Improving Deceased Identification and Claiming System in Mortuaries Using Fingerprint: A Developing Country Perspective
Автор: Iwara I. Arikpo, Chidalu Prince Egeonu
Журнал: International Journal of Mathematical Sciences and Computing @ijmsc
Статья в выпуске: 4 vol.7, 2021 года.
Бесплатный доступ
The mortuary industry in most developing countries are in need of improvement on the receiving and releasing of deceased persons. Paper-based mortuary systems lack reliability, timely information retrieval, accountability, data security and access control; compared to computer-based, mortuaries are the norm in advanced countries. This study reports the development of a fingerprint-based biometric mortuary system for deceased identification and claiming. The system design methodology was based on the object-oriented analysis and design approach using the UML. The system was implemented with Java as the frontend and processing logic, interacting with MySQL Server at the backend for transaction management. As generated from the University of Calabar Teaching Hospital Calabar, the result of this study shows that, with the fingerprint verification technique, mortuary establishments in Nigeria and related countries can enhance the deceased claimant verification process to avoid releasing the deceased to wrong persons and reduce deceased identification anomalies. The study has shown that biometrics technology can enhance deceased identification and release in resource-constrained settings like Nigeria.
Mortuary, deceased, biometric, paper-based, fingerprint, identification, claimant
Короткий адрес: https://sciup.org/15018236
IDR: 15018236 | DOI: 10.5815/ijmsc.2021.04.04
Текст научной статьи Improving Deceased Identification and Claiming System in Mortuaries Using Fingerprint: A Developing Country Perspective
Published Online December 2021 in MECS DOI: 10.5815/ijmsc.2021.04.04
A mortuary is a hospital service point for the security and safety of the deceased awaiting identification, burial, or post-mortem service. Mortuaries have for long been used as places to preserve and prevent the deterioration of the deceased. They are valuable sources for tracking records and information on dead persons as well as an institution for research. Unfortunately, mortuary services are a neglected business, especially in developing countries. Mortuaries are usually not of an acceptable standard with old infrastructure like post-mortem tables and are often treated as dumping grounds for the deceased [1].
Biometric identification systems employ the use of biological data, in the form of voice, face and signature scans. The most common physiological biometric include scans for: finger, retina, hand, and iris. Biometric identification cannot be forgotten or stolen and involves the use of information technology to acquire, analyze, store, manage and transmit genetic data. Generally, one could digitally authenticate a user with any of these authentication methods: “what you know, what you have, what you are or who we are” refer to what is unique about people, their physical bodies as human beings. Biometric authentication is referred to as 1:1 (one-to-one) matching [2].
The emergence of biometric identification and verification security systems have shown a significant improvement in data security and have gradually silenced password security systems. The biometric systems are currently integrated into computer devices like laptops and smartphones to improve their security and access control. With the increasing use of information technology and the need to protect data, people have multiple accounts and passwords. Humans are not likely to remember so many passwords or draw up patterns to unlock devices or perform secure tasks; so, they end up using things they know to create these passwords (birthdays, wife’s name, pet’s name, etc.). It is easy to crack passwords because most user passwords are weak. If we create strong passwords (that should be meaningless to us), we will forget them, and it will be very difficult to remember several passwords [3].
Biometrics-based security techniques, identification and verification using human characteristics and behavioural traits, such as fingerprint and iris recognition, are playing an increasingly critical role, alongside traditional computerbased security systems, in securing information systems and physical assets, and are helping to mitigate identity theft and internet-based fraud [4]. It is believed that no two people have an identical fingerprint in the world, so fingerprint verification and identification is the most popular way to verify the authenticity or identity of a person wherever the security is a problematic question. The reason for the popularity of the fingerprint technique is the uniqueness of a person, which arises from his behaviour and personal characteristics [5].
Identification of the deceased after embalmment and authentication of the claimant has posed a great challenge in mortuary operations as the authors were informed during the information gathering process at the University of Calabar Teaching Hospital (UCTH), Calabar, and other hospitals across Nigeria. It was discovered that most deceased are only identified by the tags attached to them after embalmment. Deceased in most cases are kept on racks on arrival and moved to refrigerators after undergoing necessary mortuary registration. The Morticians and Anatomists work on shift and most often do not validate deceased records as required before going-off. Perhaps, dead tags are lost or displaced during the process, leading to the displacement of the deceased.
Verification of the deceased claimant is so less-stringent that the dead are released to anybody with the mortuary receipt but without clear verification of whether it is with the original claimant’s consent. Gang-related, marital and community crises can cause people with different motives to claim a deceased. Possibly, the deceased might be released to the wrong person if proper claimant verification is not in place.
Clearly, some of the problems include, displacement of deceased due to difficulty in identification; illegal receiving and releasing of deceased; documentation of funds (morticians and anatomists have often reported cases where some deceased are illegally released with accrued mortuary service cost that was never accounted for); difficulty in retrieving deceased information; inadequate management and maintenance of autopsy reports.
The goal of this study is to improve the identification and claiming of deceased in Nigerian mortuaries using a biometric system that monitors and maintains reliable deceased records and claimant verification.
-
2. Literature Review
-
3. Materials and Methods
Many related works regarding the biometric system in schools, colleges, healthcare and industries exist. [6] developed a biometric attendance system where students’ bio-data are taken during both the examination times and also on regular hours. A fingerprint device is used and the attendance of the students are stored in the database. Here, the study focused on students’ identification and verification during an examination. The biometric system was found suitable for the academic environment and helped to eradicate impersonation during examinations.
Mortuary management started in ancient times. Most famous are the Egyptians who embalmed their dead then. In the United States, mortuary management was not generally in high esteem before the 20th century, especially compared to physicians, but because many mortuary heads study embalming as part of mortuary science programmes, they can be classified as a part of the medical profession. Mortuary heads gained a higher status that peaked in the 1950s, but this later declined in the 1960s and 1970s. Many reputations were eroded as a result of high-profile exposes on unethical practices and police investigations that followed the criminally negligent behaviour of some morticians [7].
Over time, a lot of effort has been made worldwide to improve the management of the deceased in mortuaries. A few of these approaches are presented in this paper. Hospital Authority (2013) [8], reports some enhancement programmes introduced in the mortuaries in Hong Kong which include: Development of the Mortuary Information System to help minimize the risk of wrong identification through a barcode system; and streamlining of the procedures on body collection and identification both on the nursing side during the collection of bodies from the ward, and on the mortuary side with enhanced counterchecking and standardized documentation.
The Hong Kong government was able to reduce deceased identification problems by attaching every deceased that arrives in their mortuaries with a tag containing a barcode that can be decrypted by a bar code reader. But the only outstanding problem with this technology is that if the bar code tag is misplaced or mistakenly removed from the deceased, then identification will be an issue. However, the bar code system handles only identification problems and does not account for their financial transaction and staff schedules.
Compugroup Forensic Information Management and Mortuary System (CGM FIMMS) is an application specifically designed to manage deceased persons in the hospital setting in Malaysia. The application addresses the core functional requirements of a Forensic Department, such as receiving, storage and release of dead bodies. Besides, it facilitates the performance of autopsies by enabling documentation of post-mortem findings by the pathologist. The application consists of a number of modules configurable to create a complete solution for the forensic department of any government or teaching hospital and any regional centres designated as centres of excellence for Forensic Medicine. The application is integrated with the Patient Management System to facilitate the deceased person’s registration from the wards or bodies brought in dead by the Police for autopsy.
Strengths of the CGM FIMMS application include Auto flow-in of demographic information of the deceased persons during registration for admitted patients; Reading from MyKad (Malaysian Identity Card) to capture demographic data of the deceased person; separate freezers for storage of Muslim and Non-Muslim bodies; generation of body tags and freezer labels on registration of personnel for bodies that are brought in dead, etc. However, some of its deficiencies include: failure to account for accrued mortuary service cost for individual deceased; the information security does not employ biometric technology; the CGM FIMMS is also an embedded system. It uses entirely customized hardware devices that differ from a typical personal computer, making it expensive, difficult to develop and deploy; it does not auto-count days the deceased has stayed in the mortuary.
The system design approach for the system developed in this study was based on the object-oriented analysis and design methodology (OOAD) using the unified modelling language [9], [10]. The conceptual model for the system is shown in Figure 1. Other logical and physical design components for the system are also presented.
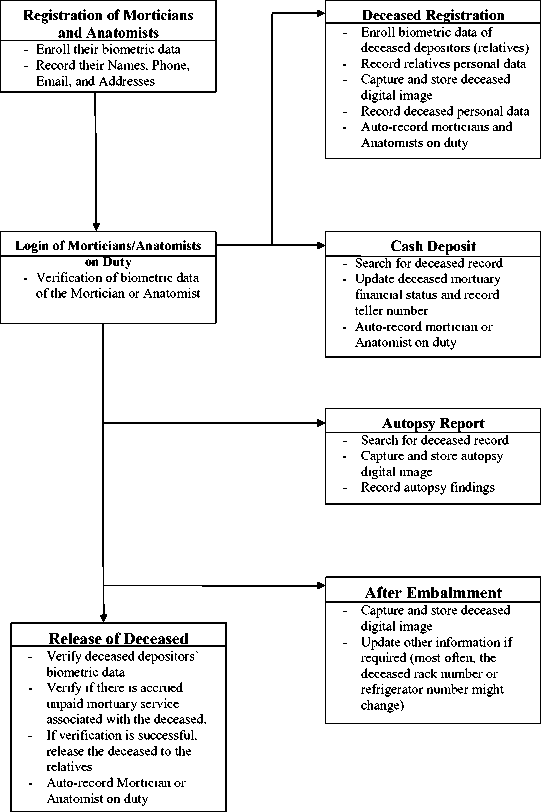
-
Fig. 1. Conceptual model of the system
From Figure 1, seven fundamental entities and activities were established. The first activity handles the registration of morticians and anatomists, which includes their fingerprints, enrollment and personal details. The second activity authenticates the mortician and anatomist on duty through fingerprint verification. The third, fourth, fifth, sixth and seventh activities: deceased registration, cash deposit, autopsy report, embalmment, and release of deceased, respectively, are the functions the authenticated mortician or anatomist can perform. The summaries of the functions of each activity are contained in their respective objects.
-
A. System design components
The Use case diagram for the system is presented in Figure 2 and shows the system entities and their activities. These activities are the privileges of the entities that are associated with them.
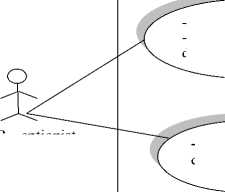
-Search/Update deceased record
-Capture deceased
-Enroll deceased depositor’s fingerprint
Receptionist (Mortician/ Anatomist)
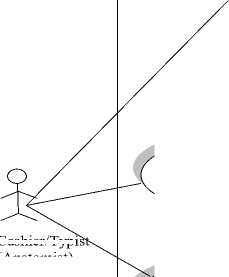
Cashier/Typi (Anatomist)
-Record cash In-flow
-Record autopsy findings

-Cash discount
-Set Cost of embalmment
-Set Service charge
Mortuary Director
-Verify claimant fingerprint
-Release deceased
-
Fig. 2. Use-Case Diagram of the mortuary biometric system
The system class diagram, as shown in Figure 3, identifies five classes and the relationships among them. In the Cash and Deceased classes, the attribute ‘staffId’ is a foreign key (FK) which is a primary key (PK) in the Staff class. This entry is required to identify the staff that receives the cash or the deceased as the case may be.
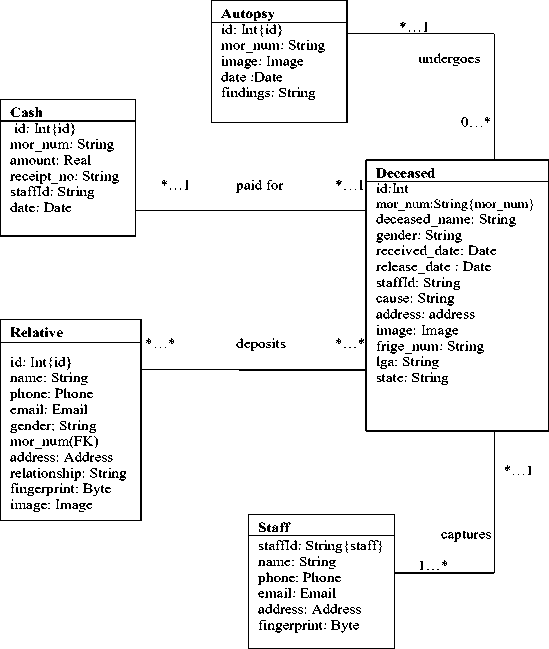
-
Fig. 3. The system class diagram
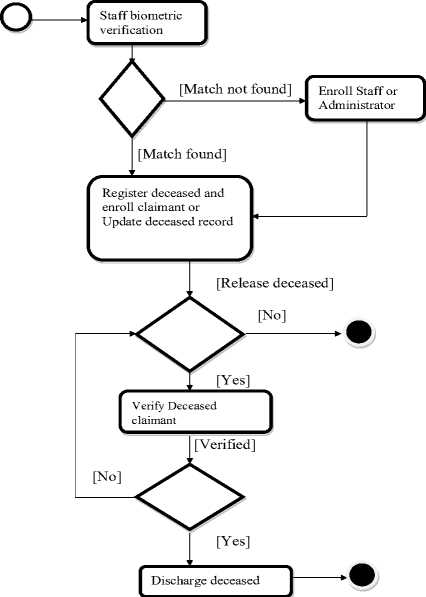
Figure 4 shows the mortuary biometric system Activity diagram. The diagram identifies preconditions and postconditions associated with each activity and of which, they must be satisfied before an activity is performed. These conditions include matching the staff fingerprint with the templates and authenticating the staff, only if a match was found. This biometric verification is also applied to the deceased claimant before a deceased is discharged.
-
Fig. 4. The system activity diagram
-
B. System development tools
The software developed in this study was implemented with a combination of tools:
-
1. NetBeans: Integrated Development Environment (IDE) with Java libraries and compiler. It also provides an interface for drag-and-drop of design elements with Java as the underlying programming language. The system’s graphic user interface (GUI) was designed with the available design tools in the NetBeans IDE.
-
2. Adobe Photoshop: Graphical design environment used to design the system background graphics. Graphical tools like eraser, cropper, color selector, add text, and others unmentioned were used in the system graphic design.
-
3. U.4.U fingerprint biometric documentation: The biometric documentation provided information about the scale
-
4. Apache WAMP Server version 2.4.4: for database management and data storage using MySQL at the backend using Java’s MySQL database connector library (mysql-connector-java-5.1.24-bin).
-
4. Results and Discussion
of acceptance and rejection of a fingerprint sample. This understanding helped the authors to determine the correct, acceptable range of fingerprint sample qualities the biometric device can accept.
The results consist of a set of screenshots from the software system implementation, as presented in Figures 5 – 12. Brief discussions/comments will be made where the meaning of the output on a figure needs further explanation.
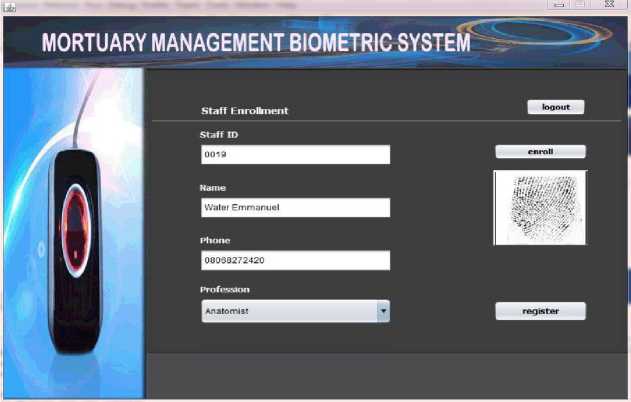
Fig. 5. Staff registration and enrollment interface
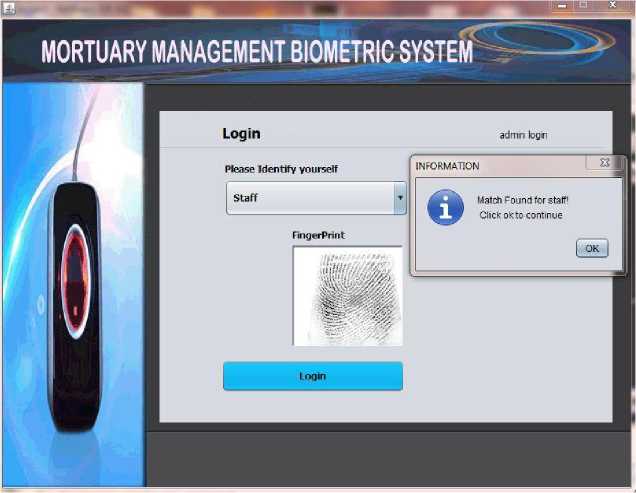
Fig. 6. Staff biometric verification login interface
Figure 7 shows the screenshot of Late Mr. Abasi Kenkwo, with mortuary number ‘S1’; fridge/rack number ‘F1602’; place of death ‘General Hospital, Calabar’; state ‘Cross River’; date of arrival ‘1/1/2016’; age ‘77’; gender ‘Male’; cause of death ‘Cancer’ and address ‘7 abasi st. Calabar’. He was also captured and his photograph uploaded onto the system.
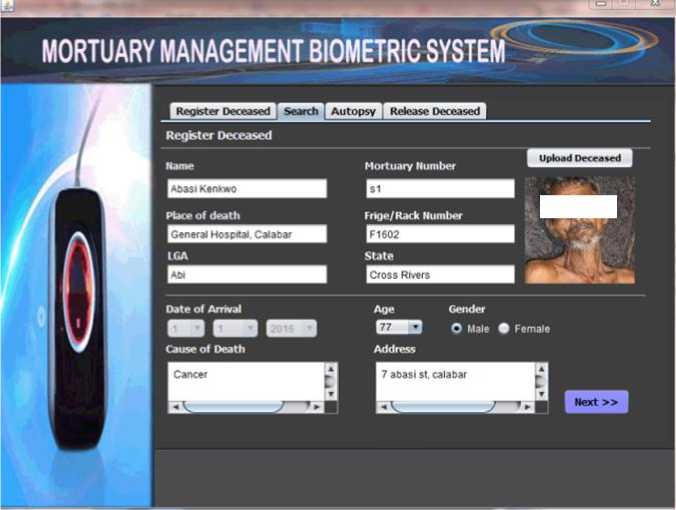
Fig. 7. Deceased registration screenshot
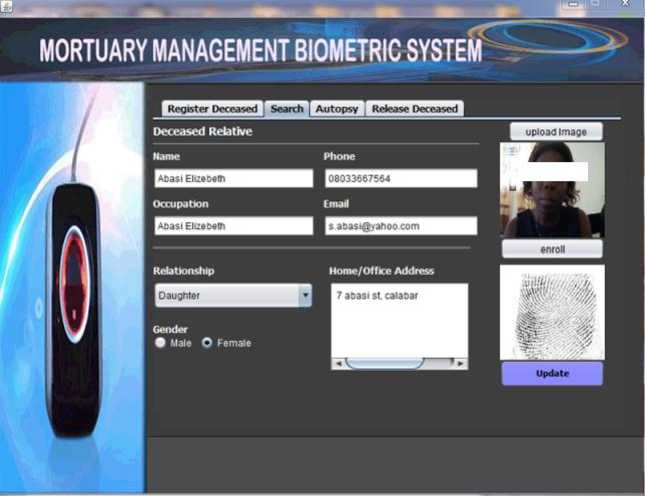
Fig. 8. Deceased relative enrollment and registration interface
Figure 10 shows the screenshot of the search result with the mortuary number ‘s1’. The search interface shows the deceased name, Fridge/Rack number, deceased relative name, phone number, deceased date of arrival, deceased photograph and deceased claimant (relative) photograph. There are also two buttons; one is for cash deposit while the other is for updating the deceased record.
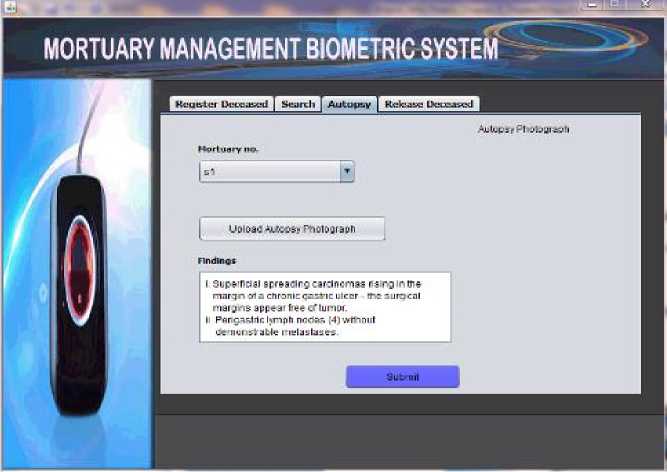
Fig. 9. Autopsy result for mortuary number s1 registration interface
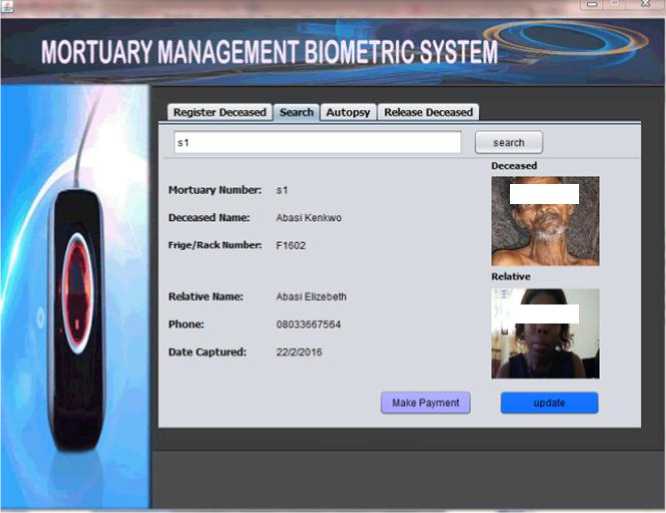
Fig. 10. Deceased search interface using the mortuary number
Figure 11 shows the screenshot of the cash deposit interface. The interface contains the name of the deceased, mortuary number, name of deceased relative and date of arrival. The right part of the interface shows the cash history of the deceased. There are two forms on the interface; one records the amount deposited while the other records the teller number.
Figure 12 shows the screenshot of the deceased claimant fingerprint verification interface. The mortuary number ‘s1’ was selected, and after that, the Verify button was clicked. The deceased claimant supplied her left thumb fingerprint, and the system checked if it matches the fingerprint template saved on the system during the deceased claimant enrollment. The system found a match and checked if there are outstanding debts and there was none, then the system displayed the Release button requesting the system operator to select the release date and press the Release button to discharge the deceased.
Improving Deceased Identification and Claiming System in Mortuaries Using Fingerprint:
A Developing Country Perspective
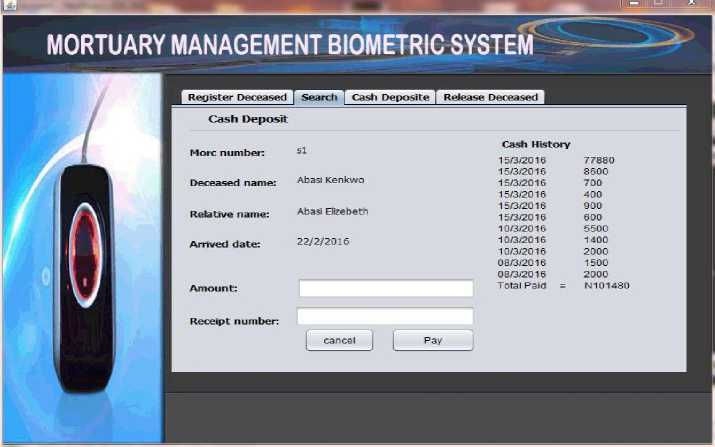
Fig. 11. Cash record and transaction history screenshot
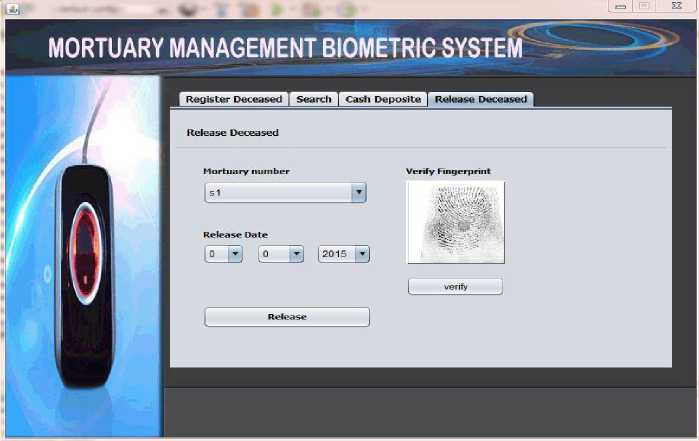
Fig. 12. Deceased claimant biometric verification screenshot
-
a. Summary of result
Table 1. Summary of the result of the mortuary biometric system
Series no.
Morc no.
Date received
Deceased name
Deceased claimant
Biometric
Verific a tion
Date
released
1
2137
09/06/2015
Uzoma Eja
Okoi Ojah
Match
25/06/2015
2
2138
10/06/2015
Eke Solomon
Solomon Ikang
No match
3
2138
10/06/2015
Eke Solomon
Solomon Ikang
Match
04/07/2015
4
2139
11/06/2015
Nse Hogan
Eke uno
Match
26/06/2015
5
2140
11/06/2015
Victor Chukwudi
I.P.O Inap Ubana
Match
15/08/2015
6
2141
11/06/2015
Imaobong Ekong
Ekong Archibong
Match found with outstanding debt
7
2141
11/06/2015
Imaobong Ekong
Ekong Archibong
Match
11/07/2015
The summary of results from this study is shown in Table 1. The data was basic data was provided by the Mortuary Unit of the University of Calabar Teaching Hospital, Calabar – Nigeria. The mortuary biometric system verifies the deceased claimants to ensure the dead are not released to the wrong hands. In Table 1, for example, Solomon Ikang, the claimant of the deceased ‘Eke Solomon’ with the mortuary number of ‘2138’; instead of verifying his left thumb fingerprint, mistakenly supplied his right thumb fingerprint, and the system could not find a match for his right thumb fingerprint. But in serial number ‘3’, Solomon Ikang supplied his left thumb fingerprint and a match was found, which enabled the system to release the deceased to him.
-
5. Conclusion
-
6. Future Scope
Studies on mortuaries by non-morticians have been quite a few due to the anxiety about dead bodies. This has led to a few publications in mortuary systems in developing countries like Nigeria. The mortuary is the last room everybody must enter before going down to mother Earth, and therefore, should be treated with much regard. This study succeeded in identifying the problems of traditional approaches to deceased management, provided technology that analyzed and solved the identified problems, and developed a software system that improved the identification and claiming of dead bodies in mortuaries using biometrics technology.
The mortuary management biometric system was developed using a single algorithm that only U.4.U digital personal fingerprint product can understand. This is a key limitation of this study. This was done to reduce cost; however, if the system must work with other fingerprint devices, there is a need to purchase and install “griaule package” which has several Software Development Kits (SDKs) that support most fingerprint devices. Further research is recommended to focus on deceased identification through teeth biometric identification and verification.
Conflict of Interest: This paper is the result of a study implemented at the University of Calabar Teaching Hospital, Calabar, Nigeria. There are no conflicts of interest.
Acknowledgements
The authors will like to thank the following senior staff of the University of Calabar Teaching Hospital, Calabar, who provided the domain knowledge of this study: Dr. Nnoli Martin, Dr. Cornel Chukwuegbo, Dr. Ebughe Godwin, Dr. Ayo Omotoso, Dr. Theophilus and Dr. David Ushie. We remain grateful for your availability and support.
Список литературы Improving Deceased Identification and Claiming System in Mortuaries Using Fingerprint: A Developing Country Perspective
- J. Kazungu, M. Nanyingi, S. P. Katongole, A. R. Ddm, and L. N. Wampande, ‘The State of Mortuary and Mortuary Services in Public Health Facilities of South Western Uganda’, Int. J. Public Health Res., vol. 3, no. 6, Art. no. 6, Nov. 2015.
- G. D. Mogli, ‘Role of Biometrics in Healthcare Privacy and Security Management System’, Sri Lanka J. Bio-Med. Inform., vol. 2, no. 4, p. 156, Jun. 2012, doi: 10.4038/sljbmi.v2i4.2245.
- M. Khartanovich, ‘The case against traditional passwords — and how biometrics can better secure us’, TNW | Syndication, Oct. 02, 2019. https://thenextweb.com/news/the-case-against-traditional-passwords-and-how-biometrics-can-better-secure-us (accessed Jun. 08, 2021).
- A. K. Jain, A. Ross, and S. Pankanti, ‘Biometrics: a tool for information security: IEEE Transactions on Information Forensics and Security: Vol 1, No 2’, 2006. https://dl.acm.org/doi/abs/10.1109/TIFS.2006.873653 (accessed Jun. 08, 2021).
- S. Rao and K. J. Satoa, ‘An Attendance Monitoring System Using Biometrics Authentication’, Int. J. Adv. Res. Comput. Sci. Softw. Eng., vol. 3, no. 4, pp. 379–383, 2013.
- K. Vignesh, S. S., and A. Sumithra, ‘A Foolproof Biometric Attendance Management System - PDF Free Download’, Int. J. Inf. Comput. Technol., vol. 3, no. 5, pp. 433–438, 2013.
- Mortuary Science, ‘Mortuary science - Wikipedia’, 2011. https://en.wikipedia.org/wiki/Mortuary_science (accessed Jun. 08, 2021).
- Hospital Authority, ‘Hospital Authority Quality and Risk Management Annual Report (Apr 13 - Mar 14) - PDF Free Download’, 2013. https://docplayer.net/14812085-Hospital-authority-quality-and-risk-management-annual-report-2013-2014-apr-13-mar-14.html (accessed Jun. 08, 2021).
- K. Fakhroutdinov, ‘UML 2.5 Diagrams Overview’, 2016. https://www.uml-diagrams.org/uml-25-diagrams.html (accessed Jun. 08, 2021).
- L. Favre, ‘UML and the Unified Process’, 2003. https://ng1lib.org/book/487821/60643d?id=487821&secret=60643d (accessed Jun. 08, 2021).


