An Application of Rule-Based Classification with Fuzzy Logic to Image Subtraction
Автор: Marlon D. Hernandez
Журнал: International Journal of Engineering and Manufacturing @ijem
Статья в выпуске: 2 vol.13, 2023 года.
Бесплатный доступ
Surveillance camera is used as a new technology for security. In this research, the combination of OpenCV with image processing will be discussed. Saving the space in the hard drive by recording only video when here would be an image formed in the subtraction of the original image to the next image captured. With the use of Image Processing and Fuzzy logic, the research was enhanced by eliminating the recording of same image captured. After analyzing the background images, it can now determine when to start recording the video or when to stop recording a video by subtracting the images in the backdrop image and comparing the image if there was an object in motion using template matching. With the application of the project, memory storage saved up to forty-six percentage points.
Image Processing, Surveillance Camera, OpenCV, Fuzzy Logic, Rule-Based
Короткий адрес: https://sciup.org/15018689
IDR: 15018689 | DOI: 10.5815/ijem.2023.02.03
Текст научной статьи An Application of Rule-Based Classification with Fuzzy Logic to Image Subtraction
Computers are used as an educational tool in academe, it let the students to work on worksheets, documents, presentations, programming, and other related educational requirements[1]. Students in Bulacan State University give students free time to use the computer laboratory if there are school requirements and when the laboratory has no schedule. Computer parts are easy dismantled by people and are prone to damage in computer laboratories when the classroom is not monitored by the staff. The settings of the computers may also be changed such as wallpapers, enabling and disabling peripherals and even installing unauthorized software’s which is not related to academic tracks such as games and others[2, 3].
In Department of Education (DepEd), there are reported stolen computer laptops in school vicinities which the suspects are still unknown[4]. In 2018, there are also reported students that bring tools to dismantle and steal computer parts and LCD projectors in DepEd which was addressed by the Philippine National Police where it launched a counter measure to the issue to provide DepEd Computerization Program (DCP) which installed CCTV cameras in school premises[5]. Moreover, some are recovered because the computer parts, laptops and LCD projectors are placed in the marketplace online.
The most problems in computer laboratories in Bulacan State University Sarmiento campus are some computes are reconfigured by the students, they tend to change the peripherals of the computer to another computer, and some of the computer parts are stolen. With these trendy problems that cannot be monitored by the security and the faculty, a solution was proposed. A surveillance that would record the events in 4 computer laboratories. With this technology, another problem arises. The hard drive will be full in a month time due to continuous recording with 1920x1080 resolution per camera. Tracing back the CCTV footage would only be limited because it will continuously record everything even there are no people or movement in the classrooms[6]. The project also used high resolution to provide clearer recordings and to identify the person involved. However, the average file size of this resolution is 20-30 MB per minute, and this is per camera[7]. This would be from 80MB – 120MB per minute for all the cameras installed in the classrooms[8].
Some of the solutions provided are the users may unplug the CCTV cameras after classes, reduce the resolution size gathered by the cameras and use motion sensor cameras. However, this project used subtraction of image with the use of Open CV and fuzzy logic. This would still use high resolution video and would only record images when there are motion detected using image subtraction[9].
The researcher also employed the Anfis Model analysis. Template Matching[10] is the ability to compare the preceding image with the backdrop image (TM). The TM program assesses the sensitivity of the image subtraction and calculates the difference, resulting in measurements of the unknown picture in the frame[11]. This would also cause the system to activate the alarm system that is part of the project. The alarm goes off between 8 p.m. and 6 a.m., when the classroom is empty of students and faculty. Sensitivity is also set when a window is left open or an electric fan or air conditioner is left on, which causes other objects in the classroom to move. The security guard or the utilities will be notified and can fix the problem.
2. Background
For years, technology advancement had gone through so much, in terms of security. One of the most popular in terms of security is the Closed Circuit Television (CCTV). There had been security cameras that had been introduced which have the advance capability of introducing alarm. Surveillance is used not only by the private sectors but also in home security. Security cameras don’t prevent crime and intrusion but it will have a copy of the incident that took place. The main purpose of implementing surveillance cameras is to provide a playback feature and it can be viewed over the internet with a use of a computer or even a mobile phone.
Here are the following components that can be considered to help develop the project:
-
A. AdHoc Technology
The term Internet of Everything has been used by companies like Qualcomm and CISCO[12]. The basic structure of the IoE is based on four components that are composed of things, data, people and the process of communication.
The basic process of each component represents the interconnection and the basic property of networking. The Machine to Machine (M2M), People to People (P2P) and People to Machine (P2M) [13]. Everything that enclose the idea of this network represents the IoE. Figure1 also combines all the components that will show the manipulation of the entity with the prescribed process.
-
B. Human Computer Interface (HCI)
The basic input set-up of a computer is the traditional keyboard and mouse which is still used. The track ball mouse has upgraded to an optical mouse with the same function and the keyboard became a multimedia or even extended keyboards. Today, many input devices are sold in the market like joysticks, drawing pad, and others[14].
Other peripherals to have communication between M2M are by input output ports and wireless communications. Most of the HCI uses wireless connectivity like ADHOC, Bluetooth, Radio Frequency or Wireless Fidelity.
With regards with the data that was processed and transferred through this medium, connection must not break. Once the data was not received by the recipient, the sender resends the data through the network. This is applicable in the Response Time and Throughput.
-
C. Image Processing
The application of image processing on image comparison has been in the base of research of most journals in the line of visual mining. The digital image has 3 dimensions, the Red, Green, and the Blue (RGB) format. In image processing, the core factors are seen through histogram. Each histogram of the RGB format has different levels.
This format cam produce the histogram of the image by using the formula IRGB = (FR, FG, FB) where FR(x , y) id the concentration of the pixel distribution for the Red Histogram of the image. The FG( x , y) is the concentration of the pixel distribution of the Green histogram and FB(x , y) is the concentration of the pixel distribution of the Blue histogram [4]. If we combine all the histograms, it will result to the histogram of the image.
To get the luminance gray scale value of the image, we have to convert the image to grayscale. Each color will only require partial distribution for the gray scale. 30% for the Red, 59% for Green and 11% for Blue will be added together to formulate the gray scale value of the image[15]. Thus
IGRAY = (FR * 0.3, FG * 0.59, FB * 0.11) (1)
will compute for the histogram of the luminance gray scale of the image.
The case of converting the image to grayscale would determine the comparison of the edges of the different image comparison or template comparison. The histogram of the image formed is the combination of the different colors that was given by the RGB combination. The images can be compared to the series of data in the database with the use of area process.
Area process must have a kernel [16] to process the image and convert the data into a matrix form using the values of gray from 0 – 255. Comparing the result of the two values can determine the equality of both image that came from the user and the data from the database.
Based from figure 3 and 4, the word level approach gets the emphasized word[17]. The word commands will pertain to short words [18, 19]as an instruction such as ON and OFF. The emphasized word will be Cut [20, 21]and will be translated into image. For example, the command words are “Lights Off”, the first word would be Cut and will be translated to an image that will be compared to the database of commands. The second word will be cut and translated into an image then will be compared to the database of instructions. If the command and instruction will match, then the command and instruction will be executed in the program.
Comparing the images by the use of template matching [22]. In OpenCV, the use of template matching helps to search for matches between an image patch and an input image.
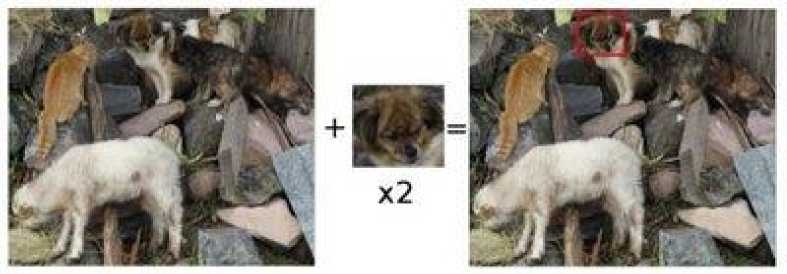
Fig. 1. Searching for the image template from the input image.
The goal of searching the template image in the desired input image has to be the highest matching area shown in figure 4 to identify the matching area, the template will be compared to the input image by sliding it from left to right and from top to bottom. At each location, It is calculated if the comparison how good or bad the match at that location [23].
-
1. Objective of the Research
-
2. Methodology
To create a paper that will introduce the use of Open CV with the fusion of Fuzzy logic in conserving memory space of the hard drive. When the images that are captured by the camera does not match, it will re compare when it captures the third image. Comparing the first image from the second image and comparing the third image to the first and second image would tell a sequence that would trigger the image recording to start. Having several information as an input now enters the problem of having a rule based expert system. To system will be able to save more hard drive space using template matching and Anfis Model.
Based on the different methodology used by the in the Information Technology, Agile Methodology is the most adaptable to be used because it lets the researcher to iterate the process once the objective is not met or there is a need to enhance the project.
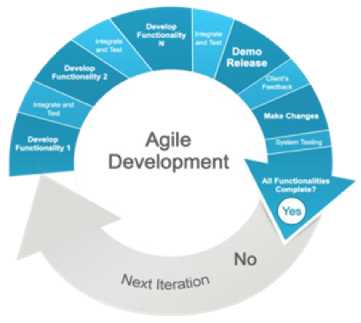
Fig. 2. Methodology of the study using Agile
The project followed the approach because Agile methodology, as shown in Figure 2, enables for quick output and employs the throwaway prototype theorem. When the project's functionality is being tested, it is recommended that the system be revised in accordance with ISO 25010. Each functionality will be developed in parallel with others, resulting in a more comprehensive development of the study.
3. Discussion
The paper will focus on the different applications and hardware components that can be used to provide better solution on the school administration, staff, students, and faculty.
The innovation through time of the components using 4G wireless connection can be an advantage in the paper, thus it must be flexible to adopt in the 5G in the future.
-
A. Application of OpenCV.
OpenCV implements template matching in the function of match template. This would be used in the research to identify if there would be a movement in the vicinity[24, 25, 26]. There are 6 methods that may be used and these are:
CV_TM_SQDIFF
R(x,y,) = Xx,y,(T(x',y') - I(x + x',y + y'))2
CV_TM_SQDIFF_NORMED
nz A E x уу(Т(х ',y ‘ )-/(x+x ‘ ,y+y ‘ ))2
X,y, E xry '(T (x ' ,y ' )2*EI(x+x ' ,y+y ' ))2
CV_TM_CCORR
R(x,y,) = Z y,y, (T(x ' ,y ' ) - I(x + x ' ,y + y ' ))2
CV TM CCORR NORMED
— -
—
R(x,y,) =
X x'y' (T(x ' ,у ' )Дх+х ' ,у+у ' ))
^ЁХТу^'Сх ' У'Р.ЁХТуйсх+х ' У+у ' )2
CV_TM_CCOEFF
R(x,y,) = Zyy'(T (x',y').I(x + x',y + y'))
where
T'(x',y') = T(x',y')-1/(^wh).Ex'',''T(x'',y'')
I'(x + x',y + y’} = I(x + x',y + y’} - 1/(w;. h). Т-x''y'' I(x + x",y + y'')
CV TM CCOEFF NORMED
- —
—
R(x,y) =
E x'y' T ' (x ' ,y ' )*!'(x+x ' ,y+y ' )) ^Е х',у‘ T'(x ' ,y ' 2* E x'y' I'( x+x ' ,y+y ' )2
-
B. Sugenio Method.
Both Mamdani and Sugenio [22]are used in different ways. Sugenio in the other hand supplies information in the project relatively because it focuses more on minimal inputs. The configuration of the rules is suitable in using Sugenio because the translation of the data can be identified to be more reliable.
The interpretation of the data is expressed in terms of generating signals if the surveillance camera would start the recording of the video or to stop recording.
-
C. Rule-Based Expert System.
The implementation of the rules in Bio informatics is used in the research to prove whether the application would record the instance of the video or stop. With the set of rules given, the analysis would define a definite procedure of the system.
Table 1. Rules of the image subtraction in the system
|
Original Image |
Second Image |
Subtraction |
Motion Detection |
|
1 |
1 |
1 |
1 |
|
1 |
1 |
0 |
WAIT |
|
1 |
0 |
1 |
WAIT |
|
1 |
0 |
0 |
0 |
|
0 |
1 |
1 |
1 |
|
0 |
1 |
0 |
WAIT |
|
0 |
0 |
1 |
WAIT |
|
0 |
0 |
0 |
0 |
The application of the subtraction would define that there was a movement detected in the vicinity, then the motion detection would be logically on. But in the fourth row, the original data was on then the original image was off, this means that there was a movement but the subtraction did not get a value. This means that the data may be the same so the motion did was not triggered.
-
D. Application of Fuzzy Logic.
The focus of the proposed paper will be on the data that would be the result of the subtraction using OpenCV. The difference of the data would result to recording the video and will only stop the recording when there is no more evaluation of difference from the original image to the next image captured by the project.
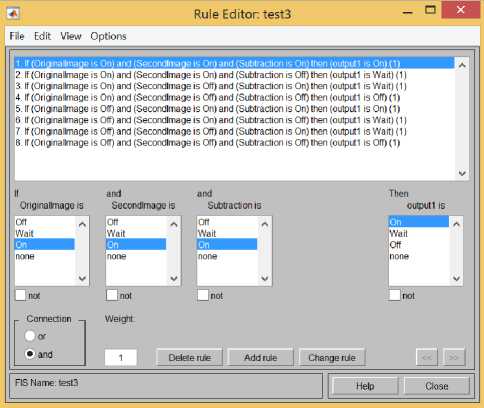
Fig. 3. Rules in the Fuzzy Logic
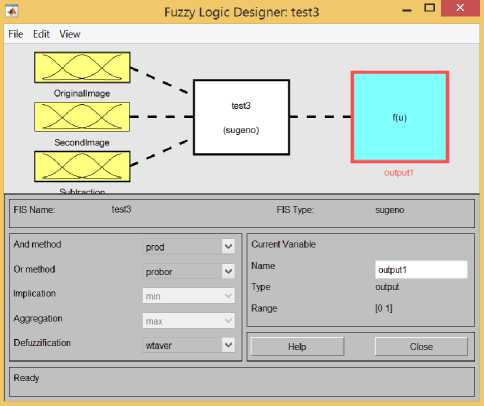
Fig. 4. The structure of the application.
4. Load Testing, Results and Discussions
These are the set of rules that the research is going to use. The main purpose of the rules is to set the dataset and to analyze the data if there would be any movement in the area. The set of instruction will also guarantee the rules are followed and may be adjust if the system needs improvements
There are three inputs of the data to be analyzed. The output would depend if the data that are analyzed would be on, off or wait status. The wait status would wait for the next image to be captured, the uncertainty of the values would determine that there are still unrecognized data. Using Sugeno, the application of the rules set will determine if there is motion in the specific frame by using image subtraction
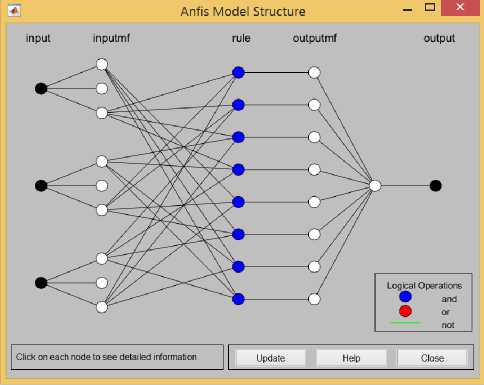
Fig.5. Anfis Model
The Anfis model of the research is presented where the representation of 3 inputs that will be evaluated in the set of rules that would produce the output. This is also a representation of the process of the hidden layers and the evaluation on how to evaluate on how does the fist image affects the background image that is the second image and the subtracted image as the third output. The determination of the difference thru image subtraction allows the system to identify if there was a motion detected. In every sensitivity settings, there are different output that was gathered, hence, the best fit sensitivity was tested that may add in setting the bias of the Anfis Network.
The surveillance cameras are tested to see the application of image subtraction and motion detection based on the given set or rules.

(a)

(b)
-
Fig. 6. Set up of the surveillance camera.
The surveillance camera can detect motion if the featured is on. In figure 6a, the feature of the motion can be turned on or off. Once there was a motion detected. The boarder of the video would turn to red. This will determine that a motion had occurred. This setting also provides the users to configure the level of sensitivity as to the desired output where the in Figure 6b, the sample of cameras of cam2 and cam3 was turned off to identify the notification of the system’s functionality. This also allows the system to not notify the personnel in charged of the project deployment. Testing and calibrating each camera was also shown in figure 6a and 6b.

-
Fig. 7. OpenCV application
In this figure 7, when the application detects a motion through the subtraction of the original image and the second image using image processing. Then it will trace the object through match template function and will draw a box to identify the area of the match. This will identify the bounding box of the images that was detected by the system which was the result of the image subtraction.
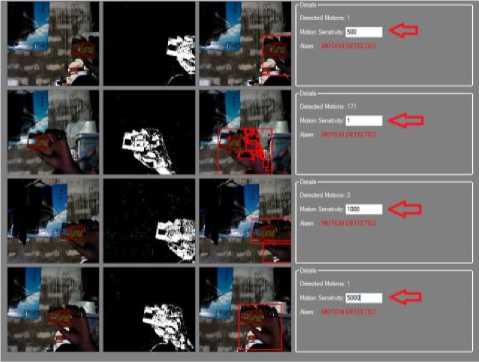
Fig. 8. Sensitivity Testing.
5. Conclusion
Changing the sensitivity level of the application, the figure 8 states that the lesser the value of the sensitivity, the more it is sensitive to a motion. When the sensitivity level was set to 1, all of the movement are determined and was it results to slower interaction but more précised. When the sensitivity level was set higher, the motion was determined by group. The transition and the output was faster.
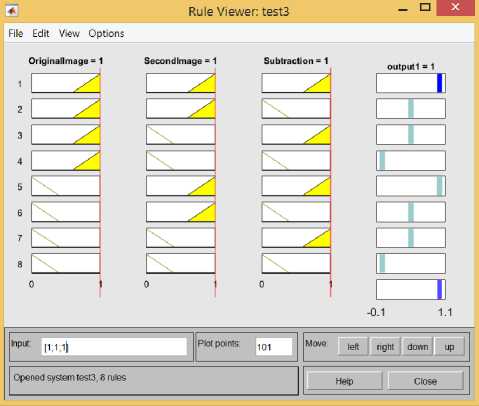
Fig. 9. Rule Viewer
Testing of each data in the fuzzy system will make trigger the image to capture the video. When the set of rules was applied to the system, it integrates the Sugeno method in the subtracted image that is determined by the second image and would create a bounding box to signify the difference. The rules covers all the instances that may occur in the system, hence the boundaries of capturing images that was effectively subtracted from the first image also depends on the sensitivity level that was set by the user.
The proposed study is composed of different technology which was combined by the author to answer the different difficulties which was encountered by the school and may be applied in different establishments.
Based from the experiment conducted, using rule-based expert system with fuzzy expert system in a surveillance camera would save some amount of hard drive space. In the experiment, it was not measured, but by recording only when there is a motion, the surveillance camera would not record from 9 pm until 7 in the morning. The sensitivity level in the experiment shows that the lesser the value, the more sensitive the detection becomes in detailed areas. The larger the value, the motion are detected as a group. It is shown in figure 3 that the set of rules was predetermined to be a guidelines for the whole system while in figure 8 showed the sensitivity level, this will allow the user to interact with the settings. The lower value of the sensitivity, the more sensitive the system which takes more time to evaluate the image subtracted while the higher the value, the faster the detection. However, if the value of sensitivity is high, the tendency to identify the object is not precise that may detect objects as batch.
A natural 1-day video of a CCTV footage with a 1920x1080 resolution, Audio Codec AAC and H. 264 codec specification usually consumes 20-30 MB per minute which is roughly 1.5 GB per day. With this approach, the recordings will take place every motion detected, saving a lot of memory spaces. The school hours start from 7:00 am with a maximum of 8:00 pm which is 13 hours, may have the maximum of 13 hours, saving 11 hours of video recordings which is 46% of memory storage per day.
Список литературы An Application of Rule-Based Classification with Fuzzy Logic to Image Subtraction
- G. Constantino, “DEPED COMPUTERIZATION PROGRAM,” 2018. https://www.deped.gov.ph/2018/04/06/deped-computerization-program/
- Y. Bai et al., “Impact of online computer assisted learning on education: Experimental evidence from economically vulnerable areas of China,” Econ. Educ. Rev., vol. 94, p. 102385, Jun. 2023, doi: 10.1016/j.econedurev.2023.102385.
- S. J. Lee, G. M. Francom, and J. Nuatomue, “Computer science education and K-12 students’ computational thinking: A systematic review,” Int. J. Educ. Res., vol. 114, p. 102008, 2022, doi: 10.1016/j.ijer.2022.102008.
- M. T. Montemayor, “Return stolen computers: DepEd,” 2018. https://www.pna.gov.ph/articles/1048448
- Department of education, “DepEd, PNP foil illegal online sale of DepEd-issued laptop; warns of legal action vs theft of gov’t property,” 2018, [Online]. Available: https://www.deped.gov.ph/2018/10/03/deped-pnp-foil-illegal-online-sale-of-deped-issued-laptop-warns-of-legal-action-vs-theft-of-govt-property/
- G. Wang, H. Ding, M. Duan, Y. Pu, Z. Yang, and H. Li, “Fighting against terrorism: A real-time CCTV autonomous weapons detection based on improved YOLO v4,” Digit. Signal Process., vol. 132, p. 103790, Dec. 2022, doi: 10.1016/j.dsp.2022.103790.
- P. Siagian and E. Fernando, “The Design and Implementation of a Dashboard Web-Based Video Surveillance in OpenStack Swift,” Procedia Comput. Sci., vol. 179, pp. 448–457, 2021, doi: 10.1016/j.procs.2021.01.028.
- V. Cho, K. C. Mansfield, and J. Claughton, “The past and future technology in classroom management and school discipline: A systematic review,” Teach. Teach. Educ., vol. 90, p. 103037, Apr. 2020, doi: 10.1016/j.tate.2020.103037.
- M. D. Hernandez, A. C. Fajardo, R. P. Medina, J. T. Hernandez, and R. M. Dellosa, “Implementation of data augmentation in convolutional neural network and gradient boosted classifier for vehicle classification,” Int. J. Sci. Technol. Res., vol. 8, no. 12, pp. 185–189, 2019, [Online]. Available: http://www.ijstr.org/final-print/dec2019/Implementation-Of-Data-Augmentation-In-Convolutional-Neural-Network-And-Gradient-Boosted-Classifier-For-Vehicle-Classification.pdf
- A. S. Alon, M. C. A. Venal, S. V. Militante, M. D. Hernandez, and H. B. Acla, “Lyco-frequency: A development of lycopersicon esculentum fruit classification for tomato catsup production using frequency sensing effect,” Int. J. Adv. Trends Comput. Sci. Eng., vol. 9, no. 4, pp. 4690–4695, 2020, doi: 10.30534/ijatcse/2020/72942020.
- M. D. Hernandez, A. C. Fajardo, and R. P. Medina, “A Hybrid Convolutional Neural Network-Gradient Boosted Classifier for Vehicle Classification,” IJRTE J., no. 2, pp. 213–216, 2019, doi: 10.35940/ijrte.B1016.078219.
- Cisco System, “The Internet of Everthings - Global Private Sector Economics Analysis,” Cisco Syst., pp. 1–9, 2013, [Online]. Available: https://www.cisco.com/c/dam/en_us/about/ac79/docs/innov/IoE_Economy_FAQ.pdf
- N. Di Cicco, F. Tonini, V. Cacchiani, and C. Raffaelli, “Optimization over time of reliable 5G-RAN with network function migrations,” Comput. Networks, vol. 215, p. 109216, Oct. 2022, doi: 10.1016/j.comnet.2022.109216.
- C. H. Lee et al., “On natural language call routing,” Speech Commun., vol. 31, no. 4, pp. 309–320, 2000, doi: 10.1016/S0167-6393(99)00064-3.
- T. D. Shashikala, S. L. Sunitha, and S. Basavarajappa, “Quantification of worn surface using digital image processing,” Tribol. Int., vol. 176, p. 107864, Dec. 2022, doi: 10.1016/j.triboint.2022.107864.
- S. Sahoo, N. Dash, and P. Sahoo, “Word Extraction from Speech Recognition using Correlation Coefficients,” Int. J. Comput. Appl., vol. 51, no. 13, pp. 21–25, 2012, doi: 10.5120/8102-1694.
- Himanshu Jain, D. Kroening, N. Sharygina, and E. Clarke, “Word level predicate abstraction and refinement for verifying RTL Verilog,” in Proceedings. 42nd Design Automation Conference, 2005., 2005, pp. 445–450. doi: 10.1109/DAC.2005.193850.
- H. Li and Q. Liu, “Hardware Trojan detection acceleration based on word-level statistical properties management,” in 2014 International Conference on Field-Programmable Technology (FPT), Dec. 2014, pp. 153–160. doi: 10.1109/FPT.2014.7082769.
- J. Yadav and K. S. Rao, “Generation of emotional speech by prosody imposition on sentence, word and syllable level fragments of neutral speech,” in 2015 International Conference on Cognitive Computing and Information Processing(CCIP), Mar. 2015, pp. 1–5. doi: 10.1109/CCIP.2015.7100694.
- X. Sun, P. Kalla, and F. Enescu, “Word-level traversal of finite state machines using algebraic geometry,” in 2016 IEEE International High Level Design Validation and Test Workshop (HLDVT), Oct. 2016, pp. 142–149. doi: 10.1109/HLDVT.2016.7748268.
- C. Yu and M. Ciesielski, “Automatic word-level abstraction of datapath,” in 2016 IEEE International Symposium on Circuits and Systems (ISCAS), May 2016, pp. 1718–1721. doi: 10.1109/ISCAS.2016.7538899.
- A. Saepullah, “Comparative Analysis of Mamdani, Sugeno and Tsukamoto Method of Fuzzy Inference System for Air Conditioner Energy Saving,” J. Intell. Syst., vol. 1, no. 2, pp. 143–147, 2015.
- OpenCV, “Template Matching,” 2019. https://docs.opencv.org/2.4/doc/tutorials/imgproc/histograms/template_matching/template_matching.html (accessed Mar. 10, 2023).
- J. Xu and P. Mishra, “Combining deep learning with chemometrics when it is really needed: A case of real time object detection and spectral model application for spectral image processing,” Anal. Chim. Acta, vol. 1202, p. 339668, Apr. 2022, doi: 10.1016/j.aca.2022.339668.
- T. Scharf, C. L. Kirkland, M. L. Daggitt, M. Barham, and V. Puzyrev, “AnalyZr: A Python application for zircon grain image segmentation and shape analysis,” Comput. Geosci., vol. 162, p. 105057, May 2022, doi: 10.1016/j.cageo.2022.105057.
- T. Peng-o and P. Chaikan, “High performance and energy efficient sobel edge detection,” Microprocess. Microsyst., vol. 87, p. 104368, Nov. 2021, doi: 10.1016/j.micpro.2021.104368.


