Performance Analysis of TCP and its Enhancement for Quality of Service in Mobile Wireless Networks in Single Traffic Using Prioritised Hard Handoff (PH2)
Автор: Goudru N.G, Vijaya Kumar B.P
Журнал: International Journal of Information Technology and Computer Science(IJITCS) @ijitcs
Статья в выпуске: 5 Vol. 8, 2016 года.
Бесплатный доступ
The research activities in mobile computing and wireless networks strongly indicates that mobile computers and their wireless communication links will be an integral part of the current internet works. Communication over wireless links is characterised by limited bandwidth, high latency, high bit-error rates and temporary disconnections. Most often, networks with wireless links and mobile hosts incur significant losses due to handoff. It is also most important that in wireless environment TCP (transmission control protocol) causes degraded end-to-end performance. In this paper, we tried to give solutions to these problems. We adopt a new method to improve the end-to-end reliable transport performance in mobile wireless environment by incorporating changes to network-layer at the base station and mobile host and preserve end-to-end semantics of TCP. The methodology employs NDG (normalised delay gradient) loss-predictor function to determine congestion losses from that of transmission loss. The sender window can adjust its size depending on the loss information. If the loss is due to congestion, congestion control algorithm is invoked to decrease the flow rate. If the loss is due to handoff (transmission loss), immediate-recovery algorithm is invoked to recover the losses caused by the sender TCP. Stochastic equations are used to analyse, i) arrival rate handoff calls, ii) blocking probability of handoff request, iii) distinguish packet loss due to congestion or handoff, iv) dynamics of sender window, v) queue length at the ingress point of the BS router , vi) throughput, and vii) the losses due to congestion and handoff blocking. Our results provide better way understanding the problem of calls drop due to handoff, and providing most accurate solutions for mobile wireless system.
Base station, handoff, immediate-recovery, loss-predictor, mobile station, NDG, TCP
Короткий адрес: https://sciup.org/15012490
IDR: 15012490
Текст научной статьи Performance Analysis of TCP and its Enhancement for Quality of Service in Mobile Wireless Networks in Single Traffic Using Prioritised Hard Handoff (PH2)
Published Online May 2016 in MECS
TCP is a reliable transport protocol which performs satisfactorily in wired networks where congestion is the primary cause of packet losses. When it traverses wireless links and mobile hosts incur significant packet losses due to bit errors and handoff. In wireless environment TCP does not satisfy many of the assumptions made, causing degradation in end-to-end performance [1]. Current research activity in mobile computing and wireless networks indicates that mobility and their wireless communication links are the integral parts of the internet works. A wireless communication link is characterised by limited bandwidth, high latencies, frequent bit-error rate, and temporary disconnections. The associated network protocols and applications must deal with these characteristics to provide quality of service (QoS). In addition to this, protocols and applications must handle the situation of user mobility and handoff that occurs when users move from cell to cell in cellular wireless networks. This handoff involve transfer of communication state in network level from one base station (a router between a wired and wireless network) to another base station (BS) and often results in either packet loss or variation in packet delays. In most network systems, handoff may last between few tens to few hundreds of milliseconds. In presence of wireless characteristics, TCP explicitly assume that packet loss is due to congestion and drops its transmission window size before retransmitting packets and then initiate congestion control mechanisms. These measures results in significant degradation in the performance of TCP [2]. In this paper, we describe the design and implementation of flow based stochastic models to alleviate the degradation and present the results of several experiments by using these models. Our aim is to improve the end-to-end performance on networks with wireless links without changing the existing TCP implementations at hosts in fixed networks and without recompiling or relinking existing applications. We achieve this by simple set of modifications to the standard internet network-layer (IP) at the base station and mobile host. PH2 traffic model is used to find arrival rate of handoff calls and blocking probability of handoff calls in a cell. Blocking probability values are used to implement congestion control such as AIMD (additive increase and multiplicative decrease) mechanism. Modified-RED (random early detection) protocol is used as congestion control mechanism. NDG mechanism is used to distinguish the congestion loss from that of handoff losses by sender TCP. We found that these combinations make TCP more robust, and easy implementation. The rest of the paper is organised as follows. Section II describes on system model for mobile wireless networks, Section III presents PH2 management scheme in mobile wireless networks. We then present in Section IV simulation and performance analysis of TCP under different conditions. We conclude the paper in Section V with a summary of results.
-
II. System Model for Mobile Wireless Networks
The model proposed by Leith and Clifford [3] satisfying AIMD rule in wireless networks is, ws t(t + 1) = as ДО ТДО + Ss ДО ws i(t) (1)
The first term of right side of (1) refers to congestion control scheme (AIMD) and second term refers to transmission losses in wireless networks. The factor as,i(t) is an effective additive increase rate in packets per second, Ts(t) is the duration of congestion epoch, bs,i (t) corresponds to whether the flow experiences a packet loss or nor during the congestion event. The indexing parameters ‘s’ corresponds to wireless stations, sϵ[1,N] and ‘i’ correspond to TCP-flows.
Equation (1) can be written as, dw 1 w(t)w( t-7?(t))
"dt Ж)- 2R( t-R(t))
P w(t-R(t)) (2)
The factor BH is blocking probability of a handoff request. β is called NTG loss-predictor parameter. It has some constant rate of transmission-loss and by choice β ϵ[0,1].
The round-trip time (RTT) is given by,
R TTS ДО^^^+Т^ (3)
where T ds,i is the propagation delay of the flow-i, q s (t) denote the number of packets in the queue at station s, and Bs(t) is the service rate of the station.
The differential version of Lindley’s equation for capturing the dynamic behaviour of instantaneous queue length is given by,
8qs(t) _ N w .( t) _
Э t = Rs( t) L d,s
Where, ws(t)/Rs(t) is increase in queue length due to arrival of the packets from N- TCP flows. The down-link capacity, Cd ,s =qs(t)/Rs(t) is the decreasing factor in queue length due to servicing of the packets and delay of the packet departure from the router. The service time is variable. The mathematical version of modified-RED scheme for packets blocking probability is given by,
0,
B H (^ = bh ,
I 1 ,
q (t) E [0,tmin\ q (t)E[ tmin, W max\ (5)
q (O > Waiax
Congestion loss is assumed to take place when queue buffer of the router in the BS reaches a value of Wmax packets. The maximum buffer size, Wmax of the router is given by, Waax = "^ Й (t) + M , Where C d /S is the bandwidth delay product, M (in packets) is the buffer size of the router, R(t) is the round-trip time, Cd is the downlink bandwidth.
-
III. PH2 Management Scheme in Mobile Wireless Networks
The cellular structure of PH2 model is as show in fig.1.
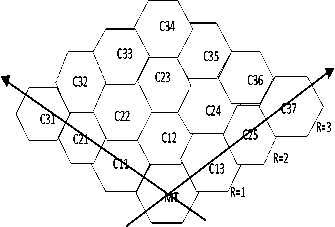
Fig.1. Cellular Structure for radius=3
In the cellular network architecture, each cell is served by a base station (BS) and the BSs are connected together by using wireless network. Mobile users are moving in the coverage area. When users are moving from one cell to another cell handoff occurs [4, 5,14,15]. The movements of mobile station (MS) or mobile caller (MC) towards or away from the mobile terminal (MT) is as shown in fig. 1.
-
A. Priority Traffic Scheme
Originating calls (λ0) are the newly generated calls in a cell. When a mobile station (MS) approaches the cell from a neighbouring cell with significant signal strength, a handoff request is generated in the cell. Let S be the number of channels in a cell. Let SR be the number of priority channels out of S channels. Priority is set to handoff request by assigning SR channel. Both originating calls and handoff requests share the remaining SC (SC=S-SR) channels. When in a cell number of available channels is less than or equal to SR, an originating call is blocked. When no channel is available in the target cell then a handoff request is failed. This is illustrated in fig. 2.
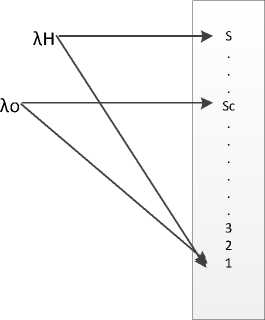
Fig.2. system model with priority for handoff calls
We define the state i(i=0,1,2,……,S) of a cell as the number of calls in progress for the BS of that cell. Let P(i) represent the steady-state probability that the BS is in state i. The probabilities P(i) can be determined using birth-death process [9, 10, 11,12,13]. The pertinent state transition diagram is as shown in fig.3.
λO+λH
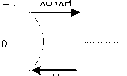
Fig.3. state transition diagram for fig. 2
From fig. 3, the state balance equations are
[ i№ (i) = (A0 + AH)P( i-1) , 0c UuP(i) = A H P(i), Sc
and Zf. oP(O = 1
The steady-state probability is calculated by using,
y°^P(0), 0 < i < Sc
P(0 = “ rsc (7)
( 0 ") / н—cP (0), S c
Where
[ ■ Г. T' ■ 5 + “' 7" I '
The blocking probability B 0 for an originating call is given by
в 0 = Zf. sc P (i) (9)
The blocking probability BH of a handoff request is given by
bh = p(^) =(0 w;,Ms "— p(0) (io)
A blocked handoff request call can still maintain the communication via current BS until the received signal strength goes below the receiver threshold or the conversation is completed.
-
B. Mathematical Description
-
a. Determination of λ H
For each cell, we consider the adjacent cell in just upper and lower levels for calculating the arrival rate of handoff calls. The generalised formula for the arrival rate of handoff calls for different radius levels r is given by
8r+2
-
b. Determination of µ
Usually one caller at a time gets serviced while the cell is changing from state (i) to (i-1). Thus, it is preferable to set the service rate µ=1.
-
c. Determination of λ 0
We assume that there is atleast one mobile caller resides in every cell at any r. So, the arrival rate of originating calls λ0 =1.
-
d. Channel Assignment
Both originating call and handoff call requests may share the same common channel. To handle handoff call needs an exclusive channel. Thus, minimum number of total channels
S=2, S R =S c =1.
-
C. Normalised Delay Gradient (NDG) as LossPredictor
Based on R. Jain [7], Saad Biaz and Nitin Vaidya [8], and David A. Hayes and Armitage [9], let, R (round-trip delay(rtt-delay)) and T (throughput) are functions of the w (sender window). To determine the Knee (the point at which throughput starts increasing), measure R and the gradient, ^ of the delay window-curve. To make the congestion avoidance feasible, adjust (increase or decrease) the window size. To determine the correct direction of the window adjustment, we use normalised dR delay gradient (NDG). The NDG=^.
Let Pi be the ith monitored packet. When acknowledgement of ith monitored packet is received then the normal delay gradient function (fNDG) is given by,
(RTTi - RTTi 1)(Wi+Wi 1) fNDG = (RTTi + RTTi 1) (Wi -Wi 1)
If load is low, NDG is low. If load is high, NDG is high. Thus, by computing (fNDG), we may be able to decide whether the next packet loss is due to congestion or transmission. Based on that information whether to increase or decrease the sender window size. When acknowledgement is received for a monitored packet P i , sender TCP calculates the quantity of NDG loss-predictor value (f ).
-
(i) If f > 0, the next packet loss is due to congestion.
-
(ii) If f ≤ 0, the next packet loss is due to handoff error.
The sender TCP use the loss predictor to recognise a particular packet was lost due to congestion or due to wireless transmission errors. The loss predictor NDG is a congestion avoidance technique.
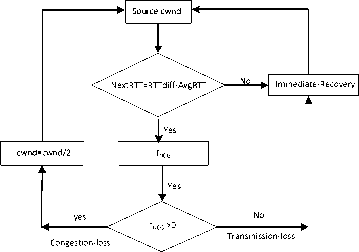
Fig.4. Flow diagram of NDG loss-predictor
-
D. Implementation of NDG Loss-Predictor in Simulation Cycle
If (f NDG > 0) % Previous packet loss is due to congestion.
β =0 % Initiates congestion control-
% algorithm using equation (2).
end
If (f NDG ≤ 0) % Previous packet loss is due to handoff.
β=0.1 % Initiates immediate-recovery
% algorithm using equation (2).
end
When the source detect that loss is due congestion, NDG parameter, β=0. The threshold value of sender window is fixed to half of the current window size and slow start phase started. When source detects that loss is due to handoff, a loss recovery module called Immediate-recovery algorithm is invoked, where sender window size is added with β-times the sending rate in the previous RTT.
-
IV. Simulation and Performance Analysis
A number of simulation experiments are conducted to evaluate the performance of TCP with NDG loss- predictor. The blocking probability BH of a handoff request is responsible for probability of packet-loss due to congestion in the queue. All simulations are performed using Matlab R2009b. TCP which has been modeled represent the last hop transmission between BS router and the destinations.
Table 1. Performance metrics of handoff parameters in different radius levels
|
r |
λ H |
B H |
fndg value |
β |
congest ionloss |
Wirele ss -loss |
|
1 |
3.3333 |
0.5263 |
-1.2934 |
0.1 |
0.0 |
75.31 |
|
2 |
3.6000 |
0.5455 |
0.3815 |
0.0 |
71.9 |
0.0 |
|
3 |
3.7143 |
0.5532 |
1.6219 |
0.0 |
71.39 |
0.0 |
|
4 |
3.7778 |
0.5574 |
2.1501 |
0.0 |
71.82 |
0.0 |
|
5 |
3.8182 |
0.5600 |
1.9032 |
0.0 |
72.28 |
0.0 |
|
6 |
3.8462 |
0.5618 |
1.5290 |
0.0 |
72.64 |
0.0 |
|
7 |
3.8667 |
0.5631 |
1.3149 |
0.0 |
72.92 |
0.0 |
|
8 |
3.8824 |
0.5641 |
1.2161 |
0.0 |
73.14 |
0.0 |
|
9 |
3.8947 |
0.5649 |
1.1682 |
0.0 |
73.31 |
0.0 |
|
10 |
3.9048 |
0.5655 |
1.1410 |
0.0 |
73.45 |
0.0 |
|
11 |
3.9130 |
0.5660 |
1.1228 |
0.0 |
73.57 |
0.0 |
|
12 |
3.9200 |
0.5665 |
1.1092 |
0.0 |
73.67 |
0.0 |
|
13 |
3.9259 |
0.5668 |
1.0986 |
0.0 |
73.76 |
0.0 |
|
14 |
3.9310 |
0.5672 |
1.0899 |
0.0 |
73.83 |
0.0 |
Table 2. Statistical results of wireless network Parameters in different radius levels
|
Radius |
RTT (sec) |
Sender window |
queuelength |
Through put |
|
1 |
0.1280 |
22.1 |
117 |
172.6 |
|
2 |
0.1354 |
19.84 |
128 |
146.55 |
|
3 |
0.1305 |
19.18 |
121 |
147.05 |
|
4 |
0.1277 |
18.99 |
116 |
148.77 |
|
5 |
0.1266 |
18.92 |
115 |
149.5 |
|
6 |
0.1261 |
18.88 |
114 |
149.75 |
|
7 |
0.1258 |
18.85 |
113.76 |
149.85 |
|
8 |
0.1257 |
18.83 |
113.5 |
149.89 |
|
9 |
0.1256 |
18.82 |
113.32 |
149.92 |
|
10 |
0.1255 |
18.81 |
113.18 |
149.93 |
|
11 |
0.1254 |
18.80 |
113.07 |
149.95 |
|
12 |
0.1253 |
18.79 |
112.99 |
149.96 |
|
13 |
0.1253 |
18.79 |
112.91 |
149.97 |
|
14 |
0.1252 |
18.78 |
112.85 |
149.97 |
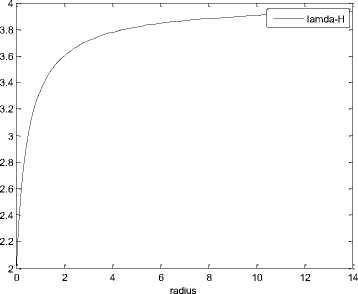
Fig.5. Arrival rate of handoff calls
The mobile caller (MC) or mobile station (MS) is moving towards or away from the MT. For each cell, we are considering the adjacent cells in just upper and lower levels for calculating the arrival rate of handoff calls. The traces of the graph of Fig. 5, demonstrate the arrival rate of handoff call request for different radius levels. The Table I , illustrates the range of values of λ H as [3.3333, 3.9310]. The behaviour of various handoff calls is established and formulated on the basis of generated priority queue.
0.6
0.58
0.56
0.54
0.52
0.5
0.48
0.46
0.44
0.42
0.4
0 2 4 6 8 10 12 14
radius
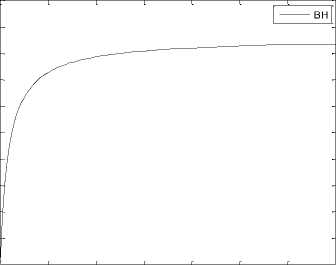
Fig.6. Growth rate of blocking probability of handoff request
The traces of the graph of Fig. 6, demonstrates the growth rate of an important performance metrics namely blocking probability for a handoff request call at different radial distances. From Table I, it varies over the range [0.5263, 0.5672].
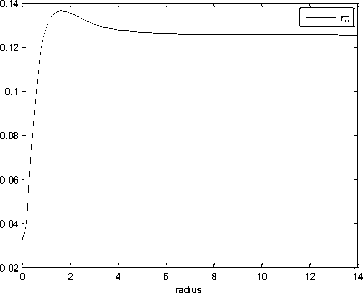
Fig.7. Variation in round-trip time
Fig.7, describes the performance of round trip time. RTT varies over the range [0.1280s, 0.1252s] with an average value of 0.1270s. The graph analysis predicts that lower the RTT value higher the end-to-end TCP performance. If the value of the new RTT sample is much lower than current RTT value, the network ignores the value of new RTT sample for some times. An effective RTT value can be used as a metrics to load balance arrival rate of handoff calls.
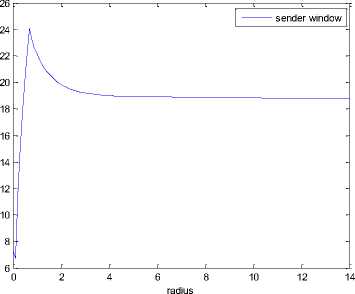
Fig.8. Sender window dynamics
Fig. 8, describes the dynamics of sender window size. It varies over the range [22.1, 18.78] packets with an average value of 19.17 packets. When source TCP recognises that packet loss is due to congestion, decrease the sender window size to half of the current value. When the sender TCP recognises that loss is due to handoff, recover immediately from one packet to the window size which was in the previous RTT. Thus, the proposed model is fine tuned for the requirements of mobile wireless environment.
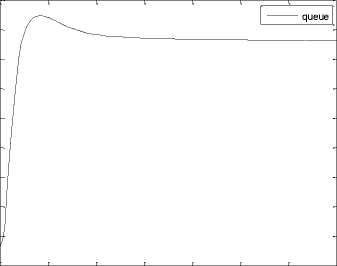
0 2 4 6 8 10 12 14
radius
Fig.9. Queue-length at the bottleneck link
140 120 100 80 60 40 20 0 -20 -40
Fig.9, illustrate the performance of instantaneous queue length due to handoff calls at the ingress point of the router present in the BS. The queue length varies between [117, 112.85] packets with an average of 115.47 packets. When the queue length is large, RTT value of the network increases and sender window size decreases. By keeping the queue length small, throughput can be increased. In this work, we use RED router in the BS. When the queue length exceeds the minimum threshold value of 100 packets, RED starts dropping of packets based on the blocking probability of handoff request. When the queue length exceeds 200 packets, all the handoff calls are dropped. It is very useful to keep queue size low to accommodate burst traffic to avoid the losses due to handoff calls.
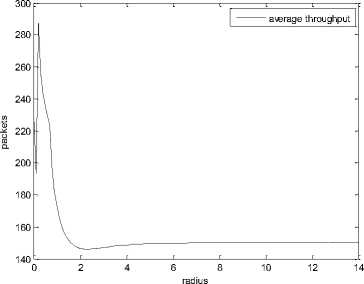
Fig.10. Performance of average throughput
Fig.10, describes the performance of average throughput. By using NDG loss-predictor, when sender TCP recognises that the loss is due to handoff, sender window gets an immediate recovery, and thereby increase throughput. The statistical results presented in table 2 illustrates that the system attains an average throughput value of 151 packets.
Congestion-loss
0 2 4 6 8 10 12 14
radius
Fig.11. Packet loss due to handoff congestion
I handoff-loss
0 2 4 6 8 10 12 14
radius
Fig.12. Packet loss due to handoff blocking
Fig. 11 and Fig.12 illustrates the congestion loss and loss due to handoff delay respectively. Handoff loss occurs in the beginning of the simulation and large part of the losses is due to congestion only.
-
V. Conclusion
A novel research work is presented in this paper. The mathematical model presented in equation (2) is an improved model of the past researcher works. The model enhances the performance of TCP in the mobile wireless networks. Our aim is to improve the end-to-end performance of TCP on networks with wireless links and mobility, without changing the existing TCP implementations at hosts in the networks and without recompiling or relinking existing applications is successfully achieved. The model has experimented through several simulations using MATLAB tools to prove that the model shows significant gain in the throughput. The results brought out in this paper can be used for improving the quality of services in heterogeneous networks with 4G, 5G and other internet technologies.
Список литературы Performance Analysis of TCP and its Enhancement for Quality of Service in Mobile Wireless Networks in Single Traffic Using Prioritised Hard Handoff (PH2)
- Hari Balakrishnan, Venkata N. Padmanabhan, Srinivasan and Randy H. Katz, “A comparision of mechanism for improving TCP performance over wireless links”, Proc. ACM SIGCOMM, Stanford, CA, August 1996.
- Hari Balakrishnan, Srinivasan Seshan, and Randy H. Katz, “Improving Reliable Transport and Handoff Performance in Cellular Wireless Networks”, ACM Wireless Networks Journal (WINET), 1(4), December 1995.
- D.J.Leith, P.Clifford. “Modeling TCP dynamics in wireless networks”, Hamilton Institute, NUI Maynooth.
- Qing-An Zeng, and Dharma P. Agarwal, “Handbook of wireless networks and mobile computing”, John Wiley and Sons, Chapter1, 2002.
- Biswajit Bhowmik, “Priority based hard handoff management scheme for minimising congestion control in single traffic wireless mobile networks”, International Journal of advancements in technology, Vol. 2, No. 1, ISSN 0976-4860, January 2011.
- Raj Jain, “A delay-based approach for congestion avoidance in interconnected heterogeneous computer networks”, ACM Computer communication review, vol. 19, pp 56-71, 1989.
- Saad Biaz, and Nitin H.Vaidya, “Sender-based heuristics for distinguishing congestion losses from wireless transmission losses”, technical report-98-013, Department of Computer Science, Texas Aand M University, USA, 2003.
- David A. Hayes and Grenville,”Revisiting TCP congestion control using delay gradient”, Centre for advanced internet architectures, Swinburne University of Technology, Melbourne, Australia, 2011.
- Biswajit Bhowmik, “A comparison study on selective traffic models with handoff management schemes for wireless mobile network infrastructure”, International journal of technology and computer science, vol.02, pp. 66-72, 2013 in MECS press.
- Biswajit Bhowmik, Pooja, Piyali Sarkar and Nupur Thakur, “Modeling prioritised hard handoff management scheme for wireless mobile networks”, International journal of computer networks and information security, vol.8, pp. 21-32, 2012 in MECS press.
- Biswajit Bhowmik, Pooja, Piyali Sarkar and Nupur Thakur, “Experimental analysis of Xie and Kuek’s traffic model handoff scheme in wireless networks”, International journal of engineering and electronic business, vol.1, pp. 34-43, 2012.
- ChengGang Liu, ZhenHong Jia, and Xi-Zhong Qin, “Improvement priority handoff scheme for multiservice wireless mobile networks”, Journal of networks, vol. 9, no.1, 2014.
- G. R. Ahmed Jamal, Tareq U. Ahmed, N. Shahadat, M. F. Islam, Marium B, “Adjusting Blocking Probability of Handoff Calls in Cellular Mobile Communication”, American Journal of Mobile Systems, Applications and Services, Vol. 1, No. 1, pp. 6-11, 2015.
- Uduak Idio Akpan, Constance Kalu, Aniebiet Kingsley Inyang, “Performance analysis of prioritized handoff schemes in wireless systems”, Communications, 2(1), 1-6, 2014.
- Nahla Nur Elmadina, R.Abdalrahman, M.Abudia and Nuha Bihary, “International Journal of Computer Science and Telecommunications”, Volume 6, Issue 5, May 2015.


