IOT Based Burglar Detection and Alarming System Using Raspberry Pi
Автор: Sahana V., Shashidhar R., Bindushree R., Chandana A.N.
Журнал: International Journal of Engineering and Manufacturing @ijem
Статья в выпуске: 6 vol.13, 2023 года.
Бесплатный доступ
In today’s world, security has become the most difficult task. With increasing urbanization and the growth of big cities, the crime graph is also on the rise. In order to ensure the security and safety of our home while we are away, we propose the use of Raspberry Pi to implement an IOT-based burglar detection and alert system. IoT involves the improvement of networks to efficiently acquire and inspect statistics from different sensors and actuators, then send the statistics via Wi-Fi connection to a personal smartphone or laptop. The concept of antitheft devices has been around for decades, but most are only CCTVs, IP cameras, or magnetic doorbells. There is a limited amount of work devoted to face recognition and weapon detection. The design of anti-theft protection devices relies primarily on face recognition and remote tracking. Here, our objective is to improve this system by incorporating weapon detection feature by image processing. The system uses Raspberry Pi, in which a person is only permitted access to the house if his/her face is recognized by the proposed system, and if he/she does not carry any weapons. From the standpoint of security, this system is more reliable and efficient. The proposed system is intended to develop a secure access control application based on face recognition along with weapon detection. By using the Telegram app, the proprietor can monitor the digital camera mounted on the door frame. As a means of improving the accuracy and efficiency of our system, we use the Python language and the Open CV library.
Passive Infrared Sensor (PIR), ARM-11, Raspberry Pi-3, Webcam, DC motor
Короткий адрес: https://sciup.org/15018717
IDR: 15018717 | DOI: 10.5815/ijem.2023.06.03
Текст научной статьи IOT Based Burglar Detection and Alarming System Using Raspberry Pi
One of the major issues that agitates people is home surveillance. The choices for home security are numerous. CCTV cameras are a good illustration. These cameras have the capacity to record and store footage for a full day. However, more work must be put into browsing the videos and looking for any malicious behavior. Additionally, there is no alert system offered by the CCTV system. These two drawbacks of this surveillance technology are possibly its biggest ones. Burglar alerts, fire alarms, and other features are offered by other systems, like American District
Telegraph (ADT) protection. However, if we look at the context of ADT, we see that there is a theft deterrent connected. Additionally, this method doesn't offer privacy. Your everyday activities in the house are recorded minute by minute. There are other systems such as bells, which alert you for people outside the house. So, considering all these issues, there is a need for a better security system for family satisfaction.
In modern times, the world is constantly changing due to the invention of advancing technologies. The growing demand for smart devices has given rise to the concept of connecting everyday objects to existing networks. In recent years, there has been a considerable selection of traditional technologies and biometrics for security needs. Some traditional technologies such as ‘password, key, ID card’ have some disadvantages like if the key or password is revealed, it can be accessed by any unauthorized person. Besides the need for security, there has been an increase in thefts and frauds lately. Today, security and privacy have become critical issues in our daily lives. The "Smart Door Locking System" is a piece of technology that is currently in demand [1]. However, this technology can only prevent unauthorized entry and cannot stop theft and fraud. Therefore, we suggest an Anti-Theft Detection and Alerting System that guards against threats and prevents unauthorized entry in addition to detecting weapons. This device uses less energy and provides better protection against weapons and theft.
In this contemporary era, generations are constantly remaking the world. The Internet has a huge impact on people’s existence and as a result, many advancing technologies such as the Internet of Things (IoT) are emerging rapidly. “Internet of Things” allows us to attach and display real-world gadgets using the Internet, allowing records to be changed between them. The home automation structure adapts to the current way of life. The proposed system is involved in constructing an anti-theft detection and alerting device using the additive interface of Raspberry Pi to send alert messages to the legal proprietor in case of any trespassers attempt to invade the house. In this way, this device prevents unlawful access. In the device we've implemented functionality that detects guns on the access factor of the door. If a person attempts to enter the premises, it can trigger the alarm and capture an image and alert messages may be dispatched to the owner and the police. The theft will be alerted, so he will have no time to start breaking in and destroying the security system.
This paper is organised as follows. Related works are presented in Section 2, where we compare different monitoring applications in various categories, including the 5 themes mentioned above. In Section 3, we briefly introduce the system design along with hardware and software specifications and understand the system workflow and its architecture. Next, in Section 4, we visualize the system results with output screenshots. Finally, we conclude in Section 5 by an outline of future improvements in Section 6.
2. Related Works
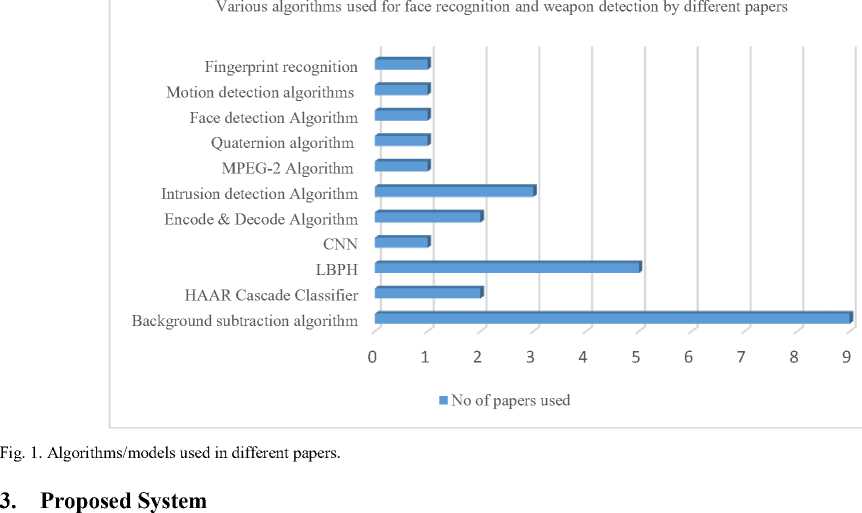
Security is one of the most important issues in every domain, due to an increasing criminal cases/crime in a social and crowded events or isolated areas [2]. Weapons detection and alarming are major applications of computer vision that can solve many different problems and issues that our society is facing. As we know, safety, security and protection of personal property are very important factors in our society that must be addressed as soon as possible, and as there is a great need for technology that can solve this problem, our society needs such a system capable of detecting weapons. The model uses Convolution Neural Network (CNN) and gives results with good accuracy and speed [3]. Accuracy and speed will be the most important factors in the practical application of this model.
-
2.1. Arm-11 Architecture
-
2.2. Raspberry Pi and PIR Sensors
The ARM architecture has a lot of helpful characteristics that set it apart from other comparable processors. They are suitable for use in embedded applications because of their small size and low power usage. The document "The ARM Architecture" by Leonid Ryzhyk taught us about the benefits of ARM processors in the area of embedded systems as well as about ARM processor characteristics.
With the help of the Internet of Things and an embedded Linux operating system with an ARM11 architecture, Sushma.N. Nicha and Prof. J.K. Singh [4] have abstracted the Smart Manager electronic device. They have used a real-time video tracking device and acquired the information. In this device, they used many PIR, temperature, humidity sensors. Before turning off, the gadget requests user authentication. When a person is detected, the device transmits information to a server or the user's smartphone.
Dr. S. Kanagasuba Raja et al. [5] has used Raspberry Pi for home automation and protection devices. In this article, the authors have implemented a guard that detects intrusions and captures video for later viewing. Additionally, household appliances have been automated. Users can remotely turn on and off household appliances.
A security device with a camera, Raspberry Pi, and proximity sensor was created by K Saravana Kumar et al. [6]. When a person is detected by the proximity sensor, the camera starts, takes a picture, uploads it to a drop box, and sends an SMS to the user alerting them to the intrusion. A few advantages have been explored, including portability and cost efficiency. The authors found that the system is helpful for home security.
The intelligent surveillance system is presented by Ms. Renuka Chuimurkar and Prof. Vijay Bagdihave [7] which is driven by a Raspberry Pi, PIR sensors, and mobile devices. Smoke alarms have also been used by authors to identify fires. The user will be informed of an intruder or a fire following the capture of a picture on their workstation via Wi-Fi. They used a smoke detection algorithm and a background subtraction algorithm to identify motion. They have cited benefits such as reliability and privacy.
Dhadiwal Kalpesh Paraskumar et al. [8] have designed and implemented a protection device using a Raspberry Pi, IR sensors and a digital camera. IR sensor detects the intruder, the camera takes a picture of the intruder and a microphone records the voice of the character. The captured picture in combination with the recorded voice could be sent to owner’s mobile phone. This article also discusses the pros and cons of this device. The authors concluded that this device facilitates real-time monitoring of household conditions.
-
R. Chandana et al. [9] have carried out tracking and surveillance device using think and communicate with the assist of Raspberry Pi. They have used Gyroscopic sensor to track character’s movement. If motion is detected, digital digicam takes a photo and send the image to the owner’s email id. They also have mentioned that device was of little importance. The authors have concluded that the device was essential for conservation purpose.
-
2.3. GSM Alert
-
2.4. Face Detection Techniques
-
2.4.1. Background Subtraction Algorithm
-
2.4.2. Haar Cascade Classifier
The GSM module is in charge of communicating instructions from the mobile station to the microcontroller as well as information from the microcontroller to the mobile station.
In order to log data off-site on FTP (File Transfer Protocol) storage, real-time implementation is accomplished by using a GSM (Global System for Mobile Communication) modem for SMS (Short Message Service) notice supplemented by e-mail notification. The HAYES AT commands developed by Dennis Hayes are the particular programming language, or collection of commands, used by GSM modems.
The goal of May, Z. B. [10] is to create and execute a real-time warning system using GSM technology and motion detection. The system architecture serves as a platform that gives users room for customization and freedom. With the suggested system, the implementation of pricey monitoring products for entry means and alert systems is successfully avoided. It is able to track motion and take pictures, transmit SMS notifications via GSM modem that mimic real-time simulation, and attach email notifications to the image file.
When a character approaches a door, a protection device created by Md. Nasimuzzaman Chowdhury et al. [11] will send an email and a tweet to the proprietor, who can then use a digital camera to see the character up close. Character pictures are taken and sent via email and Twitter. They have claimed that the owner can control the door remotely. They have arrived at the conclusion that the tool effectively blocks illegal entry.
The face detection models available in the literature can be broadly classified into three parts: Background subtraction algorithm, Haar Cascade Classifier and LBPH algorithm.
A real-time monitoring and security system using Raspberry Pi that enables users to monitor from anywhere has been demonstrated by Khushbu H Mehta and Niti P Gupta [12]. According to the authors, the system uses a background subtraction algorithm to identify faces and checks for them whenever motion is detected. If a face is found, it is then stored locally. The authors have come to the conclusion that the system can track users remotely and identify faces.
Using the Haar Classifier, Visakha, K., and Prakash, S. S. [13] created Detection and Tracking of People in a Video. Three steps make up a video monitoring system: object identification, object detection, and object decision-making. Hundreds of views of various samples of individuals (referred to as positive samples) and random images without any humans are used to train Haar Classifiers. (called negative samples). It can be used on the area of interest in each extracted image after training. The result of this procedure will be "1" if humans are probably present there, and "0" otherwise. This article's goal is to find individuals in a scene and keep track of them for as long as they are there. The authors have designed Detection and Tracking of People in a video using Haar Classifier. People can be tracked and traced through video clips that can be pre-recorded or streamed live.
-
2.4.3. LBPH Algorithm
-
2.5. Weapon Detection Techniques
-
2.5.1. Convolution Neural Network Approach
Using Local Binary Patterns Histogram (LBPH) face recognizer, Li Wang and Ali Akbar Siddique [14] have developed a facial recognition system for drone-based flight and surveillance uses. The suggested system makes use of the idea of facial recognition by identifying the person in the acquired frame using a pre-trained LBPH Face Recognizer. A live video feed was caught by a camera mounted on a drone. The video data that has been collected is processed by an integrated Raspberry Pi module. The algorithm has an accuracy rate of 89.1% for finding the desired individual.
The most common weapon detection model available in the literature is CNN.
An internet-of-things (IoT)-based smart home security system that uses computer vision for facial recognition and weapon detection was developed by M. Nandhini, M. Mohamed Rabik, Kiran Kumar, and Ashish Brahma [15]. Wherein it employs CNN approach for weapons detection.
A portable intrusion detection system with a Raspberry Pi camera was suggested by Khan A. Sultana and Tan a. Wahid et al. [16] to identify thefts. It can identify an attacker who is carrying a knife and a gun. Here, the camera sensor can create better monitoring services due to the event-driven approach. To achieve improved results, patterns are watched. Additionally, what is visible in the field of vision is watched. The camera will be ready using an event-driven method. It creates a framework that is power-efficient and only reacts when the target event is recognized to be active. They used a CNN model in this research to address this problem statement. For the purpose of detecting criminal activity in real time, the framework combines image analysis, AI computer vision, and network communication techniques. Knives and guns are used as training pictures for the CNN model. An 8:2 ratio is given to training and testing for validation and testing.
A framework for identifying objects (knives, guns, or any metal) on a moving person was suggested by Kepin Yu et al. [17]. In the conventional method, passengers must wait at the airport gate for the security check. Traffic congestion and delays will result from this. This article aims to identify suspicious objects in the W-band using AI. There are two levels in this system: primary and secondary. If the object is within 15 meters, W-band radar is used to look for suspicious objects during primary screening. In the secondary level of control, the suspicious objects and individuals from the primary level are recognized. Methods called Recurrent Convolution Neural Networks (R-CNN) are used to identify and categorize images. Here, a CNN model is trained and tested using four different kinds of suspicious objects (knife, scissors, forks, and bottle). CNN algorithms are also trained using noisy and dark images to lower the false-positive rate. (FR).
Table 1. Summarized composition of literature survey for Surveillance Systems.
|
SL no |
Paper Ref |
Year |
Techniques/Algorithms |
Tools used |
|
1. |
[1] |
May 2020 |
Fingerprint recognition |
Arduino Nano, Bluetooth HC 05, Servo motor, broken lock, smartphone |
|
2. |
[14] |
May 2020 |
Local Binary Patterns Histogram (LBPH) Face recognizer |
Raspberry Pi, Camera |
|
3. |
[15] |
November 2020 |
CNN model RetinaNet object detection model |
Raspberry Pi, Pi Camera, Servo motor, smartphone |
|
4. |
[13] |
July 2018 |
Haar Cascade Classifier |
Raspberry Pi, Camera |
|
5. |
[7] |
January 2016 |
Background subtraction and smoke detection Algorithm |
Raspberry Pi, smoke sensor, Camera |
|
6. |
[37] |
February 2016 |
MPEG-2 Algorithm |
Raspberry Pi, Camera |
|
7. |
[12] |
February 2016 |
Background subtraction Algorithm |
Raspberry Pi, OpenCV |
|
8. |
[36] |
February 2016 |
Encode & Decode, Algorithm for video streaming |
Raspberry Pi, Camera, 3g Dongle |
|
9. |
[6] |
February 2015 |
Intrusion detection Algorithm |
Raspberry Pi, Camera, Smart Phone |
|
10. |
[38] |
April 2015 |
Alarm switch, Algorithm for video streaming |
Raspberry Pi, sensor,3g Dongle |
|
11. |
[35] |
May 2015 |
Motion detection algorithms |
Raspberry Pi, camera, sensor |
|
12. |
[9] |
July 2015 |
Quaternion algorithm |
Raspberry Pi, I2C, Camera, |
|
13. |
[4] |
July 2015 |
Encode & Decode, Algorithm for video streaming |
Raspberry Pi, sensors, Camera |
|
14. |
[5] |
August 2014 |
Intrusion detection Algorithm |
Raspberry Pi, Camera, sensor |
|
15. |
[8] |
November 2014 |
Intrusion detection Algorithm |
Raspberry Pi, Camera, Microphone |
|
16. |
[11] |
November 2013 |
Face detection Algorithm |
Raspberry Pi, Camera, sensor |
The conventional door lock systems have many drawbacks, including the chance of forced entry if the homeowner loses his key, which happens occasionally. An intruder has the ability to enter the home without authorization if the password or key is disclosed to him. We have suggested a system that will enable us to track unauthorized users and all weapons in order to address the aforementioned issues. With this system, which we created using a Raspberry Pi, a person is only permitted to enter the home if the system can identify his or her face and they are not carrying any weapons. The user's picture will be taken with a digital camera and compared to an image that is already stored in a database. After a face scan, if the person is authorized, a weapon detection will be done; if they don't have any weapons, the door will open; however, if the person is not authorized or carries a dangerous weapon, an alarm will be produced, and the owner will be notified via Telegram.
The block diagram of IOT Based Burglar Detection System using Raspberry PI is shown in Fig. 2.
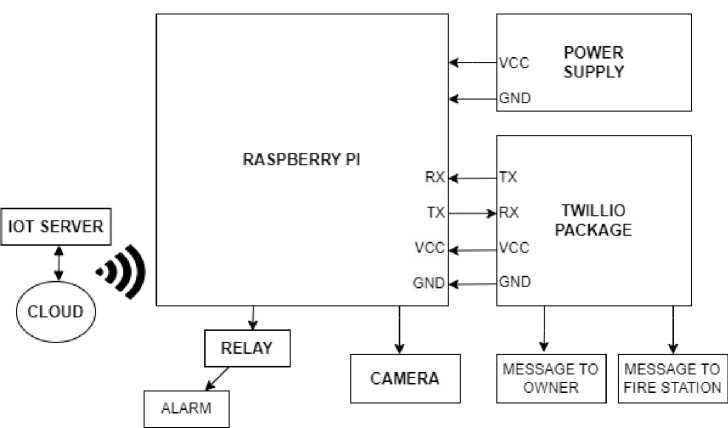
Fig. 2. Block Diagram of Burglar and Alerting Security System.
For this burglar alarm system to operate effectively, a combination of hardware and software components is needed. Firstly, Telegram will be used for the software component. When the stranger tries to enter, the system activates the monitoring function, takes a snapshot and sends it to the proprietor, and notifies the owner via Telegram.
The image processing methods in this project were coded using OpenCV. It is an open-source, Raspberry Pi-compatible computer vision software.
A Raspberry Pi 3 model B, a solenoid electric door locker, a keypad, a 1602 LCD monitor, an ultrasonic sensor module, a digital camera module, and a mini buzzer are used as the hardware components. The entire task will be managed by the Raspberry Pi. When an individual is detected by an ultrasonic sensor approaching the entrance, the camera is activated to begin taking pictures of their faces and comparing them to a database. If the detected individual is determined to be an outsider, the system notifies the home's proprietor via telegram over Wi-Fi and begins sounding the buzzer.
-
3.1. System design
-
3.1.1. System Hardware
-
3.1.1.1. Raspberry Pi 3 Model B
-
-
3.1.1.2. Raspberry Pi Camera:
-
3.1.1.3. IR Sensor:
Basically, the design and development of this system are divided into two main parts: System hardware and System software. These both which make up the surveillance system are intended to work together. When processing images, the software must perform mathematical calculations in order to validate the user's identity. The hardware must also be capable of processing the entire system flow efficiently.
For the system development, several hardware components have been created.
Table 2. Hardware components required
|
Item |
Quantity |
Remarks |
|
Raspberry pi 3 model B |
1 |
The entire system movement will be processed by a single board computer. |
|
Raspberry pi camera module |
1 |
Take a picture |
|
Buzzer |
1 |
Alert the visitor and state the situation |
|
Solenoid locker |
1 |
Lock and unlock the door |
|
5V relay module |
1 |
Control larger current solenoid |
|
Resistor |
1 |
Reduce the power to protect the component. |
|
Breadboard |
1 |
Create a foundation for building a circuit. |
|
Ultrasonic sensor |
1 |
Determine the presence of person in front of the door |
|
18650 battery |
2 |
Ensure the solenoid has enough power to operate. |
Both Linux-based and non-Linux-based open source operating systems were used in the development of the Raspberry Pi 3 Model B. The Raspberry Pi Foundation created the third generation of small single-board computers, including this development board. The third generation was selected for this endeavour because older Raspberry Pi models require the installation of a Wi-Fi connector in order to connect to the internet. A faster processor, more RAM, and an integrated Wi-Fi chipset are all features of the Raspberry Pi 3 model B over its predecessor.
The Raspberry Pi module and Pi camera serve as the video module. This Raspberry Pi camera module is used to take pictures and transmit them to the Raspberry Pi module. Its resolution is 5 megapixels, and its still image resolution is 2592 x 1944.
An electronic gadget, which produces heat in order to detect specific environmental elements. Infrared cameras gauge an object's heat and track its motion.
This sensor can identify objects up to 5 feet away. One of the most fundamental and widely used sensor modules in electronic devices is the infrared sensor circuit. Obstacle detection is one of the prevalent real-time uses for the sensor, which works similarly to human visual senses.
-
3.1.1.4. Buzzer:
-
3.1.1.5. Solenoid Locker:
-
3.1.1.6. HC-SR04 Ultrasonic Sensor:
-
3.1.2. System Software
-
3.1.2.1. Python IDE
-
-
3.1.2.2. OPEN CV
-
3.1.2.3. Telegram
-
3.2. System architecture
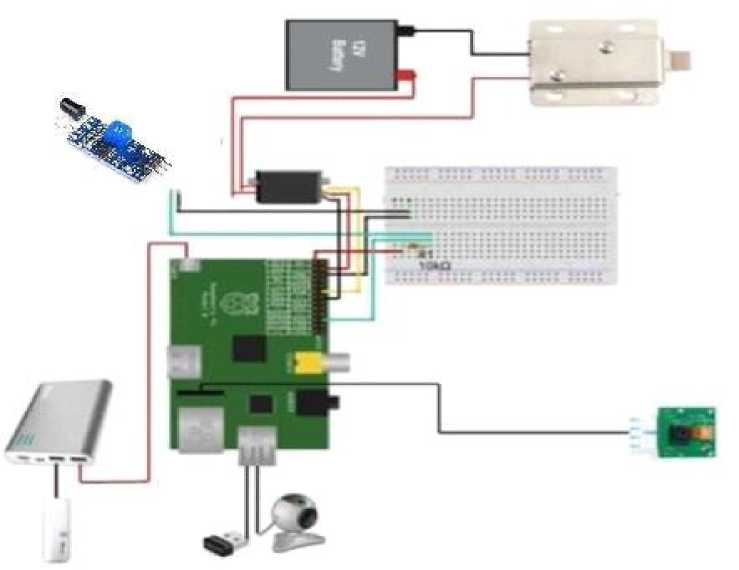
Buzzer is used to notify the user. Each time the keypad is pressed, there will a “beep”. It also indicates the locked and unlocked status of the door. It notifies the user when the door is unlocked and locked.
This electromagnetic locker needs a high current to start. It requires at least 300mA and 6.5V. A 9V battery only has 200mA, not enough to activate. In order to provide enough power and reduce frequent battery replacement and for provide an ideal experience, two 18650 rechargeable batteries are used to drive this solenoid. The electromagnetic locks are used to push and pull the locker to unlock and lock the door.
Because it is affordable and can fulfil the project's requirements, this project selected the HC-SR04 Ultrasonic Sensor. It is employed to identify human presence. This is a crucial component for improving the system's energy efficiency and lowering its energy usage. Only when a person is identified at a specific distance is the system is turned on.
Python IDLE is a free and open source computing tool and an IDE (Integrated Development Environment) for Python language. Python IDE will be used for programming of this system, including facial recognition and weapon tracking using OpenCV library.
Open CV (Open Source Computer Vision) is a software library for computer vision and machine learning. The goal of Open CV is to provide a common infrastructure for computer vision applications while also accelerating the use of machine perception in commercial goods. Open CV, as a BSD licensed product, makes it simple for businesses to use and change the code. It is available for both business and non-commercial use at no cost.
Telegram is an internet instant messaging service that can be accessed via computer and mobile phone. Third-party programmers can create their own bots on Telegram. With the bot, it can respond to various commands programmed by the creator. It is used in this project to deliver an automatic notification to the user when the system is triggered. It can also be used to manage the system by sending commands to it.
Fig. 3. System Architecture.
A system's structure, behavior, and overall viewpoint are all defined by its system architecture, which is a conceptual model. An architecture description is a formal explanation and representation of a system that is set up to facilitate analysis of its components and behavior.
The system architecture starts with upward push in the temperature in the outside medium. Then the digital digicam turns on and takes a picture for face recognition. Face recognition will start by comparing the captured image with the dataset via the HAAR cascade ruleset. In the system of face recognition, if the captured picture is not in the dataset, a warning message is sent to the proprietor via Telegram. Then, when returning to the system the digital digicam turns on and takes a picture and the face recognition system starts to function again. The system will run until a captured image is found in the dataset. If the captured photo is in the dataset, the weapon detection function comes into play. If the captured person is observed with guns or other weapons then the CNN set of rules detects and acknowledges the sort of weapon the person is carrying and sends the alert message to proprietor via telegram along with buzzer alarming sound. Again, after returning back to system the digital digicam opens and captures the picture after which face recognition system and weapon detection begins to function. These systems will function till the captured picture is found located in datasets along with no guns or any other weapons. If the person captured isn’t found with guns in the dataset can get admission to go into the house. The simplest manner to go into the house without proprietor’s permission is, to have the person image in datasets and shouldn’t have guns alongside identical image.
3.3. System workflow
 4. Result
4. Result
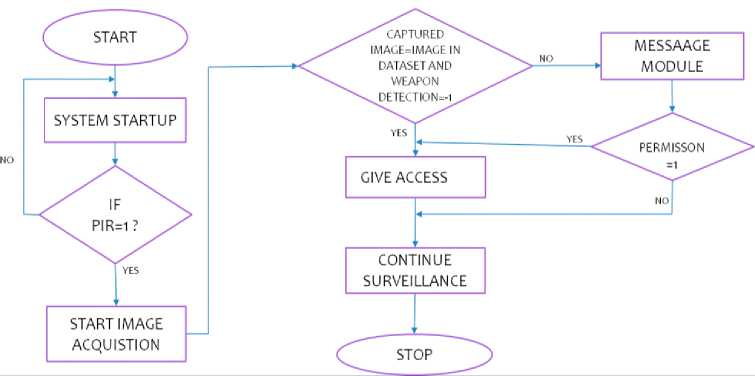
Fig. 4. Workflow Diagram.
The actions that define a task or how work should be done are shown in a workflow diagram. An illustration of the workflow shows how duties will move between resources.
The work flow process begins with system start up. If the PIR sensor input is ZERO or LOW, that means there is no rise in temperature on external medium. So, there is no further action to take about then, the PIR sensor waits till to get change in external medium. If the PIR sensor detects any noise/rise in temperature within the range of 20ft, then the PIR sensor mode will be activated (IF PIR=1).
IF PIR=1 is true, then the camera stats with image acquisition. Capturing of image and face detection is done by HAAR cascade algorithm. The captured image compares and verifies with the images in datasets. If the captured person, found with weapons/unusual activities then the CNN algorithm detects and recognizes what type of weapon. If “captured image=image in dataset and weapon detection=-1” is true the person gets access and continue surveillance will stop. Hence person can enter the home by unlocking the door. If “captured image=image in dataset and weapon detection=-1” is false then a message goes to the owner of the home through Telegram and photo through email.
If owner gives the permission as ‘1’ through telegram the person gets access to unlock the main door and the continue surveillance stops. If the owner denied the permission or gave the permission as ‘0’ then the person can’t get access, the continue surveillance will stop. Hence the person may leave or have to wait till the owner arrives.
The section represents the experimental findings of the proposed system with screenshots attached. Below figure demonstrates the face recognition of the known person.
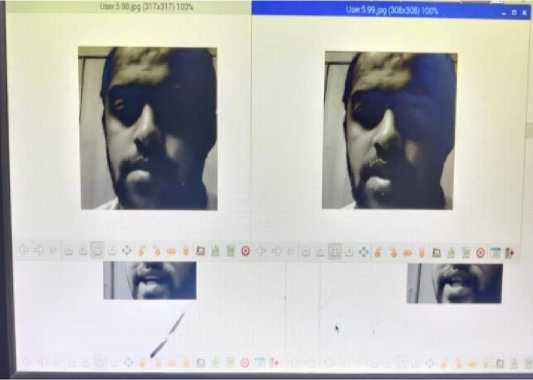
Fig. 5. Screenshot of Face Detection of known person.
The output of the unique face id of the image captured is shown in the Fig. 6.
Fig. 6. Screenshot of output of Face Id of the image captured.
Below are the screenshots of the known and unknown person recognized by the model. Fig. 7. shows the recognition of faces of the known person stored in the database.
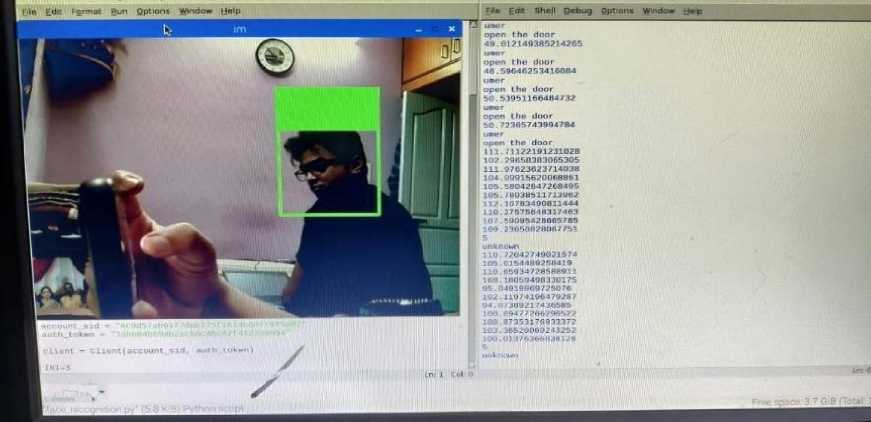
Fig. 7. Screenshot of face recognition of known person.
Fig. 8. shows the face recognition of the unknown person after processing the image using OpenCV approach.
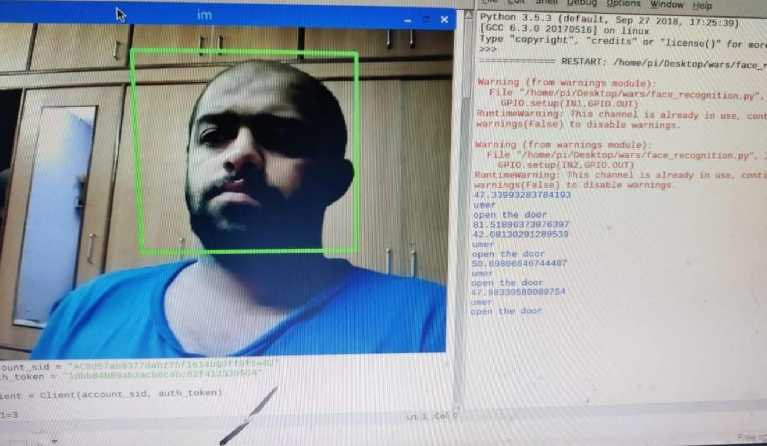
Fig. 8. Screenshot of Face Recognition of Unknown person.
Below figure shows the notification alerts sent to the owner through Telegram on detecting unknown person with weapons
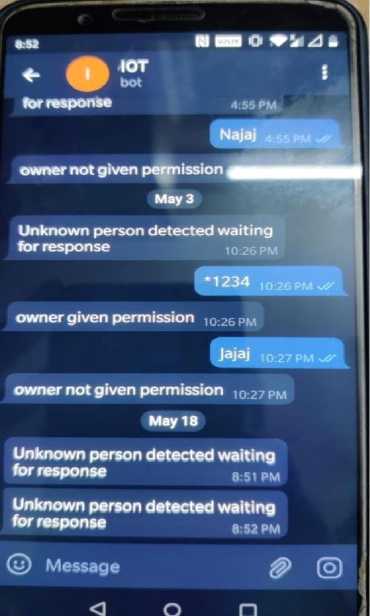
Fig. 9. Screenshot of message notification through Telegram.
The screenshot below shows the face recognition along with the weapon detection. As shown in Fig. 10. , a stranger was found in camera with the hammer. The system identifies him as an intruder and the image of the intruder along with hammer is identified.
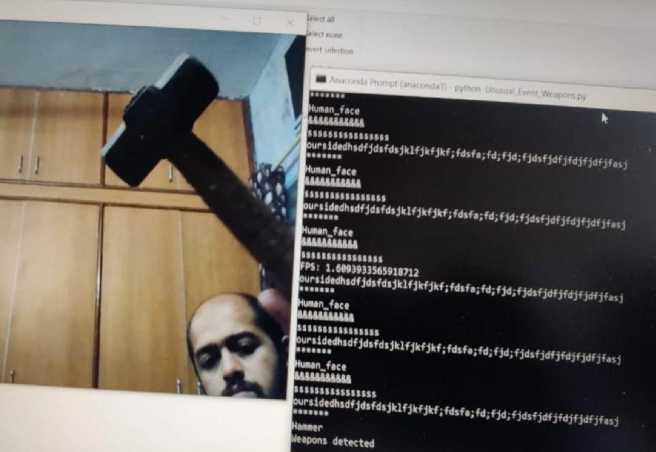
Fig. 10. Screenshot of person with weapon detected.
The connection of pi camera with Raspberry pi 3 module is shown in Fig. 11.
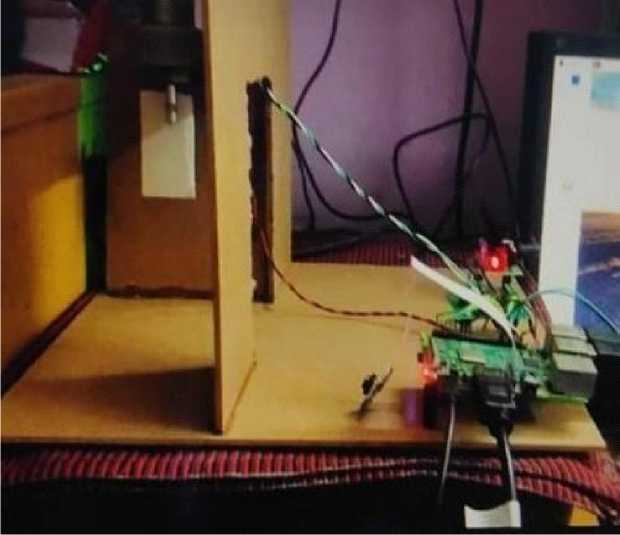
Fig. 11. pi camera with raspberry pi3.
Below figure shows the experimental setup, which includes all the hardware components used for the functioning of our system such as Raspberry pi, pi camera, PIR sensor, electric solenoid door lock, buzzer and connection wires.
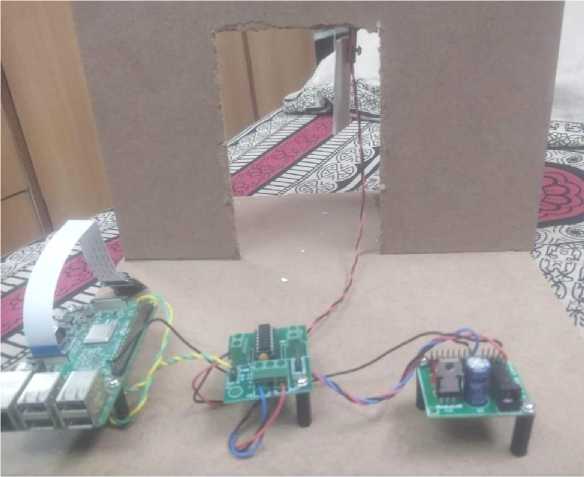
Fig. 12. Experimental setup.
Fig. 13. shows the connection of alert buzzer to the electric solenoid door locker.

Fig. 13. Alert Buzzer.
5. Conclusion
Face recognition in recent times has been broadly used on many regions specifically on Safety. The “Anti-Theft Detection and Alerting System” is used to put into effect the face recognition and weapon detection methodologies together for preserving the residence safety. We have constructed a running version of our designed system which detects and acknowledges the face of a stranger with the usage of Haar Cascade set of rules and in addition, it detects weapon with the usage of CNN set of rules. If the person is resident and no weapon is detected, he/she is authorized to go into the house. Suppose if he/she is no longer recognized, an alert message will be dispatched to the proprietor right away via Twilio bundle and Telegram application. In this contemporary era, generation is continuously converting the global. The Internet has a massive effect on people’s existence and as a result, plenty of new technologies like IoT are rising rapidly. ‘Internet of Things’ lets in us to attach and reveal actual global gadgets with the assist of the internet, which allows for changing records among the gadgets. Home Automation structures are apt for current lifestyle. The objective is to build a low-cost security system to resolve market product problems. In response to the above issues, a self-developed face recognition and weapon detection based anti-theft security system have been designed. It can help to solve the issues such as, it can trigger an alarm and capture the photo and send to proprietor when a unknown person is detected in front of door. The theft will be alerted so he got no time to start breaking in and breaching the security system. It can also assist solve the problems like a unknown person is detected with any weapon in the front of the door. This enables the proprietor to reply right away to the incident without regretting for the later and additionally the captured pics might be beneficial for the investigation. The proper hardware and software components are used as they're the vital issue to make this project. The hardware used is Raspberry Pi three version B, linked to numerous sensors and additionally linked to the Telegram cellular application. It makes use of Python Open CV and Raspbian OS for implementation.
6. Future Scope
Even though, the very last layout become determined as satisfactory, it become found out there's constantly scope for improvement. As, we've used HAAR cascade set of rules for face recognition which offers 95% accuracy and for weapon detection the use of CNN set of rules which offers 80% accuracy. In future we can also use algorithms which offers us greater accuracy. The system is not entirely error-proof despite providing fail-safe method. Some of the aspects worth nothing for future improvements are as follows:
-
• Aliveness recognition system: While the development of the facial recognition system, it was discovered that the system could be tricked by using the owner's photo to access it. Therefore, when testing a system, a live detection system is included. Depending on whether the detected face is from your mobile phone or from your own, the system can determine if the face is valid or invalid. However, the downside of this system is that it does not generalize well to all faces. It can also track eye blinks, motion detection, pixel changes and 3D depth awareness. To determine whether a face is a 2D image or a 3D volumetric object, a camera with a depth sensor is needed. It was abandoned in the final system design due to the lack of suitable materials and poor memory of the procedure. Nevertheless, it plays an important role in upgrading the system.
-
• Non frontal detections: The final model was able to detect only frontal faces. Alternate models using DeepFace may also allow non-frontal faces. By combining the description of this model with the proposed one, non-frontal facial recognition can be obtained with very low latency.
-
• Camera tampering detection: This detection can be made by image processing and prediction of image change rates.
-
• Indoor Surveillance: The encroachment and security methods discussed above can also be used in indoor surveillance using cameras to monitor babies and verify that pets are safe indoors. absence of parents.
-
• Fire Alarm: This system could be improved to alert homeowners if a fire breaks out in the home in their absence. This facilitates immediate evacuation.
-
• Sensor Nodes: To make sensors mobile and globally accessible, separate IP addresses can be assigned to their wireless and 4G LTE adapters. It helps users to access their data worldwide.
-
• Drone surveillance: The systems can be integrated into drones for short-range surveillance operations and recognize proof of individual from databases.
Список литературы IOT Based Burglar Detection and Alarming System Using Raspberry Pi
- K. Gupta, N. Jiwani, M. H. Uddin Sharif, M. A. Mohammed and N. Afreen, "Smart Door Locking System Using IoT," 2022 International Conference on Advances in Computing, Communication and Materials (ICACCM), Dehradun, India, 2022, pp. 1-4, doi: 10.1109/ICACCM56405.2022.10009534.
- A. B. P. ,. A. M. ,. D. N. G. Akash Kumar. K. S, "Weapon Detection in Surveillance System," IJERT, 2021.
- Francisco Pérez-Hernández, Siham Tabik, Alberto Lamas, Roberto Olmos, Hamido Fujita and Francisco Herrera, "Object Detection Binary Classifiers methodology based on deep," ELSEVIER, 2020.
- Sushma.N.Nichal, Prof.J.K.Singh, “Raspberry pi Based Smart Supervisor using Internet of Things (IoT)”,International Journal of Advanced Research in Electronics and Communication Engineering (IJARECE) Volume 4, Issue 7, July 2015, ISSN: 2278 – 909X.
- Dr. S. Kanaga suba raja, c. Viswanathan, dr. D. Sivakumar, m.vivekanandan, “Secured Smart Home Energy Monitoring System (SSHEMS) using raspberry pi”, 10th august 2014. Vol. 66 no.1 issn: 1992-8645
- K Saravana Kumar, Jestin Thomas, Jose Alex, Raag Malhotra, “Surveillance System Based On Raspberry Pi for Monitoring a Location Through A Mobile Device”, International Journal of Advanced Multidisciplinary Research 2(3): (2015): 103–108 ISSN: 2393-8870
- Ms. RenukaChuimurkar, Prof. Vijay Bagdi, “Smart Surveillance Security &Monitoring System Using Raspberry PI and PIR Sensor”, International Journal of Scientific Engineering and Applied Science (IJSEAS) – Volume-2, Issue-1, January 2016 ISSN: 2395-3470.
- Dhadiwal Kalpesh Paraskumar, Abhishek Pandey, Dharmendra Kumar, Pankaj Kumar, DeepaliJavale, “Home Security System”, International Journal of Inventive Engineering and Sciences (IJIES), Volume-2 Issue-12, November 2014 ISSN: 2319–9598
- R.Chandana, Dr.S.A.K.Jilani, Mr.S.Javeed Hussain, “Smart Surveillance System using Thing Speak and Raspberry Pi”, International Journal of Advanced Research in Computer and Communication Engineering Vol. 4, Issue 7, July 2015 ISSN (Online) 2278-1021 ISSN (Print) 2319-5940
- May, Z. B. (2012, November). “Real-time alert system for home surveillance”, in 2012 IEEE International Conference on Control System, Computing and Engineering (pp. 501-505). IEEE. https://doi.org/10.1109/ICCSCE.2012.6487197
- Md. Nasimuzzaman Chowdhury, Md. ShibleeNooman, SrijonSarke, “ Access Control of Door and Home Security by Raspberry Pi Through Internet”, International Journal of Scientific & Engineering Research, Volume 4, Issue 11,November-2013 ISSN 2229-5518
- Khushbu H Mehta, Niti P Gupta, “Vision Based – Real Time Monitoring Security System for Smart Home”, Vision Based – Real Time Monitoring Security System for Smart Home, Vol. 4, Issue 2, February 2016 ISSN(Online): 2320-9801 ISSN (Print): 2320-9798
- Visakha, K., & Prakash, S. S. (2018, July). “Detection and Tracking of Human Beings in a Video Using Haar Classifier”. In 2018 International Conference on Inventive Research in Computing Applications (ICIRCA) (pp. 1-4). IEEE. https://doi.org/10.1109/ICIRCA.2018.8597322.
- Zhang Y, Xu L, Zhang Y. Research on hierarchical pedestrian detection based on SVM classifier with improved kernel function. Measurement and Control. 2022;55(9-10):1088-1096. doi:10.1177/00202940221110164
- M. Nandhini, M.Mohamed Rabik, Kiran Kumar, Ashish Brahma, “Iot Based Smart Home Security System with Face Recognition and Weapon Detection using Computer Vision”. International Journal of Innovative Technology and Exploring Engineering (IJITEE), ISSN: 2278-3075 (Online), Volume-10 Issue-1, November 2020.
- T. Sultana and K. A. Wahid, "IoT-Guard: Event-Driven Fog-Based Video Surveillance System for Real-Time Security Management," in IEEE Access, vol. 7, pp. 134881-134894, 2019, doi: 10.1109/ACCESS.2019.2941978.
- K. Yu et al., "Design and Performance Evaluation of an AI-Based W-Band Suspicious Object Detection System for Moving Persons in the IoT Paradigm," in IEEE Access, vol. 8, pp. 81378-81393, 2020, doi: 10.1109/ACCESS.2020.2991225.
- A. Singh, T. Anand, S. Sharma and P. Singh, "IoT Based Weapons Detection System for Surveillance and Security Using YOLOV4," 2021 6th International Conference on Communication and Electronics Systems (ICCES), Coimbatre, India, 2021, pp. 488-493, doi: 10.1109/ICCES51350.2021.9489224.
- Jahnavi, S., & Nandini, C. (2019, March). Smart Anti-Theft Door Locking System. In 2019 1st International Conference on Advanced Technologies in Intelligent Control, Environment, Computing & Communication Engineering (ICATIECE) (pp. 205-208). IEEE
- Liu, Z., Wang, M., Qi, S., & Yang, C. (2019). Study on the anti-theft technology of museum cultural relics based on Internet of Things. IEEE Access, 7, 111387-111395.
- A. Pawar and V. M. Umale, "Internet of Things Based Home Security Using Raspberry Pi," 2018 Fourth International Conference on Computing Communication Control and Automation (ICCUBEA), Pune, India, 2018, pp. 1-6, doi: 10.1109/ICCUBEA.2018.8697345.
- R. Yu, X. Zhang and M. Zhang, "Smart Home Security Analysis System Based on The Internet of Things," 2021 IEEE 2nd International Conference on Big Data, Artificial Intelligence and Internet of Things Engineering (ICBAIE), Nanchang, China, 2021, pp. 596-599, doi: 10.1109/ICBAIE52039.2021.9389849.
- V. Patchava, H. B. Kandala and P. R. Babu, "A Smart Home Automation technique with Raspberry Pi using IoT," 2015 International Conference on Smart Sensors and Systems (IC-SSS), Bangalore, India, 2015, pp. 1-4, doi: 10.1109/SMARTSENS.2015.7873584.
- D. Yang, Abeer Alsadoon, P.W.C. Prasad, A.K. Singh, A. Elchouemi, “An Emotion Recognition Model Based on Facial Recognition in Virtual Learning Environment”, Procedia Computer Science, Vol. 125, pp.2-10, 2018.
- N. Kazanskiy, V. Protsenko, P. Serafimovich, “Performance analysis of real-time face detection system based on stream data mining frameworks”, Procedia Engineering, Vol. 201, pp. 806-816, 20
- Ratnawati Ibrahim, "Study of Automated Face Recognition System for Office Door Access Control Application", IEEE 2011
- Fan X., Zhang F., Wang H., Lu X., “The System of Face Detection Based on OpenCV”, IEEE Control and Decision Conference (CCDC), 2012 24th Chinese,648- 651, 2012.
- R. Lienhart, J. Maydt, “An extended set of Haar-like features for rapid object detection”, Vol. 46 Issue 3, pp. 518– 545. Dec. 2004.
- Archana, T., Venugopal, T., & Kumar, M. P. (2015, January). Multiple face detection in color images. In Signal Processing and Communication Engineering Systems (SPACES), 2015 International Conference on (pp. 82-85). IEEE.
- Jose, A. C., & Malekian, R. (2017). Improving smart home security: Integrating logical sensing into smart home. IEEE Sensors Journal, 17(13), 4269-4286.
- Patchava, V., Kandala, H. B., & Babu, P. R. (2015, December). A smart home automation technique with raspberry pi using iot. In 2015 International conference on smart sensors and systems (IC-SSS) (pp. 1-4). IEEE.
- Thamoethata, K., Isong, B., Dladlu, N., & Abu-Mahfouz, A. M. (2021, November). Analysis of IoT-based vehicle anti-theft security. In 2021 3rd International Multidisciplinary Information Technology and Engineering Conference (IMITEC) (pp. 1-6). IEEE.
- Fazil, P. M., Prasad, N., Ranjitha, B., & Nair, S. S. (2020). Anti-Theft Security System with Image Feedback using Raspberry PI and IoT. i-Manager's Journal on Electronics Engineering, 10(3), 8.
- Anvekar, R. G., & Banakar, R. M. (2017, April). IoT application development: Home security system. In 2017 IEEE Technological Innovations in ICT for Agriculture and Rural Development (TIAR) (pp. 68-72). IEEE.
- Harikrishnan G.R., Noufal V.P., Latheesh S., “Third Eye -An Ef ficient Home Security Automation System”, International JournalComputer Applications (0975 – 8887) Volume 117 – No. 17, May 2015
- Yogita Vijay Narkhede, S. G. Khadke, “Application of Raspberry Pi and PIR Sensor for Monitoring of Smart Surveillance System”, International Journal of Science and Research (IJSR), Volume 5 Issue 2, February 2016 ISSN (Online): 2319-7064
- ShivprasadTavagad, ShivaniBhosale, Ajit Prakash Singh, Deepak Kumar, “Survey Paper on Smart Surveillance System”, International Research Journal of Engineering and Technology (IRJET), Volume: 03 Issue: 02 | Feb-2016 e-ISSN: 2395 -0056, pISSN: 2395-0072
- Sowmiya. U, ShafiqMansoor.J., “Raspberry Pi based home door security through 3g dongle”, International Journal of Engineering Research and General Science Volume 3, Issue 2, March-April, 2015, ISSN 2091-2730


