Cooperative Medium Access Control Protocol for Mobile Ad-hoc Networks using Spatial Diversity
Автор: Tazeem Ahmad Khan, M T Beg, M A Khan
Журнал: International Journal of Intelligent Systems and Applications(IJISA) @ijisa
Статья в выпуске: 11 vol.5, 2013 года.
Бесплатный доступ
Enhancement the Performance of MANET (Mobile Ad-hoc Network) using spatial diversity. Spatial diversity implemented using cooperative transmission technique in Medium access control (MAC) layer level protocol. In noisy environment limit the network performance like coverage area, limit number of node, degrade packet transmission rate, increase packet loss rate etc. In this paper enhance the source to destination transmission range, minimize the packet loss, improve packet transmission rate and appropriate end to end delay. When direct link is fail to transmit packet then Cooperative scheme help to transmit packet. Cooperative scheme is to help the packet transmission with five handshakes instead of four. This scheme implemented in MANET network on MAC layer protocol. Cooperative scheme improve the performance with help of intermediate node between sources to destination. We are performance analysis using discrete simulator NS-2 in MANET. Our performance based on MAC layer level with cooperative scheme in IEEE WLAN standard CSMA/CA protocol.
802.11, CSMA/CA, NS-2, MAC Layer, MANET
Короткий адрес: https://sciup.org/15010493
IDR: 15010493
Текст научной статьи Cooperative Medium Access Control Protocol for Mobile Ad-hoc Networks using Spatial Diversity
Published Online October 2013 in MECS
In the world most demanded technology is wireless technology. Wireless technology is similar wired technology, the basic difference between wired network and wireless network is lower data link layer (MAC layer) and Physical layer protocol. In wireless network Medium access control protocol CSMA/CA instead of CSMA/CD and token ring, MAC mechanism is control the end to end transmission and reception process, also control performance parameters like throughputs, data loss, packets delivery ratio and share medium. In data transmission process MAC layer with RTS/TCS protocol to reduce collision rate using four way handshakes. In highly noise environment or fading channel condition RTS/CTS protocol less effective or transmission failed, if transmission fail due to atmospheric channel condition or distance, an intermediate nodes cooperate the transmission, it is called Cooperative transmission or cooperative medium access control protocol. Cooperative MAC is used five handshake process to avoid receiver frame decode problem, enhance the packet deliver ratio, throughputs and data loss rate. Cooperative technique based on the diversity technique, it is called spatial diversity. In this technique have a potential to improve the performance of wireless network, also appropriate for broadcast transmission. Our simulation this technique is implemented mobile ad-hoc network to enhance the performance of network [1, 2, 5, 6, 7].
This is hot area of Research cooperative transmission scheme. Researchers aim is enhancement wireless network parameters like throughputs, end to end delay, minimization energy consumption using cooperative scheme. The cooperative scheme is also implemented on physical layer level to improve the performance [11, 12, 13, 15].
This paper is organized as: Section-II Cooperative MAC scheme is help to data transmission using Spatial Diversity, Section-III Simulation and results using NS-2, Section- IV Conclusion of result analysis.
-
II. About the WLAN Cooperative MAC Scheme
Medium Access control is heart of wireless networks, either a centralized control or ad-hoc network. MAC is a lower sub- data link layer. MAC layer and Physical layer specification finalized by recommended committee time to time as amendment or final report IEEE wireless standers [1, 212, 13, 15]. MAC layer base on Contention free and Contention oriented access. Contention free is a distributed channel access mechanism based on Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA). CSMA/CA channel contention mechanism can also used with Request to send / Clear to Send (RTS/CTS) mechanism. The hidden node problem solved using RTS/CTS operation. DCF used different frame space DIFS, IFS, SIFS for transmission a frame. Time space depends on the channel condition (idle or busy). If the channel is busy, it enters a backoff procedure among contention window [1, 4,5,11, 12, 22].
Function of MAC layer mainly reliable transmission, access mechanism control, and also security [7,8, 9]. Procedure of data transmission and reception, data addressing, data fragmentation, packets formatting is depends on MAC sub-layer. Data link layer are divided upper sub layer logical link control and lower sub medium access control layer. Logical link layer is common line and wireless network. MAC layer receive data packet from logical link layer, send to physical layer [11, 12, 13,].
The cooperative scheme is based on a conventional MAC layer mechanism protocol. In centralized control wireless network is used cooperative scheme as known Coop MAC protocol. In our study is implemented this scheme to standard (IEEE 802.11) mobile wireless network to enhance the performance. In cooperative scheme procedure node transmit a packet, firstly identify cooperation scheme table to know about the rate of transmission, minimum time for one hop or two hop transmission via helper (intermediate node) and at instant select the appropriate helper. Instant selected helper received the packet from transmitting node at rate R 1 and send to the destination node at rate R 2 . Destination node is sending acknowledge to receiver node after successful reception. Cooperative scheme is extended form five-way handshake mechanism instead of four- way handshake using RTS-CTS to exchange data. When source node transmit need help to helper for transmission, it similar procedure as traditional RTS-CTS. The helper and destination node are send the message to transmitter node to use cooperative scheme. The helper node is idle, then helper inform a helperready to send, when it receive RTS [5, 6, 7].
Cooperative scheme is also enhance control schedule, all the helpers to contain required information in the cooperative scheme table. Appropriate MAC address is indexed in the table, one of them selected as a helper. The 3rd and 4th field in the table source and Destination table is store the information related helper. The cooperative scheme implemented to Mobile Ad-hoc Network is not similar as conventional wireless network. It is used cooperative diversity. MAC layer operation response time is better as compare to conventional MAC layer and information easily access from physical layer [5, 20, 23].
When a node has M bytes data send to another node, first check the table and find all helper to transmission time and select minimum time transmission helper. Total transmission time is source-to-helper and helper-to-destination. If source-to-helper at rate Ra 1 and helper-to-destination Ra 2 then total transmission time is
8*W
T о t a I tr arts m is s i о n ti m e --1-- (1)
Rai Ra2
If source-to-destination at rate Ra, transmission time 8*W/Ra, then we want to transmission time less than 8*W/Ra.
8 *W 8*W + <
Rai Ra2
8 *W
Ra
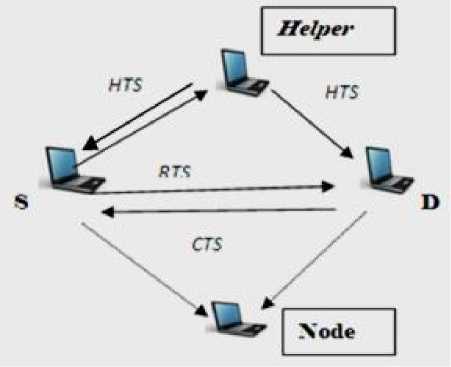
Fig. 1: Cooperative scheme of control packet Exchange technique
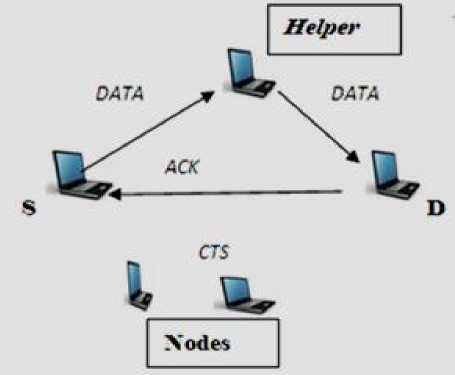
Fig. 2: Cooperative scheme of data and exchange technique ACK packet
Cooperative scheme procedure is show in the Figure 1 and Figure 2 In the figure1.shows control packet exchange procedure, when source node send a control packet RTS and helper received RTS, then helper reply helper-ready-to-send to source and destination. In Figure 2 show data and acknowledge packet exchange procedure, when source node send a data packet via helper to destination, then destination acknowledge directly to source node after successful received packet [5, 6,7,13, 20, 21].
-
III. Simulation and Performance Evaluation
The cooperative scheme implemented and in mobile ad-hoc network by mean of NS-2 simulator. A network model for MANET show in Figure 3 it consist of 7 nodes, all nodes are mobile except source node. The movement of node for 40 sec is defining as follow:
$ns at 0.0 "$node_(0) setdest 100.0 100.0 500.0" $ns at 0.0 "$node_(1) setdest 150.0 250.0 500.0" $ns at 0.0 "$node_(2) setdest 300.0 300.0 500.0" $ns at 0.0 "$node_(3) setdest 500.0 300.0 500.0" $ns at 0.0 "$node_(4) setdest 400.0 300.0 500.0" $ns at 0.0 "$node_(5) setdest 100.0 400.0 500.0" $ns at 0.0 "$node_(6) setdest 600.0 150.0 500.0" $ns at 1.0 "$node_(1) setdest 050.0 250.0 500.0" $ns at 1.0 "$node_(2) setdest 200.0 250.0 500.0" $ns at 6.0 "$node_(2) setdest 300.0 300.0 500.0" $ns at 3.0 "$node_(4) setdest 500.0 250.0 500.0" $ns at 1.0 "$node_(5) setdest 200.0 400.0 500.0" $ns at 3.0 "$node_(5) setdest 400.0 300.0 500.0" $ns at 5.0 "$node_(5) setdest 350.0 150.0 500.0" $ns at 6.0 "$node_(5) setdest 250.0 150.0 500.0" $ns at 7.0 "$node_(5) setdest 250.0 100.0 500.0" $ns at 8.0 "$node_(5) setdest 100.0 400.0 500.0" $ns at 4.0 "$node_(6) setdest 500.0 100.0 500.0" ………………..continue to 40 sec.
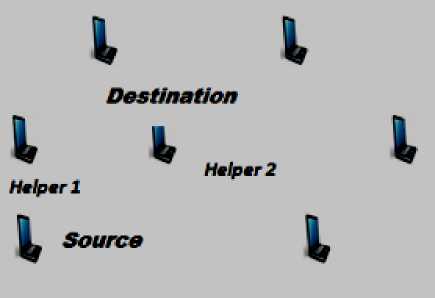
Fig. 3: Network model of Mobile Ad-hoc Network
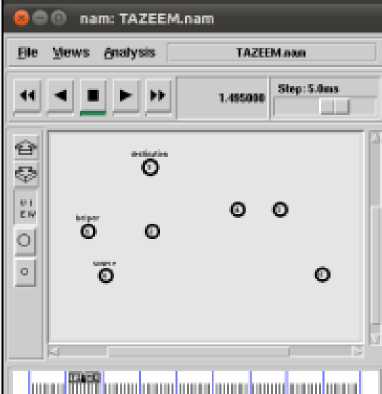
(a) Node 0 to 5 with helper Node 1
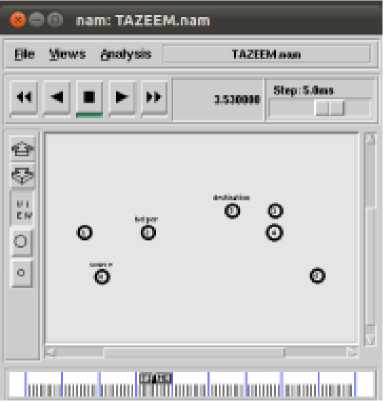
(b) Node 0 to 5 with helper Node 2
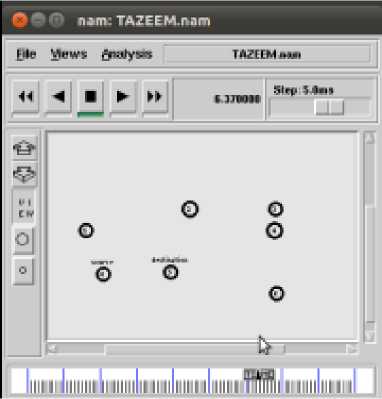
(c) Node 0 to 5 with direct transmission
Fig. 4: The cooperation is initiated when the potential cooperative link can satisfy the target data rate which the direct link cannot satisfy. Therefore, it will be automatically connect appropriate helper
$err set rate_ 0.05, .10 and 0.15
Our experiment conduct is based on a standard 802. 11g mobile ad-hoc network and set the simulation parameters. MAC layer are set payload 2500 and 2000 bytes, RTS 37bytes, CTS 31 bytes. Physical layer are set basic rate 6Mbps, data rate 802.11g standard, acknowledgement 31 bytes. We are use recently added module MAC layer and Physical layer in NS-2 simulator, which is supported cooperative scheme to enhance the performance of mobile Ad-hoc network using five handshake. Our experiment some modification in the files as signal-to interference –noise ratio, monitoring in respect to power. Format parameters in MAC and physical protocol listed in table 1.
Table 1: Simulation Parameters
|
No of nodes |
07 |
|
Slot time |
9us |
|
CCA time |
3us |
|
SIFS |
16us |
|
DIFS |
28us |
|
Preamble Length |
96 bit |
|
PLCP Header Length |
40 bit |
|
PLCP Data Rate |
6 Mbps |
|
Max Propagation Delay |
5us |
|
Short Retry Limit |
7 |
|
Long Retry Limit |
4 |
|
Header Duration |
40us |
|
Symbol Duration |
8us |
|
RTS Threshold |
2346 |
|
CW Min |
15 |
|
CW Max |
1023 |
|
Rx Tx Turn around Time |
2us |
|
Data Rate |
54 Mbps |
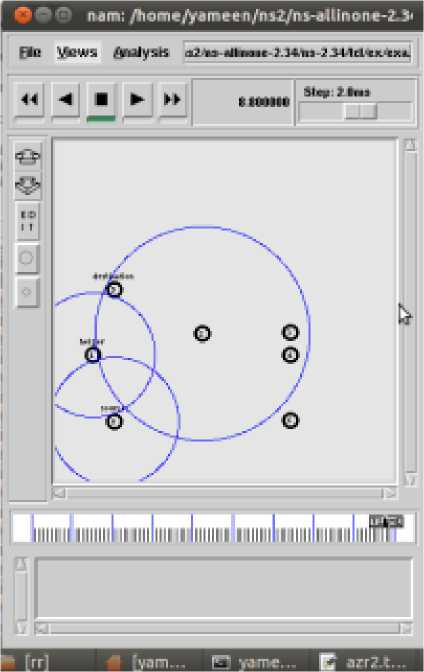
(a) Node 0 to 5 with helper Node 1
We simulate the purposed scheme as per given parameters, Figiure4 shows NS-NAM Screen shot cooperative scheme.
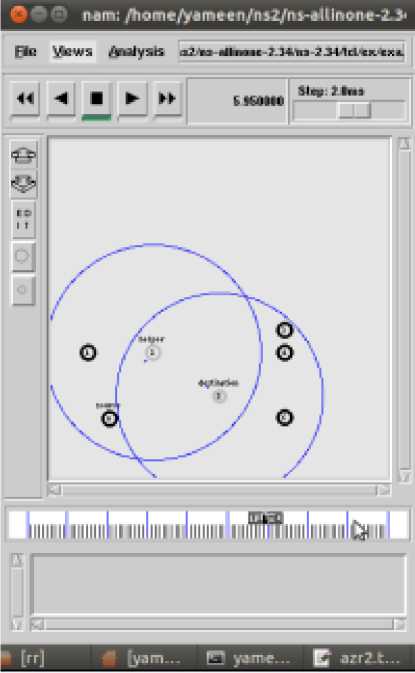
(b) Node 0 to 5 with helper Node 2
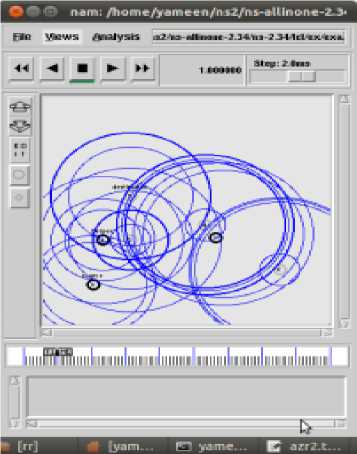
(c) Node 0 to 5 with direct transmission
End-to-End Delay for Diffrent
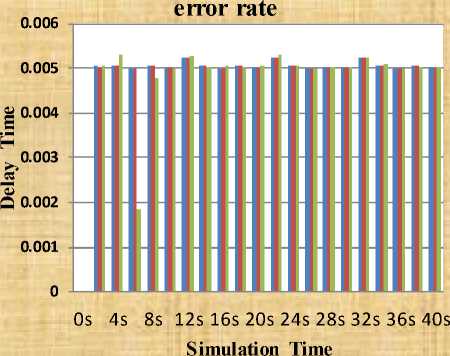
Table 2: End-To-End Delay for Different Error Rate
|
Simulation Time |
E-T-E_ delay=5% error_rate |
E-T-E_ delay=10% error_rate |
E-T-E_ delay=15% error_rate |
|
0s |
0 |
0 |
0 |
|
2s |
0.0050803 |
0.005040555 |
0.00505366 |
|
4s |
0.0050648 |
0.005051855 |
0.00531692 |
|
6s |
0.0049973 |
0.004998888 |
0.00185388 |
|
8s |
0.0050645 |
0.005061663 |
0.00479468 |
|
10s |
0.0049989 |
0.005014699 |
0.00500013 |
|
12s |
0.0052526 |
0.00525175 |
0.00527779 |
|
14s |
0.0050785 |
0.005068383 |
0.00503774 |
|
16s |
0.0049996 |
0.004997165 |
0.00504957 |
|
18s |
0.0050587 |
0.005046725 |
0.00502494 |
|
20s |
0.0050261 |
0.005039693 |
0.00505276 |
|
22s |
0.0052501 |
0.005251201 |
0.00530739 |
|
24s |
0.0050508 |
0.005049315 |
0.00504703 |
|
26s |
0.0050028 |
0.005001313 |
0.00500554 |
|
28s |
0.0050349 |
0.005036436 |
0.00503213 |
|
30s |
0.0050262 |
0.005039517 |
0.00503757 |
|
32s |
0.00524 |
0.00523915 |
0.00523743 |
|
34s |
0.0050662 |
0.005052313 |
0.00510202 |
|
36s |
0.0049975 |
0.004999981 |
0.00500152 |
|
38s |
0.0050462 |
0.00504563 |
0.00503489 |
|
40s |
0.0050392 |
0.005041054 |
0.00502807 |
-
3.1 End-to-End Delay
-
■ E-T-E_delay=5% error_rate
-
■ E-T-E_delay=10% error_rate
E-T-E_delay=15% error_rate
Fig. 5: Performance of mobile ad-hoc network using cooperative scheme in the form of end to end delay for different error rate
Table 3: End-To-End Delay for Different Packet Size
|
Simulation Time |
E-T-E_ delay=Packet_ size-2500 Bytes |
E-T-E_ delay=Packet_ size-2000 Bytes |
|
0s |
0 |
0 |
|
2s |
0.0050803 |
0.005054403 |
|
4s |
0.0050648 |
0.005037466 |
|
6s |
0.0049973 |
0.005001093 |
|
8s |
0.0050645 |
0.005035724 |
|
10s |
0.0049989 |
0.005053049 |
|
12s |
0.0052526 |
0.005251718 |
|
14s |
0.0050785 |
0.005037416 |
|
16s |
0.0049996 |
0.00499991 |
|
18s |
0.0050587 |
0.005049728 |
|
20s |
0.0050261 |
0.005052642 |
|
22s |
0.0052501 |
0.005249865 |
|
24s |
0.0050508 |
0.00503926 |
|
26s |
0.0050028 |
0.005002726 |
|
28s |
0.0050349 |
0.005032421 |
|
30s |
0.0050262 |
0.005027577 |
|
32s |
0.00524 |
0.00523768 |
|
34s |
0.0050662 |
0.005037602 |
|
36s |
0.0049975 |
0.005000022 |
|
38s |
0.0050462 |
0.0050366 |
|
40s |
0.0050392 |
0.005026532 |
End-to-End Delay for Diffrent Packet Size
■ E-T-E_delay=Packet_size-2500 Bytes
■ E-T-E_delay=Packet_size-2000 Bytes
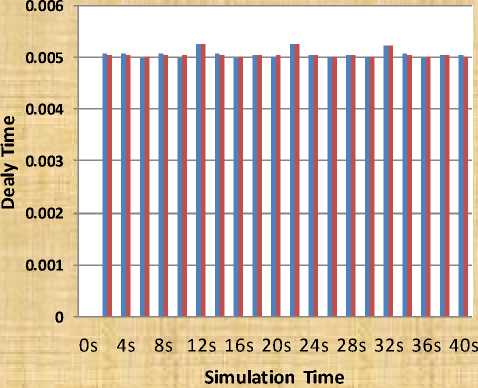
Fig. 6: Performance of mobile ad-hoc network using cooperative scheme in the form of end to end delay for different Packet Size
-
3.2 Packet Loss Ratio
Packet losss Ratio for Diffrent error rate
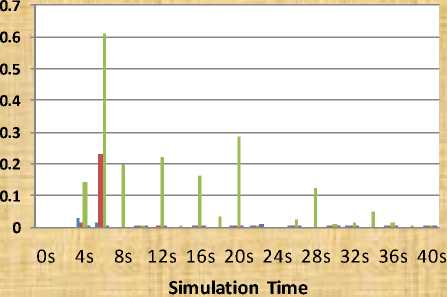
Table 4: Packet Loss Ratio for Different Error Rate
|
Simulation Time |
loss_ratio1 =5% error_rate |
loss_ratio2 =10% error_rate |
loss_ratio3 =15% error_rate |
|
0s |
0 |
0 |
0 |
|
2s |
0 |
0 |
0 |
|
4s |
0.0320197 |
0.017369727 |
0.1425486 |
|
6s |
0.0174564 |
0.231067961 |
0.61149653 |
|
8s |
0 |
0 |
0.19656357 |
|
10s |
0.0031486 |
0.003140704 |
0.00764818 |
|
12s |
0 |
0.000508388 |
0.22231172 |
|
14s |
0 |
0 |
0.00257069 |
|
16s |
0.0032538 |
0.00288913 |
0.16178304 |
|
18s |
0 |
0 |
0.03331218 |
|
20s |
0.0014057 |
0.00112328 |
0.28715107 |
|
22s |
0.0027912 |
0.005309735 |
0.00233402 |
|
24s |
0 |
0 |
0 |
|
26s |
0.0027432 |
0.001477729 |
0.02372379 |
|
28s |
0 |
0 |
0.12421053 |
|
30s |
0.0005429 |
0.000542495 |
0.01264895 |
|
32s |
0.0003388 |
0.001015057 |
0.01672355 |
|
34s |
0 |
0 |
0.04894241 |
|
36s |
0.000746 |
0.00059657 |
0.01492762 |
|
38s |
0 |
0 |
0.0061755 |
|
40s |
0.0005335 |
0.000533262 |
0.00054645 |
-
■ loss_ratio1=5% error_rate
-
■ loss_ratio2=10% error_rate
-
■ loss_ratio3=15% error_rate
Fig. 7: Performance of mobile ad-hoc network using cooperative scheme in the form of packet loss ratio for different error rate
Table 5: Packet Loss Ratio for Different Packet Size
|
Simulation Time |
loss_ratio= Packet size-2500 Bytes |
loss_ratio= Packet size-2000 Bytes |
|
0s |
0 |
0 |
|
2s |
0 |
0 |
|
4s |
0.0320197 |
0.0075 |
|
6s |
0.0174564 |
0.0075 |
|
8s |
0 |
0 |
|
10s |
0.0031486 |
0.001882058 |
|
12s |
0 |
0.004052685 |
|
14s |
0 |
0 |
|
16s |
0.0032538 |
0.001805706 |
|
18s |
0 |
0 |
|
20s |
0.0014057 |
0.001122334 |
|
22s |
0.0027912 |
0.008060453 |
|
24s |
0 |
0 |
|
26s |
0.0027432 |
0.000633179 |
|
28s |
0 |
0 |
|
30s |
0.0005429 |
0.000542005 |
|
32s |
0.0003388 |
0.000338238 |
|
34s |
0 |
0 |
|
36s |
0.000746 |
0.000893655 |
|
38s |
0 |
0 |
|
40s |
0.0005335 |
0.000532765 |
Loss Packets Ratio for Diffrent Packet Size
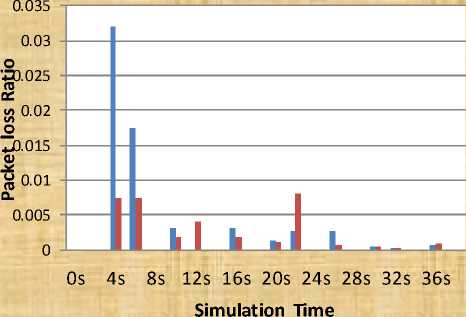
Table 6: Packets Deliver Vs Received Packets For Different Packet Size
|
Simulation Time |
Received Packets= Packet_size-2500 Bytes |
Received_ packets= Packet_size-2000 Bytes |
Expected _packets |
|
0s |
0 |
0 |
0 |
|
2s |
393 |
397 |
400 |
|
4s |
788 |
794 |
800 |
|
6s |
1188 |
1194 |
1200 |
|
8s |
1583 |
1591 |
1600 |
|
10s |
1963 |
1966 |
1980 |
|
12s |
2363 |
2366 |
2380 |
|
14s |
2757 |
2764 |
2780 |
|
16s |
3157 |
3164 |
3180 |
|
18s |
3552 |
3560 |
3580 |
|
20s |
3930 |
3938 |
3960 |
|
22s |
4330 |
4338 |
4360 |
|
24s |
4726 |
4735 |
4760 |
|
26s |
5126 |
5135 |
5160 |
|
28s |
5523 |
5532 |
5560 |
|
30s |
5902 |
5911 |
5941 |
|
32s |
6302 |
6311 |
6341 |
|
34s |
6697 |
6708 |
6741 |
|
36s |
7097 |
7108 |
7141 |
|
38s |
7493 |
7504 |
7541 |
|
40s |
7890 |
7902 |
7941 |
■ loss_ratio=Packet_size-2500 Bytes
■ loss_ratio=Packet_size-2000 Bytes
Fig. 8: Performance of mobile ad-hoc network using cooperative scheme in the form of packet Loss ratio for different Packet Size
-
3.3 Packets Deliver vs. Received Packets
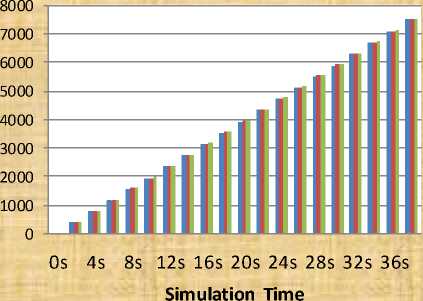
We conduct cooperative scheme experiment to analysis Packets Deliver vs. Received Packets for different packet size in mobile ad-hoc networks. The effect of packet size shown in Table VI or in Figure 9 for employed Packet size 2500 & 2000 bytes respectively in terms of Packets Deliver vs. Received Packets.
Receive Packets vs. Expected Packets
-
■ Received Packets=Packet_size-2500 Bytes
-
■ Received_packets=Packet_size-2000 Bytes
-
■ Expected_packets
Fig. 9: Performance of mobile ad-hoc network using cooperative scheme in the form of receive packet s for different packet size vs. expected packets
-
IV. Conclusion
Список литературы Cooperative Medium Access Control Protocol for Mobile Ad-hoc Networks using Spatial Diversity
- Sathya Narayanan-Thanasis Korakis Pei Liu, Zhifeng Tao and Shivendra S. Panwar. “CoopMAC: A coopera tive MAC for Wireless LANs.” IEEE Journal on Selected Are as In Communications, 25(2):340–354, February 2007.
- S. Moh, C. Yu, A Cooperative Diversity-Based Robust MAC Protocol in Wireless Ad Hoc Networks, IEEE Trans. Parallel and distributed system, vol. 22, no. 3, Mar. 2011, pp. 353-363.
- A. Sendonaris, E. Erkip and B. Aa zhang, User cooperation diversity-part I: System description, IEEE Transactions on Communications, vol. 51, no. 11, Nov. 2003, pp. 1927-1938.
- J. N. Laneman and G. W. Wornell, Distributed space–time coded protocols for exploiting cooperative diversity in wireless networks, IEEE Transactions on Information Theory, vol. 49, no. 10, Oct. 2003, pp. 2415-2525.
- J. N. Laneman, D. N. C. Tse, and G.W.Wornell, Cooperative diversity in wireless networks: Efficient protocols and outage behavior, IEEE Transactions on Information Theory, vol. 51, no. 12, Dec. 2004, pp. 3062–3080.
- H. Zhu and G. Cao, rDCF: A relay-enabled medium access control protocol for wireless ad hoc networks, Proc.of IEEE INFOCOM, vol. 1, Miami, USA, 2005, pp. 12-22.
- R. Ahlswede, N. Cai, S. R. Li, and R. W. Yeung, Network Information Flow, IEEE Transactions on Information Theory, 2003, pp. 371-381
- A. S. Ibrahim, Z. Han, and K. J. R. Liu, Distributed energy-efficient cooperative routing in wireless networks, IEEE Transactions on Communications, vol. 7, no. 10, Oct. 2008, pp. 3930–3941.
- J. Jang, A study on a cooperative MAC protocol at ad hoc networks, KIMICS, vol. 13, no. 8, Aug. 2009, pp. 1561- 1570.
- J. Jang, A study on a network coding enabled cooperative MAC protocol at ad hoc networks, KIMICS, vol. 13, no. 9, Sep. 2009, pp. 1819-1828.
- S. Moh, C. Yu, A Cooperative Diversity-Based Robust MAC Protocol in Wireless Ad Hoc Networks, IEEE Trans. Parallel and distributed system, vol. 22, no. 3, Mar. 2011, pp. 353-363.
- S. Vijay Bhanu,R. M. Chandrasekaran,"Voice Call Capacity Analysis and Enhancement of IEEE 802.11 WLAN" European Journal of Scientific Research ISSN 1450-216X Vol.76 No.2, 2012, pp.271-280
- IEEE Std. 802.11-1999, Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) specifications, 1999.
- IEEE Std. 802.11b-1999, Part 11: Wireless LAN Medium Access control (MAC) and Physical Layer (PHY) specifications: High-Speed Physical Layer Extension in the 2.4GHz Band, 1999.
- Y. Yuan, B. Zheng, W. Lin and C. Dai, An opportunistic cooperative mac protocol based on cross-layer design, 2007 International Symposium on Intelligent Signal Processing and Communications Systems, ISPACS 2007 - Proceedings, 2008, pp. 714-717.
- A. Azgin, Y. Altunbasak, and G. AlRegib, Cooperative MAC and Routing Protocols for Wireless Ad Hoc Networks, Proc. of IEEE GLOBECOM, 2005, pp. 2854-2859.
- P. Liu, Z. Tao, and S. Panwar, A cooperative MAC protocol for wireless local area networks, Proc. of IEEE ICC, vol. 5, Seoul, Korea, 2005, pp. 2962-2968.
- N. Li, N. Cheng, Y. Cai and X. Xu, Performance Analysis of a Cooperative MAC Based on Opportunistic Relaying for Ad Hoc Networks, 2010 International Conference on Wireless Communications and Signal Processing, Oct. 2010, pp. 1-6.
- Bletsas A., Khisti A., Reed D. P., A simple distributed method for relay selection in cooperative diversity wireless networks, based on reciprocity and channel measurements, IEEE 61st Vehicular Technology Conference, VTC 2005-Spring, vol. 3, Dec. 2005, pp. 1484-1488.
- T. Korakis, Z. Tao, Y. Slutskiy and S. Panwar, A Cooperative MAC protocol for Ad Hoc Wireless Networks, Fifth Annual IEEE International Conference on Pervasive Computing and Communications Workshops, May 2007, pp. 532-536.
- M A Khan, T A Khan, M T Beg, “Performance Optimization of MAC Layer IEEE802.11 WLAN using Fragmentation” VSRD International Journal of Electrical, Electronics & Communication Engineering”, VSRD IJEECE, Dec 2012 , pp 916-920
- T A Khan, M T Beg, M A Khan, “Evaluation of Back-off Algorithm performance of MAC layer IEEE 802.11WLAN” International Journal of Engineering and Management Sciences, IJEMS, ISSN 2229-600x, April’ 2013
- T A Khan, M T Beg, M A Khan, “Performance Analysis of WLAN using OPNET” International Journal of Innovative Technology and Exploring Engineering, IJITEE, Vol 2, Issue 5, April 2013, ISSN 2278-2375,PP 1-4
- G. Berger-Sabbatel M. Heusse, F. Rousseau and A. Duda. “Performance anomaly of 802.11b” In Proc. of IEEE INFOCOM, San Francisco, USA,March-April 2003.
- The ns Manual (formerly ns Notes Documentation) The VINT Project A collaboration between research at UC Berkeley, LBL, USC/ISI, and Xerox PARC Kevin Fall, and Kannan Varadha, January 6, 2009 http://www.slideshare.net/code453/ns2-manual
- NS Mannual, http://www.isi.edu/nsnam/ns


