A fuzzy-based adaptive energy efficient load distribution scheme in ad-hoc networks
Автор: Varun Kumar Sharma, Lal Pratap Verma, Mahesh Kumar
Журнал: International Journal of Intelligent Systems and Applications @ijisa
Статья в выпуске: 2 vol.10, 2018 года.
Бесплатный доступ
The traditional energy aware routing policies are not capable enough to keep up with dynamic properties of mobile ad-hoc network (e.g., mobility, quick topology changes, link-layer contentions etc.) and do not offer adequate performance in high congested situations. In past decades, authors have expressed their concerns towards smart routing paradigms concerning lesser energy consumption. However, many of these proposals are not able to offer significant performance concerning the quality of service. Consequently, the pattern of interest shifts towards cross-layer energy optimization schemes. These proposals did use of lower layers’ special information and provide significant performance enhancements. Still, many of the issues are associated with these proposals. Moreover, many of the proposals consider idle and sleep power consumption which too causes a considerable amount of energy consumption. Nevertheless, these methods require complex synchronization and efficient coordination which is too inefficient for extremely variable networks (MANETs). To address these issues, we propose an effective fuzzy- based energy efficient load distribution scheme which takes care of energy consumption considering congestion as a parameter. In comparison with some of the existing energy aware routing strategies, proposed method offers substantial improvements in terms of total energy consumption, network lifetime, total number of dead nodes, and average throughput.
Ad-hoc Networks, Routing, Energy Efficiency, Energy Optimization, Fuzzy System, Congestion
Короткий адрес: https://sciup.org/15016463
IDR: 15016463 | DOI: 10.5815/ijisa.2018.02.07
Текст научной статьи A fuzzy-based adaptive energy efficient load distribution scheme in ad-hoc networks
Published Online February 2018 in MECS
In recent years, growing demands of advanced user has led to the outburst in advancements of wireless communication technology. With the proliferation of advanced computing technologies such as smart phones, laptops, and tablets have led the requirements of a contemporary user to a significant level. However, innovative computing trend insists availability of ample amount of resources such as energy, memory, and processing power [1] [53] [56]. Consequently, these rapid advancements in wireless technology have led to the development of intense heterogeneous traffic (e.g., video, images, and audio). Mobile Ad-Hoc Networks (MANETs) relies on the standard of decentralized architecture and has no infrastructure support [2] [46] [60]. Additionally, mobility support makes MANETs highly functional in tactical and defense applications [3]. In MANETs, wireless nodes proceed both as an end node (source or destination) and router node which carries forward the data on the behalf of others [4] [60]. However, these wireless nodes operate over small, low powered battery devices. Moreover, maintaining network performance, with the heavy traffic in MANET is complicated because of these battery constrained devices. With the aim of keeping the performance of a network, routing is a key and a leading factor that should be taken care off for designing an energy-aware routing strategy [50]. Smart routing leads to better utilization of energy-rich nodes, improves the overall power consumption, and so does the performance concerning lifetime of a network [5-7] [1420] [58] [59]. In recent years, there has been an extensive amount of work done regarding energy-aware routing for both static and dynamic MANETs. Moreover, their primary motivation is to keep running the network as long as it’s potential. It can be accomplished by efficient utilization of node’s available energy during forwarding and when they are inactive as well. Additionally, energy-aware routing is a vital design factor for such a power constraint networks (MANETs). Power failure of an individual node does have an adverse effect not only its performance but, significantly affects it’s forwarding capability on behalf of others, and so does the network’s lifetime [8] [51] [54] [55] [59]. The selected energy- aware route should be more stable concerning control flooding of broadcast packets and control MAC retransmissions which offer optimality regarding power consumption [9-11]. However, the stability of a path (regarding energy utilization) should provide an adequate level of quality service to the users. Otherwise, degraded performance (concerning the quality of service) decreases the reliability of a network to a great extent. Hence, there must be an appropriate balance between energy consumption and superior quality of service [12]. Moreover, many of the emergencies based dynamic ad-hoc networks which are both energy and bandwidth constrained in nature require a significant amount of attentions for designing energy-aware forwarding strategy by considering both aspects as mentioned above [13].
Moreover, the idea of joint cooperative communication (CC) is significantly helpful in designing energy competent forwarding strategies in a wireless network, in which end node act as a collaborative node to other and share the resources efficiently. However, the previous studies in CC are based on uncomplicated three nodes scenarios (sender, intermediate, and receiver) together with the assumption of idle MAC, which effectively coordinates the resources among them. However, there is an absolute decline in benefits offered by CC because of conventional upper layer protocols designed for noncooperative systems [28-30].
-
A. Motivation
Contention based and contention free protocol schemes are two basic strategies that come under cooperative MAC. The contention based protocol (IEEE 802.11 distributed coordination function (DCF) [31]), extensively used in ad-hoc networks because of its less sophisticated features (as it does not need complex synchronization and coordination, which does in a contention free protocols). However, in [33], the authors observed that idle state of a node is equally treated (concerning power consumption) likewise as in the on state because IEEE 802.11 MAC has enormous and identical power consumption in both mentioned states. Moreover, many of the proposals [20] [21] [23] [24] [26] [52] consider a significant amount of energy wastage during idle and sleep state, and proposed diverse strategies to cope up with the higher energy wastage effectively. However, some of the proposals [15-18] based on the energy-aware routing schemes, in which intense transmissions forwarded through high powered battery devices. Moreover, the strategies proposed in [23] [24] purely designed for wireless sensor networks (WSN), generally sensor nodes are idle and sleep for a longer period and awakened (either periodically or for transmitting a small packet) only for the shorter duration of time. Hence, achieving maximum possible utilization of a channel is merely not important in WSNs, which results in an inferior quality of services. However, ensuring maximum channel usage together with minimum power consumption is the challenging issue in wireless mobile ad-hoc networks (MANETs). Additionally, the proposed energy-aware strategies [1517] do not offer well-balanced energy level in the system because of their abrupt forwarding scheme. In our previous work [46], we have given an efficient traffic rate regulation policy by appropriately classifying diverse reasons for packet losses. Specifically, we have made major congestion contributors to adjust their transmission policy. We have used adaptive MAC retransmission strategy for local level traffic rate adaptation. In addition, we have controlled congestion globally, by sending congestion notifications in an efficient manner. Subsequently, in this paper, we have studied the effects of adaptive MAC retransmission strategy on energy consumptions of a wireless node. Moreover, we have also effectively utilizes the current energy level for suitably classifying the current status of a node (concerning energy level) by using fuzzy inference system and distribute the load on energy rich nodes efficiently.
The remaining paper is organized as follows: Section II presents the literature study of energy aware routing schemes. Section III presents the problem definition. Section IV presents the design and implementation of the proposed method. Section V shows the simulation setup and parameters. Section VI presents the experimental results and Section VII concludes this work.
-
II. Related Work
Singh and Raghavendra [21] proposed an energy efficient protocol called Power Aware Multi-Access Protocol with Signaling (PAMAS) based on Multiple Access with Collision Avoidance (MACA) [22]. The PAMAS has incorporated a new signaling mechanism over MACA. The idea is to turn nodes into the sleep state when they are not transferred or relaying packets. However, the authors in [21] do not consider the node’s idle state listening which too consuming the significant amount of power. Ye et al. [23] [24], proposed sensor MAC (S-MAC) protocol, in [23], an efficient mechanism were suggested to reduce the overhead of idle listening by using periodic awake and sleeping mechanism. In [24], the authors further improved their proposed approach by effectively coordinating the sleeping schedules with synchronized neighbors to reduce the control overhead and latency. In [23], the period of sleep is fixed which leads to high latency in system, hence, in [24], authors proposed an adaptive listening mechanism to overcome the problem of high latency in the network. Dam and Langendoen [45], extends S-MAC, and recommended timeout MAC (T-MAC), the authors’ primary motivation is to reduce the idle listening efficiently. Moreover, their idea is compelling under variable load conditions. There is another approach called Piconet [25] based on the periodic sleeping mechanism likewise in S-MAC. In IEEE 802.11 DCF, the power saver mode is originally designed for the 1-hop network. Simple and less sophisticated synchronization system is the primary objective behind the design of the single hop network [24]. However, Tseng et al. [26], observed the problems of aforementioned saver mode concerning neighbor discovery, and clock synchronization. In [8], a thorough survey has been accomplished regarding energy conscious routing strategies in MANET. They classify different energy aware routing strategies by load distribution, transmission control, and sleep power down approaches. The particular idea of load distribution approach concerns with a well-balanced utilization of energy-rich nodes in the network. It should not be the case of overutilization of some specific nodes in the network and causes route disconnections. However, the aforementioned energy-aware routing strategy leads to longer routes and causes higher average end-to-end delay. Woo et al. [27], proposed LEAR protocol based on localized information. The nodes in LEAR decide whether to take part in the route discovery process or not. The decision depends on the localized residual energy threshold, and it transfers the load over high powered battery devices. Ye et al. [32] proposed an adaptive sleeping based protocol called probing environment and adaptive sleeping (PEAS); they dynamically classify the set of working and non-working sensor nodes. The approach increases the lifetime of a network by turn off the radio state for non-working sensor nodes. Zhao et al. [34], proposed cross-layer based adaptive MAC level retransmission scheme [35] to improve the performance of DSR network routing protocol over wireless mesh networks. The multiple metric such as node’s traffic load, the frame transmission efficiency, offered bandwidth are acting as a basis for obtaining an ideal path for transferring data. The proposal adopts its MAC retransmission scheme, according to the reward that is dynamically calculated corresponding to a route. Miller and Vaidya [44] proposed two radio channel based rate estimation MAC with the purpose of efficiently scheduling the wake-up state for the neighbors. However, the method entirely relies on the use of second radio which unnecessarily increases the hardware cost. Moreover, the idea of explicitly waking up the neighbors offers more complexity to the network. Meng et al. [47] have proposed a multi-agent based discovery system to come across comprehensive microgrid information. Their given discovery system offers usefulness concerning efficient broadcasting state policy. This policy subsequently helps in minimizing the overall exchange of data. Yang et al. [48] have given an optimal sensor coordination policy to enhance target tracking accuracy. They improved tracking system’s accuracy by designing a coordination policy between sensors, which includes both sensor motion and their optimal selection. Zhang et al. [49] introduced efficient denial of service (DoS) attack scheduling policy, considering inadequate energy availability at attacker’s side. Their objective is to schedule DoS attack which maximizes the attacking effects on the wireless networked control system.
-
III. Problem Definition
In [15-17], the authors introduced the concept of energy level based routing, ELBRP, classifies energy level of the nodes according to their available energy. The node energy level classification adopted in four phases (I).Safe Phase (II).Sub-Safe Phase (III).Danger Phase and (IV).High Danger Phase. In addition to this, the approach uses the requested delaying mechanism for calculating the route. However, the approach only adopts the delaying mechanism for sub-safe phase nodes and turn their radio state off for the high danger phase nodes. But the proposals mentioned above do not consider the individual classified node energy level and adopts the forwarding accordingly. If safe phase ranges from 100-50 (available energy (%)), the approach avoids the approach of delaying the route request (RREQ) packet. However, the idea of taking similar consideration (avoiding delaying mechanism) between the nodes whose available energy is approximately 95 % and those whose available energy is around 55 % (but both nodes belong to safe phase) is not up to the mark. The scheme of using the same forwarding strategy within an individual classified energy level reduces the possibility of better-balanced energy level and also equalized their (95 and 55 % available energy node) probability of inclusion in route discovery phase in the network. Moreover, ELBRP uses a simple forwarding mechanism (likewise in AODV routing strategy) when the nodes are in danger phase. Hence, there has a possibility of the inclusion of danger phase nodes instead of sub-safe nodes in the route construction phase. It causes over-utilization of danger phase nodes while; some of the available sub-safe nodes underutilized and leads to the unbalanced energy level in the network. In addition to the flaw as mentioned above, ELBRP does not take care of power consumption while data transmission is taking place. There’s a possibility that initially discovered route could be disconnected either because of dead nodes and link failures which result in the low performance of a network.
-
IV. The Proposed Solution
The primary objective of the proposed method is to well utilize those nodes which are affluent concerning their current available energy for better-balanced energy level in the network. Additionally, with the purpose of better-balanced energy level together with curtailing down the possibility of the inclusion of the lower energy level node in route construction phase, the proposed method, considers the delaying mechanism for every range of classified energy levels. For practical classification purpose, we have used the fuzzification method. The proposed method has focused on designing the routing strategy in such a way that, energy-rich nodes should always be the part of a route, considering MAC layer’s retransmission as a parameter and current radio state of a mobile node. Moreover, the proposed method also considers congestion as a parameter and adapts the MAC retransmission rate accordingly for every range of classified energy levels. While, for danger and high danger phase nodes, the proposed method turn off their radio state accordingly as discussed in further Sec. IV (E) in detail. Moreover, the proposed method also adapts according to the currently available energy of a node while intense data transmission is taking place. It also bifurcates the transmission load dynamically over other energy-rich nodes.
-
A. Analyzing the Effects of MAC Retransmissions over Total Energy Consumption
This sub-section shows the effects of MAC retransmissions over total energy consumption in the network. According to the wireless communication standards such as IEEE 802.15.4 and 802.11, the receiver transmitted an acknowledgment packet to the sender on each successful reception of a unicast data packet. If it fails to receive an acknowledgment, it simply retransmits the packet. It could be either because of the loss of a unicast or acknowledgment packet in the network. The IEEE 802.11 performs the link layer retries before dropping a packet by implementing ARQ (Automatic Repeat Request) scheme. These data packets retransmitted at a maximum of retransmissions specified by the MAC layer. These frequent packet losses are due to nature of a wireless channel and buffer overflow (congestion). Moreover, the wireless channels are highly susceptible to channel errors because of wireless channel fading, or its wireless circuitry compared to the wired channels. Hence, each packet transmission and reception causes the significant amount of energy consumption in network either because of its single or multiple transmissions in the network. The energy consumption calculated by the help of the Eq. (1) presented as follows [15] [36]. In Eq. (1), “ Ene i ” represents energy consumption of a node “ i ”, “ Pow i ” represents either transmitting or receiving power of a node “ i ” and “ Time i ” represents either transmitting or receiving time of a node “ i ”.
Enet = Pow8 * Timet (1)
The transmissions, receiving, idle, and sleep, energy consumption of a node “i” is shown in Eq. (2-5) [36]. The node “i” consumes “PowTx(i)” power in transmitting UDP segments, “PowRx(i)” power in receiving UDP segments or MAC ACKs, “PowIdle(i)” power for waiting for UDP segments or MAC ACKs.
EneTx (i) = PowTx (i) * TxTimei
EneRx (i) = PowRx (i) * RxTimei(3)
EneIdie (i) = PowIdle (i) * IdleTimei(4)
EneSleep (i ) = PowSleep (i)* SePTme,
The idle time of a node “ IdleTimei ” is calculated as in Eq. (6). While, the total time of UDP connection is “ TimeTotal ”. Hence, the total power consumption “ Pow_Cons Total (W) ” for a UDP connection is shown in Eq. (7) [37] presented as follows.
IdleTime, = Tim^ ( i ) i ) - RxTimej - TxTime, (6)
Pow _ Cons Total(W ) = Eneidle ( i ) + EneTx ( i ) + EneRx ( i ) + Enesleep ( i ) (7)
It is quite noticeable that total energy consumption is directly dependable on above mentioned parameters in Eq. 7, followed by Eq. 1-6. More the number of retransmissions more will be the total energy consumptions in the network. We have simulated a network as discussed in Sec. V, and calculate the amount of energy consumed at each MAC retransmissions, as shown in Fig. 1. The total energy consumption is continuously decreasing as the retransmission decreases. At initial energy (11 J), the average energy consumption is approximately 206.50 J at retransmission count “7”. While it is around 196.82 J at retransmission count “1”. The similar effects also observed for other two initial energy cases (10 and 9 J).
-
B. Selecting the Energy Affluent Nodes for Forwarding Traffic
The proposed method selects the energy-rich nodes by using the requested delaying mechanism [15-17]. During the route discovery phase, each node (despite those, which are having an available route to the destination or they itself are the destination nodes) according to their possible energy level delayed the RREQ packet. The holding delay is inversely proportional to currently available energy of a node according to the Eq. (8) presented as follows.
RREQ“ a a V Ene Nolble (8)
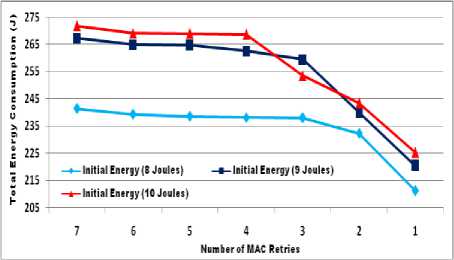
Fig.1. MAC retransmissions effect over total energy consumption.
The higher available energy leads to lesser RREQ packet delay. The idea motivates this delaying of RREQ packet; each node only accepts the earlier RREQ packet and discards the later ones. Hence, those nodes which are having the lesser available energy level hold the RREQ packet for a longer period, and the possibility of their inclusion in the route is very less. Finally, a path is constructed with higher energy nodes in the network. As far as delay is concerned, in IEEE 802.11 DCF standard, a transmitted packet has influenced by the number of delays associated with each node in the network. These delays are (I).Carrier sense delay (II).Back off delay (III). Transmission delay (IV).Propagation delay and (V).Queuing delay [23] [24]. Apart from these delays as mentioned above, an additional delay is requested delay, experiences by the RREQ packets, and periodic sleeping delay experienced by all the packets in the proposed method.
-
C. Fuzzy based Energy Classification Scheme
The proposed method classifies the current status of a node according to their available energy level by using the fuzzy method. This classification done in three energy levels: [1, α], [α, β] and [β, 0] called safe phase, danger phase, and high danger phase respectively. Where, α is first energy level and β, is the second energy level as shown in Algorithm EnergyAwareForwarding. The proposed method uses the delaying mechanism for every range of classified energy level for better-balanced energy level as mentioned earlier. The proposed method uses the fuzzy based energy classification scheme for adaptive route maintenance and load distribution scheme as discussed in further Sec. IV (F). The fuzzy thresholding applied to the available energy of nodes that are actively participating in forwarding the packets. The proposed energy classification scheme utilizes the fuzzy inference system [38], classifies the current status of a node (regarding currently available energy) more accurately. For a fuzzy system, we have used these three fuzzy sets [1, α], [α, β], and [β, 0]. These sets are used with “currently available energy” as a linguistic variable to describe the status of a node “ni”, defined as, safe phase, danger phase, and very high danger phase. The numerical variable “currently available energy”, varied between the numbers 0-100 (%) (Universe of discourse is “currently available energy”) are called as a base variable for aforementioned linguistic variable [39] [57]. These aforementioned fuzzy sets depicted through a membership function. It constructed from the set of energy input values of the variable. The degree of membership (μ) varied between interval [0, 1] and it is associated corresponding to each energy input value. The membership value defines, how firmly an input value describes the variable. If it is one, input values adequately specify the variable, and it is a perfect member corresponding to a fuzzy set. If it is zero, input value does not belong to a fuzzy set at all. Otherwise, the membership value between zero and one denotes the degree of belongingness to a particular fuzzy set. Three trapezoidal membership functions depict the “currently available energy”. This membership function is specified by four parameters (a, b, c and d) as shown in Eq. (9). We have essentially used the trapezoidal fuzzy membership function because this function gives the more appropriate classification results concerning the currently available energy in the proposed method compared to other available fuzzy membership functions. However, we have tested our proposed method by considering the triangular membership function as well, but, the appropriateness in the classification (as the vagueness is more) is not up to the mark as compared to trapezoidal fuzzy membership function. Consequently, we consider trapezoidal fuzzy membership function that well affects the energy-aware forwarding capability of the proposed method.
f O
Ene Ava ( i ) < a
( Ene Ava ( i ) - a )/( Ь - а ) a < Ene Ava ( i ) < Ъ
Trapezoid ( EneAv„ ( i ) : a , Ь , c , d ) = < 1
Ь < Ene Ava ( i ) < c
( d - Ene Ava ( i ))/ ( d - c ) c < Ene Ava ( i ) < d
Ene Ava ( i ) ^ d
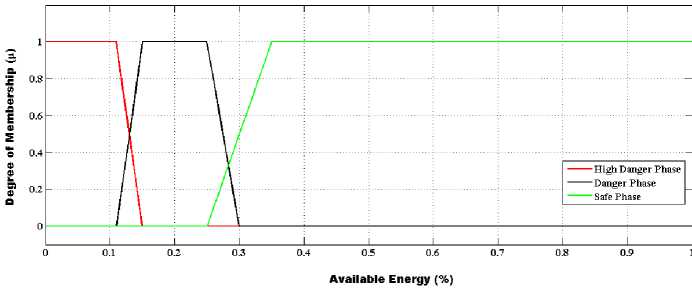
Fig.2. Output membership function indicating state of a node
-
D. Cross Layer Adaptive MAC Retransmission Scheme (Adaptive MAC ReTx)
The output membership function (shown in Fig.2), accurately defines the current status of a node. As the route constructed through a requested delaying mechanism (mentioned in Sub-sec. B), use for intense data transmissions over the network. In this paper, we have considered congestion at the local level (at every node) and adapt the MAC retransmission rate accordingly.
The proposed method monitors each packet dropping event. If it is because of reason buffer overflow, the drop queue information module (DQIM) monitors and calculate the current congestion intensity level. If current congestion intensity level is more than a specified congestion threshold “ dropThresh ” as shown in Algorithm MAC_ReTx, the DQIM passes this information into ARxM (Adaptive Retransmission Scheme) for dynamic adaptation of MAC level retransmissions for controlling congestion and avoid unnecessary energy consumption at
|
the local level as shown in Fig. 3. Otherwise, there is no |
5: |
drop(p); |
|
need to adapt the retransmission rate. |
6: |
// Congestion intensity level |
|
7: |
If CI Level > drop Thresh (P) Then |
|
|
Algorithm: MAC_ReTx(Packet P, drop Thresh , |
8: |
MAC_Rx Count = MAC_Rx Count -1; |
|
MAC_Rx Count , CI Level ) |
9: |
Else Then |
|
Begin: |
10: |
MAC_Rx Count = MAC_Rx Count +1; |
|
1: // For incoming packet at data-link layer |
11: |
End If |
|
2: If type (p) == Application Then |
12: |
End If |
|
3: // Condition for queue-overflow and packet drop from |
13: |
End If |
|
queue |
End |
4: If Queue Cur_Len ≥ Queue Len (max) Then
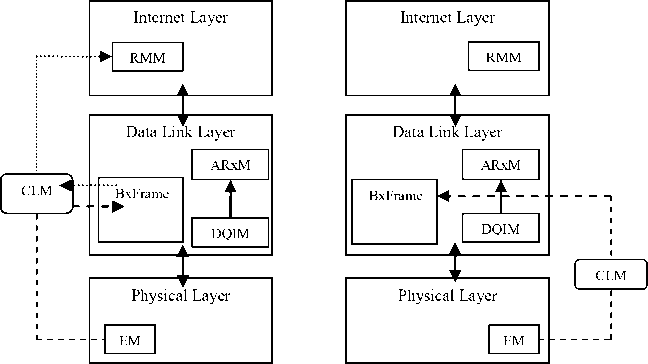
Fig.3. Cross layer adaptive retransmission and load distribution scheme.
-
E. Adaptive Sleeping by Overhearing Avoidance for Danger Phase Nodes
In this subsection, we have dynamically adapted the forwarding scheme according to the availability of energy-rich nodes in the network. The design of MAC retransmission adaptation (as discussed in Sec. IV (D)) adopted for all classified range of energy levels belonging to a node. Moreover, the proposed approach considers idle and sleep energy consumption similarly as in PAMAS [21] and S-MAC [23] [24] protocol. However, these energy consumptions are only considered for the danger and high danger phase nodes in the proposed method. It considers the overhearing avoidance and adaptive listening [21] [23] [24] mechanisms to reduce the unnecessary power consumption in the network.
To overcome the problem of collision the contentionbased MAC protocols adapts according to their contention adaptive channel access policy. In IEEE 802.11, the nodes keep on overhearing the neighbor’s traffic to compel a powerful virtual carrier sense, causes a significant amount of energy consumption in the network. In MANETs, the idea of overhearing (keep on listen to the traffic which not intended to itself) packets is advantageous because some of the routing strategies rely on gathering the local (neighbor) information, some information required for maintaining and monitoring the network’s status. However, the idea of overhearing as mentioned above causes more power consumption and it is not helpful in the high energy-constrained networks. The proposed approach efficiently exploits the concept of overhearing avoidance (inspired by PAMAS and S-MAC protocol). The danger phase classified interfering nodes shut down their radio after hearing the short RTS and CTS control packets. The overhearing of long DATA packets with its acknowledgment (ACK) causes the significant amount of energy wastage. Hence, instead of overhearing the long DATA packets, nodes turn their state from active to sleep state and conserve the considerable amount of energy. Moreover, duration of the sleeping state entirely depends on the amount of time in duration field in RTS packet. The nodes on receiving RTS packet update their network allocation vector (NAV) on the basis of duration field. That duration states about “how long the current transmission is to be?”, hence, the node scheduled their sleeping period accordingly called adaptive sleeping mechanism. Otherwise, the nodes keep on sending traffic (likewise as safe phase nodes) until their NAV is not set as shown in Algorithm OverhearingAvoidance.
Algorithm: OverhearingAvoidance (Packet P, curr_time, nav_, state_, overhear_avoid)
Begin:
-
1: // For each receiving RTS/CTS packets
-
2: If p.dst ≠ node_id Then
-
3: nav_= P.duration();
-
4: If curr_time + nav_ > nav_ Then
-
5: nav_= curr_time + nav_;
-
6: End If
-
7: // Check current status of a node
-
8: If state_== IDLE || state_== Carrier_sense
Then
-
9: sleep();
-
10: overhear_avoid = TRUE;
-
11: End If
-
12: End If
End
Algorithm: EnergyAwareForwarding (First_ene_level
(α), Second_ene_level (β), Curr Ene , E Initial , default Delay )
Begin:
-
1: // Energy level classification in EM of Physical Layer
-
2: α = EM() → level1();
-
3: β = EM() → level2();
-
4: // Current level of Energy Left
-
5: curr_ene_level_left = Curr Ene /E Initial ;
-
6: // Requested delay function of ELBRP
-
7: modify Delay = default Delay + (5/Curr Ene +5);
-
8: //Modified forwarding strategies
-
9: //Fuzzy classification (safe phase nodes)
-
10: If curr_ene_level_left ≤ 1 && curr_ene_level_left
≥ α Then
-
11: forward(modify Delay ); // RREQ Packets
-
12: // For incoming Packet at Data-link layer
-
13: If type(P) == broadcast_frame (P) Then
-
14: // Update neighbor’s state table
-
15: Insert_StateTable();
-
16: End If
17: End If -
18: // Fuzzy classification (danger phase nodes)
-
19: If curr_ene_level_left≤ α && curr_ene_level_left
≥ β Then
-
20: forward(modifyDelay); // RREQ Packets
-
21: // For incoming Packet at Data-link layer
-
22: If type(P) == broadcast_frame (P) Then
-
23: // Update neighbor’s state table
-
24: Insert_StateTable();
-
25: End If
-
26: // Start overhearing avoidance
-
27: OverhearingAvoidance(P);
-
28: // Fuzzy classification (high-danger phase nodes)
-
29: If curr_ene_level_left≤ β && curr_ene_level_left
≥ 0 Then
-
30: forward(modifyDelay); // RREQ Packets
-
31: // Notify current state to neighboring nodes
-
32: send(broadcast_frame);
-
33: // For incoming Packet at Data-link layer
-
34: If type(P) == broadcast_frame (P) Then
-
35: // Update neighbor’s state table
-
36: Insert_StateTable();
-
37: End If
-
38: // Start periodic sleeping and overhearing
avoidance
-
39: If overhear_avoid == TRUE Then
-
40: OverhearingAvoidance(P);
-
41: Else Then
-
42: sleep(); // Periodic sleep
-
43: End If
-
44: End If
End
-
F. Cross Layer Adaptive Load Distribution Scheme
In this subsection, we have proposed an approach that dynamically distributes the traffic load over other energyrich nodes, if a current forwarding traffic node belongs to high danger state. The DQIM, BxFrame (Broadcast Frame Module), and ARxM incorporated at data-link layer. RMM (Route Maintenance Module) included at the internet layer. EM (Energy Module) included at the physical layer and CLM (Cross-Layer Module) for passing dynamic information are the proposed modules. The high danger phase node notifies all of its neighbors about its current state by the help of BxFrame; for sending a broadcast packet (as shown in structure broadcast_frame) for the neighboring nodes as shown in Fig. 3. After receiving the broadcast packet, the neighbor nodes update their neighbor state table with the help of Algorithm Insert_StateTable (with an assist of structure neighbor_state). The idea for maintaining the state table is to keep track of high danger phase neighboring nodes. If the status of a neighboring node turns from danger to high danger phase, it notifies about its state to their neighboring nodes. The neighboring nodes update their aforementioned state table and the previous neighboring node dynamically distributes their traffic load over other energy-rich nodes (if available). For adaptive load distribution, the proposed method relies on the local route maintenance scheme (originally implemented in AODV [40] protocol) that bypasses high danger phase node with the help of RMM. Moreover, in proposed approach, high danger phase nodes turn off their radio state periodically. If they overhear some neighbor transmission, they just adopt the mechanism of overhearing avoidance (likewise as danger phase nodes). They take part in forwarding process only in the case, when no other energy-rich nodes are available in the network as shown in Algorithm EnergyAwareForwarding.
struct broadcast_frame struct neighbor_state
{ { int length; int node_id;
int type; structbroadcast_frame Bx_Frame;
int req_num; }; neighbor_state int src_addr;
int state;
};
// Algorithm for inserting neighbor state table entries maintained by each node in network
Algorithm: Insert_StateTable (size (MAX), curr_size=0, node_id, req_num, structbroadcast_frame Bx_TxFrame) Begin:
-
1: // Initialize neighbor table
-
2: For curr_size < size (MAX) {
-
3: neighbor_state[curr_size].node_id =0;
-
4: neighbor_state[curr_size].req_num =0;
-
5: neighbor_state[curr_size].Bx_TxFrame .state=0;
-
6: }
7: End For -
8: // Update neighbor table
-
9: For curr_size < size (MAX) {
-
10: neighbor_state[curr_size].node_id =
Bx_TxFrame.src_addr;
-
11: neighbor_state[curr_size].req_num=
Bx_TxFrame.req_num;
-
12: neighbor_state[curr_size]. neighbor_state.state=
13:End ForEnd
V. Simulation Setup and Parameters
The performance of the proposed method, ELBRP and the AODV approaches are evaluated via ns-2 simulator [36]. The transmission and interference range of each wireless node is 250 m and 550 m respectively, while, the effective distance is not more than 230 m among neighbor nodes. Consequently, wireless nodes can only communicated with their direct neighbors. As far as for simulation purpose, we have assumed that the sender always have data for transmission during simulation phase. We have strictly followed all the IEEE 802.11 simulation parameters at both the data-link and physical layers. The wireless basic data rate is 1 Mbps and channel data rate is 2 Mbps. We have considered a random flatgrid topology of 1,200 * 1,200 m2 with both static and 60% moving wireless node (with a velocity of 15 meters/second). The maximum queue size is 50, and for reception and transmission purpose an omnidirectional antenna has been used with two-ray ground propagation model. The packet size is 210 bytes with a traffic sending transport agent is UDP with AODV as a network routing protocol. The considered congestion threshold “dropThresh” is 1 Packet/second for the evaluation purpose. Additionally, we have considered 2-4 concurrent interfering traffic flows passing through a wireless link with traffic flow rate of 2 Mbps. The simulation topology with 14 competing flows is shown in Fig. 4. The fundamental behavior of MAC and the physical layer is similar in the proposed, ELBRP and the AODV approaches, regardless of the proposed modules (DQIM, BxFrame, ARxM, and EM).
Fig.4. Simulation Topology.
-
A. Energy Parameter Setup
For the evaluation purpose, we have considered the Chipcon’s CC2420 2.4 GHz for IEEE 802.15.4 RF
transceiver radio parameters. The transmitting power “ PowTx ”, receiving power “ PowRx ”, sleep power “ Pow Sleep ”, and idle power “ Pow Idle ” are 31.32mW, 35.28mW, 144nW, and 712μW, respectively [41-43]. The simulated initial energy values are 2, 3, 4, 5, 6, 7, 8 and 9 Joule. The total energy consumption while transmission, reception, idle and sleep mode is according to the formulations as mentioned in Sec. IV (A).
-
VI. Experimental Results
This section illustrates the simulating results for AODV, ELBRP and the proposed method (Adaptive MAC ReTx, Adaptive Sleeping, and Adaptive Sleeping + Adaptive MAC ReTx). The obtained results have analyzed over total energy consumption, lifetime, and the total number of dead nodes in the network. To verify the effects of proposed adaptive MAC retransmission scheme (Adaptive MAC ReTx) individually, we have simulated a network (as earlier mentioned in Sec. V). Figs 5, 6 and 7 illustrate the results of total energy consumption, the total number of dead nodes (%), and throughput (Kbps) with the aid of discrete initial energy values in the network. Concerning the UDP traffic; we use the parameters as mentioned in Sec. V. As initial energy increases, total energy consumption increases too for all shown approaches in Fig. 5. The results are relatively better in proposed (Adaptive MAC ReTx) compared with AODV and ELBRP approaches. All of the approaches (AODV, ELBRP, and Proposed (Adaptive MAC ReTx)) run over 2 Mbps traffic rate (with 2 Mbps channel data rate (mentioned earlier in Sec. V)). AODV and ELBRP approach do not consider the adaptive MAC retransmission scheme (while buffer overflow event arises to a node) or handling congestion at the local level. The approaches are continuously sending the packet up to their maximum MAC retransmissions, causes the significant amount of energy wastage. At initial energy (2 J) case, the ELBRP, AODV and Proposed (Adaptive
MAC ReTx) approach offer same performance (considering average throughput (Kbps) as shown in Fig. 7). While total energy consumption and the total number of dead nodes in proposed (Adaptive MAC ReTx) is approximately 60 J and 57% respectively. Moreover, AODV offers, 64 J (total energy consumption) and 65% (total number of dead nodes). While ELBRP offers 63 J (total energy consumption) and 63% (total number of dead nodes). At initial energy (5-9 J) cases, the performance of proposed (adaptive MAC Retx) regarding average throughput (Kbps) relatively outperforms the AODV approach and offers the significant amount of better results compared to ELBRP approach, together with better energy consumption and the total number of dead nodes. The proposed (adaptive MAC Retx) method offers 276 Kbps (Average Throughput), AODV provides 245 Kbps and ELBRP offers 260 Kbps, which is approximately 13% and 6% better than AODV and ELBRP respectively. The average number of dead nodes in AODV and ELBRP is about 44% and 41% respectively, while, in proposed method (adaptive MAC Retx), it is around 39%. In addition to this, the average energy consumption is approximately 213 J in AODV, 211 in ELBRP, and 207 J in the proposed method (adaptive MAC Retx).
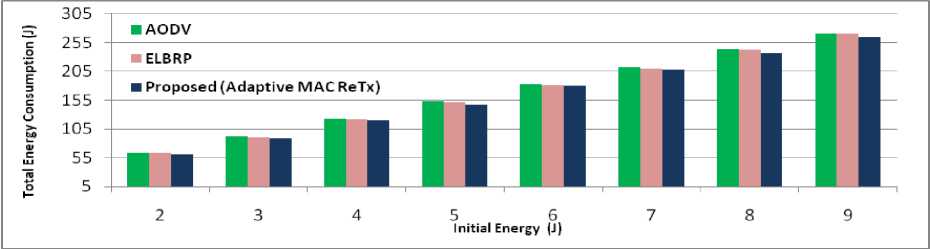
Fig.5. Total Energy Consumption (Joules).
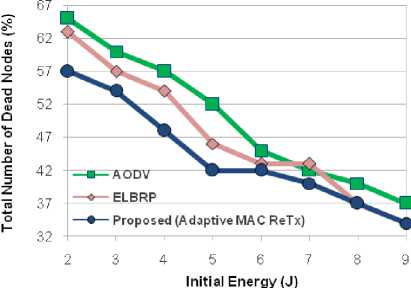
Fig.6. Number of Dead Nodes (%).
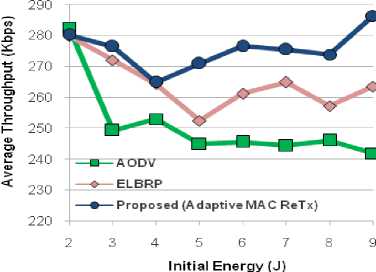
Fig.7. Average Throughput (Kbps).
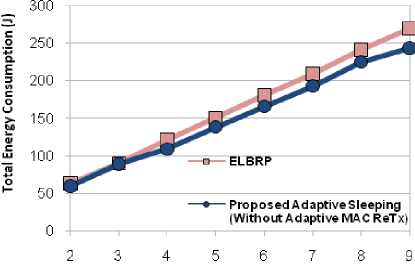
For simulated network as discussed in Sec. V, Figs. 8 and 9 show the total energy consumption (J) and the total number of dead nodes (%), by using adaptive sleeping mechanism. Here, with the intention of evaluating the individual effects of adaptive sleeping, we are not considering the adaptive MAC retransmission effects [as earlier mentioned in Sec. IV (D)]. The results are significantly better in the proposed adaptive sleeping compared to ELBRP, as ELBRP does not consider the danger phase nodes and adapt the same delaying policy of AODV protocol, while, the proposed approach uses the delaying mechanism for all classified range of nodes. Moreover, the proposed approach avoid the overutilization of danger phase nodes by well utilized the safe phase nodes (as their RREQ packet delay is very much lesser than danger phase nodes and the probability of their inclusion is very high compared to danger phase nodes). Figs.8-10 illustrates total energy consumption (J), the total number of dead nodes (%) and the lifetime (sec) of a network, the average energy consumption in ELBRP is approximately 166 J, while, proposed adaptive sleeping method, offers around 152 J as shown in Fig.8. The proposed method provides 9 % lesser utilization of available energy in the network. Moreover, an average number of dead nodes in ELBRP approach is approximately 47 %, while, it is around 23 % in proposed adaptive sleeping method as shown in Fig.9. Furthermore, the optimal sleeping mechanism for both danger and high danger phase nodes improves the network’s lifetime by 6 % in proposed method as shown in Fig. 10.
To better understand the performance of the proposed method, we merge both approaches as mentioned earlier (Adaptive MAC ReTx [referred to in Sec. IV (D)] and Proposed Adaptive Sleeping [referred to in Sec. IV (E)]). Therefore, total energy consumption (J), the total number of dead nodes (%) and the lifetime of a network (sec), and throughput (Kbps) in proposed method (Proposed (Adaptive MAC ReTx) + Proposed Adaptive Sleeping) is compared to both ELBRP and AODV approach. As the proposed method uses the modified forward delaying (as mentioned in Algorithm EnergyAwareForwarding in Sec.
IV (E)) mechanism for every level of energy classification leads to the better-balanced energy level in the network compared to ELBRP.
Initial Energy (J)
Fig.8. Total Energy Consumption (J).
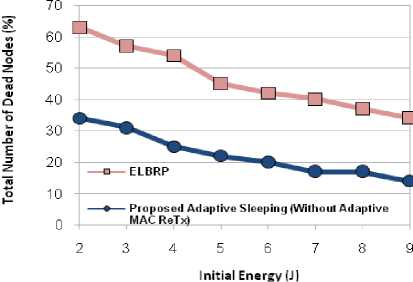
Fig.9. Total Number of Dead Nodes (%).
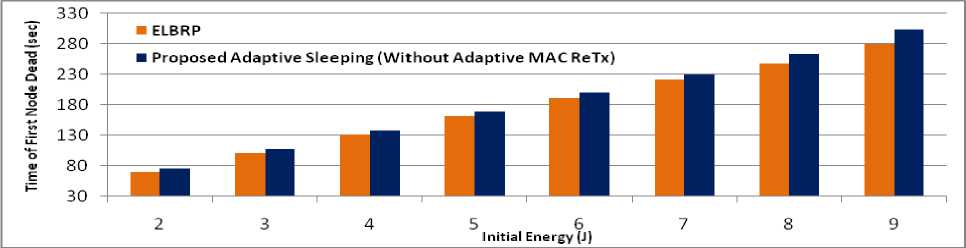
Fig.10. Lifetime of Network (sec.).
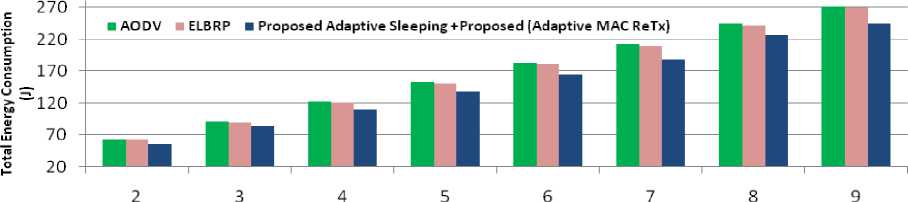
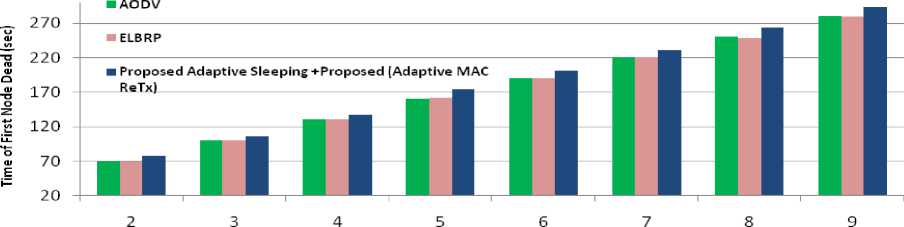
Moreover, the proposed approach also considers the mechanism of unnecessary overhearing and MAC retransmissions which cause significant amount of energy wastage. The mechanism of overhearing avoidance adopted for danger phase nodes in the network. The danger phase sleeping nodes are awakened after its NAV is set to zero (neighbor transmission is over) as mentioned in Algorithm OverhearingAvoidance in Sec. IV (E). While, in the case of high danger phase nodes, the nodes periodically off their radio and sets a timer (until when it sleeps), and then awakened only when the timer reaches to zero. Otherwise, if their periodic sleeping timer is not set, the nodes checks for neighbor transmission (overhearing avoidance) as mentioned in Algorithm OverhearingAvoidance in Sec. IV (E). Furthermore, ELBRP only adapts its forwarding strategy for safe-phase (despite high danger phase nodes) nodes. As it causes a high probability of the inclusion of danger phase nodes (despite sub-safe phase nodes) in the route construction phase leads to under-utilization of sub-safe phase nodes and causes unbalanced energy level in the network. In the case of AODV approach, there is no provision for energy aware routing and the approach relies on shortest path construction, causes maximum amount of energy consumption with the most number of dead nodes in the network as shown in Figs. 11-13. Fig. 11, depicts total energy consumption for all of the approaches, the average energy consumption in AODV is approximately 168 J, while, it is around 166 J and 151 J in ELBRP and proposed method respectively. The proposed method offers 11% and 9% lesser average energy consumption compared to AODV and ELBRP respectively. Furthermore, the optimal MAC retransmission and adaptive sleeping scheme improve the network’s lifetime by 6% (shown in Fig.12).While the average number of dead nodes in AODV is approximately 50%, around 48% in ELBRP and 22% in the proposed method.
-
VII. Conclusions
The majority of preceding energy aware approaches highlighted the benefits of routing through energy-rich nodes. However, routing through energy affluent nodes may not necessarily be the shortest path. Moreover, many of the previous approaches minimize the total energy consumption by considering the idle, sleep, and active communication energy expenditures. Thus, an appropriate complex synchronization based MAC protocol needed which effectively handles the abovementioned energy consumption parameters. In this paper, we have proposed an adaptive fuzzy based energy efficient load distribution scheme, which mainly focuses on minimizing the total energy consumptions considering congestion and the lower layer (MAC) parameters. Additionally, the proposed method classifies the current status of a node (either in safe, danger and high danger phase) and also handles the congestion at the local level and adapts the MAC retransmission rate accordingly. The proposed method considers the idle and sleeps energy consumptions for danger and high danger phase nodes. The simulation results show that the proposed method performed better as compared to ELBRP and AODV considering total energy consumption, total number of dead nodes, network’s lifetime, and average throughput.
Initial Energy (J)
Fig.11. Total Energy Consumption (J).
Initial Energy (J)
Fig.12. Lifetime of Network (sec.).
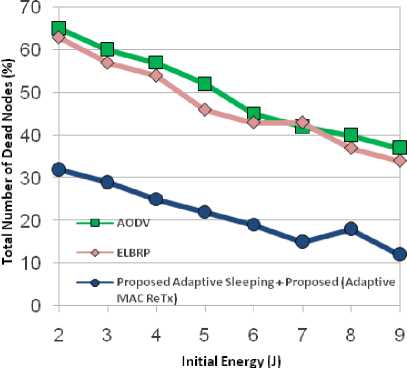
Fig.13. Total Number of Dead Nodes (%).
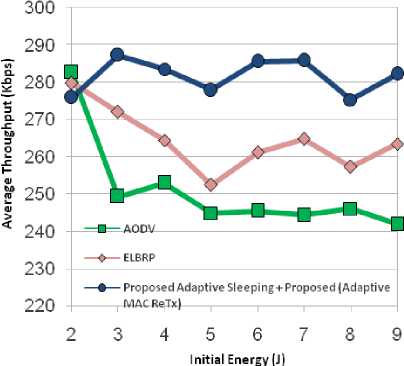
Fig.14. Average Throughput (Kbps)
Список литературы A fuzzy-based adaptive energy efficient load distribution scheme in ad-hoc networks
- O. G. Aliu, A. Imran, M. A. Imran, and B. Evans, “A survey of self organisation in future cellular networks,” IEEE Communications Surveys & Tutorials, vol. 15, pp. 336–361, Feb. 2013.
- S. Corson, and J. Macker, “Mobile Ad hoc Networking (MANET): Routing protocol performance issues and evaluation considerations,” RFC 2501, IETF Internet draft, Jan. 1999. https://tools.ietf.org/html/rfc2501 [Accessed on 04.06.14.].
- N. Pogkas, G. E. Karastergios, C. P. Antonopoulos, S. Koubias, and G. Papadopoulos, “Architecture design and implementation of an ad-hoc network for disaster relief operations,” IEEE Transactions on Industrial Informatics, vol. 3, pp. 63-72, Feb. 2007.
- J. M. Kim, and J. K. Jang, “AODV based energy efficient routing protocol for maximum lifetime in MANET,” In: Proceedings of Advanced International Conference on Telecommunications and International Conference on Internet and Web Applications and Services (AICT/ICIW), pp. 77-83, Feb. 2006.
- D. Feng, C. Jiang, G. Lim, L. J. Cimini, G. Feng, and G. Y. Li, “A survey of energy-efficient wireless communications,” IEEE Communications Surveys & Tutorials, vol. 15, pp. 167-178, Feb. 2013.
- L. Feeney, and M. Nilsson, “Investigating the energy consumption of a wireless network interface in an ad-hoc networking,” In: IEEE INFOCOM, pp.1548-1557, Apr. 2001.
- J. H. Chang, and L. Tassiulas, “Maximum lifetime routing in wireless sensor networks,” IEEE/ACM Transactions on Networking, vol. 12, no. 4, pp. 609-619, Aug. 2004.
- C. Yu, B. Lee, and H. Youn, “Energy efficient routing protocol for mobile ad-hoc networks,” Wireless Communication and Mobile Computing, vol. 3, pp. 959-973, Dec. 2003.
- F. D. Rango, F. Guerriero, and P. Fazio, “Link-stability and energy aware routing protocol in distributed wireless networks,” IEEE Transactions on Parallel and Distributed Systems, vol. 23, pp. 713-726, Apr. 2012.
- X. Wu, H. R. Sadjadpour, J. J. Garcia-Luna-Aceves, and H. Xu, “A hybrid view of mobility in MANETs: Analytical models and simulation study,” Computer Communication, vol. 31, pp. 3810-3821, Oct. 2008.
- Y. C. Tseng, Y. F. Li, and Y. C. Chang, “On route lifetime in multihop mobile ad-hoc networks,” IEEE Transactions on Mobile Computing, vol. 2, pp. 366-376, Nov. 2003.
- P.J.M. Havinga, and G.J.M Smit, “Energy-efficient wireless networking for multimedia applications,” Wireless Communication and Mobile Computing, vol. 1, pp. 165-184, Jan. 2001.
- G. Zussman, and S. Adrian, “Energy efficient routing in ad-hoc disaster recovery networks,” In: IEEE INFOCOM, pp.682-691, Mar. /Apr. 2003.
- J. H. Chang, and L. Tassiulas, “Energy conserving routing in wireless ad-hoc networks,” In: IEEE INFOCOM, pp.22-31, Mar. 2000.
- L. Li, C. Li, and P. Yuan, “An energy level based routing protocol in ad-hoc networks,” Wireless Personal Communications, vol. 81, pp. 981-996, Apr. 2015.
- L. Li, F. Zheng, C. Li, and P. Yuan, “An energy constrained routing protocol for MANET,” In: Proceedings of the Sixth International Conference on Machine Learning and Cybernetics, pp. 3205-3210, Aug. 2007.
- L. Li, C. Li, and P. Yuan, “An energy level based routing protocol in ad-hoc networks,” In: Proceedings of IEEE/WIC/ACM International Conference on Intelligent Agent Technology, pp. 306-312, Dec. 2006.
- J. Vazifehdan, R. V. Prasad, E. Onur, and I. Niemegeers, “Energy-aware routing algorithms for wireless ad hoc networks with heterogeneous power supplies,” Computer Networks, vol. 55, pp. 3256-3274, Jun. 2011.
- C. E. Jones, K. M. Sivalingam, P. Agrawal, and J. C. Chen, “A survey of energy efficient network protocols for wireless networks,” Wireless Networks, vol. 7, pp. 343-358, Jul. 2001.
- S. Singh, M. Woo, and C. Raghavendra, “Power-Aware Routing in Mobile Ad Hoc Networks,” In: MobiCom 98 Proceedings of the 4th annual ACM/IEEE International Conference on Mobile computing and networking, pp. 181-190, Oct. 1998.
- S. Singh, and C. Raghavendra, “PAMAS: Power aware multi-access protocol with signaling for ad-hoc networks,” ACM SIGCOMM Computer Communication Review, vol. 28, pp. 5-26, Jul. 1998.
- P. Karn, “MACA-A new channel access method for packet radio,” In: ARRL/CRRL Amateur Radio 9th Computer Networking Conference, pp. 134-140, Sep. 1990.
- W. Ye, J. Weidetnann, and D. Estrin, “An energy-efficient MAC protocol for wireless sensor networks,” In: IEEE INFOCOM, pp. 1567-1576, Jun. 2002.
- W. Ye, J. Weidetnann, and D. Estrin, “Medium access control with coordinated adaptive sleeping for wireless sensor network,” IEEE/ACM Transactions on Networking, vol. 12, pp. 493-506, Jun. 2004.
- F. Bennett, D. Clarke, J. B. Evans, A. Hopper, A. Jones, and D. Leask, “Piconet: Embedded mobile networking,” IEEE Personal Communication Magazine, vol. 4, pp. 8-15, Oct. 1997.
- Y-C Tseng, C-S Hsu and T-Y Hsieh, “Power-saving protocols for IEEE 802.11-based multi-hop ad hoc networks,” In: IEEE INFOCOM, pp. 200-209, Jun. 2002.
- K. Woo, C. Yu, H. Y. Youn, and B. Lee “Non-Blocking, Localized Routing Algorithm for Balanced Energy Consumption in Mobile Ad-hoc Networks,” In: Proceedings of International Symposium on Modeling, Analysis and Simulation of Computer and Telecommunication Systems (MASCOTS), pp. 117-124, Aug. 2001.
- M. Sami, N. K. Noordin, F. Hashim, S. Subramaniam, and A. Akbari-Moghanjoughi, “An energy-aware cross-layer cooperative MAC protocol for wireless ad-hoc networks,” Journal of Network and Computer Applications, vol. 58, pp. 227-240, Dec. 2015.
- A. Nosratinia, T. E. Hunter, and A Hedayat, “Cooperative communication in wireless networks,” IEEE Communication Magazine, vol. 42, pp. 74-80, Oct. 2004.
- Z. Weihua, and M. Ismail, “Cooperation in wireless communication networks,” IEEE Wireless Communication, vol. 19, pp. 10-20, Apr. 2012.
- IEEE standard for wireless LAN medium access control (MAC) and physical layer (PHY) specifications, ISO/IEC 802-11: 1999(E), Aug. 1999.
- F. Ye, G. Zhong, J. Cheng, S. Lu, and L. Zhang, “PEAS: A Robust Energy Conserving Protocol for Long- Lived Sensor Networks,” In: Proceedings of 23rd International Conference on Distributed Computing Systems (ICDCS’03), pp. 1-10, May 2003.
- M. Stemm, and R. H. Katz, “Measuring and reducing energy consumption of network interfaces in hand-held devices,” IEICE Transactions Communications, vol. E80-B, pp. 1125-1131, Aug. 1997.
- H-T. Zhao, Y-N Dong, H. Zhang, and Y. Li, “A Cross-Layer Routing Scheme Using Adaptive Retransmission Strategy for Wireless Mesh Networks,” Wireless Personal Communications, vol. 63, pp. 345-361, Aug. 2010.
- J. He, J. Yang, C. An, H. Liu, and X. Li, “Analysis on MAC Layer Retransmission Scheme in Wireless Networks,” In: Proceeding of the 6th ACM international symposium on Mobility management and wireless access, pp. 163-165, Oct. 2008.
- Home Page NS-2 Simulator Tool. http://www.isi.edu/nsnam/ns/, [Accessed on 04.12.14.]
- H. Singh, S. Saxena, and S. Singh, “Energy consumption of TCP in ad-hoc networks,” Wireless Networks, vol. 10, pp. 531-542, Sep. 2004.
- S. Guillaume, “Designing fuzzy inference systems from data: An interpretability-oriented review,” IEEE Transactions on Fuzzy Systems, vol. 9, pp. 426-443, Jun. 2001.
- L. A. Zadeh, “Fuzzy Sets,” Information and Control, vol. 8, pp. 338-353, Jun. 1965.
- C. E. Perkins, E. M. Royer, and S. R. Das, “Ad hoc on-demand distance vector (AODV) routing,”, RFC 3561, IETF Internet draft, July 2003. http://dl.acm.org/citation.cfm?id=RFC3561 [Accessed on 04.06.14.].
- B. H. Li, M. U. H. A. Rasyid, and H. K.Wu, “Analysis of super-frame adjustment and beacon transmission for IEEE 802.15.4 cluster tree networks,” EURASIP Journal on Wireless Communications and Networking, vol. 219, pp. 1-12, July 2012.
- AS Chipcon, SmartRF® CC2420 datasheet (rev 1.2) (Chipcon Corp, 2004).
- B. Gao, C. He, and L. Jiang, “Modeling and analysis of IEEE 802.15.4 CSMA/CA with sleep mode enabled,” In: International Conference on Communication Systems, pp. 6-11, Nov. 2008.
- M. J. Miller, and N. H. Vaidya, “A MAC protocol to reduce sensor network energy consumption using a wakeup radio,” IEEE Transactions and Mobile Computing, vol. 4, pp. 228-242, Apr. 2005.
- T. V. Dam, and K. Langendoen, “An adaptive energy-efficient MAC protocol for wireless sensor networks,” In: The First ACM Conference on Embedded Networked Sensor Systems (Sensys‘03), pp. 171-180, Nov. 2003.
- V. K. Sharma, and M. Kumar, “Adaptive congestion control scheme in mobile ad-hoc networks,” Peer-to-Peer Networking and Applications, vol. 10, pp. 633-657, May 2017.
- W. Meng, X. Wang, and S. Liu, “Distributed load sharing of an inverter-based microgrid with reduced communication,” IEEE Transactions on Smart Grid, Jul. 2016. [doi: https://doi.org/10.1109/TSG.2016.2587685]
- Z. Yang, X. Shi, and J. Chen, “Optimal coordination of mobile sensors for target tracking under additive and multiplicative noises,” IEEE Transactions on Industrial Electronics, vol. 61, pp. 3459-3468, Jul. 2014.
- H. Zhang, P. Cheng, L. Shi, and J. Chen, “Optimal DoS attack scheduling in wireless networked control system,” IEEE Transactions on Control Systems Technology, vol. 24, pp. 843-852, May 2016.
- K. Wang, T. Y. Chai, and W-C. Wong, “Routing, power control and rate adaptation: A Q-learning based cross-layer design,” Computer Networks, vol. 102, pp. 20-37, Mar. 2016.
- M. Akram, and T. H. Cho, “Energy Efficient Fuzzy Adaptive Selection of Verification Nodes in Wireless Sensor Networks,” Ad Hoc Networks, vol. 47, pp. 16-25, Sep. 2016.
- V. K. Sharma, S. S. P. Shukla, and V. Singh, “A tailored Q-Learning for routing in wireless sensor networks,” In: 2nd IEEE International Conference on Parallel, Distributed and Grid Computing, pp. 663-668, Dec. 2012.
- L. P. Verma, and M. Kumar, “An adaptive data chunk scheduling for concurrent multipath transfer,” Computer Standards & Interfaces, vol. 52, pp. 97-104, May 2017.
- S. P. Singh, and S. C. Sharma, “A particle swarm optimization approach for energy efficient clustering in wireless sensor networks,” International Journal of Intelligent Systems and Applications, vol. 6, pp. 66-74, Jun. 2017.
- Sivaraj C, Alphonse P J A, and Janakiraman T N, “Energy-efficient and load distributed clustering algorithm for dense wireless sensor networks,” International Journal of Intelligent Systems and Applications, vol. 5, pp. 34-42, May 2017.
- N. Arianpoo, and Victor C. M. Leung, “A smart fairness mechanism for concurrent multipath transfer in SCTP over wireless multi-hop networks,” Ad-hoc Networks, vol. 55, pp. 40-49, Feb. 2017.
- A. Amini, and N. Nikraz, “Proposing two defuzzification methods based on output fuzzy set weights,” International Journal of Intelligent Systems and Applications, vol. 2, pp. 1-12, Feb. 2016.
- L. Baccouche, and J. D. Rekik, “A QoS architecture for real-time transactions guarantee in mobile ad hoc networks,” Wireless Personal Communications, vol. 83, pp. 1595-1616, Jul. 2015.
- W.A. Jabbar, M. Ismail, R. Nordin, and S. Arif, “Power-efficient routing schemes for MANETs: A survey and open issues,” Wireless Networks, Apr. 2016. [doi: 10.1007/s11276-016-1263-6]
- S. S. Basurra, M. D. Vos, J. Padget, Y. Ji, T. Lewis, and S. Armour, “Energy efficient zone based routing protocol for MANETs,” Ad-hoc Networks, vol. 25, pp. 16-37, Feb. 2015.


