Measurement Based Admission Control Methods in IP Networks
Автор: Erik Chromy, Tomas Behul
Журнал: International Journal of Information Technology and Computer Science(IJITCS) @ijitcs
Статья в выпуске: 10 Vol. 5, 2013 года.
Бесплатный доступ
Trends in telecommunications show that customers require still more and more bandwidth. If the telecommunication operators want to be successful, they must invest a lot of money to their infrastructure and they must ensure required quality of service. The telecommunication operators would devote to development in this area. The article deals with quality of service in IP networks. Problems of quality of service can be solved through admission control methods based on measurements. These admission control methods take care of control of incoming traffic load. New flow can be accepted only if needed quality of service is ensured for it and without quality of service breach causing of already accepted flows. In the article were made description of simulations and results of simulations for Voice over IP, constant bit rate and video sources. Simulations were realized in Network simulator 2 environment. These simulations were evaluated on the base of some parameters such as: estimated bandwidth, utilization and loss rate.
Admission Control Method, MBAC Method, Quality of Service
Короткий адрес: https://sciup.org/15011973
IDR: 15011973
Текст научной статьи Measurement Based Admission Control Methods in IP Networks
Published Online September 2013 in MECS DOI: 10.5815/ijitcs.2013.10.01
The telecommunication operators must invest a lot of money to build their infrastructure. They try to obtain many customers. The telecommunication companies want provide to customers a lot of services, but they must ensure required quality of service. Customers are interested in telephony (fixed network, mobile network and VoIP) and multimedia services such as video on demand or a lot of TV channels as well.
Now we can see at the market many smart phones and other devices, which can with one click login to different accounts, where customers can download some applications. Customers use data connection for watching video clips, films and playing online games.
All these services need large bandwidth. If the operators want to increase their profit and acquire a lot of customers, then they have to invest more money to their infrastructure. Or they cooperate with research centers in order to try to develop efficient bandwidth utilization and quality of service (QoS) [1-7].
A lot of methods exist, which deals with use of effective bandwidth – mathematical models and timeconsuming simulations. This article deals with admission control (AC) methods in IP networks.
These methods take care of control of incoming traffic load. AC methods consist of a set of measurements needed for acceptance or rejection of incoming flows. New flow can be accepted only if required QoS is ensured for it and without QoS breach causing of already accepted flows.
The paper deals with simulation of measurement based admission control (MBAC) algorithms with MBAC mechanisms. Effective bandwidth is minimal bandwidth that ensures required QoS.
The remainder of this paper is organized as follows: in section 2, 3, 4 the theory about MBAC methods, MBAC algorithms and measurement mechanisms is addressed. In section 5 is description of simulations and results of simulations for VoIP, CBR and video source. Summary of all simulations is in section 6.
-
II. Measurement Based Admission Control Methods
MBAC method can be performed on end-to-end connection [8-12].
MBAC methods can be divided into two categories:
-
• passive MBAC – based on data packet,
-
• active MBAC – based on test packet.
-
3.2 Measured Sum
These two methods solve the problem of scalability that occurs in parameter based admission control (PBAC) method.
Bandwidth estimation is defined by:
This algorithm detects bandwidth of current traffic load. If the following condition is accomplished, then new flow can be accepted:
с = т , + Р measured new
measured
where m is average measured transfer rate of current traffic load, P is maximal transfer rate of flow requesting admission, e is upper limit of overflow probability (probability that bandwidth of link will be exceeded) and coefficient a is defined by:
v+ ra < ц.V (4)
Л
V is bandwidth of current traffic load, r a is transfer rate requested by flow a , Ц is bandwidth of link and V is utilization of network defined by user ( 0 < V < 1 ) .
a = 4 - 2ln ( e ) - ln(2 n )
-
3.3 Hoeffding Bound
The basic principle of Hoeffding Bound (HB) algorithm is based on calculation of bandwidth of the current traffic load. If the sum of the peak rate of new
-
III. Measurement Based Admission Control Algorithms
MBAC algorithms decide if new flow will be accepted, or not. There exists a lot of support algorithms and each of them is suitable for different types of traffic load and has some advantages and some disadvantages
Between MBAC algorithms belongs [9] [12] [13]:
-
• Simple Sum,
-
• Measured Sum,
-
• Hoeffding Bound,
-
• Acceptance Region:
-
- Tangent at Peak,
-
- Tangent at Origin,
-
- Tangent at Arbitrary Point.
-
3.1 Simple Sum
Algorithm of simple sum ensures that the number of required sources will not exceed the capacity of link.
Л
Let V is bandwidth of current traffic load, Ц is link bandwidth, a is index of flow requesting of admission and r a is transfer rate of flow a . New flow can be accepted if the following condition is fulfilled:
v+ ra < ц. (3)
This condition is ensured by the input routers and switches.
Л
flow p and bandwidth of current traffic load C is
H
less than the bandwidth of the link, then new flow will be accepted. If the following condition is not accomplished, then flow will be rejected:
Л
Ch +P^Ц.
For the bandwidth calculation of current traffic load the following equation is used:
Л where n is the number of accepted flows, v is the bandwidth of current traffic load estimated by measure mechanism of exponential averaging, p is the peak rate of accepted flow and e is loss rate.
-
3.4 Acceptance Region
Let a is the average transfer rate and p is peak transfer rate of on/off source, then the bandwidth of source C can be defined by following equation:
C (s )= flog 1 + a (e-p -1) s L p
where s is space parameter of acceptance region and it is from interval < 0,1 > .
To the MBAC algorithms of acceptance region belong algorithms based on tangent at point.
-
1) Tangent at Peak
np(1 — e sp )+ e sp v < ц
where n is the number of accepted flows, p is peak transfer rate of the new accepted flow, s is space parameter of acceptance region and it is from interval
A
< 0,1 > , V is the bandwidth of current traffic load and Ц is the bandwidth of link.
-
2) Tangent at Arbitrary Point
pesp
p + a (esp — 1)
na(ep - 1)+ pv < ц
A where a is average measured traffic rate of source.
estimation i s immediately raised to the new calculated average value [8], [12].
-
2) Point Samples
This measurement mechanism is used with Acceptance Region - Tangent at Origin (ACTO) algorithm and Acceptance Region -Tangent at Peak (ACTP) algorithm. Algorithm takes an average load sample every period S [8], [12].
-
3) Exponential Averaging
The exponential averaging mechanism of current traffic load is used with algorithm Hoeffding Bound. Current traffic load vS is measured every sampling period S . This measurement mechanism is calculated with using an infinity impulse response function with weight to .
v = ( 1 — w ) v + w. V S (11)
A where v is bandwidth of current traffic load, v is an average load in previous period, w is a weight of flow and vS is actual traffic load [8], [12].
-
3) Tangent at Peak
esp v < ц . (10)
-
IV. Measurement Mechanisms
There exist several measurement mechanisms, which are used with combination of MBAC algorithms. Their task is to correctly estimate the bandwidth of current traffic load. To these mechanisms belong:
-
• Time Window,
-
• Point Samples,
-
• Exponential Averaging.
-
1) Time Window
Mechanism of time window is used with measured sum algorithm. It calculates an average bandwidth every sampling period S . At the end of the measurement window T , the highest average value is denoted, which is used for estimation of bandwidth for the next window T . If the new flow is accepted, the estimation of window is increased by transfer rate of new flow. If a newly calculated average is above the estimation, the
-
V. MBAC Algorithms for Different Traffic Sources
This chapter deals with simulations of four MBAC algorithms and evaluation of achieved results. Simulations are realized in simulation program Network Simulator 2.
MBAC algorithms have been simulated for three different traffic sources: Voice over IP (VoIP), constant bit rate (CBR) and video. These simulations were evaluated on the base of some important parameters: estimated bandwidth, utilization and loss rate.
The following algorithms have been simulated:
-
• Measured Sum (MS),
-
• Hoeffding Bound (HB),
-
• Acceptance Region - Tangent at Origin (ACTO)
-
• Acceptance Region - Tangent at Peak (ACTP).
Following three measurement mechanisms have been used with these algorithms:
-
• Time Window (with algorithm MS),
-
• Point Samples (with algorithms ACTO and ACTP),
-
• Exponential Averaging (with algorithm HB).
The following parameters were used for these algorithms:
-
• v – network utilization,
-
• T – time window parameter,
-
• S – sampling period,
-
• w – weight of flow,
-
• ε – probability of loss rate,
-
• s – space parameter of acceptance region.
-
5.1 Simulation of MBAC Algorithms for VoIP Traffic
Table 1: Simulation parameters
|
MS |
HB |
ACTO |
ACTP |
|
v = 0.95 |
w = 0.125 |
--- |
--- |
|
T = 3 ms |
ε = 0.7 |
s = 2e-6 |
s = 2e-6 |
|
S = 5000 ms |
S = 5000 ms |
S = 5000 ms |
S = 5000 ms |
In this simulation VoIP exponential on/off source with maximum traffic rate of 64 kbit/s (typical voice traffic) is used. The size of sending packet is 125 bits. Bandwidth of link is 10 Mbit/s. Topology of simulated topology is shown in the figure 1.
MBAC algorithms
VoIP sources

10 Mbit/s

10 Mbit/s

Fig. 1: topology of simulated network (VoIP)
MBAC algorithms MS, HB, ACTP and ACTO are compared. These simulations are evaluated on the base of some parameters such as: estimated bandwidth, utilization and loss rate.
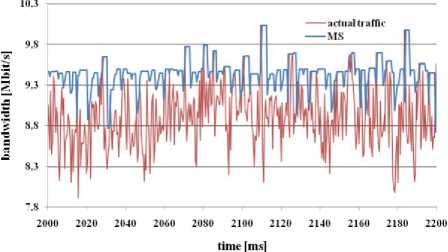
Fig. 2: bandwidth estimation through MS algorithm
MBAC MS algorithm (figure 2) tries to adapt bandwidth estimation to bandwidth of actual traffic load. It always tries to estimate bandwidth that is sufficient for actual traffic load in the network. Disadvantage of MS algorithm is that estimated bandwidth was often bigger than required bandwidth of actual traffic load.
HB Algorithm (figure 3) not reacts on increase of actual traffic load. Disadvantage of HB algorithm is that actual traffic load was often bigger than link bandwidth (10 Mbit/s). All these packets were included between lost packets. This result shows that HB algorithm is not suitable for situations, when traffic load fluctuation in network occurs. This fluctuation is caused by measurement mechanism of exponential averaging that is not able to adapt quickly and dynamically to actual traffic load changes.
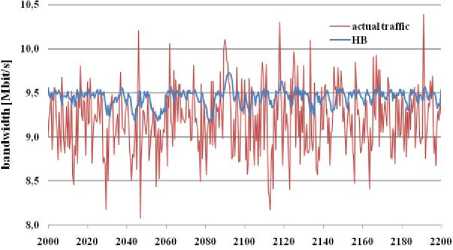
time [ ms]
Fig. 3: bandwidth estimation through HB algorithm
Link utilization was the best for the HB algorithm, but loss rate was the worst from all the simulated algorithms. These results show that HB algorithm is not suitable for VoIP traffic.
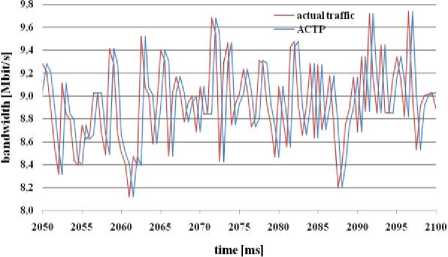
Fig. 4: bandwidth estimation through ACTP algorithm
The process of simulations shows that MBAC algorithms ACTP (figure 4) and ACTO (figure 5) are estimating bandwidth flexible, but always with time delay. They try to adapt to the network traffic load what is very suitable for real time application.
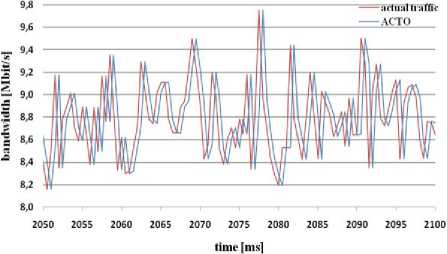
Fig. 5: bandwidth estimation through ACTO algorithm
All results have shown that the most suitable algorithms for implementation to the VoIP network are ACTP and ACTO (if we consider bandwidth prediction and loss rate). Of course, very important is to consider the situation in the network (because with other conditions could be other algorithm suitable for VoIP traffic).
Table 2: Algorithm comparison for VoIP traffic
|
loss rate (%) |
link utilization (%) |
number of sent packets |
number of lost packets |
|
|
MS |
4.59e-06 |
88.96 |
26128058 |
120 |
|
HB |
7.54e-05 |
92.00 |
26995932 |
2038 |
|
ACTP |
1.57e-06 |
88.44 |
25992207 |
41 |
|
ACTO |
1.20e-06 |
87.81 |
25743808 |
31 |
-
5.2 Simulation of MBAC Algorithms for CBR Traffic
In the next simulation the source with constant bit rate (CBR) 800 kbit/s is used, size of packet is 125 bits and interval between sent packets is 0.01ms.
MBAC algorithms
CBR sources

10 Mbit/s
10 Mbit/s

Fig. 6: topology of simulated network (CBR)
In the next simulations MBAC algorithms are compared: MS, HB, ACTP and ACTO. These simulations are evaluated on the base of some parameters such as: estimated bandwidth, utilization and loss rate.
From the figure 7 we can see, that MS algorithm predicts the required bandwidth very exactly. This preciseness of MS algorithm let minimum packets from
CBR source to the network (from all simulated algorithms).
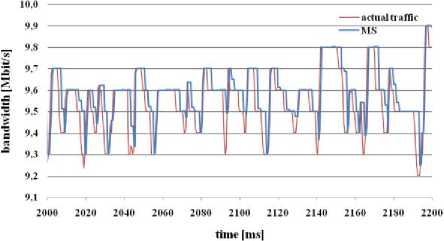
Fig. 7: bandwidth estimation through MS algorithm
MS algorithm tries to predict the bandwidth that not exceeds the link capacity 10 Mbit/s. Very important parameter for this method is loss rate. By use of MS algorithm the number of lost packets was minimal (from all the simulated algorithms).
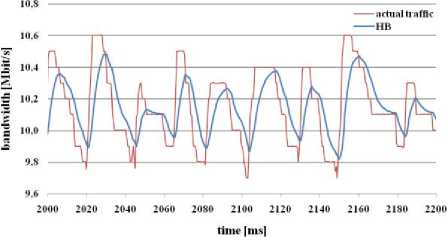
Fig. 8: bandwidth estimation through HB algorithm
From the figure 8 we can see that HB algorithm reacts very slowly on changes of traffic load. Mainly, it is caused by cooperation of HB algorithm with measurement mechanism - point samples. Link utilization is almost 100%, but loss rate was the highest from all the simulated algorithms. This is caused because this algorithm let packets access to the network, although there was no more sufficient bandwidth.
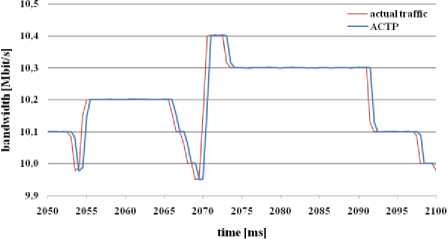
Fig. 9: bandwidth estimation through ACTP algorithm
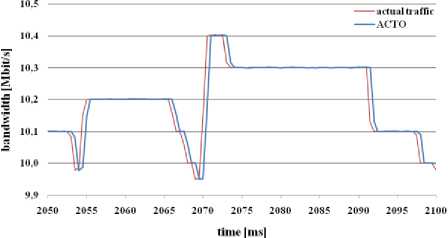
Fig. 10: bandwidth estimation through ACTO algorithm
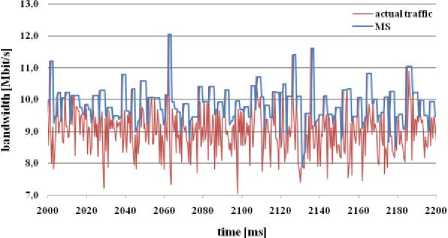
Fig. 12: bandwidth estimation through MS algorithm
ACTP (figure 9) and ACTO (figure 10) algorithms try to adapt the estimated bandwidth to the actual traffic load, even though the bandwith of the link was often exceeded (10 Mbit/s). These algorithms reacted in the same way on loss rate, link utilization and the number of lost packets.
All results have shown that the most suitable algorithm for implementation to the network for constant bit rate sources is MS algorithm.
Table 3: Algorithm comparison for CBR traffic
|
loss rate (%) |
link utilization (%) |
number of sent packets |
number of lost packets |
|
|
MS |
1.96e-05 |
95.41 |
28499594 |
559 |
|
HB |
0.0164 |
99.68 |
30243225 |
496006 |
|
ACTP |
0.008205 |
99.89 |
30058393 |
246635 |
|
ACTO |
0.008205 |
99.89 |
30058393 |
246635 |
-
5.3 Simulation of MBAC Algorithms for Video Traffic
In the next simulation exponential source with maximal bit rate 600 kbit/s and constant size of generated packets 125 bits is used.
MBAC algorithms
Fig. 11: topology of simulated network (video)
Once again, there are compared four MBAC algorithms: MS, HB, ACTP and ACTO. These simulations are evaluated on the base of some parameters such as: estimated bandwidth, utilization and loss rate.
As shown in the figure 12, MS algorithm estimated sufficient bandwidth, but in some cases, this estimated bandwidth was higher than link bandwidth (it means lost packets). This algorithm has the smallest loss rate, because MS algorithm allows the source to send less number of packets than by HB and ACTP algorithms (in these cases was higher lost rate).
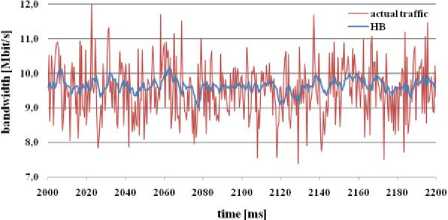
Fig. 13: bandwidth estimation through HB algorithm
HB algorithm (figure 13) predicts bandwidth under defined value of link bandwidth 10 Mbit/s, but actual traffic load was often higher than link bandwidth (because the flows with higher transfer rate asked to access to the network). Link utilization was more than 92%, but loss rate was one of the worst. If the maximum value of link 10 Mbit/s was exceeded, the flows were dropped.
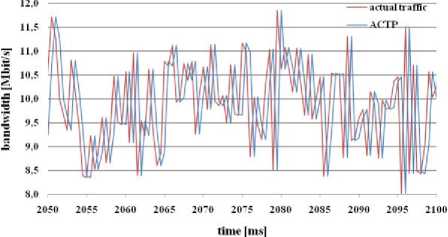
Fig. 14: Bandwidth estimation through ACTP algorithm
In the figure 14 we can see that ACTP algorithm adapts the estimation of bandwidth to the actual traffic load. This algorithm does not take into account the fact that there is no free sufficient bandwidth for accepting new flows. The flow was accepted even though the defined link bandwidth 10 Mbit/s was exceeded. Therefore, loss rate and link utilization were the highest from all the simulated algorithms. This method is not suitable for video traffic.
In ACTO algorithm (figure 15) simulation the number of lost packets is very important. Loss rate was the smallest from all simulated algorithms. ACTO algorithm estimated bandwidth of actual traffic load so that the bandwidth 10 Mbit/s is not exceeded.
This goal was not always successful, but ACTO algorithm was the best in bandwidth estimation from all the simulated algorithms (on the base of number of lost packets).
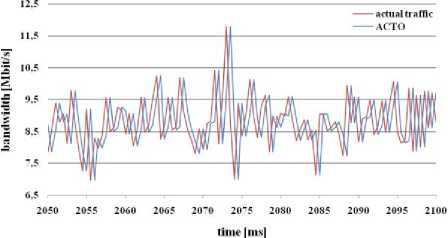
Fig. 15: Bandwidth estimation through ACTO algorithm
All results have shown that the most suitable algorithm for implementation to the network with video traffic sources is ACTO algorithm. Of course, the situation could change, if there was for example video source and ftp source in the network. In this case ACTO algorithm would be not the best choice.
Table 4: Algorithm comparison for video traffic
|
loss rate (%) |
link utilization (%) |
number of sent packets |
number of lost packets |
|
|
MS |
0.01233 |
88.23 |
26603367 |
328230 |
|
HB |
0.02439 |
92.29 |
28057719 |
684526 |
|
ACTP |
0.03989 |
94.73 |
29271307 |
1167840 |
|
ACTO |
0.01153 |
87.80 |
26464869 |
305262 |
-
VI. Conclusion
This article deals with simulations of measurement based admission control (MBAC) algorithms for different traffic source (Voice over IP, constant bit rate and video). Algorithms Measured Sum (MS), Hoeffding Bound (HB), Acceptance Region - Tangent at Peak (ACTP) and Acceptance Region - Tangent at Origin (ACTO) were compared. These simulations were evaluated on the base of some parameters such as: estimated bandwidth, link utilization and loss rate.
On the base of realized simulations, we can say following:
ACTP and ACTO algorithms are the best MBAC algorithms for networks with VoIP traffic. Obtained results for both algorithms are comparable. In both cases the link utilization was about 88%.
The most suitable MBAC algorithm for bandwidth estimation in network with CBR traffic is MS. MS algorithm was the best from all simulated algorithms in all monitored parameters. Link utilization was about 95%.
The most suitable MBAC algorithm for bandwidth estimation in network with video traffic is ACTO. Link utilization was about 88%. Good results were reached also for MS algorithm.
Acknowledgements
This work is a part of research activities conducted at Slovak University of Technology Bratislava, Faculty of Electrical Engineering and Information Technology, Institute of Telecommunications, within the scope of the projects „Support of Center of Excellence for SMART Technologies, Systems and Services II., ITMS 26240120029, co-funded by the ERDF“ and project VEGA No. 1/0106/11 “Analysis and proposal for advanced optical access networks in the NGN converged infrastructure utilizing fixed transmission media for supporting multimedia services”.
Список литературы Measurement Based Admission Control Methods in IP Networks
- Kyrbashov B, Baronak I, Kovacik M, Janata V. Evaluation and Investigation of the Delay in VoIP Networks. In: Radioengineering. vol. 20, no. 2, 2011, pp. 540-547, ISSN 1210-2512
- Baronak I, Kockovic L. Alternatives of Providing IPTV Using IMS. In: Journal of Computers & Technology [online]. 2012, vol. 3, no. 2, [cit. 2013-01-23]. pp. 188-192, ISSN 2277-3061. Available at: http://cirworld.com/index.php/ijct/article/view/463
- Halas M, Klucik S. Modelling the Probability Density Function of IPTV Traffic Packet Delay Variation. In: Advances in Electrical and Electronic Engineering [online]. 2012, vol. 10, iss. 4, [cit. 2013-01-23]. ISSN 1804-3119. Available at: http://advances.uniza.sk/index.php/AEEE/article/view/726/806.
- Balogh T, Medvecky M. Average Bandwidth Allocation Model of WFQ. In: Modelling and Simulation in Engineering. Vol. 2012 (2012), Article ID 301012, 7 pages, doi:10.1155/2012/301012, ISSN 1687-5605.
- Pistek M, Medvecky M. Comparison of Standardized Bandwidth Constraint Models. In: ELITECH 13, 15th Conference of Doctoral Students, June 5, 2013, pp. 1-6, ISBN 978-80-227-3947-4.
- Kavacky M, Baronak I. Evaluation of Two Statistical CAC Methods for Variable Bit Rate Traffic Sources. In: Journal of Electrical Engineering. Vol. 59, No. 4 (2008), pp. 178-186, ISSN 1335-3632.
- Siska M, Kavacky M. Can Open-Source PBX Compete with Professional Communication System? In: RTT 2009. Research in Telecommunication Technology: 11th International Conference, Srby, Czech Republic, 2009, ISBN 978-80-01-04410-0.
- Statovci B. Support of IP Multi-service through Admission Control. In: Innovations in NGN: Future Network and Services. 2008, K-INGN 2008, First ITU-T Kaleidoscope Academic Conference, Geneva, 2008, pp. 407-414.
- Yi-ran G, Suo-ping W, Hai-ya W. A Structural Comparison of Measurement-based Admission Control Algorithms. In: The Journal of China Universities of Posts and Telecommunications. 2006 vol. 13, Issue 3, pp. 81-86.
- Gelenbe E, Sakellari G, D’arienzo M. Admission of QoS Aware Users in a Smart Network. In: SASO '07 Proceedings of the First International Conference on Self-Adaptive and Self-Organizing Systems 2007, Washington, USA, pp. 205 -213.
- Georgoulas S, Trimintzios P, Kin-hon H. Measurement-based Admission Control for Real-time Traffic in IP Differentiated Services Networks. In: Proceedings of IEEE International Conference on Telecommunications (ICT'2005), Capetown, South Africa, IEEE, May 2005.
- Jamin S, Shenker S. Measurement-based Admission Control Algorithms for Controlled-load Service: A Structural Examination. University of Michigan CSE-TR-333-97, April 1997.
- Breslau L, Jamin S, Shenker S. Comments on the Performance of Measurement-Based Admission Control Algorithms. In: INFOCOM 2000. Nineteenth Annual Joint Conference of the IEEE Computer and Communications Societies, Proceedings IEEE, 2000, pp. 1233-1242.


