A Literature Survey of Topology Control and Its Related Issues in Wireless Sensor Networks
Автор: Debasmita Sengupta, Alak Roy
Журнал: International Journal of Information Technology and Computer Science(IJITCS) @ijitcs
Статья в выпуске: 10 Vol. 6, 2014 года.
Бесплатный доступ
Issues of Topology control (TC) have captured more attentions in Wireless Sensor Networks (WSN). While WSN applications are normally optimized by the underlying network topology. Now a day’s WSNs is one of the most interesting areas of research and are universally being used and deployed or implements to monitor the surrounding physical environments. A number of approaches have been invested in wireless sensor networking, such as topology directed routing, sensor coverage based TC and network connectivity based TC. Many schemes have proved to be able to provide a better network monitoring and communication performance with prolonged system lifetime. In this survey paper, it provides a view of the studies in the area of WSN with different topology issues. By summarizing previous achievements and analyzing existed problems, we provide some idea within this field and also point out some research direction for the future.
Wireless sensor networks, Topology Control, Topology Awareness, Coverage Problem, Geographic Routing, Power Management
Короткий адрес: https://sciup.org/15012167
IDR: 15012167
Текст научной статьи A Literature Survey of Topology Control and Its Related Issues in Wireless Sensor Networks
Published Online September 2014 in MECS DOI: 10.5815/ijitcs.2014.10.03
Now-a-days there is a huge interest of using wireless sensor networks (WSNs) in different fields of life. It has become an emerging technology that has a wide range of potential applications including environment monitoring, object tracking, scientific observing and forecasting, Traffic control and etc. Normally a WSN is comprised of a large number of distributed nodes and arrange them as a multi-hop wireless network and habitually some common work is achieved with these nodes. Generally the devices are inexpensive and small, hence they can be originated and deployed in large numbers as shown in Fig 1. Most sensor node is composed of memory, controller, power supply, communication device, sensing device [1]. According to J. L. Hill [2], a simple mathematical equation describes the concept of WSNs as “ Sensing + Computation + Radio operation = Thousands of potential application ”. Sensing, computation and radio operation are the three main sources for energy consumptions in WSNs, but energy loss maximizes in WSNs due to several radio operations [3].
According to P. Basu [4] WSNs are classified into two main categories, they are “Query-driven” and “Event-driven”.
In case of query-driven approach user submits query from base station node and then the query is broadcasted via the network. The sensor responds to the base stations that are related to the corresponding query or satisfies the query. Whereas in case of Event-driven whenever the sensor detects any event, the sensor itself sends data to base stations or Data collection center or sink nodes.
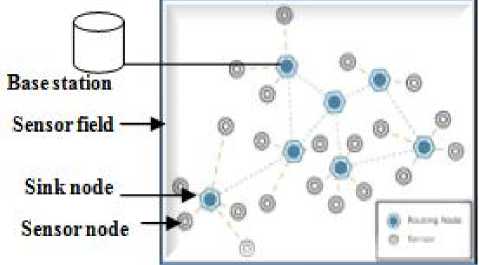
Fig. 1. Ideal Wireless Sensor Network
-
A. States in WSN
Sensor nodes in WSNs can be in four different states [5] as follows:
-
1) Sensing: If a node is in a sensing mode, then only it can monitor the source using an integrated sensor. For transferring information at first it stores the needed data in a small buffer memory and then transmits to the base station.
-
2) Relaying: In this state, a node forward data towards the ultimate destination by receiving the data from other nodes.
-
3) Sleeping: Here most of the sensor nodes are shut down or work in a low power-mode and hence a sleeping node cannot participate either in sensing or relaying. However, it “wakes up” periodically and listens to communication channels for responding to corresponding requests, for that a state transition to “sensing” or “relaying” may prevail.
-
4) Dead: This is the state of the node that resembles it is no more available to the sensor network and it has either used its energy or. From dead state it cannot be rescued to any other state.
-
B. Aspects of WSNs
To achieve a lasting and scalable WSNs design for recovering of topological issues or for topology control, the following aspects have to be carefully taken into account in the design stage:
-
1) Energy conservation: One of the primary goals of the design is to use this limited energy as efficiently as possible to conserve energy. Energy efficiency is especially important in WSNs whereas replacing or refilling sensor batteries is, in general, infeasible. If energy conservation techniques are used at different levels of the wireless architecture, the functional lifetime of both individual units and the network can be extended considerably.
-
2) Limited bandwidth: A very limited bandwidth is available to nodes that are characterized in typically wireless multi hop networks. Although the theoretical bandwidth in industrial standards such as IEEE 802.11 can be as high as 54Mb/Sec [IEEE 1999], the situation is far worse in reality because of radio inference due to simultaneous communications.
-
3) Unstructured and time-varying network topology: Nodes in the networks may be arranged arbitrarily in the deployment region; hence, the graph thus formed represents communication links is generally unstructured. Furthermore the network topology may vary due to the mobility and/or failure of one or more nodes’. For a consequence, determination of the proper value of fundamental network parameters (e.g., the critical transmitting range of connectivity) is a difficult task.
-
4) Low-quality communications: Reliability of
communication on wireless medium is generally much lesser compared to wired medium and also the quality of communication is influenced strongly by environmental factors that are probably time-varying.
-
5) Operating in hostile environments: In many scenarios, it has been observed that, WSNs are expected to operate in hostile environments so sensors must be explicitly designed to work under extreme conditions which causes individual unit failure a likely event. Hence, resilience to sensor faults should be explicitly addressed at different network layers.
-
6) Data processing: Given the energy constraints and the expected poor communication quality, sensed data must be compressed and/or aggregated with data of neighboring sensors before sending them to the gateway node(s).
-
7) Scalability: As mentioned before depending on the scenario, WSNs might be composed of several thousands of sensors. Thus, the scalability of the proposed protocols is an important issue.
Several solutions have been studied in the paper which addresses at least some of the above issues. In particular, great efforts have been devoted to the design of energy efficient message delivery and data retrieving methods. With the awareness of the underlying network topology, more efficient routing or broadcasting schemes could be achieved. Furthermore, the network topology in WSNs can be changed or improvised by varying the nodes’ transmitting range and adjusting the wake/sleep schedule of all nodes. Therefore, further energy can be saved and utilized efficiently if the network topology can be maintained in an optimal manner.
Topology issues have been studied minutely and carefully in distributed systems. In this paper, the focus is on the topology related issues in WSNs. Sensor node deployment and topology control (TC) are the two main factors that should be controlled rather it can affect the performance of WSNs. The two mentioned factors if not managed properly can rise to many problems viz. Loss of energy (energy efficiency and energy conservation), coverage holes and delay in network. The paper also focuses on the topology awareness problem and TC problem which further introduce the TC approaches for both sensor coverage topology and sensor connectivity topology.
The rest of the paper is organized as follows. Section 2 reviews background details, followed by problem statement in section 3. Taxonomy of topology issues, topology awareness problems are reviewed and summarized in section 4. Section 5 introduces some of the topology control approaches for both sensor coverage topology and sensor connectivity. Finally, in section 5 concludes with a summarization of the study and the outline of future research directions.
-
II. Background Details
The most important part of the sensor network is a deployment and connectivity between the nodes where these works alone in the unattended environment. In most cases the WSNs contains hundreds of nodes that have to operate on small built-in batteries. Low power capacities of sensor node leads to limited coverage and communication range for sensor nodes as compare to other mobile devices [6]. When there is a shortage of energy in the network, then the sensor node stop working and therefore it causes harm to the structure of WSNs if many sensors exhaust their on-board energy supply [7]. Due to the limited energy storage capability of sensor nodes the network goes through different challenges and energy consumption is the significant one, for this different strategies and protocols have been taken into account to resolve it. In power limited wireless network research, the main goal is to achieve minimum communication energy consumption [8]. WSNs consist of several nodes that are deployed very close to each other and each node can directly communicate with their neighboring nodes. For this, nodes will consume a lot of energy and thus can cause many problems like: Energy loss, load on a MAC protocol, Volatility in Routing Protocol [1] .
According to M. Cardei and J. Wu [9], the coverage of a wireless sensor node can be estranged into three classes; area coverage (how to cover an area with the sensors), point coverage (coverage for a set of points of interest) and barrier coverage (decreasing the probability of undetected saturation is the main issue in barrier coverage). Most of the coverage problems in WSNs are due to the following three main reasons; not enough sensors to cover the whole region of interest, limited sensing range and random deployment [10]. Many techniques can be applied to prohibit the nodes that are considered as neighbors and this can be done by controlling the transmission power, introducing hierarchies in the network and signaling out some nodes to take over certain coordination tasks or simply turning off some nodes for a certain time. Therefore, by use of TC techniques, the topology of the network is deliberately restricted in order to decrease the power consumption [1]. Different techniques can be classified as TC mechanisms. One of the simplest types of TC issues deals with finding the minimum value for transmitting range such that a certain network wide property is satisfied [11].
According to [12, 13] the problems in sensor node deployment are categorized in the following four classes, they are: 1) Node problems that involve only a single node; 2) Link problems that involve two neighboring nodes and the wireless link between them; 3) path problems that involve three or more nodes and a multi-hop path formed by them; and 4) global problems that are properties of the network as a whole.
Different Topology Control (TC) techniques are studied for WSNs and it has observed that some scholars minimized link interference when the network topology is modeled, someone uses Euclidean minimum spanning tree, other Sleep-based TC [14, 15]. In [16] it is discussed that when the network topology is modeled as a connectivity graph in which each wireless link is either connected or disconnected, but the energy efficiency TC is that one which has less connected sets. Zhang and Hou proposed a method for maintaining sensor coverage and communication connectivity by utilizing a WSN with a minimal number of Sensor Nodes [17].
-
III. Problem Statements And Objectives
Topology issues have been extensively studied in WSNs. Taxonomy of topological issues has introduced in this paper that are named as follows:
-
• Topology Awareness problems : This is categorized into two parts, i.e. geographic routing and various sensor holes.
-
• Topology Control problems : In this section of problem there are several issues and that are mainly classified into two groups, they are: Sensor coverage topology (includes static, mobile and hybrid network) and sensor connectivity topology (includes power control and power management mechanism). There are various problems that arise in sensor network as mentioned earlier. For that, several approaches have been taken into account to solve the above issues Viz. Greedy Perimeter Stateless Routing (GPSR) [18] for MANETs, compass routing [21], BOUNDHOLE Algorithm [27], PEAS protocol [34], power control mechanism and power management mechanism, etc.
Another form of technique is there to recover some topological issues that prevails in the sensor networks, is to implement Color based topology control Algorithm (CBTC Algorithm) [53]. There are two most important factors that should be deployed properly to maintain the performance of WSNs. The two main factors are: sensor node deployment and topology control. Both the factors have to be properly managed to guarantee the maximum lifetime of sensor nodes, minimize network delay and removal of sensor holes.
In the immediate section, followed by this, contains the coherent taxonomy of topological issues that will be illustrated along with a diagrammatic representation in fig 2.
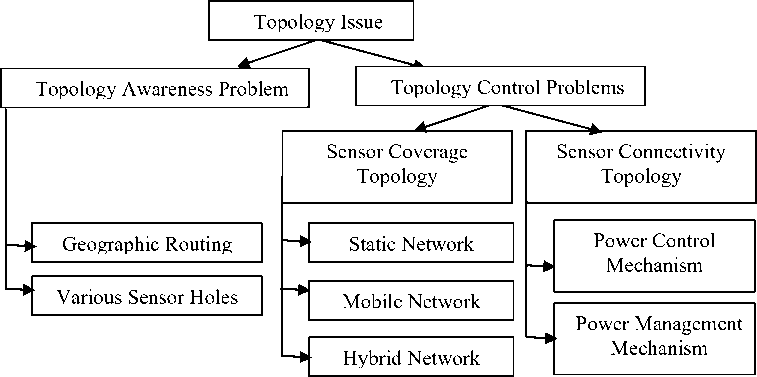
Fig. 2. A Taxonomy of topology issues in WSNs
-
IV. Taxonomy of Topology issues
Topology issues have been extensively studied in WSNs. In this section, a coherent taxonomy is organized and depicted in Fig 2. Topology issues are divided into two categories: Topology Awareness Problems and
Topology Control Problems. Topology Awareness Problems consist of geographic routing problems and sensor hole problems. To achieve optimal routing schemes Geographic routing uses geographic and topological information of the network with high routing efficiency and low power consumption. Different sensor holes, viz.
Jamming holes, sink/black holes and worm holes, can be developed in a WSN and hence create variations in network topology which trouble the upper layer applications. For examples, jamming holes can occur due to intense communication and thus message delivery to exterior node fails. Exhausted nodes around a sink node or pretended sinks or by malicious nodes causes Sink/Black holes and worm holes. If issues of sensor holes are not properly handled, it will create a costly routing table and the intermediate nodes will be exhausted rapidly. Topology Control Problems can be further divided into two types: Sensor Coverage Topology and Sensor
Connectivity Topology. The topology of sensor coverage is illustrated by the coverage topology and is concerned about the maximization of a reliable sensing area provided consuming less power. On the other hand connectivity topology emphasizes on the network connectivity and analysis the retrieve and delivery of the message in the network. Two types of mechanisms have been used for the maintenance of an efficient sensor connectivity topology: Power Control Mechanisms and Power
Management Mechanisms. To achieve optimized connectivity topology the former controls the radio power level and the later maintains a good wake/sleep schedule.
-
A. Topology Awareness Problem
-
1) Geographic routing : Geographic routing approach
relies on greedy forwarding to route packets on the basis of nodes’ local information on the network topology. Karp et al. [18] propose the Greedy
Perimeter Stateless Routing (GPSR) for MANETs. The protocol starts in a greedy forwarding mode, and assumes the location information of sensor nodes can be obtained by supporting systems [19, 20]. GPSR recovers from local maximum position by utilizing perimeter rouging mode and the right-hand rule. Kranakis et al. [21] proposes the Compass Routing algorithm and FACE-1 algorithms that guarantees the destination is reached even when the local minimum phenomenon occurs in greedy forwarding. Similar to the work in [21], Bose et al. [22] propose the FACE-2 routing algorithm. In contrast to GPSR, routing in FACE-2 is done through the perimeter of the Gabriel Graph (GG) formed at each node. It also modifies the FACE-1 so that the perimeter traversal follows the next edge whenever that edge crosses the line from the source to destination. Obviously, the downside of FACE-2 is that it consumes more energy in the perimeter nodes. As an extension to the compass routing algorithm, Kuhn et al. [23] introduce deterministic fall back mechanism to get back in the greedy mode from the perimeter routing mode without necessarily exploring the complete face boundary. In [24], a probabilistic solution is proposed to call Intermediate Node Forwarding (INF). Negative Acknowledgment (NAK) packet has been adopted to provide feedback to the source about packet drops in this approach. Li et al. in [25] propose an active message transmission by relaying scheme for communication in a disconnected mobile ad-hoc wireless network. The protocol relays messages using mobile agents by moving nodes appropriately to complete a routing path in a disconnected network. For WSNs, the proposed protocol can avoid routing holes due to sparse deployment or node failures, but will fail to achieve any significant results if the routing holes are formed. Yu et al. [26] proposed Geographic and Energy Aware Routing (GEAR) to route a packet toward a region of interest. GEAR works well if the region to be covered is a small fraction of the total area. The efficiency drops quickly when the area of interest increases. Table I summarizes the proposed geographic routing schemes and exhibits a comparison.
Table 1. Geographic routing schemes
|
Protocol |
Maintained State |
Capability of Topology adaptive fault tolerance |
|
GPSR[18] |
Location info and the whole planar graph (RNG or GG) |
Greedy forwarding mode and Right-hand rule in perimeter mode to round the Voids. |
|
Compass Routing [21] FACE II [4] GOAFR+ [22] |
Location info and the whole planar graph (GG) i.e. Gabriel Graph |
To avoid routing holes use Face routing on planar graph. |
|
INF [24] |
Location info |
Active NAKs and source initiated repair. |
|
Active Message Relay [25] |
Location info |
By node movement to reach disconnected neighbors. |
|
GEAR [26] |
Location info and learned and estimated cost values |
Learned and estimated cost of energy efficient geographical routing and limited flooding in region. |
-
2) Holes Problems: In most geographic routing schemes, a routing hole refers to a region in the network, where either the nodes are not present or the available nodes cannot take part in the actual routing of the data due to several possible reasons. To protect the infection to the packet delivery by sensor holes, the geographic routing schemes described in Table 1 do not provide methods to detect and localize the holes. Fang et al. [27] provide a theoretical work on determining sensor holes in
which so-called stuck node is defined and an algorithm called BOUNDHOLE is proposed to find the holes utilizing the strong stuck nodes. Li and Liu [28] study an application specific scenario for the underground monitoring in the coal mine. They propose a topology maintenance protocol SASA, which claims to rapidly detect the structural variation during underground collapse by regulating the mesh sensor network deployment and formulating a collaborating mechanism based on the regular beacon strategy for sensors. The so-called edge nodes outline the sensor hole and report it to the sink. To the best of our knowledge, the SASA protocol is the first work which relates the topology variation to the actual geographical changes. Wood et al. discuss jamming hole in [29]. A jamming hole circumvents the ability of nodes in a specific area to communicate/sense, so that a virtual hole emerges. Wood et al. propose a JAM protocol to detect and map jammed regions in a sensor network. The detection part of the protocol applies heuristics based on available data, e.g. bit-error rates, etc., to distinguish jamming from normal interference. The JAM protocol assumes that the location information and unique ID is known to each node.
Sink/Black holes and worm holes are gradually formed due to sensor node power exhausted and the possible denial of service attacks in the network. The sink hole is characterized by intense resource contention among neighboring nodes of the malicious node for the limited bandwidth and channel access [30]. A worm hole is another kind of denial of service attack [31]. It is formed when a malicious node causes nodes located in different parts of networks to believe that they are neighbors, which result in incorrect routing convergence. Karlof et al. [32] analyze the resilience of various routing protocols and energy conserving topology maintenance algorithms against sink holes. They showed that popular routing protocols like directed diffusion, rumor routing and multi-path variant of directed diffusion, etc. are all vulnerable to sink holes attacks. For geographical greedy forwarding
The algorithms it is more difficult to create sink holes because in this case a malicious node has to advertise different attractive locations to different neighbors in order to qualify as next hop. Wood et al. in [30] identified a number of possible defenses against the sink holes. In the authorization solution, only authorized nodes can exchange routing information with each other. The solution is not scalable due to high computation and communication overhead. Also, public key cryptography is not feasible in sensor networks given the capacities and constraints of the sensor devices.
There is another way to remove the sensor hole which is by using “Color Based Topology Control” (CBTC) Algorithm [52]. Through this algorithm, an identifier, i.e. “color flag” is used in the code area of the sensor node, denoting the color of that node. All the sensor nodes are sensitive for any particular application, i.e. humidity, temperature or pressure, etc. A node of the same color flag can sense another node in its coverage area and communication between them is possible. As we know in sensor network when a node; which is on the way to some sink node become dead then there occur a coverage hole. Through this coverage hole other nodes cannot transmit their data to the sink node. To remove this problem with the color based topology algorithm, when a node of some color, let the node of color flag “blue” becomes dead, then it should work by choosing some node of the other color flag within its coverage area.
-
B. Topology Control Problem
-
1) Sensor Coverage Topology: We distribute this family of problems into small categories: Static Network, Mobile Network and Hybrid Network.
-
a) Static Network: There are some proposed
approaches that have different coverage objectives for a static sensor network. We elaborate these approaches separately.
-
• Partial Coverage: In [33], Ye et al. propose PEAS, which extends WSN system functioning time by keeping only a necessary set of sensors working in case the node deployment density is much higher than necessary. PEAS protocol consists of two algorithms: Probing Environment and Adaptive Sleeping. In PEAS protocol, the node location information is not required as a pre-knowledge. Cao et al. [34] develop a near-optimal deterministically rotating sensory coverage for the WSN surveillance system. The aim of their scheme is to partially cover the sensing area with each point eventually sensed within a finite delay bound. They assume that the neighboring nodes have approximately
synchronized clocks and sensing node of each other is known to them.
-
• Single coverage: For single coverage requirement, Zhang et al. [35] have proposed the Optimal Geographical Density Control (OGDC) protocol. This protocol tries to minimize the overlap of sensing areas of all sensor nodes for cases when RC ≥ 2Rs where RC is the node communication range and Rs is the node sensing range. OGDC is a fully localized algorithm, but the node location is needed as a pre-knowledge.
-
• Multiple Coverage: Wang et al. [36] present the Coverage Configuration Protocol (CCP) that can provide flexibility in configuring a sensor network with different degrees of coverage. The CCP protocol needs node location information as assistance. Huang et al. [37] propose polynomialtime algorithms to verify whether every point in the
target area is covered by at least the required number of nodes. The authors suggest a central controller entity that can collect the details of insufficiently covered segments and dispatch new nodes to supplement. However, this centralized approach lacks scalability [38].
-
b) Mobile Network: Wang et al. [39] study the deployment schemes for movable sensors. Given an area to be monitored, the proposed distributed selfdeployment protocols first discover the existence of coverage holes in the target area, then calculate the target positions and move sensors to diminish the coverage holes. Voronoi diagrams [40,41] are used to discover the coverage holes and three movements-assisted sensor deployment protocols VEC, VOR and Minimax are designed. Howard et al. [43] and Heo et al. [42] study the sensor network in the viewpoint of virtual forces. In [43], nodes only use their sensed information to make moving decisions. It is a cost effective and no communication among the nodes or localization information is needed. For the DSS (Distributed Self-Spreading) algorithm proposed in [42], sensors are randomly deployed initially. They start moving based on partial forces exerted by the neighbors. The forces exerted on each
node by its neighbors depend on the local density of deployment and on the distance between the node and the neighbor.
Hybrid Network: Now a days, the active research area includes the coverage scenario with only some of the sensors that are capable of moving, especially in the field of robotics for exploration purpose. The sensors that are capable of moving can help in deployment and network repair by moving to appropriate locations within the field to achieve desired level of coverage. Batalin et al. [44] suggest a combined solution for the exploration and coverage of a given target area. The coverage problem is solved with the help of a constantly moving robot in a given target area. The algorithm does not consider the communications between the deployed nodes. All decisions are made by the robot by directly communicating with a neighbor sensor node. Wang et al. [45] address the single coverage problem by moving the available mobile sensors in a hybrid network to heal coverage holes. A comparison of different sensor coverage approaches is listed in Table 2. As you can see from the table, most of the proposed approaches need node location information as assistance and the unit-disk model is widely adopted as a simplification of the node transmitting model.
Table 2. Coverage approaches
|
Categorization |
Approach |
Features |
|
Static Network |
Partial coverage |
Sleeping schedule is distributed |
|
Guarantee finite delay bound. |
||
|
Single coverage |
Energy consideration is residual. |
|
|
Coverage calculations are Sector based. |
||
|
Uniform disk sensing model. |
||
|
Multiple Coverage |
Configurable degree of coverage. |
|
|
Supports non-unit disk model. |
||
|
Grid based differentiated degree of coverage. |
||
|
Mobile Networks |
Computational Geometry |
It is Localized, Scalable, and Distributed. |
|
Energy consideration is single coverage based. Residual. |
||
|
Virtual forces |
Scalable, Distributed. Local communication not required. |
|
|
Scalable, Distributed. Residual energy based. |
||
|
Hybrid Networks |
Single Mobile Sensor |
No multi-hop communications, distributed. |
|
Multiple Mobile Sensor |
For single coverage requirement Voronoi diagram is used. |
-
2) Sensor connectivity Topology
-
a) Power Control Mechanisms: The aim of power control mechanisms is to change the transmitting range of nodes’ dynamically to maintain some property of the communication graph, while the reduction of the energy consumed by node transceivers since they are one of the basic sources of energy consumption in WSNs. Good network energy efficiency can be fundamentally achieved by Power control mechanisms. Study of Power control is done in homogeneous and non-homogeneous scenarios that can be verified by examining whether
nodes have the same transmitting range or not. In homogeneous network, the CTR (Critical Transmitting Range) problem has been found theoretically as well as practically. COMPOW [53] is a distributed protocol that helps to determine the minimum common transmitting range required to ensure network connectivity. It shows that adjusting the transmitting range for this value has the optimal effects of maximizing network capacity, reducing the contention to access the wireless channel, and minimizing energy consumption. During the communication graph investigation has been done on the tradeoff between the transmitting range and the size of the largest connected component. The results of the experiment presented show that, in sparse two and three-dimensional networks, the transmitting range can be decreased significantly if weaker requirements on connectivity are acceptable: halving the critical transmitting range, the largest components that are connected has an average size of approximately 0.9n. It means that to connect relatively few nodes a considerable amount of energy is spent. Since nodes are allowed to have different transmitting ranges the Non-homogeneous networks are more challenging. The assignment problem of a transmitting range with nodes in such a way that the resulting communication graph is connected strongly and have minimum energy cost is called the Rang Assignment (RA) problem [54]. It is described as NP-hard in the case of 2D and 3D networks. However the optimal solution can be approximated within a factor of 2 using the generated range assignment. An important variant of RA has been studied recently on the basis of the concept of symmetry of the communication graph. More practical significance is shown due to the high overhead needed to handle unidirectional links in routing protocols or MAC protocols that are naturally designed to work under the symmetric assumption, Symmetric Range Assignment (SRA). However, NP-hard in 2D and 3D networks still includes SRA, and it even incurs a considerable extra energy cost over RA. I can refine SRA as WSRA (Weakly Symmetric Range Assignment) which weakens the requirement that the communication graph contains only bidirectional links by allowing the existence of the unidirectional links, but requiring the symmetric sub graph of the communication graph resulting from connecting RA.
In the released WSRA problem, only marginal effect has been induced on the energy cost while the desired symmetry property remains.
-
b) Power Management Mechanisms: Power
management is dealing with which set of nodes should be turned on/off and when, for the purpose of construction of energy saving topology to prolong the network lifetime. Available information in the stack of protocol from all the layers can be used by this. In GAF approach [46], nodes use location information for fragmentation of the field into fixed square grids. The size of each grid keeps constant, regardless of node density. Nodes inside a grid switch between sleeping and listening mode, with the guarantee that individual node in each grid remains so that a dynamic routing backbone is managed to forward packets. A power saving topology maintenance algorithm called Span [49] is used for multi-hop wireless networks that elects coordinators adaptively from all nodes to form a routing backbone and most of the time to conserve power turn off the other nodes’ radio receivers. For exploiting the time dimension rather than the node density dimension to control, a power saving topology of active nodes STEM approach [50] is used. They provide switching of nodes between, “transfer state” and “monitoring state”. In the transfer state Data are only forwarded. In the monitoring state, nodes keep their radio off and will switch into transfer state on event detected to be an initiator node. The additional study of integrating STEM and GAF shows the potential of further power saving by exploiting both time dimension and node density dimension. Table 3 summarizes the mechanisms of power management, and provides an in-depth knowledge of the characters of proposed mechanisms.
Table 3. Approaches of power management mechanism
|
Protocols |
Synchronization |
Mobile/Static |
Distributed |
Location info |
|
GAF[46] |
None |
Mobile |
Yes |
Yes |
|
Asynchronous Wakeup protocol[47] |
None |
Static |
No |
No |
|
Power saving protocol [48] |
None |
Mobile |
Yes |
No |
|
Span[49] |
None |
Static |
Yes |
No |
|
STEM[50] |
None |
Static |
Yes |
No |
|
S-MAC[51] |
Yes |
Static |
Yes |
No |
V. Conclusions
In this survey paper, we have revised two major topology issues in WSNs, namely topology awareness and topology control problems. Topology awareness, problems constructs applications or upper protocols to conform the underlying topology. Typical approaches applied in this category do not actively consider improving the topology itself for the specific applications. Topology control mechanisms concentrate mainly on constructing an energy-efficient and reliable network topology and normally do not touch applications individually. Furthermore, Power control and power management are two different types of topology controlling methods. By focusing on integrating power control and power management, it is possible to provide noticeable improvements on network topology and efficiencies of energy usage. This is another interesting research topic for the researchers in the field. In this paper, we present a comprehensive survey on topology issues for WSNs. We provide our classifications of the problems and approaches. Under this frame, we list, review and compare some classical works in the field.
In most of the paper sensor coverage topology and sensor connectivity topology have been separately discussed. Sensing coverage topology resembles the network sensing ability, whereas the connectivity topology should be maintained for the successful information delivery, including queries, sensing data and control message. How to construct optimized coverage topology by managing efficient and low cost connectivity is not properly understood so future studies is required.
Power control and power management are two different kinds of topology controlling methods. By focusing on combining power control and power management, it is possible to provide noticeable improvements on network topology and efficiencies of energy usage which is another area of future study.
Список литературы A Literature Survey of Topology Control and Its Related Issues in Wireless Sensor Networks
- H. Karl and A. Willig, “Protocols and Architectures for Wireless Sensor Networks,” John Wiley & Sons, Hobo-ken, 2005. doi:10.1002/0470095121
- J. L. Hill, “System Architecture for Wireless Sensor Networks,” University of California, Berkeley, 2003.
- Demirkol, C. Ersoy and F. Alagoz, “MAC Protocols for Wireless Sensor Networks: A Survey,” IEEE Communication Magazine, Vol. 44, No. 4, 2006, pp.115-121.
- P. Basu and J. Redi, “Effect of Overhearing Transmissions on Energy Efficiency in Dense Sensor Networks,” Proceedings of the 3rd International Symposium on In- formation Processing in Sensor Networks, Berkeley, 26-27 April 2004, pp. 196-204.
- W. Li and C. G. Cassandras, “A Minimum-Power Wire- less Sensor Network Self-Deployment Scheme,” IEEE Wireless Communications and Networking Conference, Vol. 3, 2005, pp. 1897-1902.
- A. Roy and N. Sarma, “Energy Saving in MAC Layer of Wireless Sensor Networks: A Survey,” National Work- shop in Design and Analysis of Algorithm (NWDAA), Tezpur University, Assam, 2010, pp. 961-994.
- M. Younis and K. Akkaya, “Strategies and Techniques for Node Placement in Wireless Sensor Networks: A Survey,” Ad Hoc Networks, Vol. 6, No. 4, 2008, pp. 621-655. doi:10.1016/j.adhoc.2007.05.003
- C. Suh, Y.-B. Ko, C.-H. Lee and H.-J. Kim “Numerical Analysis of the Idle Listening Problem in IEEE 802.15.4 Beacon-Enable Mode,” 1st International Conference on Communications and Networking in China, Beijing, 25-27 October 2006, pp. 1-5.
- M. Cardei and J. Wu, “Coverage in Wireess Sensor Networks,” In: M. Ilyas and I. Mahgoub, Handbook of Sensor Networks: Compact Wireless and Wired Sensing Systems, CRC Press, Leiden, 2005.
- N. A. Ab. Aziz, K. Ab. Aziz and W. Z. W. Ismail, “Coverage Strategies for Wireless Sensor Networks,” World Academy of Science, Engineering and Technology, Vol. 50, 2009, pp. 145-150.
- P. Santi, “Topology Control in Wireless Ad Hoc and Sensor Networks,” John Wiley & Sons, Hoboken, 2005, pp. 27-95. doi:10.1002/0470094559.ch3
- M. Ringwald, K. Romer and A. Vitaletti, “Passive In- spection of Wireless Sensor Networks,” Proceedings of the 3rd International Conference on Distributed Com- puting in Sensor Systems, Vol. 4549, 2007, pp. 205-222.
- J. Beutel, K. Romer, M. Ringwald and M. Woehrle, “De- ployment Techniques for Sensor Networks,” Signals and Communication Technology, 2009, pp. 219-248. doi:10.1007/978-3-642-01341-6
- G. N. Purohit and U. Sharma, “Topology Control for Energy Conservation in Wireless Sensor Network,” In-ternational Journal of Contemporary Mathematical Sci-ences, Vol. 7, No. 5, 2012, pp. 227-239.
- Y. Y. Zhou and M. Medidi, “Sleep-Based Topology Con- trol for Wakeup Scheduling in Wireless Sensor Net- works,” 4th Annual IEEE Communications Society Con- ference on Sensor, Mesh and Ad Hoc Communications and Networks, San Diego, 18-21 June 2007, pp. 304-313.
- J. Ma, Q. Zhang, C. Qian and L. M. Ni, “Energy-Efficient Opportunistic Topology Control in Wireless Sensor Net- works,” Proceedings of the 1st International MobiSys Workshop on Mobile Opportunistic Networking, San Juan, 11 June 2007, pp. 33-38.
- S. Tanabe, K. Sawai and T. Suzuki, “Sensor Node De- ployment Strategy for Maintaining Wireless Sensor Net- work Communication Connectivity,” International Jour- nal of Advanced Computer Sciences and Applications, Vol. 2, No. 12, 2011, pp. 140-146.
- B. Karp and H. T. Kung, "Greedy Perimeter Stateless Routing for Wireless Networks," in proceedings of the Sixth Annual International Conference on Mobile Computing and Networking (Mobicom), 2000.
- N. Bulusu, J. Heidemann and D. Estrin, "GPS-less Low Cost Outdoor Localization for Very Small Devices," IEEE Personal Communications Magazine, 2000.
- Y. Liu, L. Xiao, X. Liu, L. M. Ni and X. Zhang, "Location Awareness in Unstructured Peer-to-Peer Systems," IEEE Transactions on Parallel and Distributed Systems (TPDS). vol. 16, February, pp. 163-174, 2005.
- E. Kranakis, H. Singh and J. Urrutia, "Compass Routing on Geometric Networks," in proceedings of the 11th Canadian Conference on Computational Geometry, 1999.
- P. Bose, P. Morin, I. Stojmenovic and J. Urrutia, "Routing with Guaranteed Delivery in Ad Hoc Wireless Networks," Wireless Networks, vol. 7, pp. 609 - 616, 2001.
- F. Kuhn, R. Wattenhofer, Y. Zhong and A. Zollinger, "Geometric Ad-Hoc Routing: Of Theory and Practice," in proceedings of ACM PODC, 2003.
- S. Douglas, D. Couto and R. Morris, "Location proxies and intermediate node forwarding for practical geographic forwarding," MIT Laboratory for Computer Science MIT-LCS-TR-824, 2001.
- Q. Li and D. Rus, "Sending Messages to Mobile Users in Disconnected Ad-Hoc Wireless Networks," in proceedings of ACM Mobicom, 2000.
- Y. Yu, R. Govindan and D. Estrin, "Geographical and Energy Aware Routing: A Recursive Data Dissemination Protocol for Wireless Sensor Networks," UCLA Computer Science Department UCLA/CSD-TR-01-0023, 2001.
- Q. Fang, J. Gao and L. J. Guibas, "Locating and Bypassing Routing Holes in Sensor Networks," in proceedings of IEEE INFOCOM, 2004.
- M. Li and Y. Liu, "Wireless Sensor Network for Underground Monitoring," submitted to ACM Sensys'06, 2004.
- A. D. Wood, J. A. Stankovic and S. H. Son, "JAM: A Jammed-Area Mapping Service for Sensor Networks," in proceedings of 24th IEEE Real Time System Symposium (RTSS), 2003.
- A. D. Wood and J. A. Stankovic, "Denial of service in sensor networks," IEEE Computer Magazine, vol. 35, pp. 48 - 56, 2002.
- Y. C. Hu, A. Perrig and D. B. Johnson, "Wormhole Detection in Wireless Adhoc Networks," Department of Computer Science, Rice University 2002.
- C. Karlof and D. Wagner, "Secure Routing in Wireless Sensor Networks: Attacks and Countermeasures," in proceedings of 1st IEEE International Workshop SNPA, 2003.
- F. Ye, G. Zhong, S. Lu and L. Zhang, "PEAS: A Robust Energy Conserving Protocol for Long-lived Sensor Networks," in proceedings of International Conference on Distributed Computing Systems (ICDCS), 2003.
- Q. Cao, T. Abdelzaher, T. He and J. Stankovic, "Towards Optimal Sleep Scheduling in Sensor Networks for Rare-Event Detection," in proceedings of IPSN, 2005.
- H. Zhang and J. Hou, "Maintaining Sensing Coverage and Connectivity in Large Sensor Networks," Department of Computer Science, UIUC UIUCDCS-R-2003-2351, 2003.
- X. Wang, G. Xing, Y. Zhang, C. Lu, R. Pless, et al., "Integrated Coverage and Connectivity Configuration in Wireless Sensor Networks," in proceedings of ACM SenSys, 2003.
- C. F. Huang and Y. C. Tseng, "The Coverage Problem in a Wireless Sensor Network," in proceedings of ACM WSNA, 2003.
- W. Xue, Q. Luo, L. Chen and Y. Liu, "Contour Map Matching For Event Detection in Sensor Networks," in proceedings of ACM SIGMOD, 2006.
- G. Wang, G. Cao and T. L. Porta, "Movement-Assisted Sensor Deployment," in proceedings of IEEE INFOCOM, 2004.
- F. Aurenhammer, "Voronoi Diagrams - A Survey of a Fundamental Geometric Data Structure," ACM Computing Surveys, 1991.
- D. Du, F. Hwang and S. Fortune, "Voronoi diagrams and Delaunay triangulations," Euclidean Geometry and Computers, 1992.
- N. Heo and P. K. Varshney, "An Intelligent Deployment and Clustering Algorithm for a Distributed Mobile Sensor Network," in proceedings of IEEE International Conference on Systems, Man and Cybernetics, 2003.
- A. Howard, M. J. Mataric and G. S. Sukhatme, "Mobile Sensor Network Deployment using Potential Fields: A Distributed, Scalable Solution to the Area Coverage Problem," 2002.
- M. A. Batalin and G. S. Sukhtame, "Coverage, Exploration and Deployment by a Mobile Robot and Communication Network," Telecommunication Systems Journal, Special Issue on Wireless Sensor Networks, vol. 26(2), pp. 181 - 196, 2004.
- G. Wang, G. Cao and T. L. Porta, "A Bidding Protocol for Deploying Mobile Sensors," in proceedings of IEEE International Conference on Network Protocol (ICNP),2003.
- Y. Xu, J. Heidemann and D. Estrin, "Geography-informed Energy Conservation for Ad Hoc Routing," in proceedings of ACM Mobicom, 2001.
- R. Zheng, J. C. Hou and L. Sha, "Asynchronous Wakeup for Ad Hoc Networks," in proceedings of ACM Mobicom, 2003.
- Y. C. Tseng, C. S. Hsu and T. Y. Hsieh, "Power-Saving Protocols for IEEE 802.11 - Based Multi-Hop Ad Hoc Networks," in proceedings of IEEE INFOCOM, 2002.
- B. Chen, K. Jamieson, H. Balakrishnan and R. Morris, "Span: An Energy-Efficient Coordination Algorithm for Topology Maintenance in Ad Hoc Wireless Networks," in proceedings of Mobicom, 2001.
- C. Schurgers, V. Tsiatsis, S. Ganeriwal and M. Srivastava, "Topology Management for Sensor Networks: Exploiting Latency and Density," in proceedings of ACM Mobihoc, 2002.
- W. Ye, J. Heidemann and D. Estrin, "An Energy-Efficient MAC Protocol for Wireless Sensor Networks," in proceedings of IEEE INFOCOM, 2002.
- Muhammad Asghar Khan, Asfandyar Khan, Said Khalid Shah, and Azween Abdullah “An Energy Efficient Color Based Topology Control Algorithm for Wireless Sensor Networks” Institute of Engineering and Computing Sciences, University of Science and Technology Bannu, Bannu, Pakistan, 2012.
- S. Narayanaswamy, V. Kawadia, R. Sreenivas and P. Kumar, "Power control in ad hoc networks: Theory, architecture, algorithm and implementation of the COMPOW protocol," in proceedings of European Wireless, 2002.
- L. Kirousis, E. Kranakis, D. Krizanc and A. Pelc, "Power Consumption in Packet Radio Networks," Theoret. Comput. Sci.,pp.289-305,2000.


