A new robust and imperceptible image watermarking scheme based on hybrid transform and PSO
Автор: Tamirat Tagesse Takore, P. Rajesh Kumar, G. Lavanya Devi
Журнал: International Journal of Intelligent Systems and Applications @ijisa
Статья в выпуске: 11 vol.10, 2018 года.
Бесплатный доступ
In this paper, a new robust and imperceptible digital image watermarking scheme that can overcome the limitation of traditional wavelet-based image watermarking schemes is proposed using hybrid transforms viz. Lifting wavelet transform (LWT), discrete cosine transform (DCT) and singular value decomposition (SVD). The scheme uses canny edge detector to select blocks with higher edge pixels. Two reference sub-images, which are used as the point of reference for watermark embedding and extraction, have been formed from selected blocks based on the number of edges. To achieve a better trade-off between imperceptibility and robustness, multiple scaling factors (MSF) have been employed to modulate different ranges of singular value coefficients during watermark embedding process. Particle swarm optimization (PSO) algorithm has been adopted to obtain optimized MSF. The performance of the proposed scheme has been assessed under different conditions and the experimental results, which are obtained from computer simulation, verifies that the proposed scheme achieves enhanced robustness against various attacks performed. Moreover, the performance of the proposed scheme is compared with the other existing schemes and the results of comparison confirm that our proposed scheme outperforms previous existing schemes in terms of robustness and imperceptibility.
Lifting wavelet transform, discrete cosine transform, singular value decomposition, edge detection, particle swarm optimization
Короткий адрес: https://sciup.org/15016544
IDR: 15016544 | DOI: 10.5815/ijisa.2018.11.06
Текст научной статьи A new robust and imperceptible image watermarking scheme based on hybrid transform and PSO
Published Online November 2018 in MECS
Due to the rapid advancement of digital technologies and widespread of the Internet, digital multimedia recording, storing, copying, modifying, and sharing becomes an easy task. Malicious attackers can use these technologies for illegal recording, copying, distributing or selling copyrighted valuable multimedia data of someone else without getting permission or compensating the authorized owners. Furthermore, they modify or even destroy the whole or part of the document to illegally claim ownership or prevent the information transfer to the intended recipient. Hence, protecting digital properties from unauthorized use become a critical issue to content producers and publishers that the demand for an effective data security technique is growing from time to time. Cryptography is one of the most commonly used methods for digital property protection. The content producer first encrypts the document before delivering it to the user, and the person who has a decryption key can only decrypt and access the data. However, this method fails to ensure security when the document is once decrypted. Pirates can easily purchase a legit single copy and distribute a large number of duplicated copies for a low price or for free over a shared network. Therefore, it is necessary to find another method to protect these digital media data with a more stringent way.
In recent years, the newly emerging technique called digital watermarking becomes the best alternative method to protect a copyright of multimedia data over a shared medium [1-3]. Digital watermarking is a process which embeds a watermark into host multimedia content in such a way that the embedded digital signature is extractable whenever information about the identity of the content owner is required. The embedded secret data could be visible or invisible. Invisible watermark is the most commonly used for copyright protection application. Besides to copyright protection, a digital watermarking technique has been used for many other applications such as content authentication, copy control, broadcast monitoring and tamper detection.
The existing digital watermarking techniques can be classified into numerous groups based on different criteria. Depending upon the embedding domain, they can be categorized into two: spatial domain and transform domain techniques. Spatial domain watermarking technique embeds a watermark into a host data by modifying the pixel intensity values; whereas, transform domain technique insert a watermark by altering the values of transform coefficients. Although spatial domain watermarking techniques are easy to implement and low in computational complexity, transform domain watermarking techniques are often preferred and widely used for copyright protection application due to their ability to provide better robustness against different attacks. Discrete wavelet transform (DWT), discrete cosine transform (DCT), singular value decomposition (SVD) and Lifting wavelet transformation (LWT) are the most commonly used transforms in digital watermarking field [4-6]. To meet different watermarking requirements in the best way, hybrid transform techniques are the most preferable for watermarking schemes. Hybrid transform technique combines two or more transforms and exploits the advantage of those transforms to enhance the performance. The other classes of watermarking are text, image, audio and video watermarking which are based on the type of signal used as a cover or host document. Furthermore, watermarking techniques can be classified into fragile, semi-fragile and robust based on the ability to resist attacks, and into blind, semi-blind and non-blind depending upon the information required for watermark extraction. However, in this paper, robust and blind image watermarking scheme using a hybrid transform technique is proposed.
For copyright protection application, imperceptibility and robustness are the two major requirements that watermarking schemes are expected to fulfill and often they are used as criteria to evaluate the performance of the schemes. The term imperceptibility refers to the degree of visual similarity between an original image and its watermarked version. Generally, a watermark embedding process is accompanied with quality loss due to the added signal. However, for invisible watermarking schemes, the embedding process should leave the level of degradation unnoticeable to human observers. Peak signal to noise ratio (PSNR) is the most commonly used metric to evaluate the level of imperceptibility. A higher PSNR value indicates a higher imperceptibility. Furthermore, a good watermarking scheme should also satisfy the robustness requirement against different attacks. A watermarking scheme is said to be robust to an attack if the embedded watermark is able to resist the performed attacks and is extractable even after the attacks. Improving the robustness against attacks by preserving the visual quality is the core motivation of most existing watermarking schemes.
The remainder of this paper is organized as follows. Section II provides an extensive literature survey of related works. In Section III, the basic concepts of transforming techniques which we have adopted in the proposed scheme are explained in detail. Brief summary of PSO based scaling factors optimization processes is described in section IV. Section V illustrates the proposed watermark embedding and extraction procedure. Section VI presents experimental setup and results. Finally, our concluding remarks are presented in section VII.
-
II. Related Works
In the field of watermarking, designing a robust watermarking scheme which can hide information without significantly affecting the visual quality has been the major challenging problem due to the existence of two conflicting watermarking requirements, viz. robustness and imperceptibility. Thus far, different strategies have been adopted to address the issue. Among these strategies, feature extraction based image watermarking technique become more popular due to its advantages, and one of which is the ability to embed a watermark in a region of an image bearing the basic character information such as texture and edge. Edge detection based suitable region selection technique has been used extensively as the best method to improve the robustness and imperceptibility. Authors in [7] proposed a new digital image watermarking algorithm based on texture block and edge detection in the DWT in order to balance between the invisibility and robustness and improve the ability of resisting to attacks of the digital image watermark. Khoo et al. [8] proposed a robust image watermarking scheme based on the human visual system (HVS) and used edge entropy as a HVS character for selecting significant blocks to embed a binary watermark. After the first level of DWT decomposition, the SVD is performed on the low-low sub-band to modify the elements of U matrix according to predefined conditions. However, in the proposed watermark embedding process the defined threshold value (T) which was used to modify U elements could not assure the trade-off between robustness and imperceptibility unless its value is determined by using an optimization algorithm.
The other alternative approach that has been adopted to improve the performance of the watermarking scheme is choosing suitable transform techniques for watermark embedding process. Numerous watermarking schemes using different transform techniques have been proposed and available in the literature. SVD is used widely for watermarking application due to its significant advantages [9, 10]. However, most of SVD based watermarking schemes suffered from the false positive problem, in which fake watermark is detected from the content where a different watermark was embedded. W. Yongdong [11] proposed a watermarking scheme which can resist counterfeiting attack using SVD technique. Although the proposed scheme is able to solve the false positive problem, it may be vulnerable to other attacks. In [12], a novel image watermarking algorithm based on SVD has been proposed and the algorithm performs well in both security and robustness. However, to overcome the drawbacks of SVD based watermarking algorithm and improve the performance, another transform techniques such as DWT, DCT or LWT should be used together with SVD. A watermarking scheme which uses hybrid transform techniques can utilize the advantages these transforms and achieve the required goal. S. Fazli and M.
Moeini [13] proposed a digital image watermarking algorithm using DWT-DCT-SVD techniques, and the algorithm gave improved robustness against various geometric attacks. In recent years, due to its better computational efficiency and lossless decomposition, LWT becomes more popular in watermarking than traditional wavelet transforms. Moreover, LWT can map integer to integer without the rounding error; hence it can be used for lossless data hiding. Ansari et al. [14] proposed robust and false positive free watermarking scheme using LWT and SVD. The authors employed a metaheuristic optimization technique in their scheme to find the optimal value of scaling factor. Scaling factors (SF), which are used to modify the coefficients during watermark embedding process, profoundly determine the level of robustness and imperceptibility. Ramanjaneyulu et al. [15] proposed a quality guaranteed robust image watermarking algorithm using Genetic Algorithm (GA). The objective of optimization was to provide maximum possible robustness without exceeding a predefined distortion limit. The authors in [16] proposed an efficient watermarking scheme which can achieve the desired robustness level without causing significant distortion in the original image. They employed particle swarm optimization algorithm in the scheme to find the optimum multiple scaling factors.
So far, a lot of researchers across the globe have conducted different studies in the field of watermarking and they have proposed several schemes for different applications. But, still there exist some challenging gaps in the area which requires further study. The first challenge is designing a watermarking scheme which can achieve improved robustness and imperceptibility while maintaining better trade-off between them. The other is the challenge of practical implementation. Due to computational complexity and large memory requirement, some proposed schemes are infeasible and uneconomical for practical application. To address aforementioned problem and fill the existing gape, in this paper, we have proposed a new, efficient watermarking scheme which can simultaneously meet imperceptibility and robustness requirement. The scheme uses LWT to avoid rounding error and reduce computational complexity which will occur due to traditional DWT. DCT is another transform which is used to improve the robustness of the scheme against noising, compression, sharpening and filtering attacks. A binary watermark is embedded into the image by modifying the singular value using optimized multiple scaling factors. The two sub-images which are formed from blocks based on the number of edge pixels are used as a reference point for watermark embedding and extracting. Therefore, the scheme requires neither original image nor a watermark for the extraction process. Since our proposed scheme is able to achieve good imperceptibility and improved robustness and is free from false positive problem, it can be an ideal choice for copyright protection application.
-
III. The Mathematical Preliminaries of used Transforms
-
A. Lifting wavelet transform
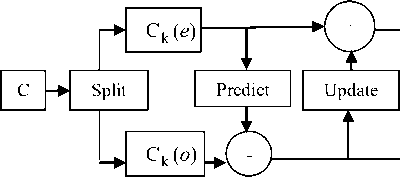
The existing proposed watermarking schemes using traditional wavelet transform have some drawbacks. Since the traditional wavelet transform is a floating point algorithm, the limited ability of a computer to process a finite word length will result in rounding error, and the process of reconstructing the exact signal becomes unattainable. Furthermore, the traditional wavelet transform technique requires sophisticated computation facilities, and this makes hardware implementation to be complex and uneconomical. To overcome the problems the lifting wavelet transform (LWT) technique has been adopted in this paper. LWT is a more flexible technique, and it was first introduced by W. Sweldens in 1995 [17]. The technique inherits multi-resolution properties of traditional wavelet transform and adds new other properties. The primary procedure of LWT involves three main operations, namely splitting, predicting and updating.
Splitting: This operation divides the original signal, C into two sample sets: even C ( e ) and odd C ( o ) sets.
C k ( e ) = C 2 k , 1
C k ( o ) = C 2 k +J
Predicting: In this phase, odd samples are predicted from even samples and the difference between the odd samples, and the predicted result is taken as a high-frequency coefficient of the next level.
C k ( o ) = P ( C k ( e )), C k ( o ) = C k ( o ) - P ( C k ( e )).
Updating: This step produces the low-pass coefficient by adding the original even sample and the predicted odd sample after updating them using an update operator.
C U ( e ) = C k ( e ) + U ( C D ). (3)
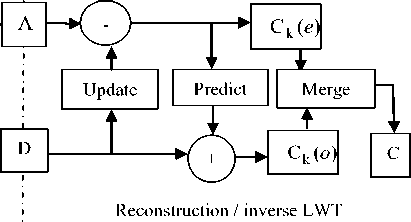
The inverse lifting wavelet transform (ILWT) is obtained by inverting the forward steps and replacing the split operator with a merge operator. In Fig. 1, the block diagram of forward and inverse lifting wavelet transform procedure is shown [18].
-
B. Discrete cosine transforms
Discrete cosine transform (DCT) is a well-known transform method that converts an image from a spatial domain to a frequency domain. Let 2D image of size M×N is defined as, F= {g (x, y), x=0, 1, 2… M, y=0, 1, 2… N}, then formulae for forward DCT and inverse DCT can be given as:
M - 1 N - 1
G ( u , v ) = a ( u ) a ( v ) £ £ g ( x , y )cos x = 0 y = 0
(2 x + 1) u n 2 M
where a ( u\ a ( v ) = ^, for
u,v =0, and a ( u ), a ( v ) = 1,
cos
(2 y + 1) v n 2 N
(4) for u =1,2,..., M and v =1,2,., N .
M - 1 N - 1
g ( x , y ) = a (u ) a ( v ) S Z G ( u , v )cos u = 0 v = 0
(2 x + 1) u n
2 M
X
cos
(2 y + 1) v n 2 N
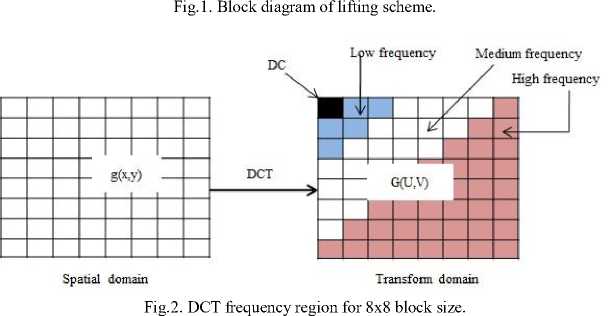
Fig. 2 shows the various frequency regions of 8×8 block size DCT coefficients [13]. In this proposed algorithm, we have used DCT to mitigate the limitation of SVD and improve the robustness of the scheme to noise, compression, sharpening and filtering attacks.
Decomposition / forward LWT
-
C. Singular value decomposition
From the perspective of image processing, a digital image can be viewed as a matrix such that pixels intensity values are considered as elements of the matrix. Thus, SVD which is a linear algebra technique can be used in digital watermarking due to its unique properties. SVD factorize an image F of size M×N into three unique matrices U, S and V such that,
|
u 11 ' |
■ u 1 M |
s 11 |
0 |
||
|
F = USV T = |
u 21 ■ |
u 2 M |
X |
0 |
s 22 |
|
( u M 1 ■ |
■ uMM J |
. 0 |
0 |
T v11 - v1 N v 21 - v 2 N
,0
s MN J
.vN 1 ■•■ vNN J where F e«MXN , U еЭТMXM , S e«MXN and V g^NXN . The matrix U and V are called the left and right singular vectors. Since U and V are orthogonal matrices, then
UU T = U T U = I , VV T = V T V = I .
The matrix S is a nonnegative diagonal matrix containing the square root of the eigenvalues of either U or V, and the elements are arranged in descending order (i.e. S [ [> s 22^— Sm v ). The process of singular value decomposition begins with pre-multiplying both sides of expression (6) by FT.
FTF = ( USVT ) T ( USVT ) = VS T U T USV T . (8)
FFT = ( USV T )( USVT ) T = USTVTVSUT . (9)
Based on (7), UUT and VVT give the identity matrix I and STS= SST=S2 because S is diagonal matrix.
Inserting the expression into (8) and (9) we can obtain
F T F = VS 2 V T ,'
T 2 Г [ (10)
FFT = US 2 UT .
Since the result of multiplication FTF and FFT is a symmetrical matrix, the problem FTF=VS2VT and FFT=US2UT can be solved by using Eigen-decomposition operation. For square matrix F of size k^k , if X is an associated Eigenvalues then:
FV j = XV j , for j = 1,2,... k , (11)
where, v is called eigenvector of matrix F, associated with eigenvalues X.
Using identity matrix I of size k×k, the expression (11) can be rewritten as,
Fv, = XIv,, I jj (12)
( F - XI ) Vj = 0. J
Equation (10) will have non-zero solution if the determinant of (F- XI) is equal to zero, (i.e. | F- XI) |=0). Solving this equation, eigenvalues of the matrix can be obtained. For each eigenvalues, the corresponding eigenvectors can be found by plugging back into expression (11). Singular matrix S is obtained by taking the square root of the eigenvalues and populating them diagonally in descending order. The process to calculate the right singular vector U follows the same steps as calculation of V.
In this paper, we have employed block based SVD to embed a binary watermark by modifying singular values using multiple scaling factors. The following are the benefits that we can obtain when we use SVD technique in image watermarking scheme.
The visual quality of the cover image is not affected significantly due to a slight change of singular values.
Singular values have good stability and their values are rotationally invariant.
SVD can a pack large energy signal within few coefficients.
-
IV. PSO based Scaling Factor Optimization
In watermarking, robustness and imperceptibility highly depend on the quantity of signal embedded. Scaling factors which are used to modulate the coefficients during watermark embedding can control the quantity. Therefore, the problem of finding suitable scaling factors, which can give optimum performance and maintain the trade-off between imperceptibility and robustness, can be viewed as an optimization problem. However, some authors use a trial-and-error method to set the value of these scaling factors. Indeed, suitable optimized scaling factors can be obtained using metaheuristic optimization algorithms. For robustness R and imperceptibility Q, the optimization problem can be defined as,
Maximize : R ( a ), 1
k I (13)
Mantaining : Q(a ) ^ QTи, J where αk is scaling factors and QTh is a user defining quality threshold. Putting the above objectives into consideration, we have formulated the fitness function (ff) as follows.
n f = Max {PSNR(F, Fw ) + /^ NCC(W, We ) }, (14)
i = 1
where PSNR (.) and NCC (.) are metrics to measure imperceptibility and robustness respectively, and their definition is presented in section VI. F and Fw are an original host image and a watermarked image respectively; while W and WE are an original watermark and extracted watermark respectively.
In this paper, we have used particle swarm optimization (PSO) to find optimized scaling factors that can provide the best compromise between robustness and imperceptibility. PSO algorithm was first developed by Eberhart and Kennedy in 1995 [19]. The algorithm starts a searching process by initializing particles randomly having position, xi(t) and velocity, vi(t). Then, the quality of each particle is evaluated using a fitness function (also known as objective function), and based on their fitness score both personal best (pbest) and overall global best (gbest) are determined. Until the predefined stopping conditions are satisfied, the algorithm continues searching the optimum value by updating the velocity and position using formulae, vi( t + 1) = Wivi(t) + C, rand (Pbest - Xi(t)) + (15)
C2rand (gbest -xi(t)), x (t +1) = x (t) + v (t +1), (16)
where wi is inertia weight which determines the step size and C1 and C2 are learning factors which determine the effectiveness of local and global learning. The term ‘rand’ refers to an operation which randomly generates numbers between 0 and 1. In Fig. 3, the flowchart of PSO based solution searching and objective value calculation is shown.
-
V. Proposed watermarking scheme
Digital image watermarking scheme based on feature detection based reference sub-image forming technique becomes a popular strategy to improve the performance of the scheme and enables designers to select the best region (or blocks) of the image for watermark embedding
-
[16] . The blocks having the desired feature are used as a reference point for watermark embedding and extraction. There exist different feature extracting methods, and in this study, we have used canny edge detector due to its superior performance in edge detection. Thus, a watermarking scheme using edge detection based reference sub-image (EDBRI) forming technique is proposed. A flowchart of EDBRI forming technique is shown in Fig. 4, and from the figure, we can observe that two sub-images are formed from selected significant blocks. The first sub-image, which is formed from blocks having largest number edge pixels, is used as a region for watermark embedding and the other one is used as a
Список литературы A new robust and imperceptible image watermarking scheme based on hybrid transform and PSO
- G. C. Langelaar, I. Setyawan, and R. L. Lagendijk, “Watermarking digital image and video data. A state-of-the-art overview,” IEEE Signal Process. Mag., vol. 17, no. 5, pp. 20–46, 2000.
- C.-H. Chou and K.-C. Liu, “Robust and transparent watermarking scheme for colour images,” IET Image Process., vol. 3, no. 4, pp. 228–242, Aug. 2009.
- S. Bajracharya, R. Koju,"An Improved DWT-SVD Based Robust Digital Image Watermarking for Color Image", International Journal of Engineering and Manufacturing (IJEM), Vol.7, No.1, pp.49-59, 2017.
- N. M. Makbol and B. E. Khoo, “Robust blind image watermarking scheme based on Redundant Discrete Wavelet Transform and Singular Value Decomposition,” AEU - International Journal of Electronics and Communications, vol. 67, no. 2, pp. 102–112, 2013.
- A. Dixit, R Dixit, "A Review on Digital Image Watermarking Techniques", International Journal of Image, Graphics and Signal Processing(IJIGSP), Vol.9, No.4, pp.56-66, 2017.
- V. S. Verma and R. K. Jha, “LWT–DSR based new robust framework for watermark extraction under intentional attack conditions,” Journal of the Franklin Institute, vol. 354, no. 14, pp. 6422–6449, 2017.
- Y. Wang, X. Bai, and S. Yan, “Digital image watermarking based on texture block and edge detection in the discrete wavelet domain,” In Proc. IEEE International Conference on Sensor Network Security Technology and Privacy Communication System, 2013.
- B. E. Khoo, N. M. Makbol, and T. H. Rassem, “Block-based discrete wavelet transform-singular value decomposition image watermarking scheme using human visual system characteristics,” IET Image Process., vol. 10, no. 1, pp. 34–52, Jan. 2016.
- G. Çetinel, L. Çerkezi,"Robust Chaotic Digital Image Watermarking Scheme based on RDWT and SVD", International Journal of Image, Graphics and Signal Processing (IJIGSP), Vol.8, No.8, pp.58-67, 2016.
- R.-S. Run, S.-J. Horng, J.-L. Lai, T.-W. Kao, and R.-J. Chen, “An improved SVD-based watermarking technique for copyright protection,” Expert Syst. Appl., vol. 39, no. 1, pp. 673–689, Jan. 2012.
- W. Yongdong, “On the security of an SVD-based ownership watermarking,” IEEE Trans. Multimed., vol. 7, no. 4, pp. 624–627, Aug. 2005.
- R. Liu and T. Tan, “An SVD-based watermarking scheme for protecting rightful ownership,” IEEE Trans. Multimed., vol. 4, no. 1, pp. 121–128, 2002.
- S. Fazli and M. Moeini, “A robust image watermarking method based on DWT, DCT, and SVD using a new technique for correction of main geometric attacks,” Optik - International Journal for Light and Electron Optics, vol. 127, no. 2, pp. 964–972, 2016.
- I. A. Ansari, M. Pant, and C. W. Ahn, “Robust and false positive free watermarking in IWT domain using SVD and ABC,” Engineering Applications of Artificial Intelligence, vol. 49, pp. 114–125, 2016.
- K. Ramanjaneyulu and K. Rajarajeswari, “Wavelet-based oblivious image watermarking scheme using genetic algorithm” IET Image Processing, vol. 6, no. 4, pp. 364, 2012.
- T. T. Takore, P. R. Kumar, and G. L. Devi, “Robust Image Watermarking Scheme Using Population-Based Stochastic Optimization Technique,” International Journal of Image, Graphics and Signal Processing, vol. 9, no. 7, pp. 55–65, Aug. 2017.
- W. Sweldens, "The lifting scheme: A construction of second generation wavelets." SIAM journal on mathematical analysis, vol. 29, no. 2, pp. 511-546, 1998.
- N. M. Makbol and B. E. Khoo, “A new robust and secure digital image watermarking scheme based on the integer wavelet transform and singular value decomposition,” Digit. Signal Process., vol. 33, pp. 134–147, Oct. 2014.
- J. Kennedy and R. Eberhart, “Particle swarm optimization,” Proceedings of IEEE International Conference on Neural Networks, Piscataway, NJ.vol. 4, pp. 1942–1948.1995.
- V. S. Verma, R. K. Jha, and A. Ojha, “Significant region based robust watermarking scheme in lifting wavelet transform domain,” Expert Systems with Applications, vol. 42, no. 21, pp. 8184–8197, 2015.


