An empirical investigation on the impact of trust mediated determinants and moderating factors on the adoption of cloud computing
Автор: Saad Alharbi
Журнал: International Journal of Information Technology and Computer Science @ijitcs
Статья в выпуске: 11 Vol. 9, 2017 года.
Бесплатный доступ
In a prior study we found out that trust is an effective factor in the acceptance and adoption of cloud computing using the UTAUT. However, various relationships from the original UTAUT were not confirmed in the extended model for cloud computing. Therefore, we present here a study aimed at investigating the mediation effect of trust on users’ attitude toward the adoption of cloud computing using UTAUT. It is also aimed to examine the role of five moderating factors which are gender, age, education, managerial level and job domain on subjects’ behavioral intention to use cloud computing services. Data were collected from 219 subjects in order to test the modified model and were analyzed using Partial Least Square (PLS) algorithm. Experimental results demonstrated that Performance Expectancy and Facilitating Conditions are strongly mediated by trust for the behavioral intention to adopt cloud computing. Statistical results, on the other hand, indicated that the majority of the moderating factors did not have a significant impact on the acceptance of cloud computing. The paper finally concludes with the limitations of current study and directions for future work.
Adoption, Cloud Computing, Mediation, Moderation, Trust, UTAUT(Unified Theory of Acceptance and Use of Technology)
Короткий адрес: https://sciup.org/15016205
IDR: 15016205 | DOI: 10.5815/ijitcs.2017.11.02
Текст научной статьи An empirical investigation on the impact of trust mediated determinants and moderating factors on the adoption of cloud computing
Published Online November 2017 in MECS
Despite the fact that benefits of cloud computing are known almost to everybody in the field of computing, organizations still facing challenges and obstacles transforming their services and applications to the cloud. Trust is one of the major and most critical factors that would prevent organizations adopting cloud computing. According to [1], Fujitsu Research Institute carried out a survey on cloud computing adoption and showed that 88% of consumers were worried about who have permission to access their data and 84% had concerns about the location of storing their data. In addition, [2] highlighted that trust management and security is one of the top 10 challenges and obstacles of adopting cloud computing. This is mainly because of concerns about privacy, compatibility and security. Also, with the growing number of Cloud Service Providers (CSP) in the market who offer almost the same services, selecting the most trustworthy one has become challenging task. In order to assure Cloud Clients (CC) with their services, CSP usually offer Service Level Agreement (SLA). However, researchers such as [3] highlighted that such approach would not be sufficient for gaining consumers’ trust as unclear specifications and ambiguous statements would make it difficult to recognize the trustworthy CSP. Furthermore, doubts of CSP would not be obliged to Service Level Agreement (SLA) maybe one of the issues that make SLA is not a sufficient trust management system for cloud computing. Various cloud trust management systems were proposed in the literature that deal with cloud trust from different perspective (see Section II.A). However, to the best of our knowledge the question Would trust affect adopting cloud computing applications? Have not been fully addressed at present. On the other hand, numerous studies were carried out in order to evaluate the acceptance of cloud computing in organizations in various domains using different models (see Section II.B). However, the effect of trust on the acceptance of cloud computing was not addressed. In a prior study [4] we investigated the relationship between trust and acceptance of cloud computing by extending the Unified Theory of Acceptance and Use of Technology (UTAUT) and it was found that trust is an effective factor of cloud acceptance. However, some of the relationships amongst the constructs of the original UTAUT were not validated and whether trust would affect these relationships. Therefore, this study tries to fill this gap by extending the usefulness of the Unified (UTAUT) to understand the direct and indirect effects of trust on the attitude of users toward adopting cloud computing. The study also aims to examine the effect of five moderating factors (i.e. gender, age, education, managerial level and job domain) on the behavioral intention to adopt cloud computing.
The reminder of the paper is organized as follows section II.A shed the light on technology trust and how trust becomes one of the crucial factors for adopting cloud computing. Section II.B shows previous studies in the field of cloud acceptance and adoption and discusses factors influencing the readiness of organizations for adopting cloud computing. The proposed model and experimental hypotheses are discussed in Section III. Subjects profile are explained in section IV. The results and data analysis are then presented in Section V. Next, we discuss these results in Section VI and show the findings and implications of the study. Finally, conclusion is shown in section VII.
-
II. Literature Review
Recently, cloud computing has extensively been studied technically and from other point of views such as [5, 6]. As the aim of this paper is to investigate the determinants of trusting cloud computing, this section will be divided into the following two sub-sections.
-
A. Technology and Trust
According [7], interpersonal trust can be defined as “willingness of a party to be vulnerable to the actions of another party based on the expectation that the other will perform a particular action important to trustor irrespective of the ability to monitor or control the other party”. It is also believed that trust can be existed between people and non-human entities. For example, we trust airplanes that travel us safely from place to another. Furthermore, [8] pointed out that we sufficiently trust bridges and walk under them calmly. Though, various researchers such as [9] claimed that trust between people and technology is not existed. Furthermore, others stated that such relationship does not last long as if the technology fails to perform a particular task trust it would be transformed to frustration [10]. However, we believe that human today highly trust technology and several examples are available in our daily life. For instance, [11] highlighted that people usually trust word processing applications to save their documents as well as sharing images and personal information with others over the internet. Therefore, researchers are investigating the factors affecting the trust of technology and how trust would affect the usage of technology. Interpersonal personal was found to be affected by numerous factors more importantly benevolence, understandability, integrity and competence [7, 12]. However, [13] pointed out that trusting technology is affected by other factors that are related to the weakness and limitations of technology. For instance, validity, robustness, reliability, utility and false-alarm are considered as major factors of technology trust. Furthermore, [12] performed a study in order to investigate whether trust affect users’ satisfaction and their intention toward using technology. The results indicated that trust is significantly affected by performance, usefulness, ease of use, satisfaction and disconfirmation. Moreover, technology trust can be classified into two different forms particularly humanlike trust and system-like trust [11]. However, it is not straight forward to decide which form to use and which factors to adopt.
In fact, it depends entirely on the technology being used and the domain it is implemented in. Therefore, various studies where carried out in the literature to investigate the effect of trust on the adoption of new technology in different domain such as e-commerce [1419] and e-government [20-26]. Furthermore, trust has become one of the most critical factors affecting the adoption and usage of cloud services. Therefore, numerous studies are existed in the literature studying how to provide trustworthy cloud services. In such studies researchers usually implement trust management systems based on several cloud attributes and present the results. For instance, [3] claimed that at present trust evaluation systems that evaluates trust based on the compliance of Cloud Service Providers (CSP) with SLA is not existed. Therefore, they proposed a Compliancebased Multi-Dimensional Trust Evaluation System (CMTES) where cloud clients can decide the trustworthy cloud service provider from different perspectives (i.e. cloud client, Cloud Broker and Peers). The proposed system is consisted of three major entities which are cloud client, cloud broker, cloud auditor where they evaluate cloud service provider independently based on the Quality of Service (QoS) in the SLA. The final trustworthiness of Cloud Service Provider is derived from the aggregated trustworthiness perceived from the three entities. The proposed system was experimented using artificial data and the results presented CMTES is effective in recognizing trustworthy Cloud Service Providers (CSP). [27], on the other hand, proposed a trust management architecture that is consisted of three main components which are Cloud Service Registry and Discovery, Dynamic Trust component and Trust calculator. Cloud Service Registry and Discovery allows cloud providers to register themselves and record their trust values where trust calculator is responsible of computing the overall trust of a provider based on previous trust values and feedback. Dynamic Trust Component, on the other hand, is responsible of keeping track the trust values which changes over time. A mathematical model was adopted to compute trust based on feedback and trust values. However, it was not tested and no experimental results were presented.
-
[28] were also proposed a framework for trust management in cloud environments. It is consisted of three layers which are hard-trust, virtual –trust and entity trust. The first one can be considered as the main block of the trustworthiness of cloud services which are a set of actions in the cloud environment. Virtual trust, on the other hand, is the set of evidence about virtual servers’ security which the cloud provider must presents to users. Entity-trust is the layer responsible about building users trust on cloud computing service based on the behavior records of other entities. They claimed that the combination of these layers would bridge the gap between trust factors. However, experimental results were not provided. [29], also, proposed an adaptive trust model to dynamically evaluate cloud servers and recommend the high quality services. It is called CloudTrust which adopts multiple trust attributes for evaluation as well as it is consisted of two integrated types of modelling tools which are IOWA and rough set operators.
Data mining and knowledge discovery techniques are applied on trust attributes and time series in order to provide real-time recommendations. Furthermore, it was developed by three modules which are SLA module, trust management module and resource management module. Cloud-Trust was tested and experimental results demonstrated that it can effectively be used for trust management in cloud computing. [30] also developed a framework called Cloud-Trust. However, it was developed to evaluate trust of the services provided by cloud providers based solely on security. A wide range of security best practices and controls were incorporated in the proposed framework. The main idea behind it, is that an overall assessment of cloud services based on high level security metrics such as integrity and confidentiality and presenting the probability of penetration of cloud services provider. [31] developed an approach using evidential reasoning (ER) to help cloud client selecting the most trustworthy services. It is a multi-dimensional approach which mainly depends on historical users’ feedback and ratings. Various issues can be addressed by the multi-dimensional approach such as establishing a real-time trust evidence for all services and dynamically identifying most trustworthy services. However, no experimental results were presented.
The literature of cloud computing is rich with studies proposing trust management models for cloud computing based on different perspectives such as [1, 32-34]. Various researchers tried to survey such models and compare amongst them such as [35] while other tried to demonstrate the obstacles and challenges of developing cloud trust management systems such as [2, 36].
-
B. Adoption of Cloud Computing
Because of the various factors and issues that were found out by many researchers, such as the above, that would affect the adoption and maximization of cloud computing, [47] proposed the concept of cloud federation. It is a cooperation amongst several cloud providers to deploy services. They highlighted that cloud federation would enhance deploying services by maximizing the utilization of IT resources. Furthermore, a study was carried out to identify factors influencing the proposed concept. The results indicated that large cloud providers are willing to adopt such an idea while small providers were found to be driven by the pressure of competitors. Six determinants of accepting cloud federation which are flexibility, service quality decline, interoperability, frim size, legal issues and competitive pressure were also identified. [48] also proposed a trust model for cloud computing environments selection. The proposed model evaluates the quality of services of cloud based on several measures such as effectiveness, performance and user ratings. In order to test the feasibility of the proposed model it was validated using different simulations and the results were promising.
As it can be noticed that most of these studies have not fully addressed the effect of trust on the adoption of cloud computing using the well-known model which is the Unified Theory of Acceptance and Use of Technology (UTAUT). In line with the literature, the results of a prior study [4] showed that trust is a crucial factor in the adoption of cloud computing. However, the direct and indirect effects of trust on the constructs of UTAUT was not considered as well as the effects of moderating factors on the adoption of cloud computing was not addressed.
-
III. Hypotheses Development
The main aim of this research is to conduct an empirical study to investigate the effect of trust on the relationships amongst independent and dependent construct in the UTAUT. The context of this research is acceptance of cloud computing applications and solutions.
Specifically, the impact of trusting cloud computing on the relationships between performance expectancy and behavioral intention to use and, facilitating conditions and behavioral intention to use cloud computing application will be investigated. Furthermore, we believed that trust would mediate the relationships of social influence and effort expectancy with behavioral intention to use cloud computing. Fig.1 shows the proposed extended model. The study also aimed at studying the effect of moderating factors specifically age, gender, education, managerial level and job domain. In addition, we are interested to find out whether acceptance of cloud computing differs across these groups. Therefore, we formulated the following hypotheses:
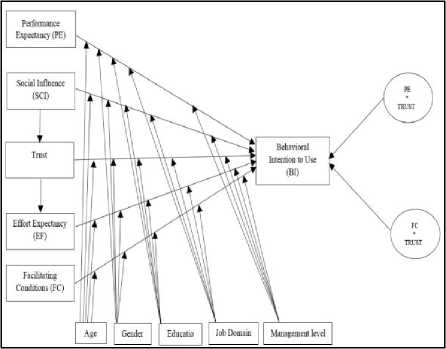
Fig.1. Research Model
H1 : Trust will positively moderate the relationship between performance expectancy and behavioral intention to use cloud computing.
H2 : Trust will positively moderate the relationship between facilitating conditions and behavioral intention to use cloud computing.
H3 : Trust will positively mediate the relationship between social influence and behavioral intention to use cloud computing.
H4 : Trust will positively mediate the relationship between effort expectancy and behavioral intention to use cloud computing.
H5 : Age will moderate the relationship between performance expectancy and behavioral intention to use cloud computing.
H6 : Age will moderate the relationship between social influence and behavioral intention to use cloud computing.
H7 : Age will moderate the relationship between effort expectancy and behavioral intention to use cloud computing.
H8 : Age will moderate the relationship between facilitating conditions and behavioral intention to use cloud computing.
H9 : Age will moderate the relationship between trust and behavioral intention to use cloud computing.
H10 : Gender will moderate the relationship between performance expectancy and behavioral intention to use cloud computing.
H11 : Gender will moderate the relationship between social influence and behavioral intention to use cloud computing.
H12 : Gender will moderate the relationship between effort expectancy and behavioral intention to use cloud computing.
H13 : Gender will moderate the relationship between facilitating conditions and behavioral intention to use cloud computing.
H14 : Gender will moderate the relationship between trust and behavioral intention to use cloud computing.
H15 : Education will moderate the relationship between performance expectancy and behavioral intention to use cloud computing.
H16 : Education will moderate the relationship between social influence and behavioral intention to use cloud computing.
H17 : Education will moderate the relationship between effort expectancy and behavioral intention to use cloud computing.
H18 : Education will moderate the relationship between facilitating conditions and behavioral intention to use cloud computing.
H19 : Education will moderate the relationship between trust and behavioral intention to use cloud computing.
H20 : Job domain will moderate the relationship between performance expectancy and behavioral intention to use cloud computing.
H21 : Job domain will moderate the relationship between social influence and behavioral intention to use cloud computing.
H22 : Job domain will moderate the relationship between effort expectancy and behavioral intention to use cloud computing.
H23 : Job domain will moderate the relationship between facilitating conditions and behavioral intention to use cloud computing.
H24 : Job domain will moderate the relationship between trust and behavioral intention to use cloud computing.
H25 : Managerial level will moderate the relationship between performance expectancy and behavioral intention to use cloud computing.
H26 : Managerial level will moderate the relationship between social influence and behavioral intention to use cloud computing.
H27 : Managerial level will moderate the relationship between effort expectancy and behavioral intention to use cloud computing.
H28 : Managerial level will moderate the relationship between facilitating conditions and behavioral intention to use cloud computing.
H29 : Managerial level will moderate the relationship between trust and behavioral intention to use cloud computing.
written in English and Arabic in order to ensure subjects’ full comprehension of statements. The first section seeking subjects’ personal information such as age, gender and In these sections, statements related to constructs were After leaving the questionnaire available online for three months, two hundred and nineteen complete responses were received, of which 29 were females (13.2%) and 190 were male (86.8%). Subjects’ age ranged from 18 to 64, the majority was aged between 25-34 (36.5%) whereas only ten subjects (4.6%) aged between 18-24. Further, subjects were distributed into three job domains, which are hardware, software and administration as well as several managerial levels. Table 1 shows more a descriptive analysis of subjects’ profile. presented to subjects and they were asked to rate their agreement on them based on a 5-point likert scales ranging from strongly agree to strongly disagree, where 1 denoted strongly disagree and 5 denoted strongly agree. All statements were adopted from previous studies and modified to suit our study context. The hyperlink of the questionnaire was sent by email to employees working in information technology centers and IT departments in the public and private sectors in the kingdom of Saudi Arabia. They were also requested to forward the survey to their colleagues and friends. education as well as asking about work information such as position and job domain. All questions were required and a multi-item where users asked to select the most appropriate items for them. This method was employed to reduce data entry errors that would affect data analysis. The remaining sections representing the constructs of the proposed UTAUT model where each section represented a construct.
|
Table 1. Subjects demographics |
|||
|
Measure |
Value |
Frequency |
Percentage |
|
18-24 |
10 |
4.6% |
|
|
25-34 |
80 |
36.5% |
|
|
Age |
35-44 |
57 |
26.0% |
|
45-54 |
60 |
27.4% |
|
|
55-64 |
12 |
5.5% |
|
|
Hardware |
22 |
10.0% |
|
|
Job Domain |
Software |
81 |
37.0% |
|
Management |
116 |
53.% |
|
|
Male |
190 |
86.8% |
|
|
Gender |
Female |
29 |
13.2% |
|
School |
20 |
9.1% |
|
|
Education |
University |
62 |
28.3% |
|
Postgraduate |
137 |
62.6.3% |
|
|
Top |
31 |
14.2% |
|
|
Managerial level |
Medium |
66 |
30.1% |
|
Low |
122 |
55.7% |
|
-
IV. Sample and Data Collection
V. Results
The data collection instrument of this study was an online questionnaire consisting of 7 sections. It was developed in bio-lingual format were all statements were
Structural Equation Modeling (SEM) using SmartPLS 3 [49] was used in this study in order to test the validity of the proposed model and to assess the relationships and effects amongst constructs. SmartPLS 3 is one of the powerful tools in performing multi-group analysis and assessing mediation and moderation effects. At the beginning of data analysis, confirmatory factor analysis (CFA) was carried out to examine the reliability and validity of the instrument used. Cronbach's Alpha is one of the common tests used to examine the reliability of constructs. Therefore, it was performed on all constructs and as seen in Table 2 that the Alpha value of all constructs is greater than the recommended value by [50].
Table 2. Factors loadings and constructs reliability and validity
|
Constructs |
Items |
α |
CR |
AVE |
BI |
EP |
FC |
PE |
SI |
TS |
|
BI1 |
0.938 |
0.549 |
0.590 |
0.590 |
0.517 |
0.602 |
||||
|
BI |
BI2 |
0.931 |
0.956 |
0.879 |
0.938 |
0.549 |
0.590 |
0.588 |
0.533 |
0.598 |
|
BI3 |
0.937 |
0.549 |
0.590 |
0.590 |
0.503 |
0.603 |
||||
|
EF1 |
0.516 |
0.851 |
0.374 |
0.573 |
0.484 |
0.525 |
||||
|
EF2 |
0.490 |
0.850 |
0.399 |
0.534 |
0.560 |
0.478 |
||||
|
EF |
0.879 |
0.917 |
0.734 |
|||||||
|
EF 3 |
0.541 |
0.858 |
0.391 |
0.603 |
0.466 |
0.544 |
||||
|
EF 4 |
0.452 |
0.867 |
0.408 |
0.559 |
0.477 |
0.491 |
||||
|
EP1 |
0.574 |
0.632 |
0.406 |
0.912 |
0.407 |
0.644 |
||||
|
EP2 |
0.578 |
0.641 |
0.407 |
0.929 |
0.364 |
0.678 |
||||
|
PE |
0.914 |
0.940 |
0.797 |
|||||||
|
EP3 |
0.558 |
0.568 |
0.322 |
0.887 |
0.384 |
0.671 |
||||
|
EP4 |
0.534 |
0.523 |
0.250 |
0.839 |
0.353 |
0.588 |
||||
|
FC1 |
0.535 |
0.389 |
0.851 |
0.339 |
0.419 |
0.347 |
||||
|
FC |
FC2 |
0.810 |
0.887 |
0.724 |
0.536 |
0.391 |
0.851 |
0.326 |
0.407 |
0.346 |
|
FC3 |
0.536 |
0.390 |
0.851 |
0.330 |
0.431 |
0.358 |
||||
|
SCI3 |
0.504 |
0.517 |
0.444 |
0.412 |
0.920 |
0.414 |
||||
|
SC |
0.816 |
0.916 |
0.844 |
|||||||
|
SCI 4 |
0.510 |
0.546 |
0.460 |
0.365 |
0.918 |
0.392 |
||||
|
Trust10 |
0.529 |
0.488 |
0.279 |
0.615 |
0.304 |
0.846 |
||||
|
Trust13 |
0.560 |
0.485 |
0.403 |
0.609 |
0.331 |
0.802 |
||||
|
Trust6 |
0.605 |
0.569 |
0.417 |
0.641 |
0.375 |
0.839 |
||||
|
Trust |
0.927 |
0.942 |
0.732 |
|||||||
|
Trust7 |
0.490 |
0.489 |
0.303 |
0.610 |
0.417 |
0.862 |
||||
|
Trust8 |
0.523 |
0.493 |
0.350 |
0.592 |
0.418 |
0.891 |
||||
|
Trust9 |
0.569 |
0.527 |
0.349 |
0.640 |
0.403 |
0.889 |
In addition, composite reliability (CR) was also computed for all constructs and the results indicated that all CR values for all constructs exceeded the recommended value by [50]. Thus, the reliability of the instrument used in this study is within good level.
The validity of the proposed model was also investigated by examining convergent and discriminant validity. Convergent validity can be examined through factor loadings where items should have the heights loadings in their related constructs and have lower ones in unrelated constructs [50]. As shown in Table 2, factor loadings of all items are the heights in their corresponding constructs. Furthermore, Average Variance Extracted (AVE) was also computed to further ensure validity of the proposed model. As shown in Table 2, the value of AVE for all construct exceeded the recommended value by [51]. Discriminant validity was also measured in order to ensure that constructs are different and do not highly correlate with each other. According to [51], the discriminant validity level can be accepted if the square root of the AVE is greater than the coefficients of the inter-constructs correlation. Table 3 shows that correlation matrix of the constructs where diagonal shows the square root of AVE. it can be noted that the values in the diagonal are greater than the below values which represent a discriminant validity of the model.
After ensuring the validity and reliability of the proposed model, path analysis was performed using Partial Least Square (PLS) algorithm in order to investigate the relationships between constructs and to test the proposed hypotheses. Fig. 2 shows the structural model with obtained results. It shows path coefficients (β) and the explained variance (R2). Furthermore, in order to test the significance of the relationships amongst constructs and to better interpret the results shown in Fig.2, the t-statistic value was calculated for each relationship by performing a bootstrapping with 5000 subsample. The results indicated that performance expectancy significantly affecting users’ behavioral intention to use cloud computing (β=0.23, t=2.70, p<0.05). Social influence was also found significantly affecting users’ behavioral intention to use cloud computing (β=0.14, t=2.32, p<0.05). Furthermore, the effect of facilitating conditions was found extremely significant on users’ behavioral intention to use cloud computing (β=0.42, t=8.15, p<0.01). Clearly, these results come in line with the original UTAUT. On the other hand, the effect of effort expectancy on users’ behavioral intention to use cloud computing was not found significant (β=0.095, t=1. 53, p=0.13) which contradicted with original UTAUT model. Moreover, the results indicated that trust would significantly affect users’ intention to use cloud computing (β=0.27, t=3. 70, p<0.01). Fig.2 also shows that all five constructs which are performance expectancy, effort expectancy, social influence, facilitating conditions and trust are predictive of intention to use cloud computing with 70% explained variance (R2=0.71).
Table 3. Constructs correlations; bold values on the diagonal are the square root of the AVE
|
BI |
EF |
FC |
PE |
SCI |
Trust |
|
|
BI |
0.937 |
|||||
|
EF |
0.586 |
0.857 |
||||
|
FC |
0.629 |
0.458 |
0.851 |
|||
|
PE |
0.629 |
0.664 |
0.390 |
0.893 |
||
|
SCI |
0.552 |
0.578 |
0.492 |
0.423 |
0.919 |
|
|
Trust |
0.641 |
0.597 |
0.412 |
0.724 |
0.439 |
0.856 |
The effect of trust on the relationship between performance expectancy and facilitating conditions with users’ intention to use cloud computing was tested. The results indicated that trust has a significant moderation effect on the relationship between performance expectancy and users’ behavioral intention to use (β=0.26, t=5. 40, p<0.01). Similarly, it significantly moderating the relationship between facilitating conditions and behavioral intention to use (β=- 0.27, t=7. 35, p<0.01). Thus, hypotheses 1 and 2 were accepted. In addition, the mediation effect of trust on the relationship between social influence and effort expectancy with behavioral intention to use cloud computing was test. In order to identify whether trust mediate the relationship between social influence and users’ intention to use, path coefficient was calculated after removing the mediator construct (trust). The results demonstrated a higher path coefficient between social influence and users’ intention to use (β=0.173) than with the existence of trust. In order to test whether this difference is significant, Sobel test was carried out using the free online Sobel calculator tool and the result indicated that trust significantly mediate the effect of social influence on users’ behavior intention to use cloud computing (t=1.73, p<0.05). Therefore, hypothesis 3 is accepted. Furthermore, the mediation here can be considered as partial because of that the relationship between social influence and behavioral intention to use was found statistically significant. On the other hand, the results demonstrated a lower path coefficient for the relationship between effort expectancy and behavioral intention to use without trust (β=0.078) than the one with existence of trust which is shown in Fig.2 the results of Sobel test indicated that trust significantly mediate the relationship between effort expectancy and behavioral intention to use (t=3.22, p<0.01). Furthermore, this mediation can be considered as full mediation as the direct relationship between effort expectancy and behavioral intention to use is not statistically significant. Thus, hypothesis 4 is accepted.
In order to investigate the influence of the moderating factors (age, gender, education, job domain and managerial level) on the constructs of the proposed model, path analysis was performed independently for each subjects’ group. The results are summarized in Table 4. As shown in Table 4, all constructs were found significantly affecting male users’ behavioral intention to use cloud computing. On the contrary, none of the constructs were found significantly affecting the attitude of female users toward the acceptance of cloud computing. In order to examine whether this difference is significant and would gender moderate the effect of constructs, multi-group analysis was performed with 100 subsample bootstrapping. The obtained results indicated that gender is not significantly moderating the effect of any of the constructs on users’ behavioral intention to use. Thus, hypotheses 10, 11, 12, 13 and 14 are rejected. Furthermore, the results indicated that the effect of most constructs on the intention to use cloud computing is more apparent with educated users.
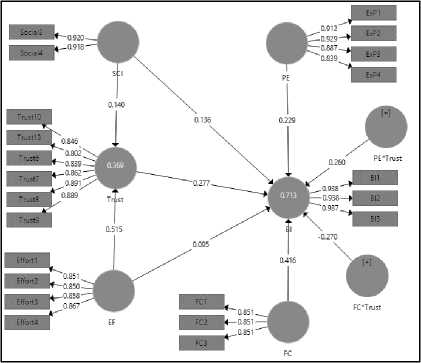
Fig.2. Estimated model by SmartPLS 3
Specifically, effort expectancy, facilitating conditions, performance expectancy and trust were found significantly affecting the attitude of users with postgraduate degree toward cloud computing applications (see Table 4). However, social influence construct had not significantly affected the attitude of the same group toward cloud computing. Users with university level degree, on the other hand, have not found any of the constructs affecting their attitude toward cloud computing except performance expectancy. Because of the limited number of users with high school education, we could not get results from statistical tests. Multi-group analysis was also carried out with the same bootstrapping properties performed for gender and the results indicated that the difference between users with university level education and those with postgraduates degrees is not statistically significant. Thus. Hypotheses 15, 16, 17, 18 and 19 are rejected. Subjects were grouped into two groups based on their age namely young and old in order to facilitate statistical tests where many age groups that were used in the survey and did not have sufficient number of responses to perform the test. As seen in Table 4, all constructs were found significantly affecting the behavioral intention of young subjects to adopt cloud computing except effort expectancy were it was not found to be significantly affecting them. On contrast, only facilitating conditions and trust were found to be significantly affecting the behavioral intention of older subjects to use cloud computing. Similarly, Multi-group analysis was carried out to investigate the significance of this difference. The results indicated that the difference between the two groups is not significant, therefore hypotheses 5, 6, 7 and 8 are rejected. Moreover, the effect of constructs amongst subjects in different managerial level were also examined. Table 4 shows that effort expectancy, facilitating conditions and trust were significantly affecting behavioral intention of subjects in the top management level whereas performance expectancy and social influence did not found to be significantly affecting their attitude toward the adoption of cloud computing. Further, attitude of subjects in medium level of management towards cloud computing were found to be significantly affected by facilitating conditions and trust while the rest of constructs were not found to be significant. By taking a deeper look at the results, it can be noticed that the difference in between these two groups in terms of effort expectancy, social influence and trust is high. Multi-group analysis was applied in order to test the difference between the two groups in terms of all constructs. The results demonstrated that the difference in the effect of effort expectancy on the attitude of subjects in the two groups is statistical significant (β= 0.193, p<0.05). The results also indicated that the difference in the other constructs is not significant. Furthermore, the effect of all constructs except social influence were found to be significantly affecting subjects at the low-level management attitude towards cloud computing. It can be noticed from Table 4 that the difference in the effect of effort expectancy and performance expectancy between subjects in medium level and low level management is considerably high. However, the results of the Multi-group analysis indicated that only the effect of performance expectancy in the two groups was significantly different. In addition, Table 4 shows that the difference in the β value of all constructs for subjects at low and high level management is slightly small therefore; the results of Multi-group analysis indicated that the difference of the effect of all constructs in the two groups is not significant. Thus, hypotheses 25 to 29 cannot be accepted. Additionally, Table 4 shows that that effort expectancy did not have significant effect of subjects’ behavioral intention to adopt cloud computing working in the Hardware, Software and administrational sides of information technology. In fact, the attitude of subjects working in the domain of administration was not found to be effected by any of the constructs including trust. The attitude of subjects working in Hardware was also not found to be effected by social influence. Actually, it can be noticed that t and β value of the three groups (i.e. Hardware, Software, Administration) are small and nearly the same therefore; Multi-group analysis results indicated there is no significant difference amongst the three groups in all constructs. Thus, hypotheses 20 to 24 cannot be accepted.
Table 4. Multi-Group analysis results
|
Moderating factors |
Groups |
Constructs |
||||
|
EF |
FC |
PE |
SCI |
Trust |
||
|
Gender |
Male |
(β= 0.08, t=1.53, p<0.01) |
(β= 0.42, t=6.14, p<0.01) |
(β= 0.22, t=3. 43, p<0.01) |
(β= 0.18, t=3. 85, p<0.01) |
(β= 0.25, t=5. 34, p<0.01) |
|
Female |
(β= 0.07, t=0. 29, p>0.05) |
(β=- 0.08, t=0. 48, p>0.05) |
(β= 0.35, t=0. 99, p>0.05) |
(β=- 0.15, t=0. 52, p>0.05) |
(β= 0.47, t=2. 09, p>0.05) |
|
|
Age |
Young |
(β= 0.06, t=0. 62, p>0.05) |
(β= 0.39, t=5. 72, p<0.01) |
(β= 0.22, t=2. 76, p<0.05) |
(β= 0.19, t=2. 31, p<0.05) |
(β= 0.24, t=3. 76, p<0.01) |
|
Old |
(β= 0.16, t=1.06, p>0.05) |
(β= 0.47, t=8. 53, p<0.01) |
(β= 0.23, t=1. 79, p>0.05) |
(β= 0.04, t=0. 52, p>0.05) |
(β= 0.35, t=3. 69, p<0.01) |
|
|
Education |
University |
(β=- 0.042, t=0. 37, p>0.05) |
(β= 0.30, t=2. 18, p>0.05) |
(β= 0.41, t=3. 22, p<0.01) |
(β=- 0.03, t=0. 27, p>0.05) |
(β=0.27, t=1. 78, p>0.05) |
|
Postgraduate |
(β= 0.15, t=2.61, p<0.05) |
(β= 0.40, t=8.16, p<0.01) |
(β= 0.21, t=2. 67, p<0.05) |
(β=0.16, t=2. 15, p>0.05) |
(β=0.29, t=3. 27, p<0.01) |
|
|
Top |
(β=- 0.48, t=2.45, p<0.05) |
(β=0.58, t=2. 29, p<0.05) |
(β= 0.39, t=1. 26, p>0.05) |
(β= 0.17, t=0. 88, p>0.05) |
(β= 0.38, t=3. 23, p<0.01) |
|
|
Managerial level |
Medium |
(β=0.00, t=0. 002, p>0.05) |
(β= 0.36, t=3. 89, p<0.01) |
(β= 0.05, t=0. 48, p>0.05) |
(β= 0.16, t=2. 14, p>0.05) |
(β=0.52, t=5. 32, p<0.01) |
|
Low |
(β= 0.18, t=1. 67, p>0.05) |
(β= 0.42, t=4. 71, p<0.01) |
(β= 0.32, t=3. 66, p<0.01) |
(β= 0.12, t=1. 61, p>0.05) |
(β= 0. 18, t=2. 64, p<0.05) |
|
|
Hardware |
(β= -0.001, t=0.005, p>0.05) |
(β= 0.48, t=5. 39, p<0.01) |
(β= 0.17, t=2. 46, p<0.05) |
(β= 0.12, t=1. 91, p>0.05) |
(β= 0. 32, t=5. 36, p<0.01) |
|
|
Job Domain |
Software |
(β= 0.16, t=1.84, p>0.05) |
(β= 0.39, t=4. 85, p<0.01) |
(β= 0.24, t=2. 29, p<0.05) |
(β= 0.16, t=4. 06, p<0.01) |
(β= 0. 25, t=2. 81, p<0.05) |
|
Administration |
(β= -0.33, t=0.86, p>0.05) |
(β= 0.34, t=0.77, p>0.05) |
(β= 0.51, t=1.76, p>0.05) |
(β= 0.15, t=0.57, p>0.05) |
(β= 0.05, t=0.18, p>0.05) |
|
-
VI. Discussion
The empirical results of our study have provided support for the validity of the proposed model and the instruments adopted to examine the acceptance of cloud computing. The reliability of the all constructs were ensured using the well know statistical test Cronbach's Alpha and the Campsite Reliability Value of all constructs have exceeded the recommended values in the literature, as well. The convergent and discriminant validity of all constructs were also established. In addition, the results obtained by this study have provided support that trust is an important factor in the acceptance of cloud computing. It was found to magnitude the relationships between performance expectancy and facilitating conditions with behavioral intention to use. Furthermore, the results indicated that trust can significantly mediate the relationship between social influence and behavioral intention to use cloud computing. Despite the fact that we found effort expectancy has not significantly affected users’ intention to adopt cloud computing, this relationship most likely will be the opposite with the existence of trust.
Surprisingly, the results obtained from this study demonstrated that the majority of the moderating factors did not have a significant effect on the acceptance of cloud computing. However, such finding would not be generalized as it is most likely because of the limitations of the study. Number of subjects in some groups was too small which make statistical test difficult and not possible for some cases. This is the major limitation of our study which would be considered in the future. For instance, the number of female subjects who participated in the study was 29 compared to 190 males. Further, most of the subjects were from management background where few of them had hardware background. Despite of these limitations we have yielded some interesting findings. For instance, the results indicated that behavioral intention of male subjects to adopt cloud computing were found to be significantly affected by all constructs (i.e. Effort Expectancy, Facilitating Conditions, Performance Expectancy, Social Influence and Trust) whereas none of them were found to be affecting female subjects’ attitude toward the adoption of cloud computing. However, gender was not found to be moderating factor for the acceptance of cloud computing. Furthermore, subjects were grouped into two categories based on their age which are young and old subjects because of the limited sample size in various age groups. Although no real difference between the two groups on the attitude toward adoption of cloud computing, the attitude of young subjects was found significantly affected by the majority of constructs which are trust, facilitating conditions, performance expectancy and social influence. Moreover, when investigating the effect of education as a moderating factor it was apparent that the effects of most constructs toward intention to use cloud is more with educated subjects. However, the difference in the perceived behavioral intention to accept cloud computing was not found statistically significant between subjects with university level and postgraduate ones. Similarly, subjects working in different domains (i.e. Hardware, Software and Administration) were found to be almost the same in terms of the effect of most constructs on the behavioral intention to adopt cloud computing. On the other hand, the effect of performance expectancy on the behavioral intention to adopt cloud computing was found to be different amongst subject in different managerial levels while no real difference was found on the other constructs.
The findings of our study have provided various implications in the users’ attitude towards adopting cloud computing. Practically, it demonstrates the direct effect of trust on the behavioral intention to adopt cloud computing. The study also gives insights to executives about the factors influencing the acceptance of cloud computing services in order to implement appropriate strategies and plans. Furthermore, the proposed model can be adopted by high level management in firms in order to evaluate the attitude of their personnel towards cloud computing. Theoretically, the study extends the usefulness of the UTAUT by providing a set of guidelines on the acceptance of cloud computing. The study also demonstrated that embedding trust into the UTAUT would show an adequate explanatory power to examine behavioral intention to use cloud computing. Furthermore, pervious research has demonstrated that trust is one of the crucial factors that would prevent firms to adopt cloud computing. Therefore, it was embedded into the UTAUT model where the results showed the validity of the proposed model for assessing the acceptance of cloud computing.
-
VII. Conclusion
We conducted an empirical study to investigate the direct and indirect effects of trust on the independent and dependent variables of the acceptance of cloud computing in organizations. The study also aimed to understand the role of five moderating factors (i.e. gender, age, education, managerial level and job domain) on the attitude of subjects toward cloud computing. Due to its usefulness in several domains and in cloud computing especially, the UTAUT was adopted and extended by adding trust as a main construct. The results indicated that trust is an important factor in the acceptance of cloud computing solutions. Specifically, it was found significantly strengthen the relationships between performance expectancy and facilitating conditions with behavioral intention to adopt cloud computing. On the contrary, the results demonstrated that the majority of the moderating factors did not have real impact on the acceptance of cloud computing. However, this is most likely due to various limitations of our study such as the distribution of the sample amongst different groups. Therefore, further studies that take into accounts these limitations would be carried out in the future.
Список литературы An empirical investigation on the impact of trust mediated determinants and moderating factors on the adoption of cloud computing
- S. M. Habib, S. Ries, M. Mühlhäuser, and P. Varikkattu, “Towards a trust management system for cloud computing marketplaces: using CAIQ as a trust information source,” Security and Communication Networks, vol. 7, no. 11, pp. 2185-2200, 2014.
- T. H. Noor, Q. Z. Sheng, S. Zeadally, and J. Yu, “Trust management of services in cloud environments: Obstacles and solutions,” ACM Comput. Surv., vol. 46, no. 1, pp. 1-30, 2013.
- S. Singh, and J. Sidhu, “Compliance-based Multi-dimensional Trust Evaluation System for determining trustworthiness of Cloud Service Providers,” Future Generation Computer Systems, vol. 67, pp. 109-132, 2//, 2017.
- S. Alharbi, “An extended UTAUT Model for Understanding of the Effect of Trust on Users' Acceptance of Cloud Computing,” International Journal of Computer Applications in Technology, vol. Accepted, 2017.
- S. A. Elmubarak, A. Yousif, and M. B. Bashir, “Performance based Ranking Model for Cloud SaaS Services,” 2017.
- S. Goyal, “Public vs private vs hybrid vs community-cloud computing: a critical review,” International Journal of Computer Network and Information Security, vol. 6, no. 3, pp. 20, 2014.
- R. C. Mayer, J. H. Davis, and F. D. Schoorman, “An integrative model of organizational trust,” Academy of management review, vol. 20, no. 3, pp. 709-734, 1995.
- D. H. McKnight, “Trust in information technology,” The Blackwell encyclopedia of management, vol. 7, pp. 329-331, 2005.
- B. Friedman, J. Peter H. Khan, and D. C. Howe, “Trust online,” Commun. ACM, vol. 43, no. 12, pp. 34-40, 2000.
- B. Shneiderman, “Designing trust into online experiences,” Commun. ACM, vol. 43, no. 12, pp. 57-59, 2000.
- N. K. Lankton, D. H. McKnight, and J. Tripp, “Technology, Humanness, and Trust: Rethinking Trust in Technology,” Journal of the Association for Information Systems, vol. 16, no. 10, pp. 880, 2015.
- N. Lankton, D. H. McKnight, and J. B. Thatcher, “Incorporating trust-in-technology into Expectation Disconfirmation Theory,” The Journal of Strategic Information Systems, vol. 23, no. 2, pp. 128-145, 6//, 2014.
- R. R. Hoffman, M. Johnson, J. M. Bradshaw, and A. Underbrink, “Trust in Automation,” IEEE Intelligent Systems, vol. 28, no. 1, pp. 84-88, 2013.
- K. S. Coulter, M. Brengman, and F. P. Karimov, “The effect of web communities on consumers' initial trust in B2C e-commerce websites,” Management Research Review, vol. 35, no. 9, pp. 791-817, 2012.
- Y. Fang, I. Qureshi, H. Sun, P. McCole, E. Ramsey, and K. H. Lim, “Trust, Satisfaction, and Online Repurchase Intention: The Moderating Role of Perceived Effectiveness of E-Commerce Institutional Mechanisms,” Mis Quarterly, vol. 38, no. 2, pp. 407-427, 2014.
- Y.-M. Li, C.-T. Wu, and C.-Y. Lai, “A social recommender mechanism for e-commerce: Combining similarity, trust, and relationship,” Decision Support Systems, vol. 55, no. 3, pp. 740-752, 6//, 2013.
- W.-T. Wang, Y.-S. Wang, and E.-R. Liu, “The stickiness intention of group-buying websites: The integration of the commitment–trust theory and e-commerce success model,” Information & Management, vol. 53, no. 5, pp. 625-642, 7//, 2016.
- I.-L. Wu, “The antecedents of customer satisfaction and its link to complaint intentions in online shopping: An integration of justice, technology, and trust,” International Journal of Information Management, vol. 33, no. 1, pp. 166-176, 2//, 2013.
- Y. Zhang, J. Bian, and W. Zhu, “Trust fraud: A crucial challenge for China’s e-commerce market,” Electronic Commerce Research and Applications, vol. 12, no. 5, pp. 299-308, 9//, 2013.
- E. Abu-Shanab, “Antecedents of trust in e-government services: an empirical test in Jordan,” Transforming Government: People, Process and Policy, vol. 8, no. 4, pp. 480-499, 2014.
- E. Abu-Shanab, and A. Al-Azzam, “Trust Dimensions and the adoption of E-government in Jordan,” International Journal of Information Communication Technologies and Human Development (IJICTHD), vol. 4, no. 1, pp. 39-51, 2012.
- L. Alzahrani, W. Al-Karaghouli, and V. Weerakkody, “Analysing the critical factors influencing trust in e-government adoption from citizens’ perspective: A systematic review and a conceptual framework,” International Business Review, vol. 26, no. 1, pp. 164-175, 2//, 2017.
- J. V. Chen, R. J. M. Jubilado, E. P. S. Capistrano, and D. C. Yen, “Factors affecting online tax filing – An application of the IS Success Model and trust theory,” Computers in Human Behavior, vol. 43, pp. 251-262, 2//, 2015.
- S. E. Colesca, “Understanding trust in e-government,” Engineering Economics, vol. 63, no. 4, 2015.
- Y. Gao, “The Influences Of Cognitive Factors And Trust On E-Government Acceptance: Evidence From A Two-Stage Model,” The Review of Business Information Systems (Online), vol. 17, no. 4, pp. 153, 2013.
- M. I. Manda, and J. Backhouse, “Addressing trust, security and privacy concerns in e-government integration, interoperability and information sharing through policy: a case of South Africa,” 2016.
- M. K. Muchahari, and S. K. Sinha, "A New Trust Management Architecture for Cloud Computing Environment." pp. 136-140.
- F. Wenjuan, Y. Shanlin, P. Jun, and H. Luo, “Building trust into cloud,” International Journal of Cloud Computing and Services Science, vol. 1, no. 3, pp. 115, 2012.
- X. Li, and J. Du, “Adaptive and attribute-based trust model for service level agreement guarantee in cloud computing,” IET Information Security, vol. 7, no. 1, pp. 39-50, 2013.
- D. Gonzales, J. Kaplan, E. Saltzman, Z. Winkelman, and D. Woods, “Cloud-Trust - a Security Assessment Model for Infrastructure as a Service (IaaS) Clouds,” IEEE Transactions on Cloud Computing, vol. PP, no. 99, pp. 1-1, 2015.
- W.-J. Fan, S.-L. Yang, H. Perros, and J. Pei, “A multi-dimensional trust-aware cloud service selection mechanism based on evidential reasoning approach,” International Journal of Automation and Computing, vol. 12, no. 2, pp. 208-219, 2015.
- D. Shapiro, M. Socher, R. Lei, S. Muralidhar, B. T. Loo, and N. Heninger, “DARUMA: Regaining Trust in Cloud Storage,” 2016.
- S. M. Khan, and K. W. Hamlen, "Hatman: Intra-cloud Trust Management for Hadoop." pp. 494-501.
- P. Manuel, “A trust model of cloud computing based on Quality of Service,” Annals of Operations Research, vol. 233, no. 1, pp. 281-292, 2015.
- M. Firdhous, O. Ghazali, and S. Hassan, “Trust management in cloud computing: a critical review,” arXiv preprint arXiv:1211.3979, 2012.
- K. Yamaji, M. Nakamura, Y. Nagai, T. Ito, and H. Sato, "Specifying a Trust Model for Academic Cloud Services." pp. 91-99.
- Z. Yang, J. Sun, Y. Zhang, and Y. Wang, “Understanding SaaS adoption from the perspective of organizational users: A tripod readiness model,” Computers in Human Behavior, vol. 45, pp. 254-264, 4//, 2015.
- R. Martins, T. Oliveira, and M. A. Thomas, “An empirical analysis to assess the determinants of SaaS diffusion in firms,” Computers in Human Behavior, vol. 62, pp. 19-33, 9//, 2016.
- M. Stieninger, D. Nedbal, W. Wetzlinger, G. Wagner, and M. A. Erskine, “Impacts on the Organizational Adoption of Cloud Computing: A Reconceptualization of Influencing Factors,” Procedia Technology, vol. 16, pp. 85-93, //, 2014.
- S. Alismaili, M. Li, J. Shen, and Q. He, “A Multi Perspective Approach for Understanding the Determinants of Cloud Computing Adoption among Australian SMEs,” arXiv preprint arXiv:1606.00745, 2016.
- C. Low, Y. Chen, and M. Wu, “Understanding the determinants of cloud computing adoption,” Industrial Management & Data Systems, vol. 111, no. 7, pp. 1006-1023, 2011.
- H. Gangwar, H. Date, and R. Ramaswamy, “Understanding determinants of cloud computing adoption using an integrated TAM-TOE model,” Journal of Enterprise Information Management, vol. 28, no. 1, pp. 107-130, 2015.
- H. M. Sabi, F.-M. E. Uzoka, K. Langmia, and F. N. Njeh, “Conceptualizing a model for adoption of cloud computing in education,” International Journal of Information Management, vol. 36, no. 2, pp. 183-191, 4//, 2016.
- W.-L. Shiau, and P. Y. K. Chau, “Understanding behavioral intention to use a cloud computing classroom: A multiple model comparison approach,” Information & Management, vol. 53, no. 3, pp. 355-365, 4//, 2016.
- N. Opitz, T. F. Langkau, N. H. Schmidt, and L. M. Kolbe, "Technology Acceptance of Cloud Computing: Empirical Evidence from German IT Departments." pp. 1593-1602.
- C. G. Cegielski, L. A. Jones‐Farmer, Y. Wu, and B. T. Hazen, “Adoption of cloud computing technologies in supply chains: An organizational information processing theory approach,” The International Journal of Logistics Management, vol. 23, no. 2, pp. 184-211, 2012.
- N. Haile, and J. Altmann, “Risk-benefit-mediated impact of determinants on the adoption of cloud federation,” in 19th Pacific Asia Conf on Information Systems, 2015.
- F. Z. Filali, and B. Yagoubi, “Global trust: a trust model for cloud service selection,” International Journal of Computer Network and Information Security, vol. 7, no. 5, pp. 41, 2015.
- J. F. Hair Jr, G. T. M. Hult, C. Ringle, and M. Sarstedt, A primer on partial least squares structural equation modeling (PLS-SEM): Sage Publications, 2016.
- I. H. Bernstein, and J. Nunnally, “Psychometric theory,” New York: McGraw-Hill. Oliva, TA, Oliver, RL, & MacMillan, IC (1992). A catastrophe model for developing service satisfaction strategies. Journal of Marketing, vol. 56, pp. 83-95, 1994.
- J. F. Hair, R. E. Anderson, B. J. Babin, and W. C. Black, Multivariate data analysis: A global perspective: Pearson Upper Saddle River, NJ, 2010.


