Performance Analysis of 802.16 (WIMAX) Networks under Various Routing Protocols and Traffic Loads
Автор: Mohammad Rehan Rasheed, Ibrahim M. Hussain
Журнал: International Journal of Information Technology and Computer Science(IJITCS) @ijitcs
Статья в выпуске: 11 Vol. 4, 2012 года.
Бесплатный доступ
The selection of an appropriate routing protocol is a key issue when designing a scalable and efficient wireless networks. In this paper, we investigate different routing protocols and evaluate their performances on 802.16 WiMAX networks. Further, we present a comparison between 802.16 and 802.11 ad hoc networks based on the performances of various rerouting protocols. The simulation results show that the table driven DSDV protocol has the best performance in terms of the delivery fraction which outperforms the rest of the protocols. In addition, we also assert from the experiments that packet delay experienced by DSDV protocol is very high. Hence, there should be a tradeoff between various performance parameters when using the DSDV protocol in 802.16 networks.
Ad Hoc Networks, Performance Analysis, Routing Protocols, WiMAX
Короткий адрес: https://sciup.org/15011778
IDR: 15011778
Текст научной статьи Performance Analysis of 802.16 (WIMAX) Networks under Various Routing Protocols and Traffic Loads
Published Online October 2012 in MECS
Wireless networks play an important role in modern era for transmitting data with minimal overhead and maximum possible speed. These networks have become more efficient with the introduction of mobility concept of nodes. Two variations of such networks exist. The first one called structured wireless networks, have fixed main nodes concerned with routing or switching of data (sometimes called gateways or base stations). These gateways are usually fixed in nature and are connected to each other using wired or wireless links. These networks are mainly used in office wireless local area networks (WLAN). The other type of networks called infrastructreless or ad hoc networks embeds the concept of mobility within the routing nodes. The nodes communicate with each other using multi-hop wireless links. These networks have no fixed routing nodes. All nodes are capable of movement and can be connected in any random manner. These networks are mainly used in disaster or emergency areas where no prior fixed infrastructure exits.
One of the challenging aspects in these ad hoc networks is to find and develop routing protocols that can efficiently find routes between any two nodes. The routing protocol should take into account the mobility factor in these networks and the topology being used. For this reason, performance evaluation of various protocols has been carried out by different authors. In [1], performance of Dynamic Source Routing (DSR) and Ad Hoc On-Demand Distance Vector Routing (AODV) has been considered. The performance is analyzed using various network load, mobility and network size. Highly Dynamic Destination-Sequenced Distance-Vector Routing (DSDV) is another protocol which is a table-driven protocol used in wireless networks [2]. Various performance parameters for these protocols have been explored including packet fractional delay (PDF), average delay, throughput, goodput, normalized routing load (NRL) and routing overhead (RO).
Considering the challenging and demanding aspects by the modern wireless systems, the broadband wireless access industry, which provides high-rate network connections to stationary locations, has matured to the point at which it now has a standard for second generation wireless metropolitan area networks. IEEE 802.16 standard which is well known as worldwide interoperability for microwave access (WiMAX) is the solution for such wireless networks [3]. Different issues are associated with this technology including cell planning and management [4], quality of service with efficient bandwidth utilization and the routing protocols being used.
In our work, we have evaluated the performance of some of these routing protocols in WiMAX networks and studied various performance parameters for such networks. The remainder of this paper is organized as follows: section 2 gives a brief introduction to WiMAX networks and the standards being used at the medium access control (MAC) layer. In section 3, various routing protocols and their respective performance analysis in conventional 802.11 ad hoc networks have been discussed. The performance analysis of different routing protocols in WiMAX networks has been carried out in section 4. Finally, the conclusion of our work is summarized in section 5.
-
II. An Overview of 802.16 WiMAX Networks
The IEEE Standard 802.16-2001 [10] defines the Wireless MAN air interface specification for wireless metropolitan area networks (MANs). The completion of this standard signs the entry of broadband wireless access as a major new tool in the effort to link end stations to core telecommunications networks worldwide. It was developed to include a set of air interfaces based on a common MAC protocol but with physical layer specifications dependent on the available frequency range. The spectrum range is from 10 to 66 GHz, as approved in 2001, which is currently available worldwide but at the expense of some physical deployment issues.
The standard defines the specifications related to the service-specific convergence sublayer (CS), the MAC common part sublayer (CPS), the security sublayer, and the physical layer. The MAC management messages are implemented to operate the WiMAX networks. All operations between the base station (BS) and subscriber station (SS) over a super frame interval follow the procedures of the 802.16 standard.
Basically, the IEEE 802.16 MAC protocol [5,6] was designed for point-to-multipoint broadband wireless applications. High data rates at both uplink and downlink is considered to be the main objective of this standard. Resource allocation algorithms are used for channel sharing among users. The 802.16 MAC layer supports continuous and burst nature traffics. The first sublayer in the MAC layer is the convergence sublayer which is used to map different traffics to a form compatible with WiMAX MAC traffic type. The second layer is the common part sublayer which provides the core MAC functionality of system access, bandwidth allocation, scheduling, contention mechanism, connection establishment, and maintenance. It receives data from various sources through the MAC service access points (SAPs), which is classified to particular MAC connections.
The quality of service (QoS) types supported by WiMAX are unsolicited grant service (UGS) for the constant bit rate (CBR) service, real-time polling service (rtPS) for the variable bit rate (VBR) service, non-real-time polling service (nrtPS) for non-real-time VBR, and best effort service (BE) for service with no rate or delay requirements. Traffic classes are associated with certain QoS parameters and according to these parameters, MAC scheduler makes appropriate handling. The upper-layer data are queued with an assigned connection ID.
For the uplink traffic, each SS should range to the BS before entering the domain. In the first ranging duration, a burst record is established between SS and BS which includes interval usage code (DIUC) to the BS. Similarly, after that, uplink interval usage code (UIUC) is going to be agreed upon between BS and SS. The downlink-MAP and uplink-MAP which contain the channel ID and the MAP information elements (IEs) describes the physical layer specification. The burst profile includes the DIUC, UIUC, and the type-lengthvalue (TLV) encoded information. The burst profile also includes type-length-value (TLV) encoded information. The TLV encoded information will notify the physical layer of the modulation type, (Forward error control) FEC code type, and encoding parameters (e.g. coding rates). The final MAC data payload is packed by these encoding types. The IEEE 802.16 uses the frame-based transmission architecture where the frame length is variable. These frames called superframes are divided into two subframes: downlink subframe and the uplink subframe.
In [11], authors developed a WiMAX module called Mac802._16 which is in accordance with the specifications of the IEEE 802.16-2004 standard and based on the ns-2 version 2.29. We have used the same module for our simulations.
-
III. Wireless Routing Protocols
-
3.1 Destination-Sequenced Distance-VectorRouting (DSDV)
-
3.2 Ad Hoc On-Demand Distance Vector Routing (AODV)
-
3.3 Dynamic Source Routing (DSR)
-
3.4 Simulation Results for 802.11 ad hoc Networks
Since our simulation results are based on three routing protocols, specifically, DSDV, DSR and AODV, a brief detail of these protocols is given below along with their performances in IEEE 802.11 ad hoc networks followed by their performances in 802.16 networks.
This is one of the table-driven routing protocols based on the Bellman-Ford routing mechanism. In table-driven routing protocols [7], the main objective is to maintain consistent and up-to-date routing information from each source node to other destination nodes in the network. Each node maintains one or more tables to store the required routing information. These tables are updated according to changes in network topology by propagating update information throughout the network. Two key elements are important in such protocols, the number of routing tables and the update method being used.
In DSDV, the entries in the table are indicated by numbers assigned by the destination node. These numbers act as status indicators of the nodes which therefore minimizes routing loops. Routing update packets are transmitted throughout the network to maintain table consistency. These packets indicate which nodes are accessible from each node and the number of hops required reaching the destination nodes using distance-vector algorithms. These update packets can result in large amount of traffic. Two types of update packets are present in DSDV based networks. The first one which is infrequently transmitted is called the full dump. This type of packet carries all available routing information. The second type called incremental packet is used to forward only that information which has changed since the last full dump. Both update packets have fixed size network protocol data unit (NPDU). The routing nodes also keep record of the average time for a route to a destination till the route with the best metric is received. One way to reduce the network traffic in DSDV is by delaying the broadcast of update packets by an amount equal to the average route time.
This protocol is based on source-initiated on-demand routing. This type of routing creates routes only when desired by the source node. Route discovery process starts on demand by the source. This process is completed once a route is found or all possible routes have been explored. It provides unicast, broadcast, and multicast communication in ad hoc mobile networks [8]. Routes are maintained as long as they are needed by the source node. AODV nodes maintain a route table in which next hop routing information for destination nodes is stored.
When a source node desires to send a data to a destination node and no route information is available, a path exploration process to find the destination node takes place. It broadcasts a route request (RREQ) packet to adjacent nodes, which in turn, forward the request to their adjacent nodes, and so on, until the destination node is found. Each node maintains a sequence number and a broadcast ID. The broadcast ID is incremented for each generated RREQ. The RREQ packet consists of the node sequence number, broadcast ID and the most recent sequence number it has for the destination node. Only those nodes reply to the RREQ which have their sequence numbers greater than or equal to that contained in the RREQ. During this whole process, the reverse path is established from destination to source. Once the RREQ reaches the destination or an intermediate node with a route, that node responds by unicasting a route reply (RREP) along the reverse path. As the RREP is routed back along the reverse path, the nodes along this path update their routing tables indicating this forward route which becomes an active route. For further maintaining the link, link failure notification messages are used periodically.
DSR protocol [9] is another on-demand routing protocol that is based on the concept of source routing. It allows nodes to dynamically discover a source route across multiple network hops to any destination in the ad hoc network. The protocol is a combination of two steps: route discovery and route maintenance. When a node wants to transmit data to a destination node, it checks it own cache for an existing route. If a route is available, the source node uses that route otherwise a route discovery takes place. A route request packet is generated containing the source and destination address, along with a unique identification number. Each intermediate node intercepts this packet and checks whether it is familiar with a route to the destination node or not. If it does not know about the route, it adds its own address to packet and forwards the packet to the next node. A reply is generated by the final node when the route request packet reaches the destination or when an intermediate node finds an unexpired route to the destination. These two steps result in finding the total number of hops to the destination. To maintain the route, route error packets and acknowledgments are used.
Figures 1 and 2 show the performance of the three protocols in terms of PDF and average delay for different pause times. PDF means the number of packets successfully delivered to the destination node divided by the total number of generated packets. Higher pause times mean low mobility of nodes. Hence, pause time of zero means maximum mobility of nodes. The Average end-to-end delay of data packets includes all possible delays caused by buffering during route discovery latency, queuing at the interface queue, retransmission delays at the MAC, propagation and transfer times. The presence of high mobility implies frequent link failures and each routing protocol reacts differently during link failures. The working of these protocols leads to differences in the performance. For this simulation, constant bit rate (CBR) traffic is generated at a data rate of 4 packets/s and node speed of 20m/s and. The total number of nodes is 50 with 20 maximum connections. It is evident from Fig. 1 that for highest mobility, AODV and DSR have better PDF compared to DSDV. In fact, AODV has almost the same PDF performance for all pause times which shows that AODV has the best performance in terms of PDF among all three protocols. Similarly, Fig. 2 shows that for the first 40 seconds pause time, the average end to end delay encountered by packets in DSDV is higher than both DSR and AODV. Again, during this pause time interval, AODV has the best performance but after 40 seconds, both DSR and AODV have slightly lower delay. This figure also shows that the delay experienced in AODV network is almost constant throughout the different node mobility whereas in DSDV and DSR, there is a considerable variation in the delay, especially
Networks under Various Routing Protocols and Traffic Loads after 10 seconds pause time. At higher rates of mobility (lower pause times), DSDV performs poorly, dropping to a 70% packet delivery ratio because stale routing table entry forwards most of the packets over a broken link. Since DSDV maintains only one route per destination and consequently, each packet that the MAC layer is unable to deliver is dropped since there are no alternate routes. For DSR and AODV, packet delivery ratio is independent of offered traffic load, with both protocols delivering between 85% and 100% of the packets in all cases. Since DSDV uses the table-driven approach of maintaining routing information, it is not as adaptive to the route changes that occur during high mobility. In contrast, the approach used by the on-demand protocols, AODV and DSR to build the routing information as and when they are created make them more adaptive and result in better performance (high packet delivery and lower packet delays). In summary, both the On-demand routing protocols, AODV and DSR outperforms the table-driven routing protocol DSDV in 802.11 ad hoc networks.
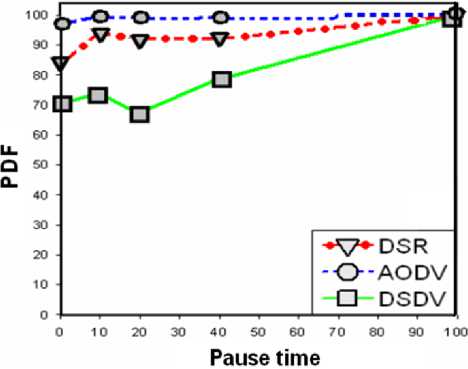
Fig. 1: PDF of various routing protocols in 802.11 ad hoc networks
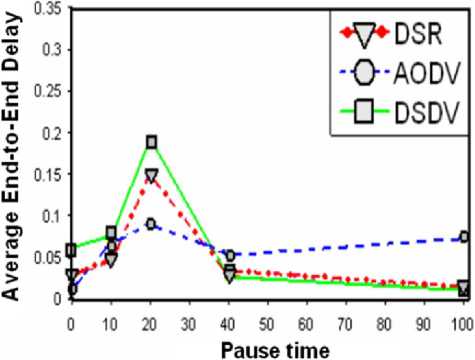
Fig. 2: Average end-to-end delay of various routing protocols in 802.11 ad hoc networks
-
IV. Performance Evaluation of 802.16 (WiMAX) Networks using Wireless Routing Protocols
In this section, we have investigated the performance of the three protocols in WiMAX networks. The results shown in Fig. 3 are obtained using the following parameters: CBR traffic type with 50 nodes having 20 maximum connections. The nodes maximum speed is 20 m/s and generating packets at the rate of 4 packets/s. The simulation is carried out for 900 simulation time and using a topology size of 1200 by 300. In Fig. 3–a, the PDF for DSDV outperforms that of both DSR and AODV. For highest mobility, almost 75% of the packets are delivered in case of DSDV. Further, almost 100% PDF is achieved at 500 pause time. The PDF performance for both on-demand routing protocols is very poor. But as shown in Fig. 3–b, the average delay is high in DSDV compared to both DSR and AODV for the first 30 seconds of pause time after which the delay is almost the same for all protocols. Similarly, Fig. 3–c shows the goodput for all the protocols. Goodput is the number of data packets successfully sent and received by the entire network within a certain period of time which is proportional to PDF. As expected, DSDV has the best goodput and outperforms the other two protocols.
The performance of the protocols in terms of normalized routing load, which is the number of routing packets transmitted per data packet delivered at the destination, and the routing overhead, which is the total number of routing packets transmitted during the simulation are shown in Figs. 3–d and 3–e respectively. Both these parameters measure the scalability of a protocol, the degree to which it will function in congested or low bandwidth environments, and its efficiency in terms of consuming node battery power. Also, these two parameters are related to PDF in the sense that lower PDF means that the delay metric is evaluated with lesser number of samples. Longer the path lengths, higher the probability of packet drops. Hence, sending large numbers of routing packets can also increase the probability of packet collisions and may delay data packets in network interface transmission queues. Thus, with a lower PDF, samples are usually biased in favor of smaller path lengths and thus have less delay [1]. As indicated in the figure, DSDV has highest routing overhead whereas both on-demand protocols have very low routing overhead. For this reason, in DSDV, packets exhibit more delay because of the increase in probability of packet collisions. For this reason, the key motivation behind the design of on-demand protocols is the reduction of the routing load.
Figure 4 shows the performance for all the protocols using different nodes. For this simulation, the pause time is fixed to zero, the data rate is 2 packets/s and the maximum number of connections is 10. PDF for all the protocols have the same pattern. For a fixed number of nodes, the PDF DSDV is better than those for the other two on-demand protocols. For average delay, it is interesting to see that the number of nodes in DSR has no impact on the delay. Further, for higher number of nodes, the delay converges to the same value. For NRL, the performance is almost the same for all nodes with DSR and AODV. But this performance shoots up for
DSDV. Although at 50 nodes, the average delay for all the protocols are same, but the routing overhead difference between DSDV and DSR or AODV is considerable.
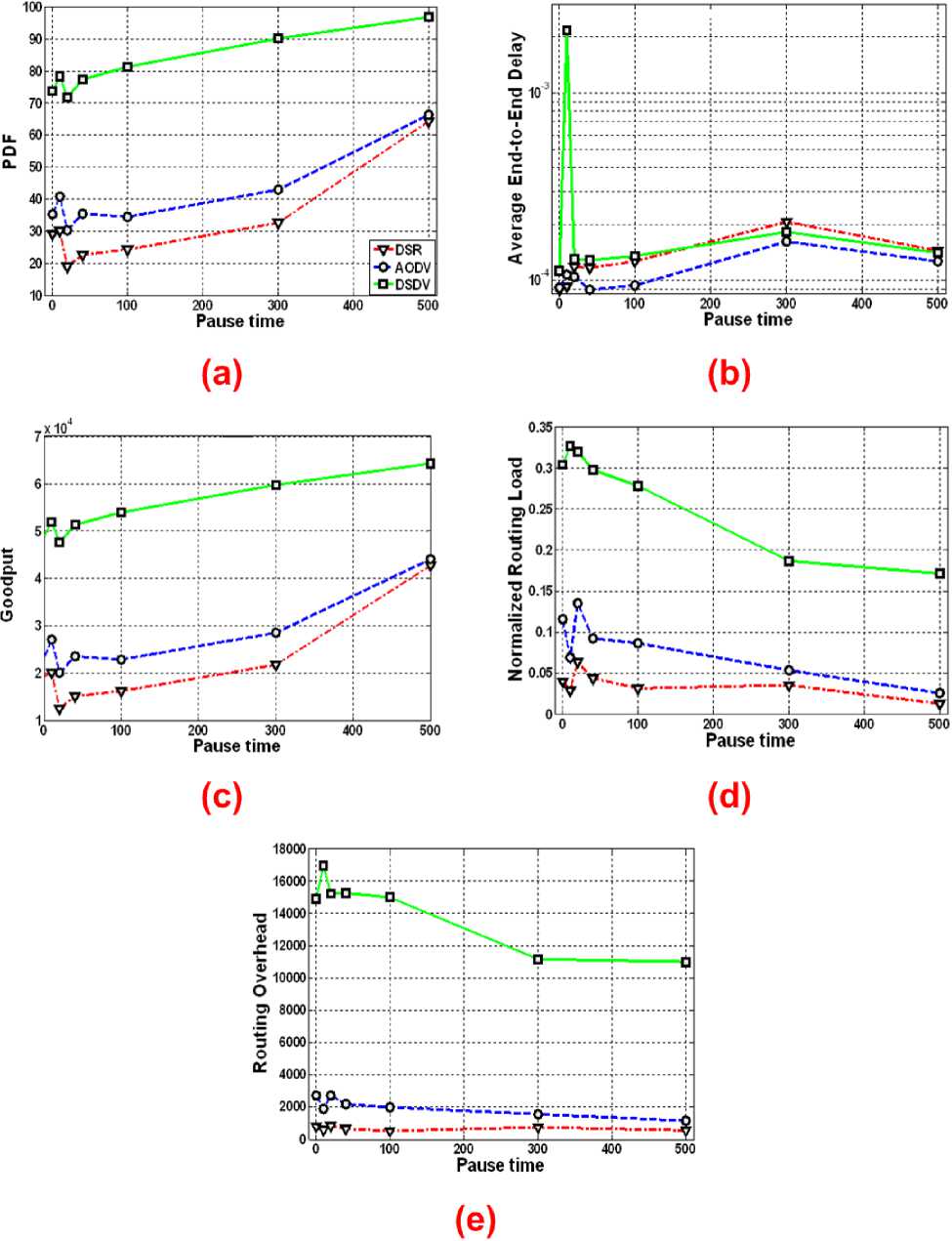
Fig. 3: Performance of various routing protocols in 802.16 networks for different pause time: (a) PDF (b) Delay (c) Goodput (d) NRL (e) RO
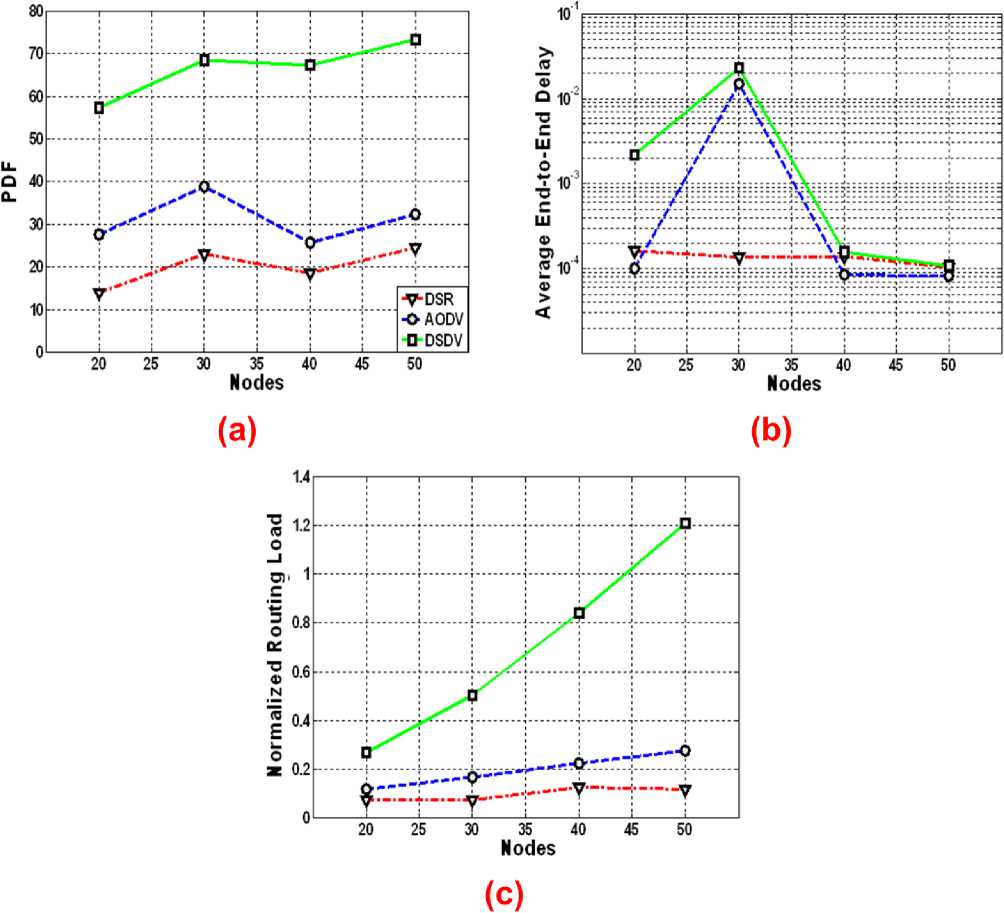
Fig. 4: Performance of various routing protocols in 802.16 networks for different number of nodes: (a) PDF (b) Delay (c) NRL
Based on the previous results, Fig. 5 shows the performance of the best protocol DSDV (i.e. PDF performance wise) for different number of connections and varying data rates. The PDF for DSDV as the number of connections and data rate vary has no large impact. But for the average delay, variation of delay is produced when the data rate is 2 packets/s. But as the data rate increases, the system becomes more stable in terms of end to end delay. On the other hand, as the number of connections increases, the NRL decreases for a fixed data rate. This is because the total number of data packets increases as the number of connections increases (i.e. larger number of nodes sending packets) and becomes much larger than the routing packets. Also, from the RO figure (i.e. Fig. 5–d), the number of routing packets is almost same for all the connections.
In summary, DSDV has the best performance in terms of PDF and goodput when it is implemented on WiMAX networks. In terms of NRL and delay, both on- demand protocols (i.e. DSR and AODV) have better performance.
-
V. Conclusion
Different routing protocols behave differently in 802.16 networks according to their internal working mechanism. It has been seen that the table-driven DSDV protocol has the best performance in terms of the packet delivery fraction parameter which outperforms both DSR and AODV but the delay experienced by DSDV packets are greater than the delay experienced by the on-demand routing protocols. Hence there should be a tradeoff between these routing protocols when incorporating them in 802.16 networks.
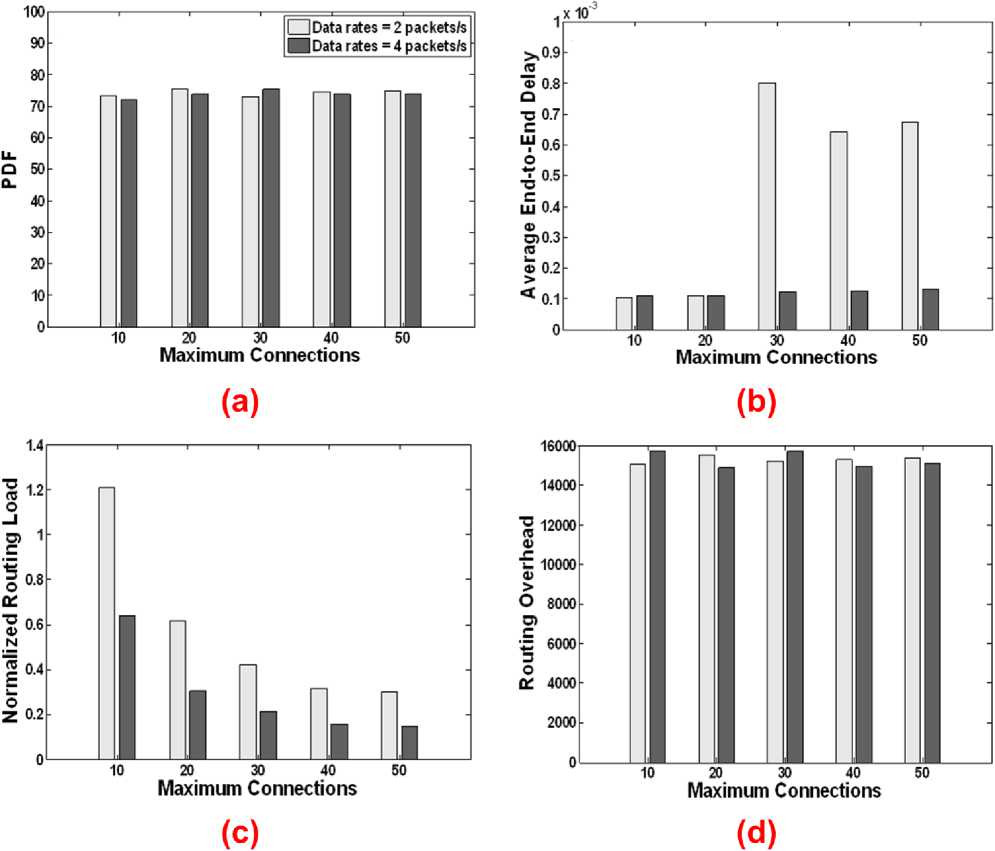
Fig. 5: Performance of DSDV in 802.16 networks for different maximum connections and varying data rates: (a) PDF (b) Delay (c) NRL (d) RO
Список литературы Performance Analysis of 802.16 (WIMAX) Networks under Various Routing Protocols and Traffic Loads
- Charles E. Perkins, Elizabeth M. Royer, Samir R. Das and Mahesh K. Marina., "Performance Comparison of Two On-demand Routing Protocols for Ad hoc Networks", IEEE Personal Communications Magazine special issue on Ad hoc Networking, vol. 8, no. 1, pp. 16 – 28, February 2001.
- Ebrahim Mahdipour, Amir Masoud Rahmani and Ehsan Aminian, "Performance Evaluation of Destination-Sequenced Distance-Vector (DSDV) Routing Protocol," in proc. of the International Conference on Future Networks (ICFN 2009), Bangkok Thailand, March 2009, pp. 186 – 190.
- Hikmet Sari, Serdar Sezginer and Emmanuelle Vivier, "Full Frequency Reuse in Mobile WiMAX and LTE Networks with Sectored Cells," in proc. of IEEE Mobile WiMAX Symposium 2009, Napa Valley, California, USA, July 2009, pp. 42 – 45.
- Jeich Mar, Chin-Chung Ko, Shao-En Chen and Chung-Hao Li, “Cell Planning and Channel Throughput of Mobile WiMAX at 2.5 GHz”, Journal of Chinese Institute of Engineering (JCIE), vol. 32, no. 5, pp. 585 – 597, March 2009.
- Carl Eklund, Roger B. Marks, Kenneth L. Stanwood, Stanley Wang, "IEEE standard 802.16: A technical overview of the wirelessMANTM air interface for broadband wireless access", IEEE Communications Magazine, vol. 40, no. 6, pp. 98 – 107, Jun 2002.
- Cicconetti, C., Erta, A., Lenzini, L. and Mingozzi, E., "Performance Evaluation of the IEEE 802.16 MAC for QoS Support", IEEE Transactions on Mobile Computing, vol. 6, no. 1, pp. 26 – 38, January 2007.
- E.M. Royer and C-K Toh., “A Review of Current Routing Protocols for Ad-Hoc Mobile Wireless Networks,”. IEEE Personal Communications, vol. 6, no. 2, pp. 46 – 55, Apr. 1999.
- Chakeres, I.D. Belding-Royer, E.M., "AODV routing protocol implementation design", in proc. of the 24th International Conference on Distributed Computing Systems Workshops 2004, Santa Barbara, CA, USA, March 2004, pp. 698 – 703.
- Mohammed Tarique, Kemal E. Tepe and Mohammad Naserian, "Energy Saving Dynamic Source Routing for Ad Hoc Wireless Networks", in proc. of the Third International Symposium on Modeling and Optimization in Mobile, Ad Hoc, and Wireless Networks 2005, Trentino, Italy, April 2005, pp. 305 – 310.
- IEEE 802.16 Working Group, "IEEE Standard for Local and Metropolitan Area Networks---Part 16: Air Interface for Fixed Broadband Wireless Access Systems," IEEE Std. 802.16-2004, October 2004.
- Jenhui Chen et al., “The Design and Implementation of WiMAX Module for ns-2 Simulator," in Proc.of the ACM VALUETOOLS 2006, vol. 202, no. 5, Pisa, Italy, October 2006.


