A reliable solution to load balancing with trust based authentication enhanced by virtual machines
Автор: Rakhi, G.L.Pahuja
Журнал: International Journal of Information Technology and Computer Science @ijitcs
Статья в выпуске: 11 Vol. 9, 2017 года.
Бесплатный доступ
Vehicular Ad hoc network is the most fast growing which shape fresh engineering opportunities like controlling traffic smartly, optimal resource maintenance and improved service for customers. Vehicular Ad hoc Network (VANET) is one of the most popular ad hoc networks. A vehicular ad hoc network generally faces the problems like trust modeling, congestion, and battery optimization issues. If the nodes are comparatively less than it can handle the traffic well when it comes to transferring the data at a rapid rate. But, when it comes to high-density traffic than a Vehicular network always faces congestion problem. This paper tried to find the reliable solution to the traffic management by adding up the virtual gears into the network and optimizes the congestion problem by using a trust queue which is updated with the broadcast concept of the hello packets in order to remove the unwanted nodes in the list. The network performance has been measured with QOS Parameters like delay, throughput, and other parameters to prove the authentication of the research.
VANET, Load Balancing, Reliability, QOS, Virtual Gears
Короткий адрес: https://sciup.org/15016210
IDR: 15016210 | DOI: 10.5815/ijitcs.2017.11.07
Текст научной статьи A reliable solution to load balancing with trust based authentication enhanced by virtual machines
Published Online November 2017 in MECS
VANET (Vehicular Ad hoc Network) has attained an extraordinary popularity in the prevailing century because of the wide collection of the prospective applications [1]. The Vehicular Ad hoc Network has a significant application that enhances the technologies in the recent years by improving the vehicle performance in terms of jitter and battery utilisation [2]. The utilization of VANET has been risen due to this improvement, and new application is being produced that does not utilize battery provision and can analyze the delay from the environment.
Basically, throughput, delay minimization, and latency are supposed to be spontaneous and there is a swapping with these parameters [3]. The foremost intention of VANET is to accumulate the data from the surroundings and delivers the data to the position where the analysis and inspection of the data can take place. The Vehicles are selfconscious in the regards of computation, power, memory and the communication potential, due to the monetary and technical reasons. That is why most of the VANET analyses had concentrated on the latency scheme and the protocols with the algorithms [4]. Dynamic latency can also be computed as:
Jitter = . С . v2 . f (1)
where:
A= active gates c= capacitance load v^2= supply voltage f= frequency
Then it can be written as:
Jitter Dynamic = ∑ Dynamic .∆ t (2)
where:
Jdynamic = dynamicJitter
Δt= dynamictime
The applications of the VANET are extremely explicit, for instance, military applications, health info, environmental monitoring, Smart Home [5]. But now, the protocols that are emerging depends basically on some special applications that bring immense problem in VANET designing with function, customizable designing following VANET reconfigurable network structure.
Passing by System





Monitoring System


Vehicles

Fig.1. Vehicular Adhoc Network
VANET possesses moving devices, known as vehicles are positioned in a particular pattern and area [6]. They can interact with each other through the transmission of the data as depicted in fig. 1. This network has “Base station” where the collected data is broadcasted [7]. The Base Station is further connected to the device that observes the entire system that can be a server/mainframe. This development has not only created an innovative prospect, but also raised number of challenges for the investigations in the sensor vehicles such as to support multi-hop communication when the constraint is being set up in radio operation for conserving the power, challenges in geographic routing, monitoring and preservation of dynamic, resource limited systems with the clarification of the challenge [8].
VANET comprises the power management as a necessary standard. A VANET can be very small consisting of 10 vehicles or it can be very big consisting of hundreds/ thousands vehicles (Large geographical monitoring). In the real time industry, the sensor readings may face failure or drop or a very long latency due to congestion [9]. This paper has attempted to solve the following problems in VANET which are:
-
• Reliability
-
• Congestion
-
• Packet Delivery on Timely fashion.
-
II. Related Work
Virtual machines are considered as an approach which is employed to reduce that load on the network. There are number of solutions proposed by the researchers in the past regarding the load balancing by using virtual machines. Each solution has its different results as compared to other solutions. Each researcher has adopted a different technique in order to reduce the load. Some of the studies related to this are presented below:
Deepa Das et al, [1], attempted to calculate the performance of cognitive radio in VANET through the describe metrics taking into account the spatial correlation in the decisions taken by vehicular secondary users which are local to network in the existence of primary user emulation attack. With the proposed algorithm the energy efficiency has been maximized as the vehicular secondary users were allocated proper power allocation. This proposed algorithm was based on the genetic algorithm under a constraint of power control which helps in restricting the negative impact of the attacker. The energy efficiency (EE) maximisation problem was resolved by the parametric transformation which is dependent on the Dinkelbach method and the second problem of non-convex constraint was solved by making use of adaptive methods or algorithms. The results showed that EE was improved by including the constraint as power control.
Xinming Zhang et al,[2] proposed an abiding geo-cast protocol that is based on the carrier sets. The uncovered vehicles which were passing by the destination region can have abiding messaged from the nearby vehicles at one-hop delivery. This process avoid a lot of overhead which is produced by multi-hop broadcast. Hence, the receiving probability was enhanced through this whole network. The results showed the efficiency and reliability of the network.
Yu Wang et al,[3] proposed an analytical model to analyze the connection within the average delay while presenting road condition information and the gap among two neighbour RSUs that are stationed beside the road in a beeline expressway situation. The vehicle speed, vehicle density, likelihood of an incident, and the distance between two RSUs are the factors that are taken into consideration by the proposed model. The effectiveness of the model can be verified from the simulation results. If the delay confinement of the time-determined purposes, then this model can be adopted to predict the average gap permitted within the two neighbour RSUs, which further provides a reference for the stationing of the RSUs in before-mentioned situations.
-
III. Simulation Model
The proposed algorithm is divided into four parts:
-
A. Setting up the network
-
B. Broadcast
-
C. Development of trust Model
-
D. Load Balancing
A network is setup having the following parameters:
Table 1. Network Parameters
|
Network width |
1000 m |
|
Network height |
1000 m |
|
Vehicles |
50, 100, 200 |
|
Coverage Length |
20 % of width |
|
Coverage Parameter |
Distance Between the vehicles |
|
Delay Model [14] |
Random Delay Model |
-
A. Setting up the network
The set-up phase consists of three different vehicle counts: 50,100 and 200. All the wireless sensor vehicles have been deployed randomly [10]. To maintain uncertainty into the network, the delayvehicle has been provided with random values of delay, battery units and consumption unit. Now, as in real-time scenario, it is apparent that some of the vehicles will be in sleep state due to:
-
• Power management mode
-
• Critical due to battery issues
-
• Dead due to environment conditions
The active and sleep states have been designed as follows:
Active-Sleep state of the vehicles // description: input;
Function act [f]=Activesleep(n)
n=total vehicles
For i=1:n output:K=round(rand)
-
f : state of the vehicle [active or sleep]
f[i]= “sleep”;
else
f[i]= “Active”
endif
Now, the vehicles will be deployed in the network with random locations to maintain the uncertainty in the network.There would be source and destination which would be involved in the data packet communication. A path is required through which the data packets would be transferred. If a situation is considered when the data has to be transferred for the first time and no vehicle is involved in any communication previously. In such a situation, it is very difficult to choose a path which is secure and fits in the budget.
-
B. Broadcast
To resolve the problem occurred at stage 1, the proposed algorithm uses the concept of broadcast when the communication link is broken or there is no communication link [11].
In figure 2, Vehicle A wants to transfer the data to the Vehicle B, but the information cache of A is empty. UN denotes unknown vehicle and hence, ‘A’ cannot directly send the data to unknown vehicle. Here, as per the algorithm, there is no channel of communication. Vehicle A will broadcast the requirements and will transfer a Welcome Packet(WP) into the network. If it receives any acknowledgement within a time frame ^wait , then it follows method A else it follows method B as explained below.
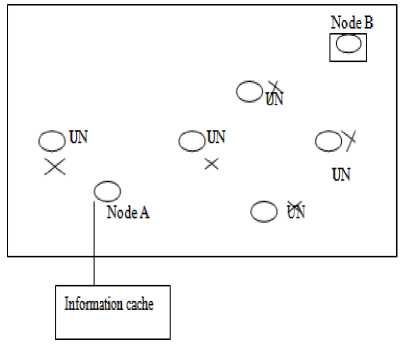
Fig.2. The first communication situation
Method A: List up all the responders and calculate the delay with the help of radio delay model [RDM]. As per RDM,choose the least delay consuming vehicleand transfer the data through that vehicle.
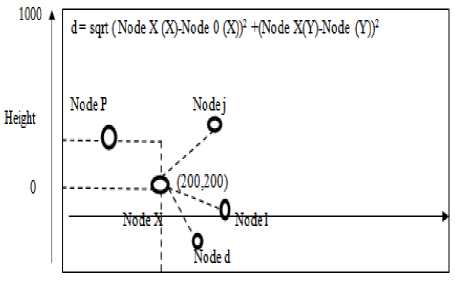
Fig.3. Coverage Set calculation
Method B: Find the coverage set of the current transmitting vehicle and choose any element in the coverage set. Store the element into the cache memory and proceed till the destination is not attained. For the next iteration, it again start from method A.
The mathematical description of both method A and B is as follows:
Method A
T N= Transmitting vehicle:
T „ . broadcast (“hello”) = true;
Rsq = Response queue
Wait for a time frame of t wait
Rqcounter=0;
If response.positive==true
Rsq [rqcounter]=Responder.Address
Rqcounter=rqcounter+1;
Endif
If request>0
Initialize REM
T XS= Transmitting Delay consumption in Joules of the current sender
R XS= ReceivingDelay consumption
For each nj in the rsq
Find min( T XS + R XS ) ;
Add min_vehicle_id to pathlist ();
Continue making path length till the destination is not attained;
End for
End if
Method B
Let λ be the coverage distance of any vehicle
λ = width * 25/100;
Co_list=[ ]; cov_dist =[ ];
For each n j in vehiclelist xi= xloc (n j ); // finding the xlocation of the vehicle yi= yloc (n j ); // finding the ylocation of the vehicle;
Covcount=0;
For each nj in the vehicle list
If nj != nj // if both the vehicles are not same xP = xloc (nj);
y p = yloc ( n j);
d = sqrt( ( x i -хp)2+(yi -yp));
if d<=λ cov_list [nJ,covcount]=nj ; cov_dist [nJ,covcount]=d;
covcount=covcount+1;
end if end for end for
Cov_list = [Vehicle d, Vehicle p, Vehicle j, Vehicle l]-Vehicle x
Cov_dist = [220,240,250,245];
Now X will transfer the data to the vehicle which is nearest to Vehicle X that is Vehicle d. Furtheron, Vehicle d will follow the same procedure as that of vehicle X. the chain will continue till the destination is not attained. Method B will be followed only when the broadcast response list is empty.
-
C. The Trust Model
Wireless network faces latency and load balancing problem due to absence of a trust model.The network has to select the path every time to transmit the packet data. In this procedure, the network has to look for available vehicles without considering the fact that whether the vehicles would be trustworthy or not. The search and solution process consumes a lot of time and delay, thus, increases the battery consumption if the data packet not delivered properly. To avoid such delay in addition to the broadcast concept a trust model is proposed. The key aspects of the trust model are as follows [12]:
-
a. If a vehicle X delivers a packet successfully between source S, and destination D,then the proposed algorithm put the vehicle into the trust list for the path P(S, D). The vehicle remains in the trust list as long as it does not start consuming delay more than ∆E for the packet transfer.
-
b. The proposed architecture in world involve a monitor system deployed into the network to check the following specification:
-
• If the vehicle X is changing its position from the co-ordinates (Xx,Yy) to (X x̅ ,Y y̅ ), but still remains in the coverage set of transferring vehicle as per method B.
-
• If the vehicle X is consuming delay less than ∆Eor not is deleted from the trust list.
-
D. The load balancing algorithm
The mathematical description of the VM creation and sharing of load are as follows [14]:
VM Creation algorithm
VM_N=function create VM(Node_Id,
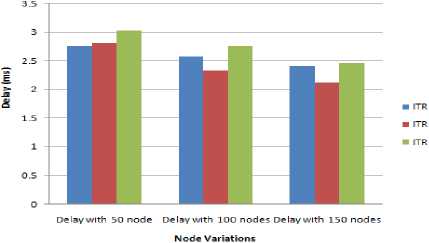
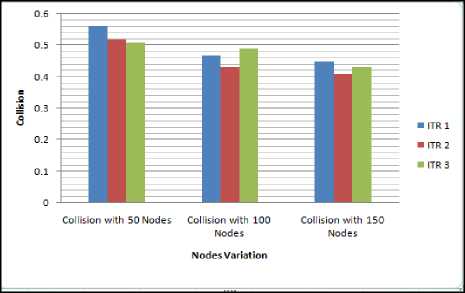
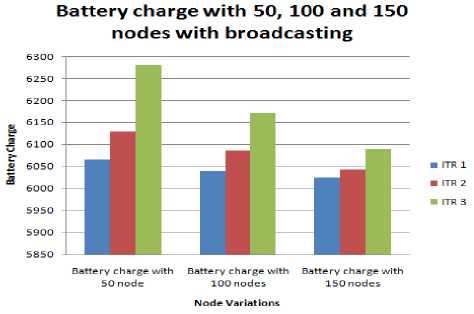
Node_E,NSink_space,VM_list_N,VM_req // Input Parameters has to be constructed // Node_E physical node // N_Sink_Space personal sink // VM_List_N Node_Id: Node at which VM Available Energy at the Space available in nodes It is an array which contains the list of VMs which the physical node contains. If the permittable VM count is already attained then the VM cannot be created // P count Permittable count of VMs at physical machine // VM_req VM requirements list If (VM_req [e_required]<(Node_E_10) If (Nsink_space>VM_req[s_required]) Add_VM_to_VM_List (VM_Id,VM_req,Node_Id,VM_list, node_prop); End if End if End if End function Function to_VM_List(VM_Id,VM_req,VM_Id,VM_list) Add_VM Count=VM_List[count]; //total member of VMs already in VMlist VM_List[count+1] =VM_Id; Node_prop[memory]=Node_prop[Memory]-VM_req[Memory]; Reduce the physical node memory upto the memory taken by VM_memory Node_prop[totalspace]=Node_prop[totalspace]- VM_space; Endfunction As soon as the VM will be considered, the memory and the space occupied by the VM will be reduced from the physical memory. Algorithm 1: Modified Best Fit Decreasing (MBFD) Input_In: hostList, vmList;Output_Op: allocation of VMs where HL= Host list, VL= VM List and ML= Migration list VL→ decreasing_ utilization_sort For each VM →VL Find Minimum_power→maximum Allocation of Host→NULL (0) For each Host →HL Do, Host = max_ resources Find Power→ (Host, VM) Power RETURN Minimization of Migration (MM) Input: HL Output: ML, where HL= Host list, VL= VM List and ML= Migration list For each Host →HL For each VM →VL VL→ decreasing_ utilization_sort hUtil→h.getUtil() Find best HL For each VM →VL if VL>HL- THRESH_UP then t←VL- HL+ THRESH_UP if t Best util fn.→t bestFit VM→vm else best Fit VM→vm break RMOVE best Fit VM GET Migration List RETURN ML Node Substitute Solution Increasing number of nodes will support a substitute methodology in the proposed work. When number of node increases, in case of failure the network will have more number of options to choose and to select transferring node rapidly [14]. This will support the improvement of the battery life as the search space will be reduced[15] IV. Simulation Results For the design of this approach, broadcasting method is being considered for quality of service (QoS) parametersparameters. The main goal of the proposed algorithm is to have the minimum energy consumption and optimum QOS parameters. There are different simulation parameters used by distinct authors to propose their theory in balancing the load in the network by using the virtual machine (VMs). The main purpose of the parameters are to evaluate the results of the algorithm or technique proposed in a way that the values can be defined in the graphical or mathematical way to prove our point of accuracy of the algorithm then the earlier proposed techniques. The various simulation parameters used in the research are: Throughput, energy, Delay and collisions. The numbers of nodes used are 50, 100 and 150 in 1000* 1000 networks. The detailed simulation parameters are shown in Table 2: Table. 2. Simulation Parameters Number of nodes 50, 100, 150 Network length 1000m Network Width 1000m Source node 20 No. of rounds 3 Fig.4. Throughput with 50, 100 and 150 nodes with broadcasting In the figure 4, the graphical representation of the throughput of the network with the variant nodes i.e. 50, 100 and 150 is described.The table 3, depicts the static value of the maximum and the minimum throughput attained by the broadcasting algorithm. The maximum throughput attained by broadcasting algorithm is 87.46, whereas the minimum throughput is 87.23 measured for 50 nodes. Similarly, the maximum throughput attained by broadcasting algorithm is 88.34, whereas the minimum throughput is 87.89 for 100 nodes and the maximum throughput attained by broadcasting algorithm is 89.45, whereas the minimum throughput is 88.22 for 150 nodes. Throughput must be high for the good working algorithm and in the proposed work the average throughput is 88.17. A high throughput reflects the good performance of the proposed technique. Table 3.Throughput with broadcasting No. of Iterations Throughput With 50 Nodes Throughput With 100 Nodes Throughput With 150 Nodes 1 87.23 88.34 89.45 2 87.46 88.23 89.43 3 87.34 87.89 88.22 0 NodeP Destination D Height ,0 Node (Xx Yy) 1 0 Node! Node (Xx, Yy) 0 Node В 0 NodeL coverage area of^ Width Fig.5. (a).Vehicle inside coverage area coverage О 7s, Node (XI Yy) Q Node В Q NodeL Fig.5. (b).Vehicle outside coverage area Destination D Node (Xx, Yy) 0 Node J Figure 5(a), shows that vehicle X ̅ has vehicle to different position but still coverable by Vehicle Xx, in this case Vehicle X ̅ will remain into the trust list as per the trust model. In Figure 5(b), the Vehicle X ̅ move to a new position and it is now it’s out of the coverage area of Vehicle Xx in such a scenario it will be deleted from the trust list. Insertion into the trust list Function create trust list = new function () If(Packet .transferred == true) If (E.transfer< ∆E) Trustlist(trustcount,1) = Sid Trustlist(trustcount,2)= Did Trustlist(trustcount,3) = Xid trustcount = trustcount + 1 End if End if Deletion from the trust list Function deletefromtrustlist = new function(Sid,Did,Xid) If !isempty(k) //Searching that whether there is any trust connection between the Sid,Did and Xid. If the search result is not empty then it means that there exists a trust connected which has to be deleted as the trust condition is violated. The Monitoring algorithm Function monitorvehicles = new function(Xloc,Yloc,Vehicles,Transmitting,Sources,Destin ation) Watch_timer(); Foreachnd in Transmitting Sources If isactive(nd)// if the transmitting vehicle is active or ready to transfer the data tn=find(trustlist(:,1)==nd); // find all the vehicles which are present into the trustlist connected to the transmitting vehicle. For i = 1:numel(tn)// if there exists any trust connection with that source Kp = find(trustlist(tn[i].Id),2); If Kp = Destination//if this trust connection has same destination as in the calling function Scr = tn[1][1].Id; Dcr = tn[1][2].Id; Active Connection[account]= ConnectionId account = account +1; Xcr = tn[1][3].Id; End if //finding all the active connections with the existing source and destination End for For s = 1: account If(connecting.Vehicle.displacement == true) Valid = 0; Valid = check coverage of current transmitting source: Valid2 = 0; If (valid == ∆) Valid2 = check(∆E) End if End if If (valid1==0 || valid2 == 0) Deletefromtrustlist(Scr,Dcr,Xcr); End if; End for; End if End function; With the implementation of the trust model, the proposed algorithm has assured that the network consumes least amount of delay. The performance of the system is enhanced as their will be guaranteed reduction in the delay, so the throughput of the network will be high. The network may also suffer from heavy load as the virtual machines are occupied by many tasks or jobs at one time. The proposed algorithm adds a load balancing mechanism which utilizes the concept of virtual machines to share and reduce the load on the network. The load is shared among the working virtual machine on the network to lessen the congestion of jobs on the network. Delay with 50, 100 and 150 nodes with broadcasting Fig.6. Delay with 50, 100 and 150 nodes with broadcasting Table 4. Delay with broadcasting No. of Iterations Delay with 50 node Delay with 100 nodes Delay with 150 nodes 1 2.76 2.57 2.40 2 2.81 2.32 2.11 3 3.02 2.75 2.45 The above figure 6 represents the delay in millisecondsduring simulation with variant nodes i.e. 50, 100 and 150. Further the table 4 describes the average delay in the variant nodes in the network. Average delay in broadcasting protocol is 2.86 ms for 50 nodes. An average delay decreases have been recorded during simulation with 100 nodes and value is 2.54 ms and the average delay through broadcasting protocol is 2.32 ms for 150 nodes. Form the above observations; the delay slightly decreases with increase in number of nodes with broadcasting. It shows that as we increase the number of nodes in the network the delay is declined. Fig.7. Collision with 50, 100 and 150 nodes with broadcasting Table 5. Collision with broadcasting No. of Iterations Collision with 50 node Collision with 100 nodes Collision with 150 nodes 1 0.56 0.46 0.45 2 0.52 0.43 0.41 3 0.51 0.49 0.43 Duplicate MACs doesn’t cause collisions. Collisions are the result of race condition i.e. transmission race between data packets from source to destination. From proposed method the figure 7 depicts, the Mac collisions for 50 nodes has found to be min. = 0.51 and max= 0.56. Similarly, Mac collisions for 100 nodes has found to be min = 0.43 and max = 0.49 and for 150 nodes has found to be min. = 0.41 and max= 0.45. It has been observed that the probability of collision is decreased with the increase in the number of iterations and number of nodes. Fig.8. Battery charge with 50, 100 and 150 nodes with broadcasting Table 6. Battery with broadcasting No. of Iterations Battery charge with 50 node Battery charge with 100 nodes Battery charge with 150 nodes 1 6065 6040 6025 2 6130 6087 6043 3 6280 6170 6089 Battery life is a measure of battery performance and prolonged existence, which can be enumerated in several ways. It is measured using percentage in proposed work. From result simulations, the battery life has found to be ≅ 6103 for 3 rounds and for 50, 100 and 150 nodes. From the above observations; the battery life slightly decreases with the increase in number of nodes with broadcasting. V. Conclusion In recent years, the various number of VANET based real applications have been increased rapidly. In real time environment, basically, some features are required i.e. high throughput, less energy consumption, reduced delay, high network lifetime and a decent battery lifespan. The proposed research work has tried to optimize the lifetime and reliability by introducing the concept of broadcast and cache memory to it. The proposed algorithm has also included a trust model due to which the extra time and to search nodes for the transfer of data is saved. The proposed algorithm is also focused on load balancing and for that well knownconcept of VM allocation and migration has been adopted. The overall architecture is compared under different scenarios and it has been observed that the proposed algorithm has solved the discussed problems to a great extent. The current research work unwraps a lot of gates for the future research workers. The future research workers may try their hands in improvising the trust model in order to prevent more energy. It would be also interesting to see the impact of Artificial Intelligence in the proposed algorithm.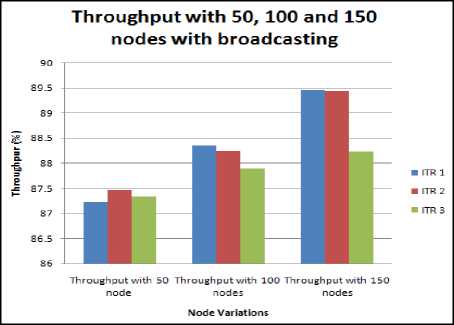
Список литературы A reliable solution to load balancing with trust based authentication enhanced by virtual machines
- D. Das and S. Das, “Adaptive resource allocation scheme for cognitive radio vehicular Ad hoc network in the presence of primary user emulation attack”, IET Networks, vol. 6, no. 1, pp. 5-13, 2017.
- X. Zhang, L. Yan and W. Li, “Efficient and Reliable Abiding Geocast Based on Carrier Sets for Vehicular Ad Hoc Networks”, IEEE Wireless Communications Letters, vol. 5, no. 6, pp. 660-663, 2016.
- Y. Wang, J. Zheng and N. Mitton, “Delivery Delay Analysis for Roadside Unit Deployment in Vehicular Ad Hoc Networks With Intermittent Connectivity”, IEEE Transactions on Vehicular Technology, vol. 65, no. 10, pp. 8591-8602, 2016.
- L. Zhu, C. Li, B. Li, X. Wang and G. Mao, “Geographic Routing in Multilevel Scenarios of Vehicular Ad Hoc Networks”, IEEE Transactions on Vehicular Technology, vol. 65, no. 9, pp. 7740-7753, 2016.
- Y. Kim, M. Lee and T. J. Lee, “Coordinated Multichannel MAC Protocol for Vehicular Ad Hoc Networks”,IEEE Transactions on Vehicular Technology, vol. 65, no. 8, pp. 6508-6517, 2016.
- J. Contreras-Castillo, S. Zeadally and J. A. Guerrero Ibañez, “Solving vehicular ad hoc network challenges with Big Data solutions”, IET Networks, vol. 5, no. 4, pp. 81-84, 2016.
- X. M. Zhang, K. H. Chen, X. L. Cao and D. K. Sung, “A Street-Centric Routing Protocol Based on Microtopology in Vehicular Ad Hoc Networks”, IEEE Transactions on Vehicular Technology, vol. 65, no. 7, pp. 5680-5694, 2016.
- Y. Bi, H. Shan, X. S. Shen, N. Wang and H. Zhao, “A Multi-Hop Broadcast Protocol for Emergency Message Dissemination in Urban Vehicular Ad Hoc Networks”, IEEE Transactions on Intelligent Transportation Systems, vol. 17, no. 3, pp. 736-750, 2016.
- M. HashemEiza, T. Owens, Q. Ni and Q. Shi, “Situation-Aware QoS Routing Algorithm for Vehicular Ad Hoc Networks”, IEEE Transactions on Vehicular Technology, vol. 64, no. 12, pp. 5520-5535, 2015.
- S. F. Tzeng, S. J. Horng, T. Li, X. Wang, P. H. Huang and M. K. Khan, “Enhancing Security and Privacy for Identity-Based Batch Verification Scheme in VANETs”, IEEE Transactions on Vehicular Technology, vol. 66, no. 4, pp. 3235-3248, 2017.
- Q. Yang, S. Xing, W. Xia and L. Shen, “Modelling and performance analysis of dynamic contention window scheme for periodic broadcast in vehicular ad hoc networks”, IET Communications, vol. 9, no. 11, pp. 1347-1354, 7 23 2015.
- H. Hu, R. Lu, Z. Zhang and J. Shao, “REPLACE: A Reliable Trust-Based Platoon Service Recommendation Scheme in VANET”, IEEE Transactions on Vehicular Technology, vol. 66, no. 2, pp. 1786-1797, 2017.
- Anton Beloglazov, Jema lAbawajy, and RajkumarBuyya, “Energy-aware resource allocation heuristics for efficient management of data centers for cloud computing”, Future generation computer systems, vol. 28, no. 5, pp.755-768, 2012.
- ShaminderKaur, and AmandeepVerma, “An efficient approach to genetic algorithm for task scheduling in cloud computing environment”, International Journal of Information Technologyand Computer Science (IJITCS), vol. 4, no. 10, pp.74, 2012.
- ManishaVerma, NeelamBhardwaj, and Arun Kumar Yadav, “Real Time Efficient Scheduling Algorithm for Load Balancing in Fog Computing Environment”, International Journal of Information Technology and Computer Science (IJITCS), vol. 8, no. 4,pp. 1,2016.


