that differ from DeBruijn graph model. The new properties are proposed to adapt with our detection methodology. We can formulate the general definition of our proposed Trusted Social Graph model (TSG) as in the next definition;
Definition 7 (Trusted Social Graph (TSG) )
Trusted Social (TSG) is a directed graph; TSG (V, E), such that each vertex v e V is defined as three tuples, v = (FP, ,lL, ,dDFA, )
-
( v ) ( v ) ( v )
Where,
FP : is a Friend Pattern of vertex v that is represented mathematically as a unique Regular Expression over a specific Alphabet ∑.
L : is an attribute label in the form user's name and specific image of vertex v by which the user associated with the vertex v can commonly represented in OSN.
DFA : is a Deterministic Finite Automaton which associated with the vertex v to recognize the trusted and authenticated relations. Also, DF A used for detecting fake social relations through parsing the predefined Rule/Protocol between vertex v and other vertices in the Trusted Social Graph (TSG) .
Also, each edge e e E from v to v 2 is identified with a derived string s of the Friend Pattern of vertex v (i.e. FP ) concatenated with a derived string s of the Friend Pattern of vertex v (i.e. FP ) in the form " s . s " which parsed by the d eterministic f inite Automata that associated with vertex v (i.e. DFA
2 ( v 2 )
-
A. Trusted Social Graph (TSG) Topology
As we mentioned above that our TSG model is based on DeBruijn graph with proposed properties and features, before we explain these additional features, we present first the common features between TSG and DeBruijn graph as follows:
-
1 TSG and DeBruijn graph are directed graph
-
2 Each arc directed from v to v can be identified as a function in v and v
-
3 Each vertex v.orv e V is labeled with a unique code that used to derive a specific string s used in identifying the relation between v andv such that v i andv j e V j .
The other side, the novelty features in our proposed TSG model are:
-
1- Each vertex v e V is described as three tuples
v, = ( FP, vL DFA ) i ( v ) ( v ) ( v )
as described in definition 7
-
2- Each vertex v e V has n in-degree and m out-degree
such that n ^ m , but in DeBruijn graph it has 2 indegree and 2 out-degree.
-
3- The Friend Pattern FP that associated with specific vertex v e V is used to derive set of strings, which used in represent instances of social
communications between vertexes v and other vertex v in the Trusted Social Graph.
-
4- The in-arcs directed to specific vertex v G v represent instances of social communications from other vertices in TSG model.
-
5- TSG is a dynamic graph such that it visualizes changeable instances of social communications between OSN users.
-
6- Any arc from v tov is labeled with a string in the form S = Sj . s. such that s is derived from the Friend Pattern of v and s is derived from the Friend Pattern
of v and S represent the Rule/Protocol of the Social Communication instance.
-
7- Each Vj G V is associated with a Deterministic Finite Automaton DFA to parse the in-relations to v
(vi ) i which labeled with the string S = s,. s. such that S, is derived from the Friend Pattern of v and s is derived from the Friend Pattern of v
-
8- TSG has no any self loop in any vertex vt G V .
Our proposed TSG topology is described in Fig. 4. that visualizes some instances of social communications between eight users(e.g.. A, B,C,D,E,F,G,H) in a specific
Online Social Network. Each node is represented as three tuples, v = ( fp l dfa )
i ( v ) ( v ) ( v )
as we previously
mentioned. The Friend Pattern in each node is represented mathematically as a unique Regular Expression over specific Alphabet as presented in Table 1.
Table.1. Friend Patterns of eight users in TSG
|
# Profile |
Alphabet ∑ |
Friend Pattern (FP) |
|
Profile of user A |
E = ( a , b , c ) |
ab * c |
|
Profile of user B |
E = (0,1) |
010* |
|
Profile of user C |
E = (#,2) |
#2*# |
|
Profile of user D |
E = ( y , x ) |
** y xy |
|
Profile of user E |
E = ( m , n , o ) |
mn * o |
|
Profile of user F |
E = (1,0, r ) |
1*0 r |
|
Profile of user G |
^ = ( k , l , m ) |
klm * |
|
Profile of user H |
^ = ( p , q , z ) |
pq * z |
For Forming authenticated and trusted social communications between a specific user and his genuine friends of his friend list, this problem requires three phases to mitigate it, as described in Fig.5
-
1. Forming the Friend Pattern (FP): in this phase, a specific Regular Expression is used to set up and form the usable Friend Pattern (FP) of each user in an Online Social Network.
-
2. Deriving strings of social communications: is the second phase, in which the regular set that involves some of strings is derived from the coordinate Friend Pattern of a specific user. The regular set of strings is used in identifying and distinguishing the current social relation between two users in OSN.
-
3. Forming the Protocol of Social Events: is the last phase, in which the Rule/Protocol that used to authenticate social relations between a specific user and his friend list is constructed. The Rule/Protocol
between a specific user and his friends can be formed
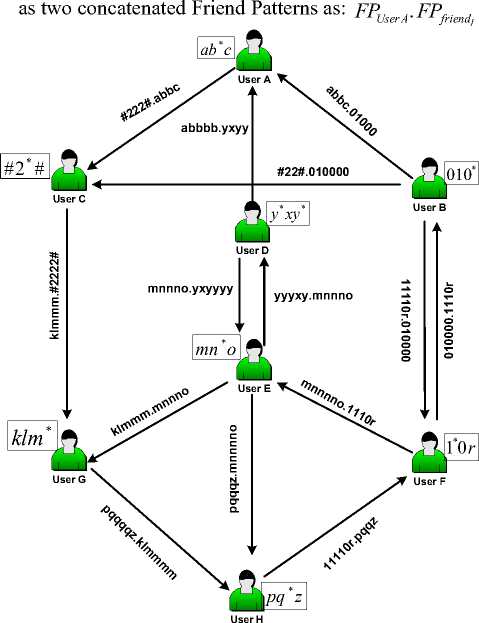
Fig. 4. The Proposed Trusted Social Graph (TSG) Topology
-
B. Friend Pattern Recognizing Process in TSG
In our dynamic Trusted Social Graph (TSG) which visualizes the instances of social events between OSN Profiles, each profile (i.e. a Vertex in TSG) is associated with a Deterministic Finite Automaton (DFA) as mentioned in Definition 7. The potential and major role of DFA that associated with a specific user's profile, is to recognize the incoming instances of social behaviors to decide whether the source of a specific social event (such as friend requests, sending messages, sharing photos or chatting, etc) is from a genuine and authenticated profile or from a fake and unauthenticated profile. As we saw in TSG topology (back to Fig.4.) in which each social relation from profile to profile is labeled with a string S = S}. S, such that Sj is a string derived from the Friend Pattern of user , and s is a string derived from j i the Friend Pattern of user . The DFA that is defined in the next definition is used to recognize the incoming social events to a specific user's profile through parsing the string that associated with a specific social event. Our proposed DFA that associated with each profile can decide to accept or reject a specific social action according to the predefined authenticated friend list of this profile (back to Fig.5.). Cloning Attack is considered one the active attacks in Online Social Networks since there is no an authenticated mechanism between a specific user and his friend list ensure specifying the identity of the source of social behavior. This vulnerability led to that the attacker can duplicate his presence with multiple profiles with the same layout. In response to this problem, we think that our proposed approach mitigates this problem in an effective manner.

∑ = ( a , b , c )
User A
A Random Profile in OSN
A Derived Strings from the Friend Pattern of User A
Forming the Friend Pattern of User A
**
FPuserA = a bac
Deriving strings of Social Communications
aabacc aaabaccc abacccc aaaaabac
Rule/Protocol of the Authentication
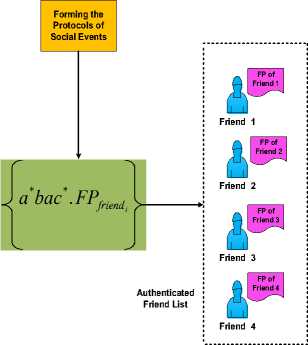
Fig. 5. a proposed methodology to authenticate user's friend list
Definition 8 (Detection Model of TSG-(DMT))
Is a Deterministic Finite Automaton. Such that, the DFA of a specific profile in TSG is consisting of five Tuples:
DMT = (Q, Z, 8, q o , F)
Such that,
Q: is a non empty finite set of states , ∀ q ∈ Q, q is called a state of Q
∑: is an input alphabet, which used to define input symbols of Friend Patterns that used in authenticating social relations between OSN profiles. Z can be defined as;
!=• и 11 и 12 и 13.....и z n
Such that " • " is the DOT concatenation operation and ∑ is the alphabet set of symbols by which the authenticated Friend Pattern of friend is defined in the friend list of profile
-
8: is a transition function that maps from state to state in Q over input symbol of the alphabet Z such that,
-
8: QXZ > Q .
-
q o : is the initial state of D FA.
-
F: is a finite set of final state of DFA, F ⊆ Q, ∀ q ∈ F , q is called the final state.
The Friend Pattern recognition process is depicted in Fig. 5. that explains how profile can recognize the authenticated and trusted social events that come from other users in OSN. The recognition process requires first to represent each profile in OSN as a Regular Expression (i.e. Friend Pattern) as we showed previously. Then it requires to create a Deterministic Finite Automaton (i.e. D(FP ) ).to parse the social relations between profile and his friend list (i.e. D(FP) ). The social behavior between any two profiles in OSN as described in the proposed TSG Topology is represented as two concatenated strings in the form string S = s . s such that s is a string derived from the Friend Pattern of user (i.e. the Receiver), and s is a string derived from the Friend Pattern of user (The Sender). if the current instance of social event is accepted by the DFA of profile , this mean the sender profile is genuine and authenticated profile in the friend list of the receiver profile (i.e. profile ), otherwise, the DFA will apply the transition OTHER which mean that the current instance of social behavior is from a fake profile or from unauthenticated one. Hence these profile will rejected
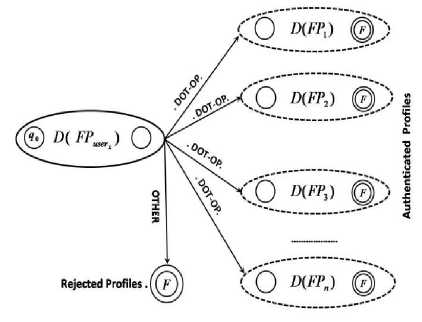
Fig. 6. A proposed Detection Model of TSG (DMT) model for recognizing Fake Profiles
-
VI. Conclusion and Future Work
One of the main malicious activities of OSN intruders today is their abilities for creating fake profiles which used as an effective way to perform cloning attacks across OSN platforms. From security and privacy point of view, detecting these fake profiles represent a major and potential problem. In this paper we proposed a theoretical framework for detecting these fake profiles in a novel view. The proposed framework depends on two dimensions: the first dimension is the proposed social graph topology which called Trusted Social Graph (TSG). We used TSG topology to visualize social relations between profiles across OSN platform in more controlled way. The second dimension is the detection methodology (i.e.DMT) that uses a Deterministic Finite Automaton (DFA) and Regular Expression techniques to parse and recognize the instances of social communications and social events that performed within OSN platform. The proposed detection model decides whether these social communications or social behavior from authenticated and trusted profiles or from fake and unauthenticated profiles. In the future work we will develop an algorithm to implement our detection framework and we will apply it on selected profiles as an experimental datasets from a specific Online Social Network.
Список литературы A Framework for Detecting Cloning Attacks in OSN Based on a Novel Social Graph Topology
- M.Bosma, E.Meij, and W.Weerkamp, " A Framework for Unsupervised Spam Detection in Social Networking Sites" ECIR 2012: 34th European Conference on Information Retrival, PP.364-375.
- Y.Altshler, Y.Elovici, A,B.Cremers, N.Aharony,and A.Pentland, "Security and Privacy in Social Networks" Springer NewYork, 2013.
- G.Stringhini, C.Kruegel, and G.Vigna, "Detecting Spammers on Social Networks" in proceedings of the 26th Annual Computer Security Applications Conference, ACM 2010,PP. 1-9.
- L.Bilge, T.Strufe,D.Balzarotti, and E.Kirda, " All Your Contacts Belong to us: Automated Identity Theft Attacks on Social Networks", in proceedings of the 18th international conference on world wide web. ACM,2009, PP.551-560.
- B.Furth," Handbook of Social Network Technologies and Applications", Springer,NewYork,2010.
- M. Balduzzi,C. Platzer, T. Holz, E.Kirda, D. Balzorotti, and C. Kruegel. "Abusing Social Networks for Automated User Profiling" Research Report RR-10-233, EURECOM, 2012, http://www.iseclab.org/ papers/ socialabuse-TR.pdf.
- D.Irani, M.Balduzzi, D.Balzorotti, E.Kirda, and C.Pu, " Reverse Social Engineering Attacks in Online Social Networks" detection of intrusions and malware and vulnerability assessment, PP.55-74, 2011.
- M.Conti, R.Poovendran, and, M.Secchiero, " Fake Book: Detecting Fake Profiles in Online Social Networks" Advanced in Social Network Analysis and Mining (ASONAM), 2012,IEEE/ACM International Conference on Pages, 1071-1078.
- M.R.Khoyyambashi, F.S.Rizi, "An Approach for Detecting Profile Cloning in Online Social Networks", e-commerce in developing countries: with focus on e-security (ECD), 2013 7th international conference, and pp.1-12.
- G.Kontaxi, I.Polakis,S.Ioannidis, and E.Markatos, " Detecting Social Network Profile Cloning" in previous computing and communications workshops (PERCOM workshops), 2011, IEEE International Conference on IEEE, 2011, PP.295-300.
- R.Baden, N.Spring,and B.Bhattachorjee, "Identifying Close Friends on the Internet," in Proc. Of workshop on hot Topics in networks (HotNets-VIII), 2009.R.Baden, N.Spring,and B.Bhattachorjee, "Identifying Close Friends on the Internet," in Proc. Of workshop on hot Topics in networks (HotNets-VIII), 2009.
- M.Fire, G.Katz, and Y.Elovici, " Strangers Intrusion Detection_Detecting Spammers and Fake Profiles in Social Networks Based on Topology Anomalies"2012, http:/www.academia.edu/1518357/ strangers_ Intrusion _Detection_Spammers_and _Fake_Profiles_in_ Social_Networks_ Based_ on_Topology_Anomalies.
- K.Lee, J.Caverlee, and S.Webb, "Uncovering Social Spammers:Social HoneyPots+ Machine Learning" in Proceeding of the 33rd International ACM SIGIR Conference on Research and Development Information Retrieval, ACM, 2010,PP. 435-442.
- L.Jin, H.Takabi, and J.B.D.Joshi, "Towards Active Detection of Iddentity Clone Attacks on Online Social Networks" Proceedings of the first ACM Conference on Data and Application Security and Privacy,NewYork USA,2011,PP.27-38.
- A.Singh, A,H.Toderici, k.Ross, and M.Stamp, "Social Networking for Botnet Command and Control",MECS, I.J.Computer Network and Information Security,2013, 6,pp 11-17.
- J.Gross, and J.Yellen, "Hand Book of Graph Theory" CRC Press LLC 2004,PP.253-256.


