Performance Evaluation of AODV, LHC-AODV, OLSR, UL-OLSR, DSDV Routing Protocols
Автор: Reza Fotohi, Shahram Jamali, Fateme Sarkohaki
Журнал: International Journal of Information Technology and Computer Science(IJITCS) @ijitcs
Статья в выпуске: 10 Vol. 5, 2013 года.
Бесплатный доступ
Mobile ad hoc networks are type of wireless networks in which any kind of infrastructure is not used, i.e. there are no infrastructures such as routers or switches or anything else on the network that can be used to support the network structure and the nodes has mobility. The routing is particularly a challenging task in MANETs that selecting paths in a network along which to send network traffic. In this paper, the performance analysis is carried out on Ad-hoc On-demand Distance Vector (AODV), Limited Hop Count AODV (LHC-AODV), Optimized Link State Routing (OLSR), Unnecessary Loop OLSR (UL-OLSR) and Destination Sequenced Distance Vector (DSDV) protocols using NS2 simulator. The delay, throughput, and packet delivery ratio are the three common measures used for the comparison of the performance of above protocols.
MANETs, Routing protocols, AODV, LHC-AODV, OLSR, UL-OLSR, DSDV, Network simulator (NS2)
Короткий адрес: https://sciup.org/15011975
IDR: 15011975
Текст научной статьи Performance Evaluation of AODV, LHC-AODV, OLSR, UL-OLSR, DSDV Routing Protocols
Published Online September 2013 in MECS DOI: 10.5815/ijitcs.2013.10.03
Routing protocols in MANETs were developed based on the design goals of minimal control overhead, minimal processing overhead, multi hop routing capability, dynamic topology maintenance and loop prevention. Classification on routing protocols in MANETs can be done on routing strategy wise or network structure wise. According to routing strategy the routing protocols can be categorized as table-driven or proactive and source-initiated or reactive or on-demand routing. Each of these types of protocols behaves differently on different wireless conditions. Hence the performance analysis of these protocols is a must task to know its behavior and work in that environment. Several factors will affect the overall performance of any protocol operating in an ad hoc network. For example, node mobility may cause link failures, which negatively impact on routing and quality of service (QoS) support. Network size, control overhead, and traffic intensity will have a considerable impact on network scalability along with inherent characteristics of ad hoc networks may result in unpredictable variations in the overall network performance [5].
The primary objective of this paper is to evaluate and quantify the effects of various factors that may influence network performance. While there has been performance analysis of ad hoc networks [6-8], still some of the influential factor evaluation is also missing. We emphasized on the performance metrics of end-to-end delay, throughput, and packet delivery ratio. The above metrics are validated for variable network load, variable mobility and variable network size. The rest of the paper is organized as follows: Section Two clarifies the Routing protocols in Mobile Ad Hoc Networks, Section Three portrays Simulation methodology and performance metrics, Section Four discusses the simulation results and finally, section Five will present the conclusion of the present paper.
-
II. Routing Protocols in Mobile Ad-hoc Networks
-
2.1 Table Driven Routing Protocols (Proactive Model)
-
2.1.1 Destination sequence distance vector routing (DSDV)
-
2.1.2 Optimized Link State Routing (OLSR)
-
2.1.3 Proposed Unnecessary Loop-Optimized Link State Routing (UL-OLSR)
Routing in the suggested algorithm is based on routing established upon demand. Each node has a routing table in which the node keeps its own routing information. The routing table contains fields such as the destination node address, the next node address, the sequence number, the distance, the minimum requested bandwidth; the maximum permitted delay, the stream type and the route validity period. The destination node address field specifies the address of the destination node. The next node address identifies the next node on the route for sending packages to the destination. The sequence number field is used to avoid the routing loops formations and repeated transmissions. As a routing message reaches to a node, if the sequence number of the received message for a specific destination node is greater than the sequence number for that specific node in the routing table, the message will be processed. This simple act will prevent from repeatedly sending of the routing packages and avoid the creation of routing loops in routing packages transmission. The distance field specifies the route length. The minimum requested bandwidth specifies the minimum amount of bandwidth required by the stream. This field is required only in cases of service quality streams (flows which require the service quality) and will be processed only when the stream type is of quality service. The maximum permitted delay field determines the maximum tolerable delay for the service quality streams. This field is also used only when service quality streams are being sent. The stream type is determined by the stream type field. This field can have the service quality level or the best effort. This field specifies the type of requested service. The validity period field determines the period in which a route is valid. After passing this period, the route will not be valid no more. If this field receives a package for a destination before the end of validity period, the field will be re-initialized. Routing protocols in mobile ad hoc networks can be divided into two categories of table-based or proactive protocols and need-based protocols, the table-based or proactive protocols are used for periodic updating of the links, the routes information are kept in a table and are used whenever they are needed. However, need-based protocols do not require keeping the routes data, and whenever a route is needed, they start to explore a route based on the source location.
Destination sequenced distance vector (DSDV) routing protocol is a table driven routing protocol based on the classical Bellman- Ford routing algorithm. The improvement made here is the avoidance of routing loops in a mobile network of routers. Each node in the mobile network maintains a routing table for all possible destinations within the network and the number of hops to each destination node. Each entry is marked with a sequence number and this number is assigned by the destination node. A sequence numbering system is used to allow mobile hosts to distinguish stale routes from new ones. Routing table updates are periodically transmitted throughout the network in order to maintain table consistency. Large amount of network traffic, route updates can employ in two types of packets they are first is the “Full Dump” and second is the “Incremental routing”. A full dump sends the full routing table to the neighbors and could cover many packets whereas, in an incremental update only those entries from the routing table are sent that has a metric change since the last update and it must fit in a packet. When the network is relatively stable, incremental updates are sent to avoid extra Traffic and full dump are relatively infrequent. In a fast changing network, incremental packets can grow big, so full dumps will be more frequent [9].
In our suggested method, when network traffic or packet delivery rate is reduced, take a statistics from the network (sent packets, receive packets, packets delivery ratio). If sent packets, received packets and packets delivery ratio significantly are reduced, there may be a network problem such as packet loss, stuck in the closed-loop and then we decided to address these issues for remove the packets that had been in the loop. When a node sends a package to other nodes within its own radio range, packages will be transmitted by nodes called MPR to the other nodes. Consequently, if the package falls into a loop, then two cases occur; (1) if the package used less number of steps (less than 255 steps) to reach the destination, and the package is IP Header, then we set dynamically its number of steps to zero to give the package the second chance to reach the destination, and (2) if the package used more number of steps (more than 255 steps), and the subjected package isn’t IP Header, then we eliminate the package, because, otherwise, many packages will remain in the network and this will cause network traffic, bandwidth occupation, high level of delay in the package delivery, and finally, the reduction of package delivery rate and network payload rate. In our suggested method, by eliminating the unnecessary loops, the package delivery rate (PDR) and the throughput is improved by about 20 percent. In this method, by eliminating the unnecessary loops and setting conditions, we prevented from eliminating these packages and consequently improved the package delivery rate and throughput in the network [13]. Pseudo code of the proposed algorithm is as follows:
\\ p = packet
If there exists a loop, must drop the packet if (ch->pkt_num_foiwards0>255) { drop(p. DROPRTRROUTELOOP); return;
Else (ch->pkt_num_forwards() <255) {
Forward packet;
// else if this is a packet I am originating, must add IP header else if (ch->num_forwardsQ = 0)
ch->size() — IP_HDR_LEN;
}
-
2.2 On-Demand Routing Protocols (Reactive)
-
2.2.1 Ad-hoc on-demand Distance Vector (AODV)
-
2.2.2 Proposed Limited Hop Count –Ad-hoc on demand Distance Vector ( LHC-AODV)
In comparison with table-based routing protocols, in this category of protocols, not all updated routes are stored on each node; instead, the routes will be constructed whenever they are needed. When a source node wants to send one message to a destination, it will request the route discovery mechanisms to find a route to the destination (RREQ). Route remains valid until the destination is available or if is not for the long-term needs. Once a route to the destination is found, the RREP mechanism sends, in reverse, the route to the source node. CBRP, AODV, DSR, TORA & ABR are some examples of need-based protocols .
Ad hoc On-Demand Distance Vector (AODV) Routing is a routing protocol for mobile ad hoc networks (MANETs) and other wireless ad-hoc networks. It is jointly developed in Nokia Research Center, University of California, Santa Barbara and University of Cincinnati by C. Perkins, E. Belding-Royer and S. Das. It is a reactive routing protocol, meaning that it establishes a route to a destination only on demand. In contrast, the most common routing protocols of the Internet are proactive, meaning they find routing paths independently of the usage of the paths. AODV is, as the name indicates, a distancevector routing protocol. AODV avoids the counting-to-infinity problem of other distance-vector protocols by using sequence numbers on route updates, a technique pioneered by DSDV. AODV is capable of both unicast and multicast routing.
In normal situations of the AODV protocol, when a node wanted to send a packet to a destination, by sending a periodical RREQ signal to its neighbors, it would eventually find its path. Then the node that wanted to send a packet using this path, if the packet reached a loop, it had to use Hops, which in this situation traffic would occur and the bandwidth would be occupied. In our proposed method, we have limited the TTL value for the RREQ request path and considered the following two states, which TTL is very low. Considering that in this state the packet (RREQ or any other packet) does not reach a node and remained in the middle nodes, therefore it was discarded. Therefore, we did not consider this state. In the second state, the TTL is very high, meaning that we allowed a larger number of Hops. In this state, the rate of packet delivery was lowered, therefore we disregarded this state. In our proposed method, we limited the Hop counts using the following condition:
INFINITY2=FFFF
If (rt->rt_last_hop_count < INFINITY2)
{ rt->rt_req_last_ttl = max(rt->rt_req_last_ttl, rt-> rt_last_hop_count);
}
This means that if the condition applies, we consider the last hop for the last TTL (i.e. the packet has used its authorized hop). However, if the condition does not apply, meaning that the packet wants to use a larger number of hops to reach its destination, the packet is discarded, because if we increase the number of hops, it will take the packets longer to reach their destination, therefore the resulting traffic will occupy and busy bandwidth. However, we freely allow the packets requiring 255 hops or less to reach their destination. For example, when we see a packet pass the 256 threshold, we limit the hops using a certain condition, this results in improvement in packet delivery rates, throughput, good put, and jitter.
-
III. Simulation Methodology and Performance Metrics
-
3.1 The Simulation Model
-
-
3.2 The Simulation Parameters
In this simulation, we used a wireless network with MAC 802.11 standards, which is a 1000 * 1000
-
3.3 Performance Metrics
In this paper the simulation of AODV, LHC-AODV, OLSR, UL-OLSR, DSDV routing protocols is done by using network simulator (NS-2) software due to its simplicity and availability. NS is a discrete event Simulator targeted at networking research NS provides substantial support for simulation of TCP, routing and multicast routing protocols over a wired and wireless network. NS-2 is written in C++ and OTCL. C++ for data per event packets and OTCL are used for periodic and triggered event [11]. NS-2 includes a network animator called Nam animator which provides visual view of simulation. NS-2 preprocessing provides traffic and topology generation and post processing provide simple trace analysis. AWK programming is used for trace file analysis [12].
simulation environment. According to, we employed MAC 802.11 protocols for the network layer, with node transmission range of 250m, link bandwidth of 11 Mbps, and packet size of 1024 bytes and simulation time of 200s. We consider 15 random simulation runs to generate 15 random scenario patterns and the performance of the considered factor is the average of these 15 outputs. In all our experiments we considered five sample points of a particular factor and verified for three different protocols i.e. AODV, LHC-AODV,
OLSR, UL-OLSR and DSDV. Therefore 200s simulation runs were conducted to analyze each performance factor for these three protocols. Since our experiments is based on network layer characteristics so changes in routing strategy is only observed where as other characteristics like antenna gain, transmit power, ground propagation model and receiver sensitivity as physical layer characteristics, MAC 802.11 as wireless Ethernet for data link layer characteristics, UDP as transport layer characteristics and CBR as application layer characteristics remain fixed. The parameters in our simulation are reported in Table 1.
Table 1: Values of Parameters for Routing Protocols
|
Simulator |
NS2 2.32 |
|
Protocols |
AODV, LHC-AODV, OLSR, UL-OLSR, DSDV |
|
Network Type |
Mobile |
|
Connection Pattern |
Random |
|
Packet Size |
1024 byte |
|
Duration |
200s |
|
Connection Type |
CBR/UDP |
|
Simulation area |
1000 x 1000 |
|
Number of Nodes |
10, 20, 30, 40, 50, 60, 100 |
|
Pause Time |
0s, 30s, 90s, 120s, 150s, 170s, 200s |
PDR is the ratio of the number of data packets received by the destination node to the number of data packets sent by the source mobile node. It can be evaluated in terms of percentage (%). This parameter is also called as “success rate of the protocols”:
PDR ( Sent Packet No ^100
I Receive Packet No /
Where PDR is the package delivery rate, Sent Packet No is the number of sent packages, and Receive Packet No denotes the number of received packages.
Throughput it is the amount of data transferred over the period of time expressed in bits per second or bytes per second. The following formula shows how to calculate the throughput:
X = C
T
Where X is the throughput, C is the number of requests that are accomplished by the system, and T denotes the total time of system observation.
End to End Delay is the time taken for an entire message to completely arrive at the destination from the source. Evaluation of end-to-end delay mostly depends on the following components i.e. propagation time (PT), transmission time (TT), queuing time (QT) and processing delay (PD). Therefore, EED is evaluated as:
EED = PT + TT + QT + PD (3)
-
IV. Simulation Results
In graphs, we presented the results for simulation of performance of the AODV, LHC-AODV, OLSR, UL-OLSR, DSDV routing protocols by increasing the number of nodes from 10 to 100 and in times from 0 until 200s in a dynamic topology and with the criteria of packet delivery ratio, End to End Delay and throughput.
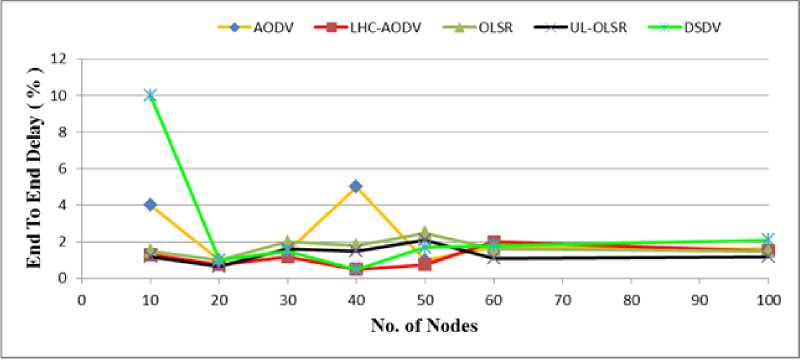
Fig. 1: E2E Delay Comparisons of AODV, LHC-AODV, OLSR, UL-OLSR, DSDV for Nodes 10-100
Fig. 1 shows the assessment of E2E criterion against the number of nodes. It shows that the UL-OLSR protocol has better performance than other protocols in terms of delay. But in the distance of 20 to 60 nodes, the delay of UL-OLSR protocol has increased, while LHC-AODV and DSDV protocols have done better in this distance and they have lower-level of delay than
UL-OLSR protocol. The reason for the lower delay of UL-OLSR protocol E2E is the omission of unnecessary rings, which cause the packets not to remain in the waiting ring. The reason for the lower delay of LHC-AODV protocol is the limiting of the number of steps, which cause the packets to be sent by the optimized route.
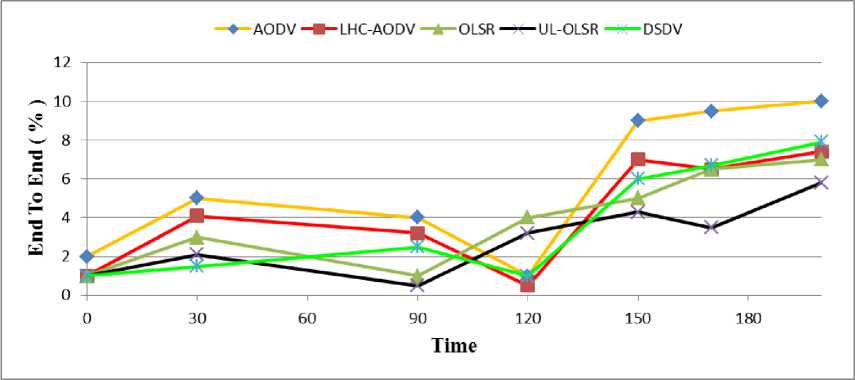
Fig. 2: E2E Delay Comparisons of AODV, LHC-AODV, OLSR, UL-OLSR, DSDV for Times 0-200s
Fig. 2 shows the assessment of E2E against time. It shows that, between the times 0 to 60, the DSDV protocol had a lower delay, while the delay of UL-OLSR protocol in these times (0 to 60) and 120 seconds has increased. But in other times till 200 seconds, the delay of UL-OLSR protocol E2E has decreased and it has better performance. The DSDV protocol E2E has lower delay because it is table driven, for it has more routes in its routing table that has already been found. Therefore, this protocol sends the packets to the desired destinations faster, with no need to route discovery process.
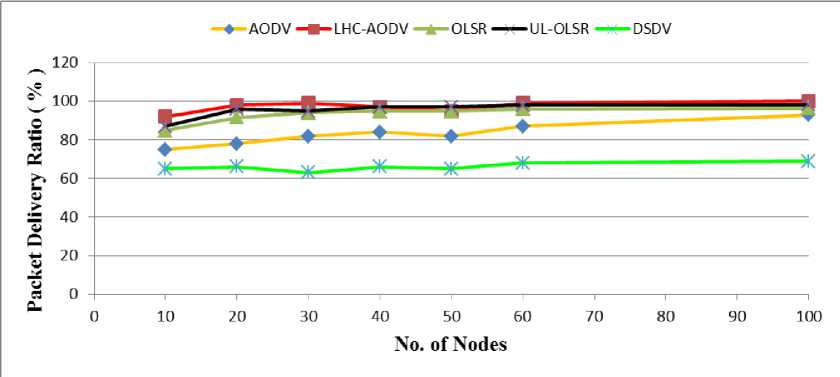
Fig. 3: PDR Comparisons of AODV, LHC-AODV, OLSR, UL-OLSR, DSDV for Nodes 10-100
Fig. 3 shows the assessment of PDR against the number of nodes. It shows that the DSDV protocol has the lower PDR compared to other protocols, while LHC-AODV shows a better PDR in the nodes ranging from 0 to 100. The higher PDR in LHC-AODV protocol can be explained as follows: In standard AODV routing protocol, packets used more steps without limitation, thus there might be a very long step that would lead to a lower rate in PDR. We have limited the number of steps in our LHC-AODV, so that a larger number of packets would be sent to their destinations, and we omit the packets that use more steps unreasonably.
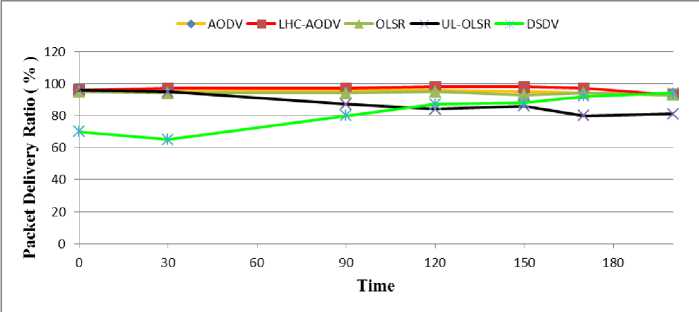
Fig. 4: PDR Comparisons of AODV, LHC-AODV, OLSR, UL-OLSR, DSDV for Times 0-200s
Fig. 4 shows the assessment of PDR against time. It shows that UL-OLSR and DSDV protocols PDRs have decreased drastically and they show worse performance compared to other protocols, while LHC-AODV protocol shows better performance in the time range of 0 to 200 seconds.
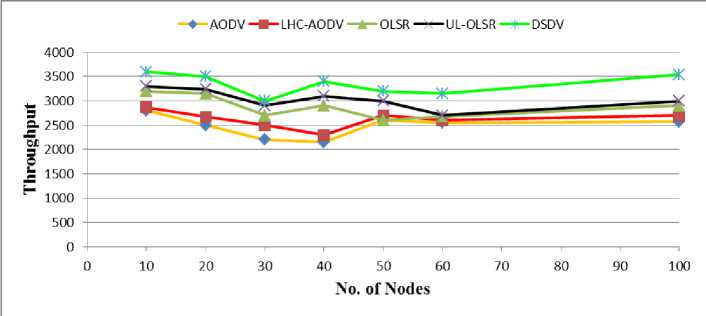
Fig. 5: Throughput Comparisons of AODV, LHC-AODV, OLSR, UL-OLSR, DSDV for Nodes 10-100
Fig. 5 shows the Throughput against the number of nodes. It shows that the DSDV protocol has the higher
Throughput and standard AODV has the worst performance in the Throughput criterion.
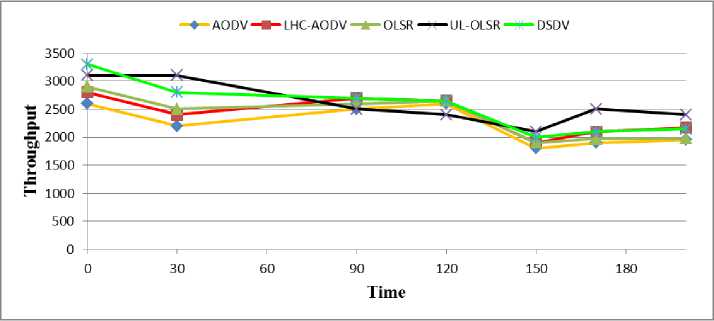
Fig. 6: Throughput Comparisons of AODV, LHC-AODV, OLSR, UL-OLSR, DSDV for Times 0-200s
Fig. 6 shows the Throughput against time. It shows that DSDV protocol has a better Throughput in the time range of 0 to 150 seconds. But in the time range of 150 to 180 seconds the Throughput of this protocol has reduced, and its performance decreases. On the contrary, in the time range of 150 to 180 seconds, UL-OLSR protocol shows the better Throughput.
-
V. Conclusion
In this paper we evaluated the three performance measures i.e. PDR, End to End delay and Throughput with different number of nodes, different Speed pause time of nodes, we have assessed the performance of five routing protocols of AODV, LHC-AODV, OLSR, UL-OLSR and DSDV in one scenario with 10 to 100 nodes and in various times between 0 to 200 seconds. As shown in simulation results section, LHC-AODV routing protocol had the better packet delivery rate (PDR) than other protocols. UL-OLSR protocol has also shown better results in E2E delay compared to other protocols, but in the range between nodes number 20 to 60, the UL-OLSR protocol delay has increased. Although LHC-AODV and DSDV have better performance in the same range, and have got the lower delay than UL-OLSR protocol. Also in the span of 0 to 150 seconds, the DSDV protocol has had a better Throughput, but between 150 to 180 seconds its Throughput has reduced and its performance has decreased. While the UL-OLSR protocol has shown a better Throughput in the times ranging from 150 to 180 seconds. In conclusion, it can be said that LHC-AODV and DSDV protocols have got good Throughput performance in short times, but they lose most of their performance in long terms. In 0 to 200 seconds, LHC-AODV protocol has good (PDR) performance, and UL-OLSR has better (End to End) and (Throughput) in longer period of time.
Список литературы Performance Evaluation of AODV, LHC-AODV, OLSR, UL-OLSR, DSDV Routing Protocols
- Y. Ge, T. Kunz, L. Lamont, Proactive QoS routing in ad-hoc networks in: Proceedings of the 2nd International Conference on Ad-Hoc Networks and Wireless, Montreal, Canada, October 2003
- Ivascu G. L., Pierre S., Quintero A., "Qos Support based on a Mobile Routing Backbone for Ad Hoc Wireless Networks", IWCMC, Canada, July 2006
- T. Clausen, P. Jacquet, Optimized link state routing protocol, IETF RFC3626, 2003.
- Li Tingjun, Lin Xueyuan, “GPS/SINS Integrated Navigation System Based on Multi-Scale Preprocessing”, Journal of Wuhan University, 2011, Vols 36(1): pp6-9
- S. Mohapatra, P. Kanungo, Performance analysis of AODV, DSR, OLSR and DSDV Routing Protocols using NS2 Simulator, Elsevier Procedia Engineering 30 (2012) 69-76
- Tuteja A, Gujral A, Thalia A, “Comparative Performance Analysis of DSDV, AODV and DSR Routing Protocols in MANET using NS2”, IEEE Comp. Society, 2010, pp. 330-333.
- Broach J, .Maltz D.A, Johnson D.B, Hu Y and Jetcheva J, “A Performance comparision of Multihop Wireless Ad-Hoc Network Routing Protocols”, ACM MOBICOM, 1998.
- Boukhalkhal A, Yagoubi M.B., Djoudi D, Ouinten Y and Benmohammed M, “Simulation of Mobile Adhoc Routing Strategies” , IEEE, 2008, pp.128-132.
- Zygmunt J. Haas, Jing Deng, Ben Liang, Panagiotis Papadimitratos, and S. Sajama, “Wireless Ad Hoc Networks” Cornell University School of Electrical and Computer Engineering, 2004.
- P.Jacquet, P. Muhlethaler. A. Laouiti, L.Viennot,T. Clauseen, "Optmized Link State Routing Protocol draft-ietf-manet-olsr 05.txt", INTERNET-DRAFT,IETF MANET working group.
- C.E. Perkins and E.M. Royer, “Ad-hoc on Demand Distance Vector Routing Protocols”, in proceeded 2nd IEEE work shop mobile computing system and applications, new ore leans, Loss Angelis, pp 90-100, February 2011.
- Md Shohidul Islam, Md Naim Hider, Md. Touhidul Haque, Leton miah “An Extensive Comparison among DSDV, DSR and AODV Protocols in MANET, “International journal of computer application (0975-8887) Volume 15-no.2, February 2011.
- Shahram Behzad, Reza Fotohi, Shahram Jamali,"Improvement over the OLSR Routing Protocol in Mobile Ad Hoc Networks by Eliminating the Unnecessary Loops", IJITCS, vol.5, no.6, pp.16-22, 2013. DOI: 10.5815/ijitcs.2013.06.03


