A Novel Approach for Spectrum Access Using Fuzzy Logic in Cognitive Radio
Автор: Ila Sharma, G. Singh
Журнал: International Journal of Information Technology and Computer Science(IJITCS) @ijitcs
Статья в выпуске: 8 Vol. 4, 2012 года.
Бесплатный доступ
In this paper, we have proposed a novel approach using Fuzzy Logic System (FLS) for the potential management of the spectrum access. We have used four descriptors such as spectrum utilization efficiency of the secondary user, mobility, distance of the primary user, and signal strengths of the secondary users. On the basis of these descriptors, there are 81 fuzzy rules have been setup, which are based on the linguistic knowledge. The output of the FLS provide the possibility of accessing spectrum band for secondary users and the user with the greatest possibility has to assigned the available spectrum band.
Cognitive radio, Fuzzy logic system, Opportunistic spectrum access, Knowledge-based spectrum access scheme
Короткий адрес: https://sciup.org/15011719
IDR: 15011719
Текст научной статьи A Novel Approach for Spectrum Access Using Fuzzy Logic in Cognitive Radio
Published Online July 2012 in MECS
Cognitive radio is an intelligent wireless communication system, which is aware about its environment and adopts the statistical variation in the input keeping objectives in mind that highly reliable communication with efficient utilization of radio spectrum without causing the interference to the primary user or licensed user [1-6]. Recently, the concept of opportunistic spectrum access has emerged as a potential way to dramatically improve the spectrum utilization by cognitive radio to adopts the opportunistic spectrum access approach, which allows the secondary users to access the spectrum hole efficiently [3, 4]. The primary users have provision to access the communication channels at any time, whereas secondary users need to sense the radio environment, and opportunistically utilize the available spectrum [7]. Meanwhile, they need to adapt to the local behaviours of primary users and vacate the spectrum immediately when the presence of primary users has detected, which is the case of spectrum handoff [8, 9]. The design of cognitive radio is very challenging due to complexity, modularity, information imprecision and mobility issues [10]. The opportunistic spectrum access encounters several challenges such as: How to access the spectrum opportunistically without causing interference with other secondary users as well as primary user? How does a device sense and identify opportunities and coordinate their use? What should be the priority mechanism? How do we control such access to be in accordance with regulatory policies [11, 12]? In the research literatures on the opportunistic spectrum access, spectrum allocation using a graph colouring algorithm is proposed but mobility of the secondary users is not considered [13]. Some work using game theoretical analysis has been performed by Nie and Comaniciu [14] to find out the strategies for spectrum sharing. The opportunistic spectrum access via periodic sensing has also been discussed by Zhao, et al [15], where framework of constrained Markov decision processes is presented, which yields the negligible loss of throughput but the presence of more than two secondary users is not considered. The concept of opportunistic spectrum access and the listen-before-talk approach leads to overlooked spectrum an opportunity which has been discussed by Zhao [16]. For enhancing the performance of cognitive radio fuzzy logic based scheme is developed by Wanbin and Dong [17], where spectrum handoff issue with efficient utilization of spectrum bandwidth is discussed. The efficient decision making in the cognitive radio by fuzzy logic is also discussed by Matinmikko et al [18], which explored the application of fuzzy logic in telecommunication. The intelligent handoff algorithms and access scheme by fuzzy logic system for fourth generation network is also discussed in [19]. Coexistence beacon protocol (CBP) is proposed by using fuzzy logic to improve resource utilization and fairness in cognitive radio as well as mobility issue is also discussed in [20]. Opportunistic spectrum access by using fuzzy logic has been discussed by Qilang et al [21], they have used three descriptors or antecedents for developing the access scheme, which are spectrum utilization efficiency, distance of secondary users from the primary user, and its degree of mobility but they have not considered the signal strength of secondary user yet, authors have not consider the effect of channel variation due to multipath and fading, thus the reliability is low. So we have look forward to overcome this limit in the present work. To achieve these objectives, we have used four descriptors or antecedents, which are spectrum utilization efficiency of the secondary user, its degree of mobility, its distance to the primary user and signal strength of secondary users. On the basis of these descriptors 81 fuzzy rules have been set up, which are based on linguistic knowledge. The output of the fuzzy logic system provides the possibility of each secondary user, which has to be assigned spectrum band and the user with the greatest possibility will be assigned the available spectrum band.
The remainder of this paper is organized as follows. Section 2 gives proposed system model. Section 3 describes knowledge processing and opportunistic spectrum access. Section 4 presents the simulation results and discussion. Conclusion and future work are given in the final section.
-
II. Proposed System Model
The proposed FLS is as shown in Figure 1 where the system operates with four antecedents and one consequence as given below:
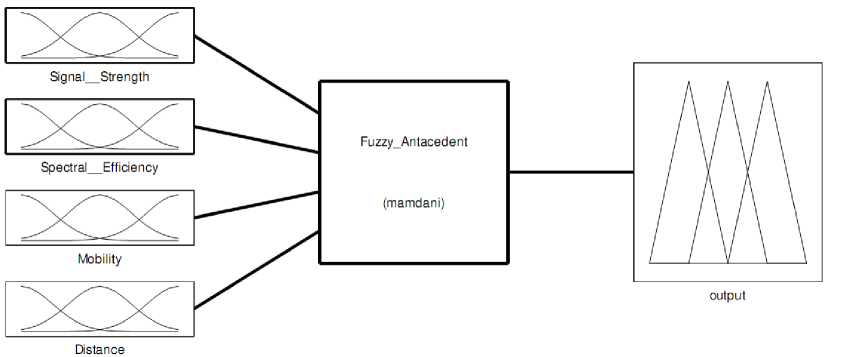
Fig. 1: Proposed FLS model structure.
Figure 1 shows the structure of a fuzzy logic system (FLS). When an input is applied to a FLS, the inference engine computes the output set corresponding to each rule. The defuzzifier then computes a crisp output from these rule output sets. Consider a p-input and 1-output FLS, using singleton fuzzification, center-of-sets defuzzification and ‘‘IF-THEN’’ rules of the form:
R l : IF x 1 is F 1 l and x 2 is F 2 l and . . . and x p is F pl ; THEN y is G l
Assuming singleton fuzzification is used, when an input x’ = {x1’, x2’, x3’……xp’} is applied; the degree of firing corresponding to the lth rule is computed as [21].
У co ( x ) =
2M cGiTi=1 H (xi) I Mi T^ H, (x-)
where M is the number of rules in the fuzzy logic system. Flow chart for this proposed scheme is as follow-
DEFINING MEMBERSHIP FUNCTION FOR EACH INPUT AND OUTPUT VARIABLE
DEFINING RULE LIST AND FUZZY OPERATOR IS USED WITH WEIGHT 1
where H and T both indicate the chosen t-norm [22]. There are many kinds of defuzzifier. In this paper, we have emphasized for illustrative purposes, on the center-of-sets defuzzifier. It computes a crisp output for the FLS by first computing the centroid, CGl ; of every consequent set Gl , and, then computing a weighted average of these centroids. The weight corresponding to the lth rule consequent centroid is the degree of firing associated with (1),
EVALUTION OF SYSTEM IS DONE, OUTPUT IS CALCULATED ACCORDING TO IF-THEN RULE
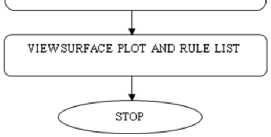
Fig.2 Flow chart for proposed scheme of opportunistic spectrum access.
-
III. Knowledge Processing and Opportunistic Spectrum Access
We have designed a fuzzy logic system to solve the opportunistic spectrum access problem in cognitive radio networks. We use the fuzzy logic system to take decision because it is conceptually easy to understand. The mathematical concepts behind fuzzy reasoning is very simple flexible. In this spectrum access scheme, we have used four antecedents or descriptor in fuzzifier as input. Expert knowledge for selecting the best suitable secondary user to access the available band is collected based on the following four antecedents:
-
1) Antecedent 1: Spectrum utilization efficiency,
-
2) Antecedent 2: Degree of mobility,
-
3) Antecedent 3: Distance to the primary user, and
-
4) Antecedent 4: Signal strength of secondary users.
We have taken “IF THEN” rules for conditional statement. Generally, the secondary user with the farthest distance to the primary user or the secondary user with maximum spectrum utilization efficiency can be chosen to access spectrum under the constraint that no interference is created for the primary user at this moment mobility of the secondary user should be low and the signal strength should be high. In the proposed approach, using the rule based FLS, we combine the above four descriptors to find optimal solutions to assign spectrum opportunistically. We see that different users will perceive different available spectrum and using spectrum efficiently and signal strength is the main purpose of the opportunistic spectrum access schemes. Hence, spectrum utilization efficiency n is introduced in proposed design and is defined as the ratio between the spectrum band which will be used by the secondary user and the available band [21].
BW n = ^ x 100% s BWa
where BWs and BWa are the spectrum bandwidth which is used by the secondary user and the total available bandwidth respectively. Mobility of the secondary user plays an important role in design. When the secondary user is moving at a velocity v m/s, it causes the Doppler shift [21, 22].
f d =
v cos #
c
Z 8=1 V« ^ F l ( x i )
У cos ( x ' ) =
Z 8‘ T i =. M f i ( x i )
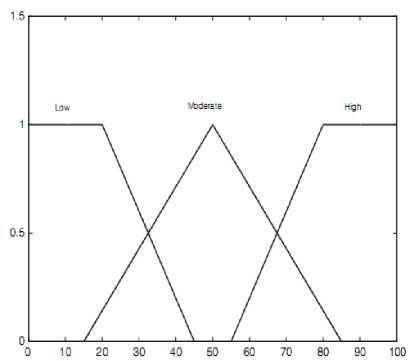
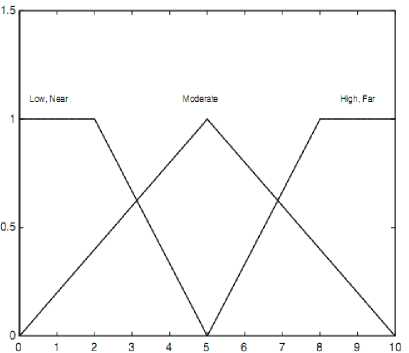
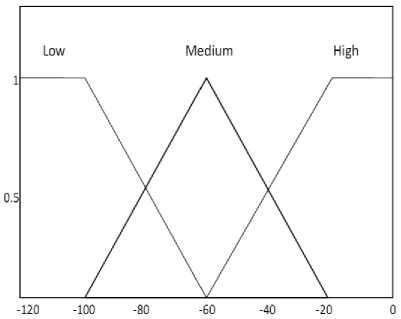
where l =1; 2; . . . 81; The linguistic variances used to represent the spectrum utilization efficiency, Signal strength and degree of mobility are divided into three levels: low, moderate, and high while we use three levels, which are near, moderate, and far to represent the distance. The consequence, that is, the possibility that the secondary user is chosen to access the spectrum is divided into five levels which are very low, low, medium, high and very high. We use trapezoidal membership functions (MFs) to represent near, low, far, high, very low and very high, and triangle membership functions to represent moderate, low, medium and high [24-26]. Membership functions are described in Fig. 2 [21]. Since we have four antecedents, we need to set up 34 = 81 rules for this FLS. Then, we design rules, which will be used to take decision, according to rules as follows:
(a)
(b)
Cl avg
l
Z wV i=1
I
Z w
i = 1
(c)
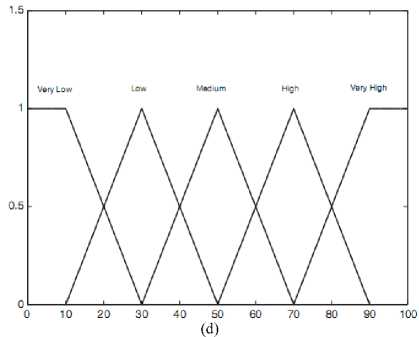
Fig. 2: Descriptors and output in linguistic variables form, where (a) is spectrum efficiency, (b) indicates mobility and distance, (c) represents signal strength and, (d) represents output.
“IF the spectrum utilization efficiency of the secondary user is moderate, its degree of mobility is low, its distance to the primary user is far and signal strength is high THEN the possibility that this user is selected to access the spectrum is ---------”here Cavg can be calculated through (5):
y ( x 1 , x 2 , x 3 , x 4 ) =
E27 ‘ ‘ ‘ ‘ । l=1 ^ ( x 1) ^F2( x^ ) ^( x3 ) ^F< ( x4 ) cavg
E27 ( ' A /'A /'A /'A l=1 ^( x 1 ) ^\. x 2 ) ^F3( x 3 ) ^4( x 4 )
The rules are defined based on the linguistic knowledge center of sets defuzzification method is used to calculate the output, according to which priority to access the spectrum is made while maintain the seamless communication [21].
-
IV. Simulation Results and Discussion
We recognize that (6) can be represented in a 2-D plot, which has been shown by Figure 3, where we fixed the mobility at moderate, varying distance at step size of two and consider the three cases of signal strength, which has been kept as low, moderate and high with varying efficiency and made it to in 2-d plot. Figure 3(b), 3(c) and 3(d) represents the opportunistic spectrum access decision plot for the cognitive user for these three cases respectively. From Fig 3, we see clearly that, at the same spectrum utilization efficiency and mobility degree, secondary users farther from the primary user have higher chance to access the spectrum. We also show the surface of three antecedent case for comparison purpose when signal strength has not been considered in Fig 3(a) we recognize that (6) is observed in a 4-D surface. Since it is impossible to plot visually, we fix one of four variables. More specifically, we fixed mobility of the primary user. We have taken the three descriptor case where signal strength of SUs is not considered for comparison purpose [21]. Mobility is fixed as moderate shown Fig 4(a), where distance and spectrum efficiency are varying but signal strength of secondary user is not considered. Similarly for observations, in our scheme we made the three cases as shown in figure 4(b), 4(c) and 4(d). Mobility is fixed as moderate and distance, spectrum efficiency are varying, but in first case shown in Fig 4(b), signal strength is kept as low, where in Fig. 4(c), signal strength is considered as moderate, and in Fig. 4(d) signal strength is considered as high.
Table 1: Rules for proposed fuzzy logic structure:
|
RULE# |
ANTECEDENT 1 |
ANTECEDENT 2 |
ANTECEDENT 3 |
ANTECEDENT 4 |
CONSEQUENCE |
|
1. |
LOW |
LOW |
LOW |
LOW |
VERY LOW |
|
2. |
LOW |
LOW |
LOW |
MEDIUM |
LOW |
|
3. |
LOW |
LOW |
LOW |
HIGH |
LOW |
|
4. |
LOW |
LOW |
MEDIUM |
LOW |
VERY LOW |
|
5. |
LOW |
LOW |
MEDIUM |
MEDIUM |
LOW |
|
6. |
LOW |
LOW |
MEDIUM |
HIGH |
LOW |
|
7. |
LOW |
LOW |
HIGH |
LOW |
VERY LOW |
|
8. |
LOW |
LOW |
HIGH |
MEDIUM |
LOW |
|
9. |
LOW |
LOW |
HIGH |
HIGH |
LOW |
|
10. |
LOW |
MEDIUM |
LOW |
LOW |
VERY LOW |
|
11. |
LOW |
MEDIUM |
LOW |
MEDIUM |
LOW |
|
12. |
LOW |
MEDIUM |
LOW |
HIGH |
MEDIUM |
|
13. |
LOW |
MEDIUM |
MEDIUM |
LOW |
VERY LOW |
|
14. |
LOW |
MEDIUM |
MEDIUM |
MEDIUM |
MEDIUM |
|
15. |
LOW |
MEDIUM |
MEDIUM |
HIGH |
MEDIUM |
|
16. |
LOW |
MEDIUM |
HIGH |
LOW |
VERY LOW |
|
17. |
LOW |
MEDIUM |
HIGH |
MEDIUM |
LOW |
|
18. |
LOW |
MEDIUM |
HIGH |
HIGH |
LOW |
|
19. |
LOW |
HIGH |
LOW |
LOW |
VERY LOW |
|
20. |
LOW |
HIGH |
LOW |
MEDIUM |
MEDIUM |
|
21. |
LOW |
HIGH |
LOW |
HIGH |
MEDIUM |
|
22. |
LOW |
HIGH |
MEDIUM |
LOW |
VERY LOW |
|
23. |
LOW |
HIGH |
MEDIUM |
MEDIUM |
MEDIUM |
|
24. |
LOW |
HIGH |
MEDIUM |
HIGH |
HIGH |
|
25. |
LOW |
HIGH |
HIGH |
LOW |
VERY LOW |
|
26. |
LOW |
HIGH |
HIGH |
MEDIUM |
MEDIUM |
|
27. |
LOW |
HIGH |
HIGH |
HIGH |
MEDIUM |
|
28. |
MODERATE |
LOW |
LOW |
LOW |
VERY LOW |
|
29. |
MODERATE |
LOW |
LOW |
MEDIUM |
LOW |
|
30. |
MODERATE |
LOW |
LOW |
HIGH |
LOW |
|
31. |
MODERATE |
LOW |
MEDIUM |
LOW |
VERY LOW |
|
32. |
MODERATE |
LOW |
MEDIUM |
MEDIUM |
LOW |
|
33. |
MODERATE |
LOW |
MEDIUM |
HIGH |
MEDIUM |
|
34. |
MODERATE |
LOW |
HIGH |
LOW |
VERY LOW |
|
35. |
MODERATE |
LOW |
HIGH |
MEDIUM |
LOW |
|
36. |
MODERATE |
LOW |
HIGH |
HIGH |
LOW |
|
37. |
MODERATE |
MEDIUM |
LOW |
LOW |
VERY LOW |
|
38. |
MODERATE |
MEDIUM |
LOW |
MEDIUM |
LOW |
|
39. |
MODERATE |
MEDIUM |
LOW |
HIGH |
MEDIUM |
|
40. |
MODERATE |
MEDIUM |
MEDIUM |
LOW |
VERY LOW |
|
41. |
MODERATE |
MEDIUM |
MEDIUM |
MEDIUM |
MEDIUM |
|
42. |
MODERATE |
MEDIUM |
MEDIUM |
HIGH |
HIGH |
|
43. |
MODERATE |
MEDIUM |
HIGH |
LOW |
VERY LOW |
|
44. |
MODERATE |
MEDIUM |
HIGH |
MEDIUM |
LOW |
|
45. |
MODERATE |
MEDIUM |
HIGH |
HIGH |
MEDIUM |
|
46. |
MODERATE |
HIGH |
LOW |
LOW |
LOW |
|
47. |
MODERATE |
HIGH |
LOW |
MEDIUM |
HIGH |
|
48. |
MODERATE |
HIGH |
LOW |
HIGH |
VERY HIGH |
|
49. |
MODERATE |
HIGH |
MEDIUM |
LOW |
LOW |
|
50. |
MODERATE |
HIGH |
MEDIUM |
MEDIUM |
MEDIUM |
|
51. |
MODERATE |
HIGH |
MEDIUM |
HIGH |
HIGH |
|
52. |
MODERATE |
HIGH |
HIGH |
LOW |
VERY LOW |
|
53. |
MODERATE |
HIGH |
HIGH |
MEDIUM |
MEDIUM |
|
54. |
MODERATE |
HIGH |
HIGH |
HIGH |
HIGH |
|
55. |
HIGH |
LOW |
LOW |
LOW |
VERY LOW |
|
56. |
HIGH |
LOW |
LOW |
MEDIUM |
LOW |
|
57. |
HIGH |
LOW |
LOW |
HIGH |
MEDIUM |
|
58. |
HIGH |
LOW |
MEDIUM |
LOW |
VERY LOW |
|
59. |
HIGH |
LOW |
MEDIUM |
MEDIUM |
LOW |
|
60. |
HIGH |
LOW |
MEDIUM |
HIGH |
MEDIUM |
|
61. |
HIGH |
LOW |
HIGH |
LOW |
VERY LOW |
|
62. |
HIGH |
LOW |
HIGH |
MEDIUM |
LOW |
|
63. |
HIGH |
LOW |
HIGH |
HIGH |
MEDIUM |
|
64. |
HIGH |
MEDIUM |
LOW |
LOW |
VERY LOW |
|
65. |
HIGH |
MEDIUM |
LOW |
MEDIUM |
MEDIUM |
|
66. |
HIGH |
MEDIUM |
LOW |
HIGH |
HIGH |
|
67. |
HIGH |
MEDIUM |
MEDIUM |
LOW |
VERY LOW |
|
68. |
HIGH |
MEDIUM |
MEDIUM |
MEDIUM |
MEDIUM |
|
69. |
HIGH |
MEDIUM |
MEDIUM |
HIGH |
HIGH |
|
70. |
HIGH |
MEDIUM |
HIGH |
LOW |
VERY LOW |
|
71. |
HIGH |
MEDIUM |
HIGH |
MEDIUM |
LOW |
|
72. |
HIGH |
MEDIUM |
HIGH |
HIGH |
HIGH |
|
73. |
HIGH |
HIGH |
LOW |
LOW |
LOW |
|
74. |
HIGH |
HIGH |
LOW |
MEDIUM |
HIGH |
|
75. |
HIGH |
HIGH |
LOW |
HIGH |
VERY HIGH |
|
76. |
HIGH |
HIGH |
MEDIUM |
LOW |
LOW |
|
77. |
HIGH |
HIGH |
MEDIUM |
MEDIUM |
HIGH |
|
78. |
HIGH |
HIGH |
MEDIUM |
HIGH |
VERY HIGH |
|
79. |
HIGH |
HIGH |
HIGH |
LOW |
VERY LOW |
|
80. |
HIGH |
HIGH |
HIGH |
MEDIUM |
HIGH |
|
81. |
HIGH |
HIGH |
HIGH |
HIGH |
HIGH |
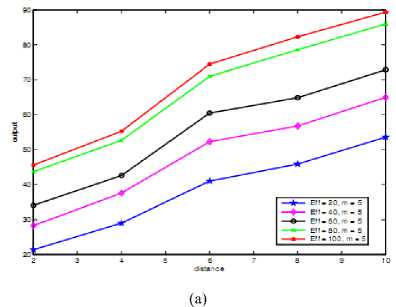
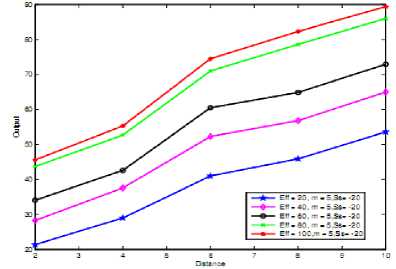
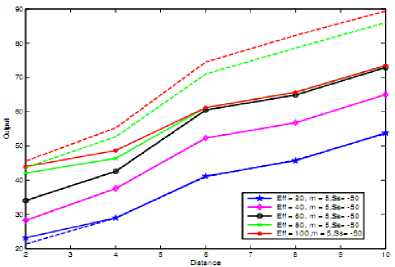
(b)
signal strength it is high, that means user with high Signal Strength is preferred. But other parameter also contribute major issues as distance, opportunity to access spectrum increases as distance increases ,and when efficiency is high. Mobility plays crucial role such that as it increases that is the number of handover increases priority for access the spectrum opportunistically decreases. Above all things can easily observed from the surface plot shown in Figure 4(a), 4(b), 4(c), and 4(d). From Fig. 3, we clearly see that, at the same spectrum utilization efficiency and mobility degree, secondary users further from the primary user with high signal strength have higher chance to access the spectrum. We have also compared our scheme with the scheme of opportunistic spectrum access (case of three antecedents with when signal strength is not considered) [21].
(c)
(a)
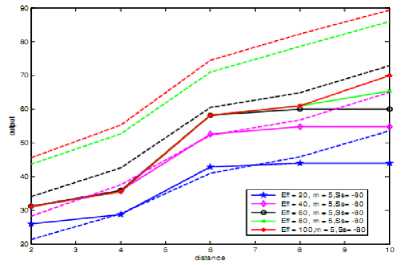
(d)
Fig 3. Observed 2-d plots in which,
(a) represent graph for three antecedents,
(b) represents case of four antecedents when signal strength is high, (c) represents medium signal strength and
(d) represents low signal strength.
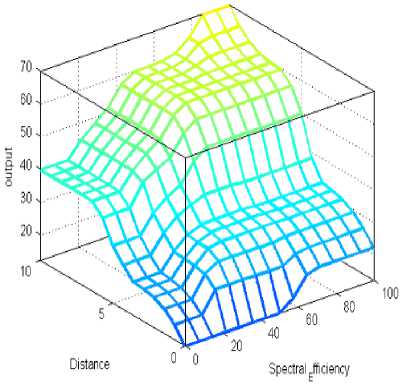
(b)
Opportunity to access spectrum calculated by (5) is calculated as low for low signal strength, and for moderate signal strength it is moderate and for high
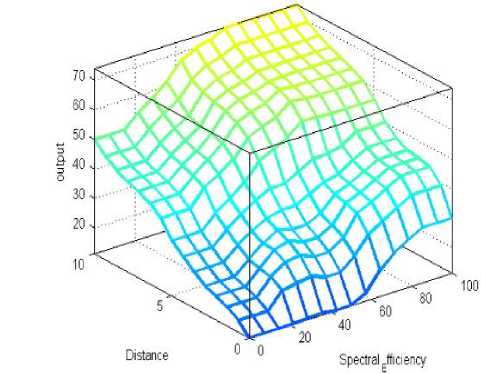
(c)
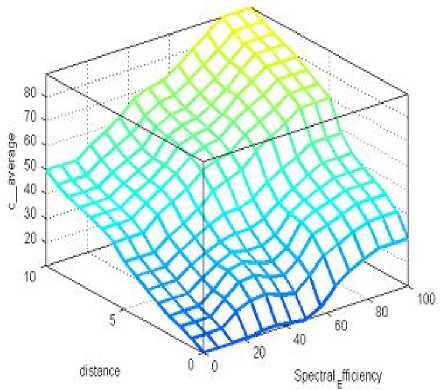
(d)
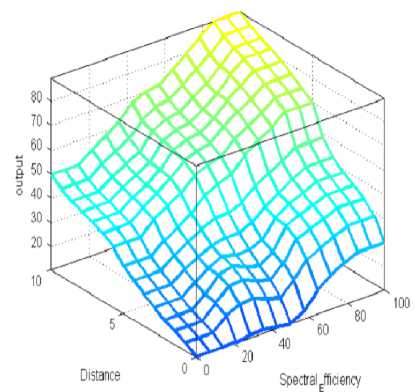
Fig. 4: Decision surface of combine three descriptor, where
(a) surface plot for three antecedents
(b) represents case of four antecedent when signal strength is high,
(c) represents medium signal strength and
(d) represents low signal strength.
We observed that in three antecedent case priority to access the spectrum is given to that secondary user which has high spectral efficiency with farthest distance from primary user, similarly in our scheme we observed same results but we have introduced the fourth antecedent as signal strength in the range of low, moderate and high which modifies the results in terms of accuracy i.e. it can observed from Fig. 4(a) and 4(b) that in case of low signal strength output or priority to access the spectrum calculated is low as compared the case of three antecedent, similarly for moderate signal strength it shows better result Fig 4(c), but when the case of high signal strength is considered we got the same result as for three antecedent. This shows that accuracy to give the priority to secondary users has been increased by introducing the signal strength as fourth parameter. Reliability of scheme is also increased as we scaled the accuracy in terms of fourth parameter introduced.
-
V. Conclusion
We have proposed a method based on the fuzzy logic system to control the opportunistic spectrum access for secondary users in cognitive radio networks. The secondary user is selected based on four antecedents (descriptors), which are spectrum utilization efficiency of the secondary user, its mobility, its distance to the primary user and Signal strengths. This scheme is based on linguistic knowledge, so that an acceptable decision can be obtained. As a result, we represent the opportunistic spectrum access decision surface. An opportunistic spectrum access scenario was analyzed and compared with the scheme [21] proposed for three antecedents approach. In proposed approach, we obtained the advantage over three antecedent’s scheme in terms of accuracy; moreover, we can modify the membership functions of descriptors in accordance to requirements of the primary user network and the spectrum policy. Hence, our approach is promising to be implemented practically in future cognitive radio networks. We see that it is better if the secondary user uses adaptive fuzzy logic system over the fixed rule based fuzzy logic system, in this way scheme will become more accurate and quality of service (QoS) degradation can be mitigated, as it will govern the adaptive rules for priority purpose to use the spectrum opportunistically.
Acknowledgement
The authors are sincerely thankful to the potential reviewers for their critical comments and suggestions to improve the quality of the manuscript.
Список литературы A Novel Approach for Spectrum Access Using Fuzzy Logic in Cognitive Radio
- S. Haykin, “Cognitive radio: brain empowered wireless communication”, IEEE Journal on Selected Areas in Communications, vol. 23, no. 5, pp .201–220, 2005.
- Jose Marinho and Edmundo Monteiro, “Cognitive radio: survey on communication protocols, spectrum decision issues, and future research directions”, Wireless Networks, vol. 18, no. 2, pp. 147-164, Feb. 2012.
- S. Mangold, S. Shankar, and L. Berlemann. “Spectrum agile radio: A society of machines with value-orientation” Proceedings of 11th European Wireless Conference, vol. 2, Cyprus, 2005, pp. 539–546.
- Nasrullah Armi, Naufal M. Saad, M. Zuki Yusoff and Muhammad Arshad, “Optimal sensing for opportunistic spectrum access in cognitive radio”, International Journal of Engineering, vol. 4, no. 3, pp. 243-253, July 2010.
- G Singh “Optimization of spectrum management issues for cognitive radio,” Journal of Emerging Technologies in Web Intelligence, vol. 3, no. 4, pp. 263-267, November 2011.
- S. Kapoor and G Singh, “Non-cooperative spectrum sensing: a hybrid model approach,” Proc. Int. Conf. on Devices and Communications (ICDeCom-11), 24-25 Feb. 2011, India, pp. 1-5.
- Eric Jung and Xin Liu, “Opportunistic spectrum access in heterogeneous user environments”, Proc. 3rd IEEE Symposium on Dynamic Spectrum Access and Networks (DySPAN), Chicago IL, 14-17 Oct. 2008, pp. 1-11.
- Ian F. Akyildiz, Won Yeol Lee, Mehmet C. Vuran, and Shantidev Mohanty, “NeXt generation/dynamic spectrum access/cognitive radio wireless networks: a survey”, Computer Networks, vol. 50, pp. 2127–2159, 2006.
- Yan Zhang, “Spectrum handoff in cognitive radio networks: opportunistic and negotiated situations”, Proc. IEEE International Conference on Communications (ICC), Dresden, Germany, 2009, pp. 1-6.
- Ekram Hossain, D Niyato, and Zhu Han, “Dynamic spectrum access and management in cognitive radio networks”, Cambridge University Press, New York, USA, 2009.
- C. Santivanez, R. Ramanathan, C. Partridge, R. Krishnan, M. Condell and S. Polit, “Opportunistic spectrum access: challenges, architecture, protocols”, Proc. 2nd Annual Wireless Internet Conf., Boston, August 2–5, 2006.
- Spectrum policy task force report, Technical report pp. 02-135, Federal communications commission (FCC), November 2002.
- H. Zheng and C. Peng, “Collabraton and fairness in opportunistic spectrum access”, Proc. IEEE International Conference on Communications (ICC 2005), 16-20 May 2005, vol. 5, pp. 3132-3136.
- N. Nie and C. Comaniciu, “Adaptive channel allocation spectrum etiquette for cognitive radio networks”, Proc. IEEE Dynamic Spectrum Access Networks (DySPAN), 2005, pp. 269–278.
- Qianchuan Zhao, Stefan Geirhofer, Lang Tong and Brian M. Sadler, “Opportunistic spectrum access via periodic channel sensing”, IEEE Transa. on Signal Processing, vol. 56, no. 2, pp. 785-796, February 2008.
- Qing Zhao, “Spectrum opportunity and interference constraint in opportunistic spectrum access”, Proc. IEEE International Conference on Speech And Signal Processing (ICASSAP), vol. 3, 15-20 April, 2007, pp. 605-609.
- Tang Wanbin, Peng Dong, “Spectrum handoff in cognitive radio with fuzzy logic control”, Journal of Electronics (China), vol. 27, no. 5, pp. 708-714, September, 2010.
- Marja Matinmikko, Tapio Rauma, Miia Mustonen, Ilkka Harjula, HeliS Arvanko and Aarne Mammela, “Application of fuzzy logic to cognitive radio systems”, IEICE Trans. Communication, vol. E92-B, no. 12, pp. 3572-3580, December 2009.
- Liu Xia and Jiang Ling Ge, “A novel vertical handoff algorithm based on fuzzy logic in aid of grey prediction theory in wireless heterogeneous networks”, Journal of Shanghai Jiaotong University (Science), vol. 17, no. 1, pp. 25-30, 2012.
- Shun-Fang Yang and Jung-Shyr Wu, “A spectrum sharing method based on fuzzy logic in IEEE 802.22 WRAN”, Proc. IEEE International Conference on Wireless Communication and Siganl Processing (WCSP), 21-23 Oct. 2010, pp. 1-5.
- Hong-Sam T. Le, Hung D. Ly and Qilian Liang, “Opportunistic spectrum access using fuzzy logic for cognitive radio networks” International Journal on Wireless Information Networks, vol. 18, pp. 171–178, 2011.
- J. M. Mendel, “Uncertainty rule based fuzzy logic systems”, Prentice Hall, pp. 345-377, Upper Saddle Rever, NJ, 2001.
- N. Hoven and A Sahai, “Power scaling for cognitive radio”, Proc. International Conference on Wireless Networks, Communications and Mobile Computing (ICWNC), 13-16 June 2005, vol. 1, pp. 250–255.
- Hongjie Liu, Zhong-Xu Wang, Shu-Fang Li, and Min Yi, “Study on the performance of spectrum mobility in cognitive wireless network”, Proc. 11th IEEE Singapore International Conference on Communication Systems (ICCS 2008), Guangzhou, November 19–21, 2008, pp. 1010-1014.
- L. Giupponi and A. Pérez-Neira, “Fuzzy-based spectrum handoff in cognitive radio networks”, Proc. 3rd International Conference on Cognitive Radio Oriented Wireless Networks and Communications (CROWN COM’), Singapore, May 15–17, 2008, pp. 1– 6.
- Marimin, Motohide Umano, Itsuo Hatono and Hiroyuki Tamura “Linguistic labels for expressing fuzzy preference relations in fuzzy group decision making”, IEEE Trans. on Systems, Man and Cybernetics Part B, vol. 28, no. 2, pp. 205–218, April 1998.


