A Review of Cloud Computing Security Issues
Автор: Manpreet kaur, Hardeep Singh
Журнал: International Journal of Education and Management Engineering(IJEME) @ijeme
Статья в выпуске: 5 vol.5, 2015 года.
Бесплатный доступ
Cloud computing is an emerging paradigm which has become today's hottest research area due to its ability to reduce the costs associated with computing. In today's era, it is most interesting and enticing technology which is offering the services to its users on demand over the internet. Since Cloud computing stores the data and its disseminated resources in the environment, security has become the main obstacle which is hampering the deployment of cloud environments. There are number of users used cloud to store their personal data, so that data storage security is required on the storage media. The major concern of cloud environment is security during upload the data on cloud server. Data storage at cloud server attracted incredible amount of consideration or spotlight from different communities. For outsourcing the data there is a need of third party. The importance of third party is to prevent and control unauthorized access to data store to the cloud. This research paper discuss the security issues of cloud storage.
Cloud computing, cloud data storage, cloud data security, Deployment models, Service models, cloud security challenges
Короткий адрес: https://sciup.org/15013851
IDR: 15013851
Текст научной статьи A Review of Cloud Computing Security Issues
Published Online October 2015 in MECS DOI: 10.5815/ijeme.2015.05.04
The term “Cloud Computing” is the computing services in Information Technology like infrastructure, platforms, or applications could be arranged and used through the internet. Infrastructure upon which cloud is built upon is a large scaled distributed infrastructure in which shared pool of resources are generally virtualized, and services which are offered are distributed to clients in terms of virtual machines, deployment environment, or software. Hence it can be easily concluded that according to the requirements and current workloads, the services of cloud could be scaled dynamically. As many resources are used, they are measured and then the payment is made on the basis of consumption of those resources.
According to the definition of[15], cloud computing is “it is a significant distributed computing model that is
* Corresponding author. Tel.:
directed by financial prudence of balance, in which stake of isolate, fundamental, loading, podium in which a facilities are supplied as per the request of exterior foreign clients through the internet”. There are some examples of cloud services like webmail, online file and business applications. Cloud computing provides a shared pool of resources, including data storage space, networks, computer processing power, and specialized corporate and user applications. Cloud storage [20] specifies the storage on cloud with almost inexpensive storage and backup option for small enterprise. The actual storage location may be on single storage environment or replicated to multiple server storage based on importance of data. The mechanism [20] model of cloud storage consists of four layers: storage layer which stores the data, basic management layer which ensures security and stability of cloud storage itself, application interface layer which provides application service platform, and access layer which provides the access platform. The basic cloud storage environment represented as below:
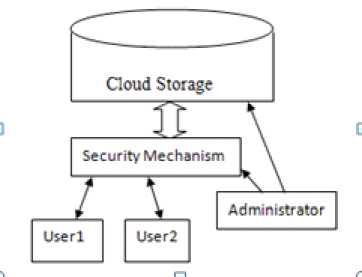
-
Fig. 1. Cloud Storage Environment
-
• Cloud Services Models
Cloud Infrastructure as a service(IaaS): In this composition of implemented environment for their system a supplier must be supply a different computing resources which include loading, processing unit. Client has flexile to achieve and switches software mutilated to be implemented and vary between different applications like operating system etc. There are different issues in IaaS such as:
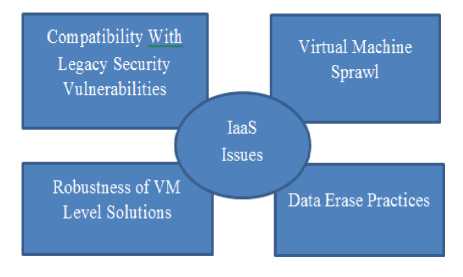
-
Fig. 2. IaaS Issues
Cloud Platform as a service (PaaS): This software supplies client with the ability to establish and extended applications that are mainly positioned on equipment and programming languages promoted by the suppliers. In this the client has no containment over the different organization but has containment over the extended applications. Examples of this class of services include Google App Engine, Windows Azure Platform and rack space. There are different issues in PaaS such as:
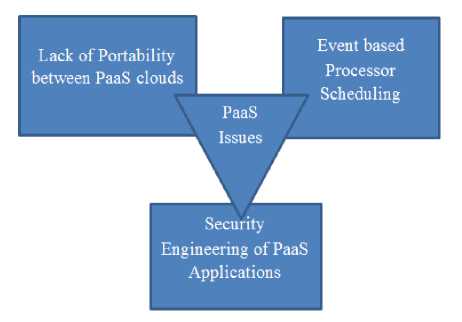
-
Fig. 3. PaaS Issues
Types of PaaS : There are different types of PaaS such as
-
• Application Delivers only Environments
-
• Standalone Developments Environments
-
• Open Platform & Open Service
-
• Add on Development Possibility
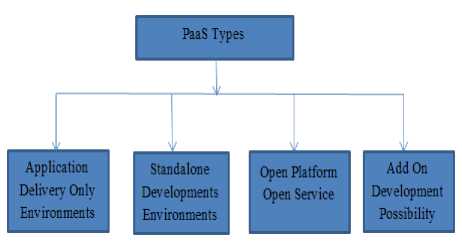
-
Fig. 4. PaaS Types
Cloud Software as a service (SaaS): This software supplies the ability to usage the appliances which implemented on cloud organization. With the usage of standard interfaces like web browser or online(e-mail) client, these appliances are obtainable. SaaS appliances are obtained from different devices like mobile, workstation from anywhere at any time.
Cloud Network as a service (NaaS): NaaS provides the capability to use the network services and intercloud network connectivity services. Improvement of possession allocation services include in view of network and computing resources. These type of services involved extensible, enhanced virtual private network.
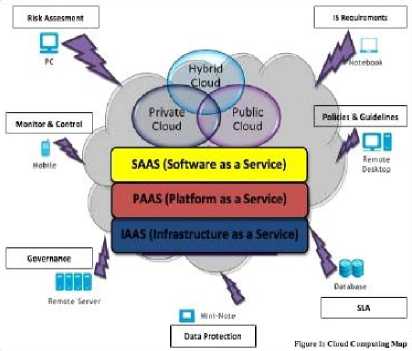
-
Fig. 5. Cloud Computing map [6]
-
• Cloud Deployment Models
Public Cloud: Public cloud describes the conventional meaning of cloud computing that is accessible, effective ways and means, which are accessible on internet from a minor party, which detached assets and charges its clients on the basis of utility. Cloud organization is possessed and accomplish by a supplier who suggest its retune to public domain. E.g. Google, Amazon, Microsoft offers cloud services via Internet. There are different benefits of public cloud model. The following figure shows some of those benefits:
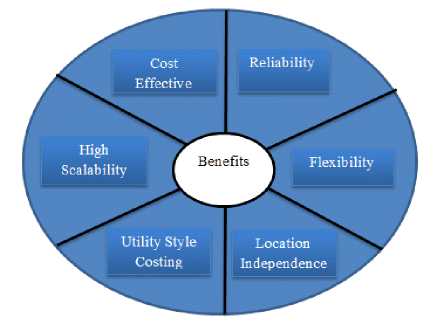
-
Fig. 6. Benefits of Public Cloud
Private Cloud: Private cloud is a term used to donate a proprietary computing architecture provisioned services on corporate networks. Big enterprises usually used this type of cloud computing to permit their private network and information Centre administrators to effectively become in-house ‘service providers’ catering to customers within the corporation. Cloud organization is establishing for a particular aggregation and managed by a third party under a service level agreement. Only single organization preferred to operate via corporate cloud. There are advantages (benefits) of internal cloud model. The diagram given below depicts a few of these advantages (benefits):
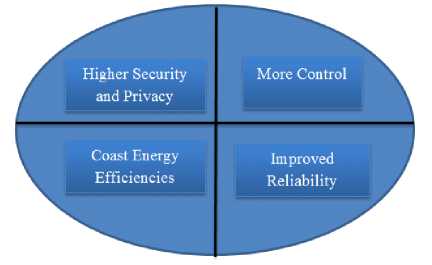
-
Fig. 7. Benefits of Private Cloud
Hybrid Cloud: A hybrid cloud comprises assets from both corporate and public providers will definitely become the demanded choice for enterprises. The hybrid cloud is a combination of both corporate cloud and public cloud.. For example, for general computing enterprise could selects to make usage of external services, and its own data Centre’s comprises it own data Centre’s. Hybrid cloud model has number of advantages (benefits).The diagram given below reveals some of those advantages (benefits):
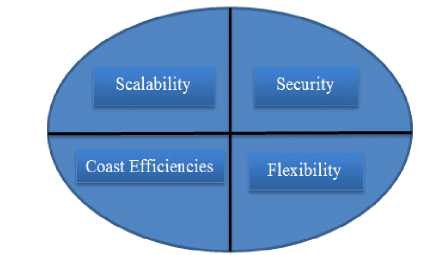
-
Fig. 8. Benefits of Hybrid Cloud
-
• Cloud Computing Characteristics
-
2. Related Work
On Demand self-service: A cloud might individually attain computing possibilities, as per the use of different servers, network storing, as on request, without communicating with cloud provider.
Broad Network Access: Services are delivered across the Internet within a standard mechanism and access to the services is possible through assorted customer tools.
Resource pooling: A multitudinous model is employed to serve different types of clients by making pools of different computing resources, as per the request of customers these have different resources which can be assigned and reassigned dynamically.
Rapid Elasticity: Capabilities might be elastically provisioned or rapidly released. From customers view, the provided possibilities come out to be limitless and must have the capability to purchase in any quantity at any time.
Measured Services: The provision procured by different clients is measurable. The use of asset will be directed, estimated, and accused for contributor and asset.
Balachandra reddy et al[1] client has total control on information which are saved on their own system. On flip side, the assistance and data handling is presuming by few assistant which leaves the client inattentive of where methods are executing on where the information is saved. So, the customer has no predominance over it. Cloud computing utilize the internet as the transmission method. In this when we look at the privacy of information in cloud computing the trader has to provide some guarantee in service level agreement to satisfy the individual on privacy issues. Company utilize cloud computing as service infrastructure, condemnatory like to scrutinize the privacy and security issues for their business insensitive applications. Yet, assurance the privacy of collaborative data in the cloud is difficult, as they offer distinct services like software as a service, platform as a service, infrastructure as a service. In this each assistance has their own privacy issues. Service level agreement has to explain distinct stages of privacy and complications based on the assurance to make the ability of client about the policies that are being implemented.
Chun-ting huang[7] explain the latest multimedia storage system and its privacy problems, their centre of attention on four latest topics that is data integrity, data confidentiality, access control and data manipulation in the encrypted domain. They explain distinct keys objectives and resolution proposed in the latest work. Their research provide a state-of-the-art knowledge to new researchers who would like to know about this new field and do some work in this field. Cong wang and kui ren wenjing lou and jin li[9] explained the multimedia cloud computing. In this researchers explained how a cloud can offer QoS support, distributed parallel processing, storage and load balancing for distinct multimedia applications and assurance.Most specifically, reseachers proposed a MEC-computing architecture that can attain high cloud QoS support for distinct multimedia services. On cloudaware multimedia, researchers addressed multimedia services and applications such as storage, sharing, authoring, mashing, adaptation and delivery, rendering and retrieval use cloud computing resources.
Er. Rimmy chuchra et al [13] explained the need of information integration, technical support and method of integration under the environment of cloud computing and way to establishing operational mechanisms to attain integration of distributed heterogeneous data sources and integration and transparency of location, structure, semantic of enterprise heterogeneous data and solve the issue of comprehensive sense, resource allocation and timely response on service integration and sharing of resource effectively.
Hassan Takabi et al [17] explained the use of cloud computing for secure dissemination of protected multimedia content as well as document and rich media. In this researchers have leveraged the UCON model for enforcing fine grained continuous usage control constraints on objects residing in the cloud. Their framework allows for the object to specify their policies including those specification the duration of each use and the number of times the object can be used etc.
Dr.R.Manicka et al.[12]explained a IP Multimedia subsystem(IMS) framework with cloud computing architecture for use in multimedia applications. It supports heterogeneous networking with quality-of-service (QoS) policy.In this Map reduce analysis is used. It is used to enhance cloud computing capability. Results indicate that the proposed mechanism improves system capacity to accommodate numerous users. The proposed IMS cloud has three layers that is Infrastructure as a service layer, platform as a service layer and software as a service layer. The IaaS layer accesses heterogeneous networks such as UMTS, WLAN and WiMAX through IP multimedia subsystem. The PaaS layer manages the cloud computing system in Hadoop Distributed File System and the Map reduce mechanism for analysing user performances. The SaaS layer accesses the desired applications such as the web, social management and management services. It also improve system throughput performances.
-
3. Cloud Security Challenges
-
4. Security Feature in Cloud Computing
There are some key security [7] challenges are:
Authentication: Throughout the internet data stored by cloud user is available to all unauthorized people. Henceforth the certified user and assistance cloud must have interchangeability administration entity.
Access Control: To check and promote only legalized users, cloud must have right access control policies. Such services must be adjustable, well planned, and their allocation is overseeing conveniently. The approach governor provision must be integrated on the basis of Service Level Agreement (SLA).
Policy Integration: There are many cloud providers such as Amazon, Google which are accessed by end users. Minimum number of conflicts between their policies because they user their own policies and approaches.
Service Management: In this different cloud providers such as Amazon, Google, comprise together to build a new composed services to meet their customers need. At this stage there should be procure divider to get the easiest localized services.
Trust Management: The trust management approach must be developed as cloud environment is service provider and it should include trust negotiation factor between both parties such as user and provider. For example, to release their services provider must have little bit trust on user and users have same trust on provider.
There are several main challenges for building a secure band trustworthy cloud system:
Outsourcing: Outsourcing brings down both capital expenditure and operational expenditure for cloud customers. However, outsourcing also means that customers physically lose control on their data and tasks. The loss of control problem has become one of the root causes of cloud insecurity. To address outsourcing security issues, first, the cloud provider shall be trustworthy by providing trust and secure computing and data storage; second, outsourced data and computation shall be verifiable to customers in terms of confidentiality, integrity, and other security services. In addition, outsourcing will potentially incur privacy violations, due to the fact that sensitive data is out of the owner’s control.
Massive data and intense computation: Cloud computing is capable of handling mass data storage and intense computing tasks. Therefore, traditional security mechanisms may not suffice due to unbearable computation or communication overhead. For example, to verify the integrity of data that is remotely stored, it is impractical to hash the entire data set. To this end, new strategies and protocols are expected.
-
5. Security Issues
The security of corporate data in the cloud is difficult, as they provide different services like Network as a service (NaaS), Platform as a service (PaaS), Software as a service (SaaS), Infrastructure as a service (IaaS). Each service has their own security issues [5]
Data Security: Data Security refers as a confidentiality, integrity and availability. These are the major issues for cloud vendors. Confidentiality is defined as a privacy of data. Confidentiality are designed to prevent the sensitive information from unauthorized or wrong people. In this stores the encryption key data from enterprise C, stored at encrypted format in enterprise D. that data must be secure from the employees of enterprise D. Integrity is defined as the correctness of data, there is no common policies exist for approved data exchanges. Availability is defined as data is available on time.
Regulatory Compliance: Customers are eventually accountable when the security and completeness of their own data is taken by a service provider. Traditional service providers more prone to outsource surveys and security certification. Cloud computing providers reject to endure the scrutiny as signalling so these customers can only make usage of paltry operations [25].
Data Locations: When users use, they probably won’t know exactly where their data will hosted and which location it will stored in. In fact, they might not even know what country it will be stored in. Service providers need to be asked whether they will accomplish to storing and alter data in particular arbitration, and on the basis of their customers will they make a fair accomplishment to follow local privacy requirement [23].
Privileged user access: Outside the resource data that is processed contains an indigenous risk, as deploy services, avoid the mortal, consistent and human resource manage IT shops works on the house programs.
Trust Issue: Trust is also a major issue in cloud computing. Trust can be in between human to machine, machine to human, human to human, machine to human. Trust is revolving around assurance and confidence. In cloud computing, user stores their data on cloud storage because of trust on cloud. For example people use Gmail server, Yahoo server because they trust on provider.
Data Recovery: It is defined as the process of restoring data that has been lost, corrupted or accident.
Cloud computing is latest technology that is being widely used all over the world. Once the organization takes the decision to move to the cloud, it loses control over the data. Thus, the amount of protection needed to secure data is directly proportional to the value of the data. Security of the Cloud relies on trusted computing and cryptography. Number of cloud platforms are available now in educational as well as in enterprises circle
In this paper, we have discussed the issues related to data location, storage, security, availability and integrity. Establishing trust is the way to overcome these security issues as it establishes entities relationship quickly and safely. These issues mentioned above will be the research hotspot of cloud computing. There is no doubt that cloud computing has bright future.
Refrences
-
[1] Balachandra Reddy Kandukuri, Rama Krishna Paturi and Dr. AtanuRakshit, “Cloud security issues ” In Services Computing, 2009. IEEE International Conference on, page 517520, 2009
-
[2] Boldreva A., Chenette N., Lee Y, O’neill A. (2009), “Order-preserving Symmetric encryption”, Advances in Cryptology-EUROCRYPT 2009 Springer, Berlin/Heidelberg, pp. 224-241.
-
[3] Boneh D., Di G., Ostrovsky R., Persiano G. (2004), “Public key encryption with keyword search”, Advances in Cryptology-Eurocrypt, Springer, Berlin/Heidelberg, pp 506–522.
-
[4] B.R kandukuri, R.Paturi V, and A.Rakshit, “cloud security issues”,2009 IEEE International Conference on Services Computing, sep. 21-25, 2009, Bangalore, India, pp. 517-520.
-
[5] Campbell, Jeronimo, “Applied Virtualization Technology,” Hillsboro, Intel Press (ISBN 09764832-3-8), 2006, pp. 69-73.
-
[6] Chandrahasan, R. Kalaichelvi, S. Shanmuga Priya, and L. Arockiam. "Research Challenges and Security Issues in Cloud Computing." International Journal of Computational Intelligence and Information Security 3.3 (2012): 42-48.
-
[7] Chun-Ting Huang, Zhongyuan Qin, C.-C. Jay Kuo., “Multimedia Storage Security in Cloud Computing: an Overview” 978-1-457701434- 4/11/$26.00,IEEE,2011.
-
[8] Cloud Security Alliance, “Top Threats to Cloud Computing v1.0,” Prepared by the Cloud Security Alliance, March 2010, pp. 1-14.
-
[9] Cong.Wang and Kui Ren Wenjing Lou and Jin Li “Towards Publicity Auditable Secure Cloud Data Storage”. Cong Wang, Qian Wang, Kui Ren, Wenjing Lou, "Privacy Preserving Public Auditing for Data Storage Security in , cloud Computing”, 2010.
-
[10] Cong Wang, Qian Wang, KuiRen and Wenjing Lou, “ Ensuring Data Storage Security in Cloud Computing”, In Quality of Service, 2009. 17th International Workshop on, page 19, 2009.
-
[11] Dong Xin, et al.”achieving secure and efficient data collaboration in cloud computing. ”Quality of service, 2013 IEEE/ACM 21st International symposium on.IEEE,2013.
-
[12] Dr.R.Manicka Chezian and C.bagyalakshmi ”a survey on cloud data security Using encryption technique” in International journal of advanced research in computer engineering & technology , Volume 1, Issue 5, July 2012.
-
[13] Er.Rimmy Chuchra,Lovely Professional University,Phagwara, India, “Data Security in Cloud Computing” , International Journal Nov.,2012.
-
[14] Feng-Tse Lin, Teng-San Shih, “Cloud Computing: The Emerging Computing Technology,” ICIC Express Letters Part B: Applications (ISSN: 2185-2766), v1, September 2010, pp. 33-38.
-
[15] Foster, I. T., Zhao, Y., Raicu, I., & Lu, S. (2009). Cloud Computing and Grid Computing 360-Degree Compared CoRR. abs/0901.0131 .
-
[16] G. Hughes, D. Al-Jumeily & A. Hussain,” Supporting Cloud Computing Management through an Object Mapping Declarative Language”, 2010 Developments in E-systems engineering.
-
[17] Hassan Takabi, James B. D. Joshi and Gail-JoonAhn , “Secure Cloud: Towards a Comprehensive Security Framework for Cloud Computing Environments” Proceedings of the 2010 IEEE 34th Annual Computer Software and Applications Conference Workshops, p.393-398, July 19-23, 2010.
-
[18] John Harauz, Lori M. Kaufman and Bruce Potter, ”Data security in the world of cloud computing” published by the IEEE computer and reliability societies in July/August 2009.
-
[19] Jouni Mäenpää, “Cloud Computing with the Azure Platform,” TKK T-110.5190 Seminar on Internet Working, April 27, 2009.
-
[20] Kant, Dr Chander, and Yogesh Sharma. "Enhanced Security Architecture for Cloud Data Security." International Journal of Advanced Research in Computer Science and Software Engineering 3.5 (2013): 571-575.
-
[21] Meiko Jensen, JlorgSchwenk, Nils Gruschka and Luigi Lo Iacono, “On Technical Security Issues In Cloud Computing”, IEEE International Conference on Cloud Computing,2009.
-
[22] Nabendu Chaki, ”A Survey on Security issue in Cloud Computing ” in 6th International conference on Electrical Engineering/Electronics, Computer, Telecommunication and Information Technology, May 2009.
-
[23] Rajkumar Buyya, Chee Shin Yeo, Srikumar Venugopal, James Broberg and Ivona Brandic, “Cloud Computing and Emerging IT Platforms: Vision, Hype, and Reality for Delivering Computing as the 5th Utility,” Future Generation Computer System, 2009, pp. 599-616.
-
[24] Ren K, Wang C, Wang Q (2012) Security challenges for the public cloud. IEEE Internet Comput 16(1):69–73.
-
[25] Tout, Sverdlik, and Lawver, “Cloud Computing and its Security in Higher Education,” In Proceedings of the Proc ISECON 2009.
-
[26] Vaquero, Merino and Lindner, “A Break in the Clouds: Towards a Cloud Definition,” ACM SIGCOMM Computer Communication Review, v.39 n.1, January, 2009, pp. 50-55.
-
[27] W. Zeng, Y. Zhao, K. Ou, and W. Song, "Research on cloud storage architecture and key technologies," in Proceedings of the 2nd International Conference on Interaction Sciences: Information Technology, Culture and Human, Seoul, Korea, 2009, pp. 1044-1048.
-
[28] Xia Z., Zhu Y., Sun X. and Chen L. (2014), " Secure semantic expansion based search over encrypted cloud data supporting similarity ranking " Journal of Cloud Computing”,Springer 3.1, pp. 1-11.
-
[29] Yunqi Ye, Liangliang Xiao, I-Ling Yen, Farokh Bastani, “Secure, Dependable, and High Performance Cloud Storage”, 2010 29th IEEE International Symposium on Reliable.
-
[30] www.academicroom.com/topics/cloud-computing
Список литературы A Review of Cloud Computing Security Issues
- Balachandra Reddy Kandukuri, Rama Krishna Paturi and Dr. AtanuRakshit, "Cloud security issues" In Services Computing, 2009. IEEE International Conference on, page 517520, 2009.
- Boldreva A., Chenette N., Lee Y, O'neill A. (2009), "Order-preserving Symmetric encryption", Advances in Cryptology-EUROCRYPT 2009 Springer, Berlin/Heidelberg, pp. 224-241.
- Boneh D., Di G., Ostrovsky R., Persiano G. (2004), "Public key encryption with keyword search", Advances in Cryptology-Eurocrypt, Springer, Berlin/Heidelberg, pp 506–522.
- B.R kandukuri, R.Paturi V, and A.Rakshit, "cloud security issues",2009 IEEE International Conference on Services Computing, sep. 21-25, 2009, Bangalore, India, pp. 517-520.
- Campbell, Jeronimo, "Applied Virtualization Technology," Hillsboro, Intel Press (ISBN 09764832-3-8), 2006, pp. 69-73.
- Chandrahasan, R. Kalaichelvi, S. Shanmuga Priya, and L. Arockiam. "Research Challenges and Security Issues in Cloud Computing." International Journal of Computational Intelligence and Information Security 3.3 (2012): 42-48.
- Chun-Ting Huang, Zhongyuan Qin, C.-C. Jay Kuo., "Multimedia Storage Security in Cloud Computing: an Overview" 978-1-457701434- 4/11/$26.00,IEEE,2011.
- Cloud Security Alliance, "Top Threats to Cloud Computing v1.0," Prepared by the Cloud Security Alliance, March 2010, pp. 1-14.
- Cong.Wang and Kui Ren Wenjing Lou and Jin Li "Towards Publicity Auditable Secure Cloud Data Storage". Cong Wang, Qian Wang, Kui Ren, Wenjing Lou, "Privacy Preserving Public Auditing for Data Storage Security in , cloud Computing", 2010.
- Cong Wang, Qian Wang, KuiRen and Wenjing Lou, "Ensuring Data Storage Security in Cloud Computing", In Quality of Service, 2009. 17th International Workshop on, page 19, 2009.
- Dong Xin, et al."achieving secure and efficient data collaboration in cloud computing. "Quality of service, 2013 IEEE/ACM 21st International symposium on.IEEE,2013.
- Dr.R.Manicka Chezian and C.bagyalakshmi "a survey on cloud data security Using encryption technique" in International journal of advanced research in computer engineering & technology , Volume 1, Issue 5, July 2012.
- Er.Rimmy Chuchra,Lovely Professional University,Phagwara, India, "Data Security in Cloud Computing", International Journal Nov.,2012.
- Feng-Tse Lin, Teng-San Shih, "Cloud Computing: The Emerging Computing Technology," ICIC Express Letters Part B: Applications (ISSN: 2185-2766), v1, September 2010, pp. 33-38.
- Foster, I. T., Zhao, Y., Raicu, I., & Lu, S. (2009). Cloud Computing and Grid Computing 360-Degree Compared CoRR. abs/0901.0131.
- G. Hughes, D. Al-Jumeily & A. Hussain," Supporting Cloud Computing Management through an Object Mapping Declarative Language", 2010 Developments in E-systems engineering.
- Hassan Takabi, James B. D. Joshi and Gail-JoonAhn, "Secure Cloud: Towards a Comprehensive Security Framework for Cloud Computing Environments" Proceedings of the 2010 IEEE 34th Annual Computer Software and Applications Conference Workshops, p.393-398, July 19-23, 2010.
- John Harauz, Lori M. Kaufman and Bruce Potter, "Data security in the world of cloud computing" published by the IEEE computer and reliability societies in July/August 2009.
- Jouni Mäenpää, "Cloud Computing with the Azure Platform," TKK T-110.5190 Seminar on Internet Working, April 27, 2009.
- Kant, Dr Chander, and Yogesh Sharma. "Enhanced Security Architecture for Cloud Data Security." International Journal of Advanced Research in Computer Science and Software Engineering 3.5 (2013): 571-575.
- Meiko Jensen, JlorgSchwenk, Nils Gruschka and Luigi Lo Iacono, "On Technical Security Issues In Cloud Computing",IEEE International Conference on Cloud Computing,2009.
- Nabendu Chaki, "A Survey on Security issue in Cloud Computing " in 6th International conference on Electrical Engineering/Electronics, Computer, Telecommunication and Information Technology, May 2009.
- Rajkumar Buyya, Chee Shin Yeo, Srikumar Venugopal, James Broberg and Ivona Brandic, "Cloud Computing and Emerging IT Platforms: Vision, Hype, and Reality for Delivering Computing as the 5th Utility," Future Generation Computer System, 2009, pp. 599-616.
- Ren K, Wang C, Wang Q (2012) Security challenges for the public cloud. IEEE Internet Comput 16(1):69–73.
- Tout, Sverdlik, and Lawver, "Cloud Computing and its Security in Higher Education," In Proceedings of the Proc ISECON 2009.
- Vaquero, Merino and Lindner, "A Break in the Clouds: Towards a Cloud Definition," ACM SIGCOMM Computer Communication Review, v.39 n.1, January, 2009, pp. 50-55.
- W. Zeng, Y. Zhao, K. Ou, and W. Song, "Research on cloud storage architecture and key technologies," in Proceedings of the 2nd International Conference on Interaction Sciences: Information Technology, Culture and Human, Seoul, Korea, 2009, pp. 1044-1048.
- Xia Z., Zhu Y., Sun X. and Chen L. (2014), "Secure semantic expansion based search over encrypted cloud data supporting similarity ranking "Journal of Cloud Computing",Springer 3.1, pp. 1-11.
- Yunqi Ye, Liangliang Xiao, I-Ling Yen, Farokh Bastani, "Secure, Dependable, and High Performance Cloud Storage", 2010 29th IEEE International Symposium on Reliable.
- www.academicroom.com/topics/cloud-computing


