Fuzzy Logic Based Trusted Candidate Selection for Stable Multipath Routing
Автор: Sujata V. Mallapur, Siddarama R Patil
Журнал: International Journal of Information Technology and Computer Science(IJITCS) @ijitcs
Статья в выпуске: 6 Vol. 7, 2015 года.
Бесплатный доступ
In mobile ad hoc networks (MANETs), providing reliable and stable communication paths between wireless devices is critical. This paper presents a fuzzy logic stable-backbone-based multipath routing protocol (FLSBMRP) for MANET that provides a high-quality path for communication between nodes. The proposed protocol has two main phases. The first phase is the selection of candidate nodes using a fuzzy logic technique. The second phase is the construction of a routing backbone that establishes multiple paths between nodes through the candidate nodes, thus forming a routing backbone. If any candidate node in the path fails due to a lack of bandwidth, residual energy or link quality, an alternate path through another candidate node is selected for communication before the route breaks, because a candidate node failure may lead to a broken link between the nodes. Simulation results demonstrate that the proposed protocol performs better in terms of the packet delivery ratio, overhead, delay and packet drop ratio than the major existing ad hoc routing protocols.
MANET, Fuzzy logic, Fuzzification, Candidate Nodes, Combined Score
Короткий адрес: https://sciup.org/15012307
IDR: 15012307
Текст научной статьи Fuzzy Logic Based Trusted Candidate Selection for Stable Multipath Routing
Published Online May 2015 in MECS
A mobile ad hoc network (MANET) is a collection of mobile nodes that can communicate with each other through multi-hop wireless links without a centralized administrator. Each node in the network acts as both host and router simultaneously and cooperates with other nodes for message transmission from source to destination [1]. Each node in a MANET is free to move independently in any direction; therefore, the network topology changes frequently. Due to their flexibility and distributed nature, MANETs have many applications such as disaster relief, emergency operations, military services, vehicular networks, casual meetings, campus networks and deep space communications [2] [3]. To provide quality of service (QoS) in these applications, many routing protocols have been designed for MANETs. The aim of any QoS support system in a communication network is to provide guaranteed services.
To provide such guarantees, many reactive routing algorithms have been proposed for ad hoc networks [4 -9]. Flooding methods are used to determine possible routes to new destinations without considering network resource limits such as bandwidth, node energy or link quality. As a result, these strategies may lead to excessive message transmissions, causing network congestion, longer delays and possible loss of packets. To avoid these problems, it is necessary to find the most stable path between nodes using the available resources in the network. The stability of a path is determined by the stability of the link and how long it can support communication between nodes.
Most of the existing stability-based ad hoc routing protocols use one or two metrics to find reliable paths between nodes. However, this is not sufficient in a MANET because wireless communication is vulnerable to node movement or fading of the wireless channel. Determining whether a link is good depends on many factors such as bandwidth, battery power, mobility, link quality and the reputation index of the mobile nodes. All of these factors are interconnected; therefore, the consideration of only one or two factors is not adequate for choosing a reliable or stable path. However, attempting to select a route that satisfies multiple constraints may result in conflicts and be difficult to model mathematically [10]. Therefore, a flexible design that can satisfy all the metrics is required. Because fuzzy logic can handle imprecise and uncertain information, we use fuzzy logic to solve this problem. Fuzzy logic is a theory that not only supports several inputs but also handles pervasive imprecise information; therefore, it is an appropriate choice to solve multi-metric problems in ad hoc networks.
This paper presents an effective stable multipath routing protocol called the fuzzy logic stable-backbonebased multipath routing protocol (FLSBMRP). The FLSBMRP uses multiple correlated metrics including link stability parameters such as bandwidth, node energy, link quality and node mobility to select candidate nodes. In the FLSBMRP, the initial candidate node selection is performed using a fuzzy logic technique that incorporates node parameters such as the residual bandwidth, residual power, link quality, node mobility and reputation index. Multiple paths are then established between the source and destination through these candidate nodes, thus forming a routing backbone. If any candidate node in the path fails due to a lack of bandwidth, residual energy or link quality, an alternate path through another candidate node is established.
The main contributions of this paper are as follows:
-
1) We propose a fuzzy logic stable-backbone-based multipath routing protocol (FLSBMRP) that finds reliable and stable paths between nodes.
-
2) The proposed protocol takes account of the available bandwidth, node mobility, node energy, link quality and reputation index metrics to select candidate nodes using a fuzzy logic technique.
-
3) The proposed protocol constructs a routing backbone between nodes.
-
4) The proposed protocol selects an alternative path from the set of established paths through the candidate nodes before the failure of a candidate node leads to route failure.
The rest of this paper is organized as follows. The next section provides a brief survey of the existing link-and route-stability-based routing protocols. The design of the proposed FLSBMRP is described in section III. Finally, the simulation results and conclusions are summarized in sections iv and v, respectively .
-
II. Related Work
Many routing algorithms that have been proposed for ad hoc networks are based on on-demand routing [11, 12]. In these routing algorithms, when a route fails, route recovery and maintenance procedures are initiated. These procedures consume considerable resources, such as bandwidth and power, and introduce extra delay. To reduce the possibility of a route failure during data transmission, it is essential to find routes that can last a long time. The stability of a route can be estimated using many parameters, such as the signal strength, the relative speed between two nodes, the bandwidth and the remaining battery power of the nodes.
The link-availability-based routing protocol (LBRP) has been proposed by Q. Han et al. [13]. The LBRP is designed to predict topology changes and to reduce the frequency of link failures. Taking these factors into account, the proposed scheme uses an analytical model for link availability with a random walk mobility model. The LBRP produces an accurate estimate of L(d 0 ,t), which is the probability that a link will be continuously available from time t 0 to t 0 + t given an initial distance d 0 (d 0 ≤ Rr). An accurate estimate of d 0 can be obtained from the signal strength. Simulation results show that the LBRP improves the availability and reliability of upper layer services and the quality of service.
-
J. Hemmes et al . [14] use a mobility prediction
technique to estimate route stability. In [15], to reduce communication overhead and storage requirements, a new routing algorithm based on fuzzy logic is designed. The proposed algorithm uses three parameters: signal power, mobility and delay.
In [16], the authors design link expiration time (LET) prediction algorithms to predict the LET between two mobile nodes on an active route. The proposed algorithms are implemented using the DSR algorithm. Three LET prediction algorithms are designed based on the received signal power, Global Positioning System (GPS) data and signal strength. These approaches are not suitable because they assume constant signal strength. The signal strength can be affected by environmental conditions, and its value can vary with node distance. The availability of a GPS signal is also not reliable; in some environments, when the mobile node energy is limited, the GPS cannot function.
In [17], the authors design a reliable routing algorithm based on fuzzy logic (RRAF) for finding a reliable reactive protocol in MANETs. During route discovery, the RRAF node with the greatest trust value and the maximum energy capacity is selected as the router based on a parameter called the reliability value. Using this value, the RRAF algorithm finds a reliable route from the source to the destination that increases the network lifetime and decreases the packet loss during transmission.
Zhang et al. [18] propose an estimated-distance-based routing protocol (EDRP) that reduces routing control overhead by restricting the propagation range of RREQ packets. In the EDRP, the change regularity of the received signal strength (RSS) is used to estimate the distance between a pair of nodes. However, because the RSS is affected by many factors, it is difficult to obtain a satisfactory result in real-world scenarios.
Celimuge Wu et al . [19] propose a portable fuzzy-constraint Q-learning protocol based on an ad hoc on-demand distance vector (PFQ – AODV) for VANETs. The PFQ-AODV protocol uses fuzzy logic to evaluate a wireless link by taking into account the available bandwidth, node mobility and link quality and uses a Q-learning-based approach to select a route that provides multi-hop reliability and efficiency. The PFQ-AODV protocol learns the best route using hello messages and RREQ messages. The PFQ-AODV protocol provides a flexible, portable and practicable solution for routing in VANETs.
In fuzzy logic wireless multipath routing (FLWMR), the hop count is the only metric used for route selection. When a source host needs to send a message to a destination, it first calls the local fuzzy logic controller to determine whether to send the message or drop it. If the decision is made to send the traffic, the FLWMR protocol floods route request packets (RREQ) to find multiple paths to the destination [20]. When the destination receives the first RREQ packet, it records the route information and waits for some period of time to receive another RREQ. The additional paths received by the source are added to the route buffer for use by the fuzzy router. When a node detects a broken link, the FLWMR protocol does not discover routes again; instead, the fuzzy controller chooses paths from the buffer for the traffic, which is ordered based on importance and network status.
Fuzzy logic wireless load-aware multipath routing (FLWLAMR) [20] chooses the route with the least delay as the primary route to transfer packets between the source and the destination node; the second route is the path that is maximally disjoint with the primary path and has the shortest distance. The source node monitors the congestion status of the active routes using a fuzzy routing algorithm and feeds the network status to the fuzzy logic controller to make the best routing decision. The network status is measured by the number of packets buffered at each node’s interface. When the RREQ packet reaches the destination, the protocol calculates the network status by measuring the number of packets buffered in each intermediate node in the network and sends this information back to the source with each RREP.
In our previous work [21], we constructed a stablebackbone-based multipath routing protocol (SBMRP) for MANETs. Initially, the nodes with high residual bandwidth, residual power and link quality and low mobility are designated as candidate nodes. Multiple paths are then established between the source and destination through these candidate nodes, thus forming a routing backbone. If any candidate node in the path fails due to a lack of bandwidth, residual energy or link quality, an alternate path through another candidate node is established. However, the selection of candidate nodes involves checking multiple constraints satisfying various threshold values. This may result in inaccurate decisions and involve more delay, and the trustworthiness or honesty of the candidate nodes is not considered.
In fuzzy stochastic multipath routing (FSMR) [22], the energy consumption rate at a node, the buffer occupancy rate at a node, the link stability between neighboring nodes and the number of intermediate hops are used to select routes, which are comparatively stable and long-lived, to ensure a lower packet loss rate, fewer route failures and less frequent route discovery.
The above protocols propose to find a stable path using the bandwidth and mobility of a node, the power and bandwidth of a node or link quality. None of these protocols use the combination of bandwidth, node energy, mobility, link quality and the reputation index of a node with a fuzzy logic approach to select multiple stable paths to provide efficient data transmission through the special nodes. Our work is motivated by observing the limitations of the existing on-demand multipath routing protocols. In the proposed protocol, we have considered bandwidth, energy, mobility, link quality and the reputation index using a fuzzy logic approach.
-
III. Proposed Protocol: Fuzzy Logic Based Stable Multipath Routing Protocol
-
A. Protocol Overview
The fuzzy logic stable-backbone-based multipath Routing Protocol (FLSBMRP) aims to find multiple stable paths between nodes through candidate nodes using a fuzzy logic approach. The FLSBMRP technique has two main phases; the first phase is candidate node selection using a fuzzy logic approach, and the second phase is the construction of a routing backbone. Efficient nodes, called candidate nodes, are selected from the set of mobile nodes in a network. These nodes have special properties and are selected based on parameters such as the Residual Bandwidth (RBW), Residual Energy (Er), Mobility of nodes ( M I ) , Link Quality (LQ) and Reputation Index (RI)of the node using a fuzzy logic technique. The second phase is the construction of a routing backbone. In this phase, multiple paths are established between the source and destination through the candidate nodes, thus forming a routing backbone. The backbone is a set of candidate nodes. If any candidate node in the path fails due to a lack of bandwidth, residual energy or link quality, an alternate established path is selected for transmission before the path fails between the nodes because the failure of a candidate node causes a route failure in the network.
-
B. Metrics Used to select candidate nodes
Let us consider the various metrics used to select the candidate nodes.
-
1) Residual Bandwidth
When a node needs to transfer data, it has to be aware of the local bandwidth and the interference and transmission range of the neighboring nodes. Consequently, the node needs to monitor the channel and estimate the local bandwidth BWL [23], which depends on the ratio of idle to busy time:
BWL = ∗ ( Ti ⁄ Tin ) (1)
Where, CCH is the channel capacity and Tin is the idle time during the predefined time period Tin .
The minimum bandwidth ( BWml ) of all of the nodes within the interference range is determined from prior neighboring node information. The residual bandwidth (RBW) of a node is given by equation (2).
RBW = - BWmi (2)
-
2) Energy Model
The energy model is used to calculate the residual node energy. Let Ei be the initial node energy [24]. The energy consumed by the node over a given period of time is estimated as
E ( t )= ntx ∗ e + ^rx ∗ 6 (3)
Where ^tx and n tx are the number of packets transmitted and received by the node, respectively, over a time period t and ε and δ are constants in the range (0,1). The residual energy ET of a node at time t is computed as
Er = - E ( t ) (4)
-
3) Node Mobility Model
The mobility of node j with respect to node i is estimated based on the ratio of the received signal strength ( RSS ) between two consecutive packet transmissions from a neighbor node, as given in equation (5) [25].
P^^new
M) ( i )=10log → (5)
→ j
Where RSS is given by
RSS = ∗ a ∗ Btx (6)
β is a constant that depends on the wavelength and the antennas, д is the channel gain and Ptx is the signal power of the transmitter.
-
4) Link Quality Model
The link quality ( LQ ) is the ratio of the number of error bits (Berror) to the number of receiving bits ( Btx ) [26]. The LQ estimates the number of retransmissions required to send packets by measuring the loss rate. The expression for the LQ is given in equation (7).
LQ = ⁄B (7)
Every time a node receives a data packet, the LQ value is updated based on the interference from the wireless channel, the additive white Gaussian noise (AWGN) and the signal transmission range.
-
5) Reputation Index
In this phase, the direct ( DR[j ) and indirect ( IDRtj ) reputation values for each node are estimated using the Eigen trust algorithm. A resolver is then used to estimate the global trust value of the node [27]. Let RSS be the signal strength from ТЦ to n each node (Qi) estimates the Eigen vector centrality of its neighbors as in equation (8); it is proportional to the sum of the nodes that are linked to n
Qi = ∑ jes ( I ) Qi = ∑ 1=1^1 , jQj (8)
Where, s ( i ) is the set of nodes linked to node i node, n = a is the number of nodes, Ψ is a constant value and
, is the adjacency matrix for the network. , = ,
Where is the wireless signal strength from node i to its neighbor node j , and , =0 if i and j are not neighbors.
This value is updated when the node receives or sends a message to its neighbors.
Each node periodically computes the connectivity rating (recent satis faction = (n )) for each of its direct neighbor nodes using the percentages computed in equation (9).
n =% F ( i , j )- % E ( i , j )
DRtj = ( pr )∗ a + n ∗ (1- a ) (10)
Where DRB ( pr ) is the previous trust of node n for node n prior to the inclusion of the current S ij , and OL is a constant representing the confidence level for the trust of n for n .If there is no link between n and n then DRij is reduced using a constant β instead of α DRB is normalized using equation (11).
DRij =
7 /( t ) max( DRij )
Where, f ( t ) max is the maximum observed DRij over time period t .
The indirect reputation ( IDRij ) is estimated from the aggregation of the trust reports received and processed b n for n which is shown below:
I 1
∑ ^[ni ∗ e ( n )∗ ^T[n lUKtj = ∑( e ( n )∗ ^in )
Where, E(71) is the degree centrality of the reporting node.
-
C. Fuzzy Logic Based Trusted Candidate Node Selection
When nodes are deployed in a network, each node broadcasts a HELLO packet to its neighbors periodically. The HELLO packet is used to select the candidate nodes. Each hello message includes the sender's node identifier Node ID , RBW , Er , LQ , Mj ( i ), RI as well as the neighboring node addresses. After receiving the Hello message, each node identifies itself and updates its neighbor list (NL) containing these values. Using a fuzzy logic approach, the candidate nodes are selected. The format of the HELLO packet is shown in table 1.
Table 1. HELLO Packet Format
|
Node ID |
RBW |
E r |
LQ |
Mi j |
RI |
Neigh. ID |
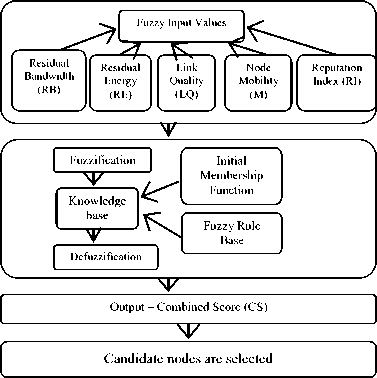
Fig. 1. Fuzzy Logic Approach for selection of candidate nodes
Fig. 1 shows the major processes in the fuzzy logic approach: fuzzification, rule evaluation and defuzzification. Node parameters RBW , ET , LQ , Mj ( i ), RI are the input parameters and are fuzzified to make fuzzy decision rules. Based on the outcome of the rules, a combined score is generated. Based on the value of the combined score, the candidate nodes are selected.
-
1) Calculation of multiple node parameters
The residual bandwidth , residual energy, mobility, link quality and reputation index of a node are calculated (Section 2B ).
-
2) Fuzzification
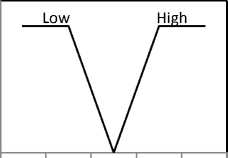
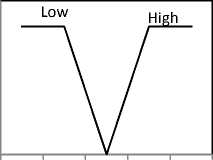
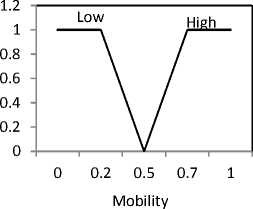
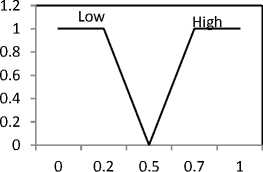
The process of converting numeric values to fuzzy values using a fuzzy membership function is called fuzzification [18]. The fuzzy membership functions of the input variables RBW, ET , LQ, М- (i), RI are defined in fig. 2. The fuzzy membership functions are defined based on the following considerations. First, we have to avoid using low bandwidth links and nodes with low energy. However, if the available bandwidth and energy are above the adequate levels for links and nodes, respectively, there is no significant preference for selecting any link. As shown in fig. 2(a) and 2(b), we do not differentiate among values greater than 0.5. Second, to provide high reliability, we prefer nodes with lower mobility and high quality links. Low node mobility means that the node has a stable link, and a high link quality provides a strong link. Therefore, the Mj and LQ membership functions are used to determine the links with values greater than 0.5. Third, to select the trusted candidate nodes, we use the reputation index. The membership function is defined to select candidate nodes whose value is greater than 0.5. It is possible to use more complicated membership functions. To maintain computational efficiency and uncomplicated formulas, triangular functions are used in the proposed protocol because we only need to distinguish candidate and noncandidate nodes.
Node parameters RВW,Er, LQ , M j (0, RI use a membership function to calculate to what degree the parameters belong to the two possibilities {high, low}.
-
3) Rule Evaluation
0.8
0.6
0.4
0.2
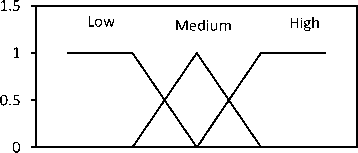
Based on the fuzzy values RВW,Er, LQ , M j (i), RI, IF-THEN rules are used as defined in table 2 to calculate a combined score for the node. The linguistic variables for the combined score are defined as {low, medium, high}. For example, in table 2, rule 30 may be expressed as follows:
If Residual Bandwidth is high, Residual Energy is high, Link Quality is high, Reputation Index is High and Mobility is low, Then, Combined Score is High.
1.2
Low

High
0 0.2 0.5 0.7 1
Residual Bandwidth
(a)
1.2
0.8
0.6
0.4
0.2
0 0.2 0.5 0.7 1
Residual Enegry
(b)
1.2
0.8
0.6
0.4
0.2
0 0.2 0.5 0.7 1
Link Quality
(c)
(d)
Reputation Index (e)
Fig. 2. Membership functions: (a)RE, (b)Er, (c) M j . (d) LQ, (e) RI
The interpretation of this rule is that high bandwidth, energy, link quality and reputation index and low node mobility are favorable inputs and will yield a high combined score. A node with the maximum combined score is chosen as a candidate node.
-
4) Defuzzification
The process of producing a numeric result based on an output membership function and the corresponding membership degrees is called defuzzification. The output membership function is defined as in fig. 3. The center of gravity method is used for defuzzification during the fuzzy decision-making process. The defuzzification method is described by.
Fuzzy_cost = Bal№ft * V (fty]/[^auiruiesV(f))A (13)
Combined Score
Fig. 3. Membership function of the combined score
Where, Fuzz__cost is used to specify the degree of the function is modified to a crisp value using this decision, ft are the fuzzy variables and V (f^ is the defuzzification method.
membership function. The output of the fuzzy cost
Table 2. Fuzzy Rules
|
Rule No. |
Bandwidth |
Energy |
Link Quality |
Node Mobility |
Reputation index |
Combined Score |
|
Rule 1 |
Low |
Low |
Low |
Low |
Low |
Low |
|
Rule 2 |
Low |
Low |
Low |
Low |
High |
Low |
|
Rule 3 |
Low |
Low |
Low |
High |
Low |
Low |
|
Rule 4 |
Low |
Low |
Low |
High |
High |
Low |
|
Rule 5 |
Low |
Low |
High |
Low |
Low |
Low |
|
Rule 6 |
Low |
Low |
High |
Low |
High |
Low |
|
Rule 7 |
Low |
Low |
High |
High |
Low |
Low |
|
Rule 8 |
Low |
Low |
High |
High |
High |
Low |
|
Rule 9 |
Low |
High |
Low |
Low |
Low |
Low |
|
Rule 10 |
Low |
High |
Low |
Low |
High |
Low |
|
Rule 11 |
Low |
High |
Low |
High |
Low |
Low |
|
Rule 12 |
Low |
High |
Low |
High |
High |
Medium |
|
Rule 13 |
Low |
High |
High |
Low |
Low |
Low |
|
Rule 14 |
Low |
High |
High |
Low |
High |
Medium |
|
Rule 15 |
Low |
High |
High |
High |
Low |
Low |
|
Rule 16 |
Low |
High |
High |
High |
High |
Medium |
|
Rule 17 |
High |
Low |
Low |
Low |
Low |
Low |
|
Rule 18 |
High |
Low |
Low |
Low |
High |
Low |
|
Rule 19 |
High |
Low |
Low |
High |
Low |
Low |
|
Rule 20 |
High |
Low |
Low |
High |
High |
Low |
|
Rule 21 |
High |
Low |
High |
Low |
Low |
Low |
|
Rule 22 |
High |
Low |
High |
Low |
High |
Medium |
|
Rule 23 |
High |
Low |
High |
High |
Low |
Low |
|
Rule 24 |
High |
Low |
High |
High |
High |
Medium |
|
Rule 25 |
High |
High |
Low |
Low |
Low |
Low |
|
Rule 26 |
High |
High |
Low |
Low |
High |
Low |
|
Rule 27 |
High |
High |
Low |
High |
Low |
Low |
|
Rule 28 |
High |
High |
Low |
High |
High |
Medium |
|
Rule 29 |
High |
High |
High |
Low |
Low |
Medium |
|
Rule 30 |
High |
High |
High |
Low |
High |
High |
|
Rule 31 |
High |
High |
High |
High |
Low |
Medium |
|
Rule 32 |
High |
High |
High |
High |
High |
Medium |
|
Rule 33 |
Low |
Low |
Low |
Low |
Low |
Low |
|
Rule 34 |
Low |
Low |
Low |
Low |
High |
Low |
|
Rule 35 |
Low |
Low |
Low |
High |
Low |
Low |
|
Rule 36 |
Low |
Low |
Low |
High |
High |
Low |
-
D. Construction of Routing Backbone
When a source needs to transmit a data packet to a destination node, it initiates the multipath routing discovery process between the source and the destination. This forms the routing backbone. When the source node needs to send information to its destination node, it must first check its routing table to determine whether the routing table contains information. If a route is found, the source will use the route to send the data packet immediately. Otherwise, the source node will broadcast a route request (RREQ) packet. The RREQ packet is shown in table 3.
Table 3. RREQ Packet Format
|
Source |
Destination |
Previous hop |
Previous |
Nodes |
|
ID |
ID |
node ID |
Nodes State |
State |
The RREQ packet contains a source identifier ID, destination ID, previous hop ID, previous node state and node state. The node state field indicates whether the node is designated as a candidate node or a non-candidate node. When a node receives an RREQ packet, it will forward the packet to all its neighbors. When an intermediate node receives an RREQ packet, if it has already received an RREQ packet with the same sequence number and destination ID, it drops the redundant RREQ packet. When an intermediate node receives an RREQ packet for the first time, it updates its routing table with the source ID and destination ID and the previous hop node ID and its state. It appends its state to the RREQ message in the node state field and analyzes the destination ID.
When the destination receives the RREQ message, it appends its state to the route reply (RREP) and unicasts the reply message on the reverse path toward the source. The destination performs this action for every RREQ it receives. When an intermediate node receives the RREP message, it appends its state to the message, updates its routing table and unicasts the RREP in the direction of the source using the previously stored hop node information.
The source chooses a path of candidate nodes to transmit the data packet. If any candidate node in the path fails (using the failure condition shown below), then the path with the failed candidate node is ignored and an alternate path through the candidate nodes is chosen for data transmission before the route breaks between the nodes. Consequently, the candidate nodes in the routing backbone are rotated, minimizing their overhead and energy.
Failure condition :
(RB < Th (RB)) || (RE < Th(RE)) 11 (M i. > Th ( Mi-)) || (LQ <
Th (LQ)) || ( RI < Th (RI))
Fig. 4 shows an example of the establishment of a multipath route between S and D. The paths (S- N 6 -N 9 N 10 -D), (S- N 8 -N 12 -D) and (S- N 5 -N 13 N 14 -N 15- D) are obtained for data transmission. As shown in the fig., N10 has failed because its residual energy has dropped below the minimum threshold. This in turn affects the data transmission. To overcome this problem, the FLSBMRP chooses an alternate path via candidate node N 8 to transmit the data before the route breaks.
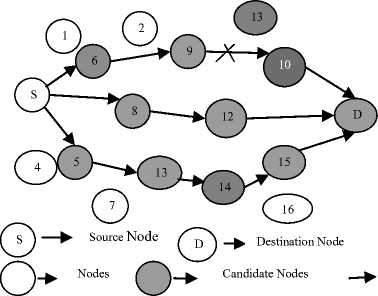
Fig. 4. Multipath establishment between source and destination with a candidate node failure.
-
IV. Results and Discussion
-
A. Simulation Setup and Parameters
A comparison of the proposed protocol with existing protocols is performed using the ns-2 network simulator [28]. The simulation models a network of 100 nodes in a 1500 m x 1000 m area with mobile node speeds varying from 5–50m/s. The radio transmission range is assumed to be 250m with a pause time of 20s. A random waypoint mobility model is used to place the nodes randomly. Each node randomly selects a position and moves toward that position with a speed between the minimum and
maximum. Once the node arrives at the position, it stays for a predefined time. After that time, it selects a new position and repeats the process. The simulations run for 200s. The detailed simulation parameters are summarized in Table 4.
Table 4. Simulation Parameters
|
Sl. No. |
Parameter Name |
Value |
|
1. |
No. of Nodes |
100 |
|
2. |
Rate |
250kb |
|
3. |
Network size |
1500 x 1000 m2 |
|
4. |
MAC Protocol |
IEEE 802.11 DCF |
|
5. |
Channel capacity |
2 Mbps |
|
6. |
Transmission range |
250 m |
|
7. |
Simulation time |
100 sec |
|
8. |
Packet size |
512 bytes |
|
9. |
Nodes speed |
10, 20, 30, 40 and 50 m/s |
|
10. |
Pause time |
20 |
|
11. |
Routing protocols |
AODV, FLSBMRP, EDRP |
The evaluation of the proposed protocol is based on parameters including the control overhead, the end-to-end delay, the number of packets dropped and the packet delivery ratio. The parameter definitions are given below.
-
1) Packet Delivery Ratio (PDR): The PDR is the ratio of the number of packets received successfully to the total number of packets transmitted.
=( ․ ⁄ ․ )×100
-
2) Packet Drop Ratio: The packet drop ratio is defined as the number of packets dropped during the transmission of data packets from the source node to the destination .
Packet Drop Ratio
= (( ․ - ․ )⁄))
-
3) Average end-to-end delay: Average end – to - end delay is the time taken to transfer the packet from source node to the destination node.
--
- ∑(( - )⁄ ․)
-
4) Normalised Routing Load (NRL): The NRL is defined as the total number of routing packets transmitted per data packet.
= ( ․)
⁄( ․)
-
B. Performance Analysis
In [29] we have evaluated the performance by considering PDR and packet drop ratio and compared proposed work with EDRP. In the protocol performance analysis, we investigate the routing performance of the EDRP [17] and the FLSBMRP compared with the conventional ad hoc on-demand distance vector (AODV) routing protocol [3]. We evaluate the performance of the FLSBMRP at varying mobile speeds. In mobile scenarios, the node speed is an important metric that affects the network topology. We fix the number of nodes at 100 and vary the maximum speed from 10 to 50m/s. The evaluation results are as follows.
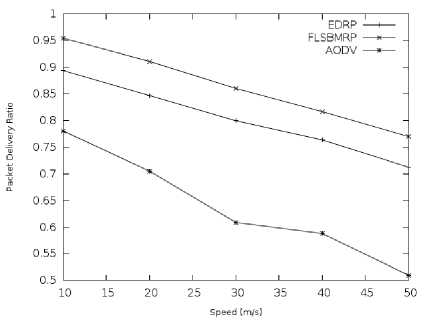
Fig. 5. Packet Delivery Ratio vs. Speed
Fig. 5 shows the packet delivery ratio for the three protocols. The packet delivery ratio decreases as the maximum speed increases because the network becomes less stable. The FLSBMRP shows significantly better performance than the other protocols. This is because the FLSBMRP considers the available bandwidth, node movement, energy and link quality in the route selection. Because the AODV protocol only considers the number of hops in the route selection, it produces poorer performance. The EDRP performs better than the AODV protocol because it takes link quality into account. However, the performance of the EDRP drops as the speed of the mobile nodes increases. The AODV and EDRP protocols reestablish the route after a route break, which results in packet losses. The FLSBMRP can switch to a better route before a route breaks, resulting in a significant improvement.
the AODV and EDRP protocols do not take node movement into account in the route selection, they produce longer delays when the node mobility is high. This is because route discovery is time consuming. Using its fuzzy logic technique, the FLSBMRP chooses the best route, which can efficiently reduce the number of route rediscoveries. As a result, the FLSBMRP produces the lowest end-to-end delay.
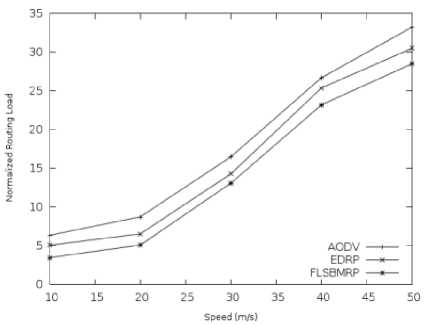
Fig. 7. Normalized Routing Load vs. Speed
Fig. 7 shows the control overhead of the FLSBMRP, AODV and EDRP protocols at different speeds. The control overhead increases as the speed increases because when the speed increases, the mobility of the nodes increases and leads to frequent path breaks. The control overhead of the FLSBMRP is lower than the EDRP and AODV protocols. This is because the FLSBMRP finds multiple paths in a single route discovery process using candidate nodes. Another reason is that the FLSBMRP restarts the route discovery process when all backbone paths have failed. The control overhead of the FLSBMRP is less than the EDRP because the EDRP finds weak links using the link quality measure.
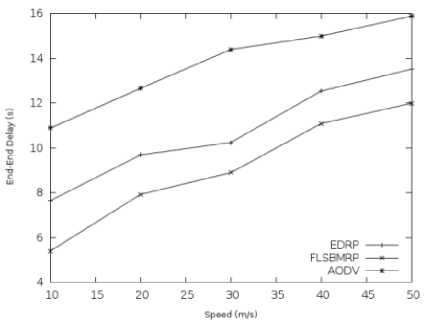
Fig. 6. End – End Delay vs. Speed
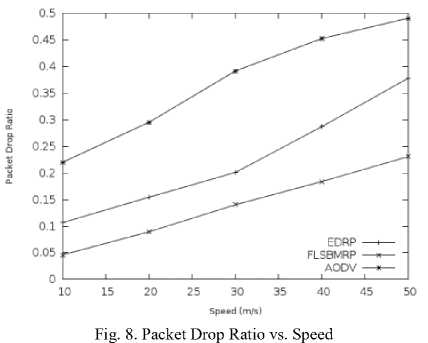
Fig. 8 shows a comparison of the packet drop ratios of the FLSBMRP, AODV and EDRP protocols at different speeds. As the speed increases, the number of packet drops increases because of the high mobility in the network. Therefore, no matter what routing scheme is used, the routing load is increased. The number of packets dropped by the FLSBMRP is less than the AODV and EDRP protocols because the FLSBMRP always
Fig. 6 shows the end-end delay for packets that are received at the destination. As the speed increases, the frequency of link breakage increases. Frequent route reconstructions incur more control overhead, increasing the probability of congestion and packet collisions. Fig. 6 shows that the FLSBMRP is effective in reducing the end-to-end delay, particularly when the speed is high. As the speed increases, the topology changes faster. Because
chooses the most stable route for transmission and finds an alternate path through the candidate nodes before the path breaks. Consequently, it reduces the number of packets dropped.
-
V. Conclusion
In this paper, we have proposed the FLSBMRP to find the most stable path between nodes using candidate nodes. In this protocol, candidate node selection is performed using a fuzzy logic technique. This technique uses node parameters that include the residual bandwidth, residual power, link quality, node mobility and reputation index. Multiple paths are then established between the source and the destination through these candidate nodes, thus forming a routing backbone. If any candidate node in the path tends to fail due to a lack of bandwidth, residual energy or link quality, an alternate path through another candidate node is established before the path breaks. The simulation results show that the proposed technique offers security and reduces the computational overhead and delay and the packet drop and increases the packet delivery ratio.
Список литературы Fuzzy Logic Based Trusted Candidate Selection for Stable Multipath Routing
- http://www.ietf.org/html.chapters/manet-chapter.html.
- P. Johnson “ Routing Protocols for Mobile Ad-Hoc Networks – a comparative performance analysis”, Proc. ACM/IEEE Int. Conf. on Mobile Computing and Networking (MobiCom’99), Seattle, WA, Aug. 15-19, 1999, pp. 195-206.
- C. Siva Ram Murthy and B. S. Manoj, “Chapter – 3 Ad Hoc Wireless Networks”, in ‘Ad Hoc Wireless Networks : Architectures and Protocols’, (Prentice Hall, june 2000, 1st Edition) , pp. 213 – 245.
- C. E. Perkins and E. M. Royer, “Ad-Hoc on-demand distance vector routing”. Proc. Second IEEE Workshop on Mobile Computing Systems and Applications, New Orleans, Louisiana, USA, 25-26 February 1999, pp. 90–100.
- D. Johnson and D. A. Maltz, “Dynamic Source Routing Protocol in Ad Hoc Wireless Networks,” Internet Draft, drfat-ietf-manet-dsr-10.txt, july 2006.
- C. K. Toh, “Associativity-based routing for Ad Hoc mobile networks”, Wireless Personal Communications, Vol.1 (2), March 1997, pp. 103–139.
- V. D. Park and M. S. Corson, “A highly adaptive distrubuted routing algorithm for mobile ad- hov networks”, Proc. Conference on Computer Communications, Sixteenth Annual Joint Conference of the IEEE Compter and Communications Societies, Driving the Information Revolution (IEEE INFOCOM 1997), Kobe, Japan, April 7-12, 1997, pp. 1405-1413.
- M K. Marina and S R. Das, “On-demand Multipath Distance Vector Routing in Ad Hoc Networks”. Proc. 9th International Conference on Network Protocols (ICNP 2001), Riverside, CA, USA, 11-14 November, pp. 14-22.
- Royer E M and Perkins C E, “ Multicast operation of the ad hoc on demand distance vector routing protocol,” In: Proc ACM MOBICOM, August 1999. pp. 207-218.
- G. Santhi and Alamelu Nachiappan, “Fuzzy-cost based multiconstrained QoS routing with mobility prediction in MANETs,” Egyptian Informatics Journal, Vol. 13, 2012, pp. 19–25.
- S. J. Lee and M. Gerla, “AODV-BR: Backup routing in Ad Hoc networks”. Proc. of IEEE Conf. Wireless Communication and Networking (WCNC 2000), Chicago, 23-28 Sep. 2000, pp. 1311 – 1316.
- Qi Xue and Aura Ganz, “ Ad Hoc on-demand QoS routing in mobile Ad Hoc networks,” Elsevier journal of Parallel Distrb. Comput., 2003, Vol. 63, pp. 154-165.
- Q. Han, Y. Bai and L. Gong , “ Link availability prediction-based reliable routing for mobilr ad-Hoc Networks,” in proceedings of IET Communications, 2011, Vol. 5, Iss,16, pp. 2291-2300.
- J. Hemmas, Matthew Fisher and K. Hopskin, “ Predictive Routing in Mobile Ad-Hoc Networks,” Proc. of IEEE fifth international conference on next generation Mobile Applications and Services, 2011, pp. 117-122.
- Sonia Gupta, P. K. Bhakti and Vishal Choudhary “ Fuzzy logic based Routing Algorithm for Mobile Ad Hoc Networks”, High Performance Architecture and Grid Computing Communications in Computer and Information Science , Volume 169, 2011, pp 574-579.
- Achour Rhim and Zbigniew Dziong, “Routing Based on Link Expiration Time for MANET Performnace Improvement,” Proc. of the IEEE Malaysia International Conference on Communication, Malayasia, 15-17 Dec 2009, pp. 555-560.
- G Ghalavand , A Dana, and M. Rezahosieni , “Reliable routing algorithm based on fuzzy logic for Mobile Ad Hoc Network”, 3rd International Conference on Advanced Computer Theory and Engineering (ICACTE), 2010, pp. v5-606-v5-609.
- Xin Ming Zhang,, En Bo Wang, Jing Jing Xia, and Dan Keun Sung, “An Estimated Distance-Based Routing Protocol for Mobile Ad hoc Networks.” IEEE Transactions On Vehicular Technology, Vol. 60, NO. 7, Sept. 2011, pp. 3473-3484.
- Celimuge Wu, Satoshi Ohzahata, and Toshihiko Kato, “Flexible, Portable, and Practicable Solution for Routing in VANETs: A Fuzzy Constraint Q-Learning Approach” IEEE Transactions On Vehicular Technology, Vol. 62, No.9, Nov. 2013, pp. 4251-4263.
- Alandjani Gasim and Johnson Eric E. “Fuzzy routing in ad hocnetworks,” IEEE International Conference on performance, computing, and communications conference, 9–11 April 2003. pp. 525–530.
- Sujata V. Mallapur and Siddarama R. Patil, “Route Stability Based on Demand Multipath Routing Protocol for Mobile Ad Hoc Networks”, IEEE third International Conference on Communication and Signal Processing, April 3-5, 2014, pp. 1288-1292.
- Rajiv V. Dharaskare and M. M. Goswami, “Intelligent Multipath Routing Protocol For Mobile Ad Hoc Network,”, International Journal of computer science and Applications, Vol .2, November/I December 2009, pp. 135-145.
- Tung-Shih Su, Chih-Hung Hsieh Lin, and Wen Shyong, ‘A Novel QoS-Aware Routing for Ad Hoc Networks’. Proc. of the 9th Joint Conference on Information Sciences (JCIS), Taiwan, 8 – 11 October 2006.
- Vinay Rashiwal, S, Verma and Bajpai, S. K.: ‘QoS Based Power Aware Routing in MANETs’, International Journal of Computer Theory and Engineering, April 2009, Vol. 1, No. 1, pp-47-57.
- P Basu, N Khan, and D. C Little, ‘A Mobility Based Metric for Clustering in Mobile Ad Hoc Networks’. Proc. 21st International Conference on Distributed Computing Systems Workshops (ICDCS 2001 Workshops), Phoenix, AZ, USA , 16-19 April 2001, pp 413 – 418.
- Rajashekhar Biradar, , Sunilkumar Manavi, and Mylara Reddy, ‘Link Stability Based Multicast Routing Scheme in MANET’ , Elsevier Journal of Computer Networks, Vol. 54, pp.1183-1196.
- R. Zakhary, Sameh and Radenkovic, Milena “Reputation-Based Security Protocol for MANETs in Highly Mobile Disconnection-Prone Environments”, IEEE/IFIP The Seventh International Conference on Wireless On-demand Network Systems and Service, Feb. 2010, pp. 161-167.
- NetworkSimulator http://www.isi.edu.nsnam/ns.
- Sujata V Mallapur & Siddara R Patil, “Fuzzy logic-based stable multipath routing protocol for mobile ad hoc networks”, In proc. of IEEE INDICON 2014, Dec 2014, pp. 1-6.


