Electronic police ambush system via vehicles/drivers safety authentication system
Автор: Hussam Elbehiery
Журнал: International Journal of Information Technology and Computer Science @ijitcs
Статья в выпуске: 9 Vol. 10, 2018 года.
Бесплатный доступ
The suggested system aims to develop the level of security for the Egyptian police ambushes and to decrease the overcrowding because the traditional police ambushes was depressing in the last decade in Egypt due to the actions of terrorism and the threatening of our nation security, which was causing a waste of human casualties and will decrease the income of the tourism and reputation of our nations. The direct interaction with the vehicles inside the police ambushes may cause an unnecessary overcrowding. The introduced system try to minimize the human element in the police ambush through utilizing RFID technology by specifying an RFID card for each vehicle and vehicle driver which will be like the electronic passport at the RFID Sensing check point before the ambush. After checking for the information saved on the RFID card supposed inside the vehicle and also registered previously on the system server results in giving the vehicle the “PASS” signal or “ARRESSTED” signal which required a capture photo shot for the vehicle. So that system aims to increase the security level and reduce casualties of police ambushes anywhere even if it is fixed or non-fixed.
Ambush, Arduino, Authentication and RFID
Короткий адрес: https://sciup.org/15016295
IDR: 15016295 | DOI: 10.5815/ijitcs.2018.09.04
Текст научной статьи Electronic police ambush system via vehicles/drivers safety authentication system
Published Online September 2018 in MECS DOI: 10.5815/ijitcs.2018.09.04
The problems in the licenses, the weakness of ambushes and points of concentration also the violence in recent times against ambushes even if military or police, which results in losing of many souls become an urgent cause to be solved by the new technology. The direct interaction between the policemen or the military persons was the most vulnerable point in the police ambush which makes it an easy target for terrorist attacks. Sometimes the attacks are camouflaged in civilian cars and it is unable to distinguish from a safe distance whether or not that vehicle was stolen or even do not have any documents, then the camouflaged terrorist vehicle must approach the ambush which may put the life of the humans in danger given them no chance tell from a safe distance whether or not the vehicle coming from far away is truly a civilian vehicle or a terrorist vehicle.
The vehicle may be stolen or unlicensed if you do not go to check and renew the license or the vehicle owner is required in any process. All of this important information will be registered in the database and also at the Ministry of the Interior system server [4]. As well as the electronic gates located at any ambush. The suggested system designed two gates, if the commander of the vehicle reports of stolen his/her vehicle, or the driver's license has expired or the car license, the electronic “Arresting Gate” will be opened and if the commander of the vehicle and his/her vehicle has no traffic violation, the electronic “Pass Gate” will be opened.
Authentication is a process in which the credentials provided are compared to those on file in a database of authorized users’ information on a local operating system or within an authentication server. If the credentials match, the process is completed and the user is granted authorization for access [7]. The permissions and folders returned define both the environment the user sees and the way he can interact with it. Driver authentication system and safety system and a way to monitor and control the use of vehicles by high-risk drivers. A central database that includes a software application can be accessed by an authorized user [5].
It is taken into account the different rules of traffic law during the design stage of that suggested system which include the basic rules of safety that guarantee the safety of the individual and the community and contribute significantly to stopping the bleeding of asphalt that has increased in recent years. The main reason for that is the lack of commitment by drivers to the global rules of traffic. The government's binding rules and the tightening of penalties to reduce accidents, was the new Traffic Law 2018 is the way to achieve this.
-
II. Related Works
There are two kinds of traffic and security ambushes, and these ambushes are carried out by security personnel from the army and the police. There are ambushes by the military police and these ambushes belong to members of the armed forces and they check the license of the individuals and large vehicles (transport).
-
A. PDA Detector Device
The officer uses it during traffic campaigns. The PDA devices have the ability to detect cars, issues traffic tickets and send them immediately after the violation is released to the central database located in the traffic, and then sent to the Traffic Department to take necessary legal action against the violator.
The monitoring system has been developed by adding a new possibility to it. It has become possible to identify the stolen cars that were reported by the owner. The traffic officer will enter the car plate numbers in the device connected to the database of the General Board of Traffic. To inform her driver that the vehicle is being detected. Fig. 1. Shows the PDA Detector Device.

Fig.1. PDA Detector Device
-
B. Traffic violations Monitor Car
However, the General Board of executives of Traffic has recently adopted modern methods of monitoring traffic violations on the highways. A large number of highways and desert roads have been supplied with monitoring vehicles. According to the new traffic law, but has not yet activated in cities. A car to monitor traffic violations on the road have modern techniques to control of violators rules and traffic etiquette and metal paintings of stolen cars, to eliminate the human element in the monitoring of violations.
These cars have the characteristic of monitoring traffic violations by providing front and rear cameras at the top of the car filming the vehicles violating while driving on the roads from all directions to show all the data of those cars violating and there are screens monitors violations and equipped with a radar. The internal screens in the traffic car have a feature to monitor the violations by the presence of colors to show the quality of the violation, including their color of stolen cars and green color of the expiration of the license and in the absence of any colors for the car is non-violation and show all the data of cars.
-
C. Police Car
These cars are used in ambush police (security wagons), cars equipped with a device connected to the battalion officer writes the name of the citizen or the national number and through the device in the car recognizes the officer if this citizen has the any records or not. It is equipped with newest technologies, communication equipment and connectivity, and is supported by CCTV and ANPR cameras to monitor and document the security situation on the roads and main axes, to identify car numbers and to identify the stolen plates. The vehicle is equipped with a SCOUT-APP device that deals with the camera system, has the property of locating cars, equipped with a system to transfer data from the vehicle to the electronic accounts located in its sections wirelessly, and link it to the operations room of the Public Security Department.
The car is equipped with surveillance cameras can pick up all the numbers of cars passing by, and within a few seconds show an indication to indicate whether this car amount stolen and registered or not, so it is difficult for thieves to get out of cars stolen on the main roads.
-
III. Recent system Problems and Obstacles
-
A. Overcrowding, Slow and waste time
Because of the existence of large numbers of vehicles in most streets for the main cities of Egypt it is hard for a traditional police ambushes to check for every vehicle papers without creating a severe overcrowding especially in the main streets. Also, because of overcrowding and the existence of traditional police ambushes that does not work with an efficient speed, there is a waste time for vehicle pass results in a slow in vehicle motion.
-
B. Lack of Security
Because of the direct interaction between the police ambushes and the civilian vehicles there will be a percentage of terrorist actions.
-
IV. Suggested System Aims and Structure
Vehicle owners should have an RFID card (Tag) that will point to the vehicle detailed description in the database [4]. While the embedded system (Arduino) will establish the related system features such as the digital camera and sensors to save much more time and quite solve the overcrowding problem and lack of security problem. That results in establishing an integrated system for police ambushes that could fit the Egyptian current state of crowding and the lake of security in some places and that utilize technologies with smaller cost and fewer risks [10,14]. The suggested system is designed to make use of the unique features of Arduino; Dynamic updating, Accessibility, and Security. So the proposed system will utilize:
-
• Vehicles will be handled quickly in any police ambush.
-
• Removing the overcrowding made by vehicles results in saving time.
-
• Trying to improve efficiency of the police ambushes.
-
• Speed up the checking of vehicle’s documents process electronically.
-
• Design a system that minimizes direct interaction and checking vehicles in safe and secured distances which results in reducing casualties of terrorist attacks.
-
V. Suggested System Design
The introduced system will be suitable to be applied in all inlets and outlets of ring roads. Also the introduced system could be practically applied at the intersections of the master roads and streets. Traffic lights will play a significant role to organize all processes before and after the suggested ambush. Fig. 2 introduced the suggested design of the ambush. Whenever the vehicle passes the check point before the real ambush, the program starts by scanning the RFID card for each vehicle. If the vehicle has not any traffic violations, “Gate A” will be opened and the vehicle passed through it. If the vehicle has any traffic violations, the “Gate B” will be opened and the vehicle passed through it and the camera take a snap shot capture for that vehicle. Fig. 3 explains via the suggested system flowchart for all operations should be verified [8].
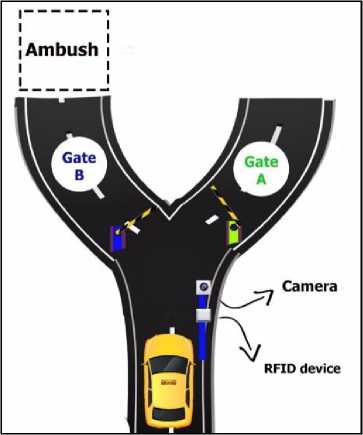
Fig.2. Suggested design of the ambush
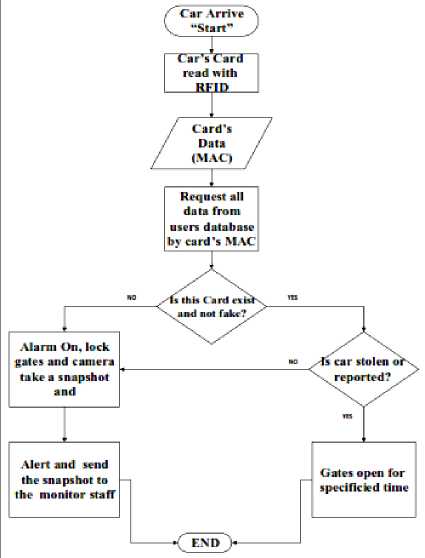
Fig.3. Suggested system Flowchart
Fig. 4 and fig. 5 show the Use Case Diagram and Data Flow Diagram (DFD) for the suggested design for the electronic police ambush. As a result, it makes it easier for programmers and software architects to communicate [1, 2].
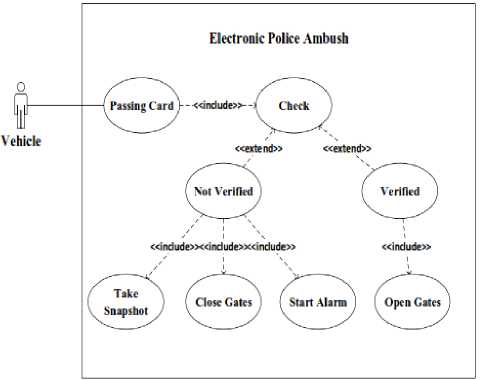
Fig.4. Suggested system Use Case Diagram
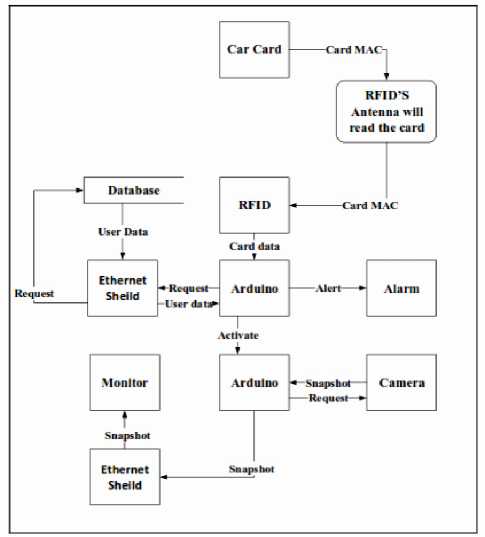
Fig.5. Suggested system Data Flow Diagram
-
VI. System Hardware Design
Arduino is an open-source platform used for building electronics projects. Arduino consists of both a physical programmable circuit board (often referred to as a microcontroller) and a piece of software, or IDE (Integrated Development Environment) that runs on your computer, used to write and upload computer code to the physical board. The Ethernet Shield is mounted on the Arduino UNO this is our Master Arduino UNO and work as one piece. Its job is to take the unique mac address of every RFID card that is specified for each car from the Passive 125 KHz RFID module reader which in turn in takes the mac address from the antenna. Then The Arduino UNO checks the MAC address taken with the MAC addresses that are registered in the local database that exists on the server through the Ethernet Shield that is connected to server through a switch [5, 8]. Fig. 6 explains the electronic circuit connection.
The Arduino checks whether nor that the mac address exists and whether nor the mac address is verified if the mac address matches a mac address that exists on our local database [13]. It is verified the green led turns on if not 3 procedures will occur in the following order:
-
1. It will send a message to the other existent Slave Arduino UNO on I2C Connection which its job will be explained later on.
-
2. It will make red led turns on.
-
3. It will make the buzzer will ring.
Slave Arduino UNO; once it gets the message from the master Arduino on the I2C connection to operate it. This Arduino will order the camera to operate and the camera will do its job by taking and saving a snap shot on the micro SD card that is mounted on this Arduino. It will make the Ethernet shield to work as a server for the pc and to upload to it the snap shot image taken by the camera on the link [11].
An Ethernet controller is an integrated circuit chip that controls Ethernet communications. Ethernet is the method used to communicate with other Ethernet controller. This is also how most computers connect with the Internet, and transfers data to the Ethernet controller, which decodes the data and puts it into a form your computer can use. The Arduino Ethernet shield allows an Arduino board to connect to the internet using the Ethernet library and to read and write an SD card using the SD library [9, 12].
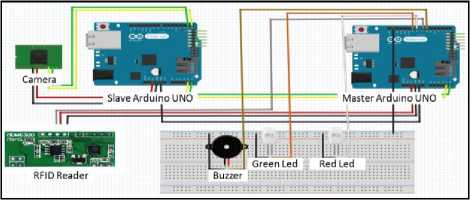
Fig.6. Suggested system electronic circuit connections
Camera will play a mail role in our project because it will take a snap for the driver in case of any error in the system which may be stored locally, transmitted to another location. This camera module can be a pretty neat project addition. It was designed to be used in security systems and achieve two main functions it outputs NTSC video and can take snapshots of that video (in color) and transmit them over the TTL serial link. It can snap pictures at 640x480, 320x240 or 160x120 and they are pre-compressed JPEG images which makes them nice and small and easy to store [6].
Switch is a computer networking device th at connects devices together on a computer network by using packet switching to receive, process, and forward data to the destination device. It connects the local Server, Master Arduino UNO and Slave Arduino UNO by establishing local network between them. Fig. 7 shows the switch used in the suggested system for police ambush [10, 15].

Fig.7. Four ports switch used in suggested system
Buzzer ; it rings in case of any invalid or unregistered mac address appears. Indicator LEDs; Green led to show that the car is authorized to pass. Red led to show that the car is not authorized to pass. All LEDs in lies in the check point for RFID Detection before the real ambush.
-
A. RFID Technology principals
Radio-frequency identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. The tags (cards) contain electronically stored information. Passive tags collect energy from a nearby RFID reader's interrogating radio waves. Active tags have a local power source (such as a battery) and may operate hundreds of meters from the RFID reader. Unlike a barcode, the tag need not be within the line of sight of the reader, so it may be embedded in the tracked object. RFID is one method for Automatic Identification and Data Capture (A IDC). Passive 125KHz RFID module reader; is designed for reading code from 125KHz card compatible read-only tags and read/write card. It can be applied in office/home security, personal identification, access control, anti-forgery, interactive toy and production control systems etc. [8].
The information contained within an RFID tag’s electronic chip depends on its application. It may be a unique identifier (UII, Unique Item Identifier or EPC code, Electronic Product Code, etc.). Once this identifier has been written into the electronic circuit, it can no longer be modified, only read. This principle is called “WORM” W rite O nce R ead M ultiple. Some electronic chips have another memory in which users can write, modify and erase their own data. These memories vary in size from a few bits to tens of kilobits. This capability makes RFID a strong choice for asset tracking. Passive RFID tags have no power. They’re activated by an electromagnetic signal sent from the RFID reader. The signal doesn’t travel as far as active RFID, so they’re used for short read ranges. RFID card with working frequency of 125 KHz, EM4100 standard. It comes with different colors. It works with passive 125 KHz RFID module reader [7, 8].
-
VII. Desktop Application Interface
The program interface contains many section and items. Fig. 8 shows the initial user interface for the suggested system which will be exist in the real ambush. The initial user interface includes many items and sections; each has its own function as next: [3]
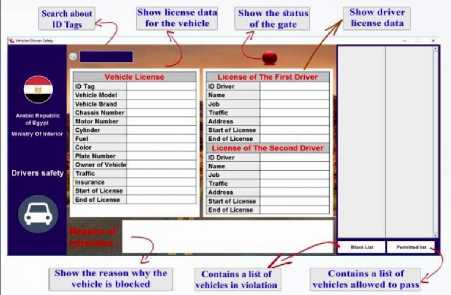
Fig.8. Desktop Application Interface
-
• Search
Search for the number of vehicle ID tag in the program database. That will inform the details about that vehicle and if it has any violations.
-
• Vehicle License
This section includes a table contains all the information about the vehicle license.
-
• Driver License
We have the license information for both drivers of the car.
-
• Reason of Violations
The reason for the vehicle arresting will be displayed on that section. Fig. 9 shows an example for a vehicle test and has a violation to become arrested in ambush.

Fig.9. Section of vehicle violation reasons
-
• Gates
The default lighting in the normal state when there are not any cars in front of the gates is the red light and when a car arrived in front of the gates (Check Point), it will be checked for its validity if it is permitted, the lighting will turn to green light and the permitted gate will opened. On the other hand, if the car is violated, the lighting will turn to blue light. Fig. 10 shows the status of gates on the user interface:
-
■ Red : The states of the two gates are off.
-
■ Green : The state of permitted gate is on.
-
■ Blue : The state of block gate is on.
non
Fig.10. Gates status indicators inside the user interface of the desktop application
-
• Permitted List
The list of vehicles allowed passing, and when the button is pressed, the vehicle and driver data will be displayed.
-
• Block List
The lists of the infringing vehicles are displayed and when the button is pressed, the driver's information and the type of violation that is performed are displayed.
Fig. 11 shows an example of RFID detection in check point and the vehicle has a traffic violation viewed in the desktop application of the suggested system.
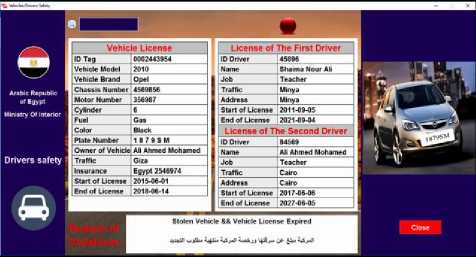
Fig.11. Vehicle has a traffic violation
Fig. 12 shows an example of RFID detection in check point and the vehicle has not the RFID tag so an error message will be pop up on the display for the desktop application of the suggested system.
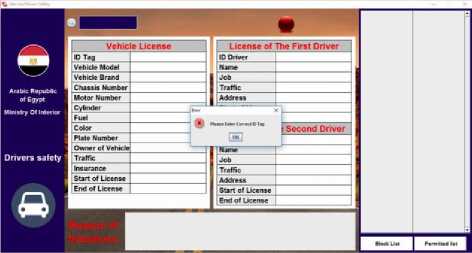
Fig.12. Vehicle has not the RFID tag
VIII. Conclusion
The suggested system introduced, some of the problems facing traffic units in Egypt, ambush safety have been solved. Technological method to manage the vehicles traffic violation especially for the vehicles that attack the ambush of the police or skip the ambush without detection. The main objective for that research was to minimize these problems as much as possible. The most important is to protect humans working in these ambushes and reduce the danger level also helping them in their work electronically to ensure their safety. Electronic devices that depend on the electromagnetic waves of RF which is known as RFID had been used. It is used in the tracking process and it is already used in our daily life in clothing stores and hotels. A desktop application had been set to make it easier for the police officer to use the RFID device easily and without the complexity.
Supposedly, the suggest will be available for all types of roads and streets organized by traffic lights before and after the ambushes and also not affected by the number of vehicles if increased especially in rush hours because it has two way working together. Clearly may be the suggested system rarely affect the flow of vehicles when the number of vehicles is over limit but the advantages is the security factor which is a factor important than the flow speed. Through the introduced application program, the police officer can check the car without exposing the car to the ambush or cause harm to the police officer or army working in this ambush. By checking if there are any traffic violations of the vehicle from a distance far from the ambush (Stolen - expiration of the driving license - expiration of the vehicle license) and sending the reason for arresting to the officer in charge of the ambush and sending an image of the driver for the vehicle if the vehicle is stolen.
Recently the author prepared a technical proposal description for that suggested system to Ministry of Interior, Traffic department research center to evaluate practically that suggested system which they accepted technically before.
Acknowledgement
This research was supported by Ahram Canadian University ( ACU ). I would like to thank my colleagues from Faculty o f Computer Science and Information Technology who provided insight and expertise that greatly assisted the research.
Список литературы Electronic police ambush system via vehicles/drivers safety authentication system
- Y. Daniel Liang, “Introduction to java programming: Brief Version,” 10th Edition, ISBN-10: 0133592200, ISBN-13: 978-0133592207, Pearson, USA, January 7, 2014.
- Oracle Fusion Middleware 11g: Java Programming,” Volume I, Student Guide Student Guide (Edition 1.1), Kate Heap, USA, May 2009.
- C. Thomas Wu, “An Introduction to Object-Oriented Programming With Java™,” 5th Edition, ISBN-10: 0073523305, ISBN-13: 978-0073523309, McGraw-Hill Education; USA, March 24, 2009.
- Ramez Elmasri and Shamkant B. Navathe, “Fundamentals of Database Systems,” 7th Edition, ISBN-10: 0133970779, ISBN-13: 978-0133970777, Pearson; USA, June 18, 2015.
- Carlos Coronel, Steven Morris, Peter Rob, “Database Systems: Design, Implementation and Management,” ISBN-10: 0538748842, ISBN-13: 978-0538748841, Cengage Learning; 9th Edition, UK, November 23, 2009.
- Technology Solutions UK Ltd, Suite A, Loughborough Technology Centre, Epinal Way, Loughborough, Leicestershire, LE11 3GE, UK. https://www.tsl.com/
- Makwana Foram R. , Rahul R. Menon , Patel Harsh K., “Automobile Driver Authentication system using Electronic Driving License,” International Journal of Innovative Research in Computer and Communication Engineering, Vol. 4, Issue 2, ISSN(Online): 2320-9801 ISSN (Print) : 2320-9798, India, February 2016,
- Min Chen, Sergio Gonzalez, Victor Leung, Qian Zhang, and Ming Li, “A 2G-RFID-based E-healthcare system,” IEEE wireless communications, pp. (1536-1284), USA, February 2010.
- Zeinab Kamal Aldein Mohammeda , Elmustafa Sayed Ali Ahmedb, “Internet of Things Applications, Challenges and Related Future Technologies,” World Scientific News (WSN) 67(2) 126-148, EISSN 2392-2192, Poland, 2017.
- Martin Evans, Joshua Noble, Jordan Hochenbaum and Mark Sproul, “Arduino in Action,” Manning Publications Company, Paperback, ISBN-10: 1617290246, ISBN-13: 9781617290244, eBay Product ID (ePID): 112138228, Waukegan, Illinois, USA, 2013.
- Richard Blum, “Arduino Programming in 24 Hours, Sams Teach Yourself,” 1st Edition, ISBN-10: 0672337126, ISBN-13: 978-0672337123, Indianapolis, Indiana, USA, August 31, 2014.
- Michael Miller, “The Internet of Things,” Pearson, Que Publishing, ISBN: 0-7897-5400-2, USA, March 2015.
- Ramez Elmasri, and Shamkant B. Navathe, “Fundamentals of database systems,” 6th Edition, ISBN: 0136086209 9780136086208, Addison-Wesley Publishing Company, USA, ©2010,
- Joseph Valacich, Joey George, “Modern Systems Analysis and Design,”8th Edition, Pearson; ISBN-10: 0134204921, ISBN-13: 978-0134204925, USA, January 17, 2016.
- James Kurose, Keith Ross, “Computer Networking: A Top-Down Approach,” 7th Edition, Pearson; ISBN-10: 0133594149, ISBN-13: 978-0133594140, USA, May 6, 2016.


