Quantum-dot cellular automata based fragile watermarking method for tamper detection using chaos
Автор: Turker Tuncer, Sengul Dogan
Журнал: International Journal of Information Technology and Computer Science @ijitcs
Статья в выпуске: 12 Vol. 10, 2018 года.
Бесплатный доступ
Fragile watermarking techniques have been widely used in the literature for tampered areas localization and image authentication. In this study, a novel quantum-dot cellular automata based fragile watermarking method for tampered area localization using chaotic piecewise map is proposed. Watermark generation, embedding, extraction and tampered area localization phases are consisted of the proposed quantum dot cellular automata and chaos based fragile watermarking method. In the watermark generation phase, quantum dot cellular automata and piecewise map which is a chaotic map are utilized. A block based method is utilized as authentication values embedding and extraction phases. To detect tampered areas, generated watermark and extracted watermark are compared. Also, block counters are used to tamper detection. In order to evaluate this method, capacity, imperceptibility and image authentication ability were utilized as performance metrics and the results of these metrics clearly illustrated that the presented method is suitable for image authentication and tamper detection.
Fragile watermarking, quantum-dot cellular automata, chaotic maps, tamper detection, information security
Короткий адрес: https://sciup.org/15016322
IDR: 15016322 | DOI: 10.5815/ijitcs.2018.12.04
Текст научной статьи Quantum-dot cellular automata based fragile watermarking method for tamper detection using chaos
Published Online December 2018 in MECS DOI: 10.5815/ijitcs.2018.12.04
Internet usage is common and cheap nowadays. People share a lot of data using internet-connected smartphones every day. Identification of these data is an important research area of today [1]. Watermarking is used to determine the ownership of the electronic medias. A watermarking system is given Fig. 1 [2] [3].
Watermark methods can be classified as follows [4]:
-
• Document type: Image, video, text, voice, audio, etc.
-
• Information variation: blind, half-blind, non-blind
-
• Human perception: invisible, visible
-
• Domain: transformation, spatial
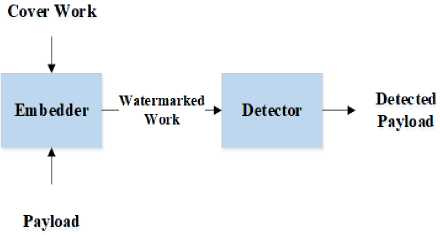
Fig.1. The general graphical outline of the watermarking model.
These methods have been varied according to the purpose of the watermarking in the literature. For example, in determining the owner of the data, it may be desirable that the marker be visible or invisible. At the same time, the user may prefer to image or text as marker [5] [6] [7].
It is desirable that a watermarking algorithm be resistant to attack so that the marker on the watermarked object is preserved. watermark embedding techniques are designed in literature [8] [9]. In the image watermarking applications, image is most used media in the literature. Arora et al. [10] suggested a hybridized watermarking technique. The marker was embedded to both spatial domain and frequency domain using Singular Value Decomposition (SVD) and Discrete Wavelet Transform (DWT) in their proposed method. Seetha et al. [11] presented a watermarking techniques for Drug’s images. This method involved transparent digital watermarking techniques by using Alpha Channels and Alpha Blending techniques. In order to measure the durability of the method, the crop attack was performed in curve, brightness, contrast, invert and color balance. Xie et al. [12] suggested a new technique to prevent counterfeiting for QR codes. In their watermarking method, DWT was used to separate into non-overlapping rectangular areas.
The marker was embedded to multi-channel in cover image. Roy et al. [13] analyzed the impact of attacks in watermarking techniques and a robust watermarking method was proposed to increase robustness against this attack. Moosazadeh and Ekbatanifard [14] proposed a robust watermarking techniques for images. In their method, YCoCg-R color space, Arnold transform map and Discrete Cosine Transform (DCT) were used to increase robustness. YCoCg-R color space and DCT provided robustness and Arnold transform ensured security of this method.
-
A. Motivation and Contributions
In this study, a novel quantum-dot cellular automata and chaos based fragile watermarking method for tampered area localization.
The contributions of this paper are given as below.
-
• The quantum computation is a popular research area for information technologies. In this paper, quantum dot cellular automata are used to watermark generation phase of an image
authentication method. Quantum dot cellular automata generally used for CMOS technologies. The polarization equation of the Quantum-dot cellular automata is used for watermark generation. In this view, this paper presents the first Quantumdot cellular automata based fragile watermarking method for image authentication as we know.
-
• In order to provide security of the proposed method chaotic maps are used to encrypt watermark. In this work, quantum and chaos are used together and they provided to present a successful image authentication method.
-
B. Organization
The organization of the rest of this article is given as follows. The quantum-dot cellular automata are presented in Section 2, the piecewise chaotic map is given in the Section 3, the proposed method is explained in Section 4, experimental results are discussed in the Section 5, conclusions and recommendations are given in Section 6.
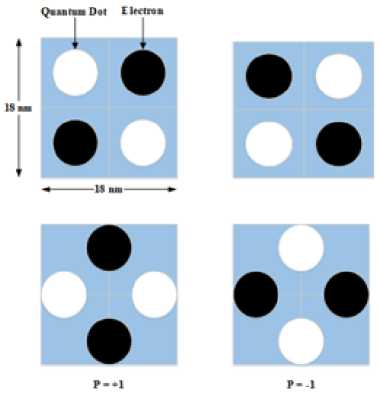
Fig.2. The samples of quantum cells.
In this paper, QCA is used for watermark generation.
-
III. Piecewise Linear Chaotic Map
0.5-p1
”
Piecewise linear chaotic map (PLCM) is one of the widely used chaotic map in the literature. Chaos is very popular research area and it uses in optimization, cryptography, SBOX generation, random number generation, etc. Therefore, PLCM utilized as a pseudo random number generator (PRNG) for diffusion in this paper. The mathematical definition of the PLCM is given as below [17].
x „+i = F(x n ,p) =
—, 0 < xn < p
p
^-,p < xn < 0.5
0,xn = 0.5
VF(1 - xn, p), 0.5 < xn < 1
Where p is piecewise value and p= (0,0.5), x 0 is starting value and x 0 = (0,1). F represents four segmented PLCM function.
-
II. Quantum-Dot Cellular Automata
Quantum-dot Cellular Automata (QCA) have been presented for electronic circuits and CMOS technologies. QCA consists of square shapes (cells) and each of them is nano-sized and a QCA cell consists of 4 quantum dots. These dots occupied by a pair of electrons and these placed diagonal due to coulomb repulsion. To measure this alignment, Eq. 1 is used [15].
P =
P 1 +P 3 -P 2 -P 4
P 1 +P 2 +P 3 +P 4
Where P measure polarity and pi are probability of presence an electron in quantum cell. The QCA cells samples are shown in Fig. 2 [16].
-
IV. The Proposed Fragile Watermarking Method
In this paper, a novel QCA and PLCM based fragile watermarking method is presented. The components of the proposed method are authentication values (watermark) generation, embedding, extraction and tampered area localization. They are explained in the subsections.
-
A. Watermark Generation
In this phase, QCA and PLCM used for watermark generation. Firstly, 2MSBs (most significant bit) are calculate for each pixel and probability of these values are calculated as using histogram. Then, secondary image is created by using these probabilities and secondary image is divided into 2 x 2 size of non-overlapping block to create a quantum cell. To calculate polarity of each cell,
Eq. 1 is used and polarities are normalized. After that, PLCM is utilized as PRNG and 2 bits values are generated. The generated random values and normalized polarities are XOR in diffusion section to generate watermark. The steps of the proposed watermark generation are given as below.
Step 1: Load cover image.
Step 2: Calculate 2MSBs of the cover image.
"'=13 (3)
Step 3: Divide MI into 2 x 2 sized non-overlapping blocks
Step 4: Calculate polarity of each block using QCA and Eq. 1.
Step 5: Create secondary image using Eq. 4.
57 = round(3 P-Pmin ) (4)
^ max ^ min
Step 6: Generate random numbers using Eq. 2.
Step 7: Generate watermark using Eq. 5.
wm = SI © rv (5)
Where wm is watermark, SI is secondary image, rv randomly generated values.
-
B. Watermark Embedding
In this study, block based watermark embedding algorithm is used. To embed watermark, 2 x 2 size of blocks are utilized. The block based methods improve fragility and imperceptibility of the watermarking. The pseudo code of the watermark embedding procedure is illustrated in Algorithm 1 [17].
Algorithm 1. Pseudo code of the block based watermark embedding method.
Input: Cover image (CI) with size of M x N, watermark (wm) size of M/2 x N/2, Output: Watermarked image (WI) with size of M x N. 1:WZ = [2]x2
-
2: row=l;
-
3: for i=l to M step by 2 do
-
4: col=l;
-
5: for j=l to N step by 2 do
-
6: value = W7nrou,coj
_ I value I
-
7: r = hrl;
-
8: c = value (mod 2)
-
9: if WIi+r j+c > 0 then
-
10: W/i+rJ+c = WIt^c - 1;
-
11: else
-
12: WZi+rJ+c = WIi+rJ+c + 1;
-
13: endif
-
14: c=c+l;
-
15: endforj
-
16: r=r+l;
-
17: endfor i
-
C. Watermark Extraction
In order to watermark extraction, a block based method is presented. The pseudo code of the proposed method is given as Algorithm 2 [18].
Algorithm 2. Pseudo code of the block based watermark extraction method.
Input: Cover image (WI) with size of M x N Output: Watermarked (wm) with size of M/2 xN/2.
l:M = g],2
-
2: row=l;
-
3: for i=l to M step by 2 do
-
4: col=l;
-
5: for j=l to N step by 2 do
-
6: counter = 0;
-
7: fork=0toldo
8: for 1=0 to 1 do -
9: if WI1+k]+l (mod 2) = 1 then
-
10: wm^ = counter;
-
11: break;
-
12: endif
-
14: counter=counter+l;
-
15: endfor 1
16: endfork -
17: c=c+l;
-
18: endfor j
-
19: r=r+l;
-
20: endfor i
-
D. Tamper Detection
In order to tampered area localization, firstly control counters are used. For each block, 3 pixels must be even and a pixel must be odd. Then, watermark generation and watermark extraction algorithm are implemented. To detect tampered areas, extracted and generated watermarks are matched. Steps of the tamper detection algorithm of the QCA and PLCM based watermarking method.
Step 1: Divide watermarked image into sized nonoverlapping blocks.
Step 2: Count even and odd pixels and detect tampered areas using Eq. 6.
([0 u
Tl t:.i+l,j:.j+1 =
°, counterePen = 3 and counterodd = 1
1], counterePen * 3 or counterodd * 1
Step 3: Apply watermarking generation algorithm to watermarked image.
Step 4: Extract watermark from watermarking image using Algorithm 2.
Step 5: Detect tampered areas using Eq. 7.
1 Iv.l+1,j:j + 1 = {[1
0 ],ew = gw
1],ew * gw
Where ew is extracted watermark and gw is generated watermark [19].
V. Experimental Results
In order to measure performance metrics of the proposed method, the test image which are shown in Fig. 3 and capacity, imperceptibility and image authentication ability are used.
B. Imperceptibility
To measure imperceptibility, peak signal-to-noise ratio (PSNR) is generally used and mathematical description of the PSNR are given as Eq. 8 [21].
PSNR = 10
2552 ХМ X N logi0 vm vn v
1 4=1 ^ j=1 V CIl,j-WIl,j )


In this paper, block based watermark embedding algorithm is utilized as data hiding function. This algorithm uses ±1 operator for embedding watermark and Therefore, the theoretical worst PSNR is calculated as 2552
10log10—— = 48.13 . The practical PSNR results were obtained from test images and imperceptibility results of the 8 gray level test images are listed in Table 1.


(d)

(e)

(f)
Table 1. PSNR Values of the Proposed QCA and PLCM based Fragile Watermarking Method.
|
Images |
PSNR |
|
Parrot |
51.19 |
|
Baboon |
51.22 |
|
Lena |
51.18 |
|
Crowd |
51.17 |
|
Peppers |
51.18 |
|
Sailboat |
51.20 |
|
F16 |
51.17 |
|
Couple |
51.16 |
|
Average |
51.18 |
To better understand to visual quality effectiveness of the proposed method, a few previously presented methods in the literature were used to obtain comparisons. The comparison results were listed in Table 2.

(g)

(h)
Table 2. The imperceptibility comparison results
|
Chang et al.’s method [22] |
Wu and Lin’s 1 Scheme [23] |
Wu and Lin’s 2 Scheme [23] |
Tuncer’s method [24] |
The proposed method |
|
|
Lena |
42.28 |
51.10 |
51.15 |
51.18 |
51.18 |
|
Baboon |
42.31 |
51.10 |
51.15 |
51.17 |
51.22 |
|
Peppers |
42.30 |
51.12 |
51.12 |
51.17 |
51.18 |
|
F16 |
42.27 |
51.14 |
51.14 |
51.17 |
51.17 |
Fig.3. The gray level test images (a) Parrot, (b) Baboon, (c) Lena, (d) Crowd, (e) Peppers, (f) Sailboat, (g) F16, (h) Couple
Size of these test images is 512 x 512 and these are gray level images. The performance metrics are given as below.
A. Capacity
Capacity is one of the most used performance metric for image authentication and watermarking method. In this paper, 2 bits watermark is embedded into 2 x 2 sized non-overlapping blocks. Therefore, the capacity of the proposed QCA and PLCM method is calculated as
-
2 x y x у
- Table 2 demonstrated that the proposed method has best visual quality among the others and these results proved the effectiveness of the proposed method in view visual quality.
-
C. Image Authentication Ability
The most important evaluation criteria are image authentication ability for image authentication methods. In order to measure this metric, detection rate (DR) is used and the mathematical description of the DR is given as Eq. 9.
DR
Detected pixels A11 m о d if ie d p ixe Is
To evaluate this capability, an attack which is shown in Fig.4 was used.

(a)

(b)

(c)
Fig.4. The attack for evaluation image authentication capability (a) original image (b) attacked image (c) tampered area
In this attack, DR is calculated as 0.94.
The capacity, imperceptibility and image authentication ability results are clearly illustrated that the QCA and PLCM based method is successful fragile watermarking method.
-
VI. Conclusions and Recommandations
In this paper a novel quantum based watermarking method is presented for tampered areas localization using chaos. This method uses QCA and PLCM for watermark generation and generated watermarks are embedded into images using block based data hiding method. Block based data hiding method improves imperceptibility and fragility. The proposed method is the first method to use quantum and chaos together up to now. In the experimental results section, payload, imperceptibility and image authentication were used to evaluate performance of this method and this section showed that, this method has high capacity, visual quality and image authentication ability.
In the future studies, novel chaotic quantum based image authentication, data hiding and watermarking methods may be presented in the literature.
Список литературы Quantum-dot cellular automata based fragile watermarking method for tamper detection using chaos
- V. Potdar, S., Han, E. Chang, “A survey of digital image watermarking techniques”. In 3rd IEEE International Conference on Industrial Informatics (INDIN 2005), pp. 709-716, IEEE, 2005.
- C. Honsinger, Digital watermarking. Journal of Electronic Imaging, 11(3), 414, 2002.
- I. Cox, M. Miller, J. Bloom, J. Fridrich, T. Kalker, “Digital watermarking and steganography”. Morgan kaufmann, 2007.
- S. Dogan, T. Tuncer, E. Avci, A. Gulten, “A robust color image watermarking with Singular Value Decomposition method”. Advances in Engineering Software, 42(6), pp.336-346, 2011.
- F. Hartung, B. Girod, “Watermarking of uncompressed and compressed video”. Signal processing, 66(3), pp. 283-301, 1998.
- M. Barni, F. Bartolini, V. Cappellini, A. Piva, “A DCT-domain system for robust image watermarking”. Signal processing, 66(3), pp. 357-372, 1998.
- C. S. Collberg, C. Thomborson, “Watermarking, tamper-proofing, and obfuscation-tools for software protection”. IEEE Transactions on software engineering, 28(8), pp. 735-746, 2002.
- C. W. Tang, H. M. Hang, “A feature-based robust digital image watermarking scheme”. IEEE transactions on signal processing, 51(4), pp. 950-959, 2003.
- P. Dong, J. G. Brankov, N. P. Galatsanos, Y. Yang, F. Davoine, “Digital watermarking robust to geometric distortions”. IEEE Transactions on Image Processing, 14(12), pp. 2140-2150, 2005.
- S. M. Arora, “A DWT-SVD based Robust Digital Watermarking for Digital Images”. Procedia Computer Science, 132, 1441, 2018.
- C. Seetha, S. Goollawattanaporn, C. Tanprasert, “Transparent Digital Watermark on Drug's Images”. Procedia Computer Science, 21, pp. 302-309, 2013.
- R. Xie, C. Hong, S. Zhu, D. Tao, “Anti-counterfeiting digital watermarking algorithm for printed QR barcode”. Neurocomputing, 167, 625-635, 2015.
- R. Roy, T. Ahmed, S. Changder, “Watermarking through image geometry change tracking”. Visual Informatics, 2018.
- M. Moosazadeh, G. Ekbatanifard, “An improved robust image watermarking method using DCT and YCoCg-R color space”. Optik-International Journal for Light and Electron Optics, 140, pp. 975-988, 2017.
- M. B. Khosroshahy, M. H. Moaiyeri, S. Angizi, N. Bagherzadeh, K. Navi, “Quantum-dot cellular automata circuits with reduced external fixed inputs”. Microprocessors and Microsystems, 50, pp. 154-163, 2017.
- S. Seyedi, N. J. Navimipour, “An optimized design of full adder based on nanoscale quantum-dot cellular automata”. Optik-International Journal for Light and Electron Optics, 158, pp. 243-256, 2018.
- Y.F. Wang, M.D. Xie, A.M. Ji, Research on a Piecewise Linear Chaotic Map and Its Cryptographical Application, Fourth International Conference on Fuzzy Systems and Knowledge Discovery (FSKD 2007), 24-27 Aug. 2007, Haikou, China.
- T. Tuncer, Y. Sönmez, Block based data hiding method for images, European Journal of Technique, (2017) 7(2) 85-95.
- T. Tuncer, A probabilistic image authentication method based on chaos, Multimedia Tools and Applications, 2018, https://doi.org/10.1007/s11042-017-5569-x.
- S. K. Lee, Y. H. Suh, Y. S. Ho, Reversiblee image authentication based on watermarking. In Multimedia and Expo, 2006 IEEE International Conference on IEEE, pp. 1321-1324, 2016.
- A. M. Alattar, “Reversible watermark using the difference expansion of a generalized integer transform”. IEEE transactions on image processing, 13(8), pp. 1147-1156, 2004.
- C.C. Chang, Y.P. Hsieh, C. H. Lin, Sharing secrets in stego images with authentication. Pattern Recogn, 41(10):3130–3137, 2008.
- W. C. Wu, Z. W. Lin, SVD-based self-embedding image authentication scheme using quick response code features. J Vis Commun Image R 38:18–28, 2016.
- T. Tuncer, A probabilistic image authentication method based on chaos. Multimedia Tools and Applications, 1-18, 2018.


