Robust, Secure and High Capacity Watermarking Technique based on Image Partitioning-Merging Scheme
Автор: Baisa L. Gunjal
Журнал: International Journal of Information Technology and Computer Science(IJITCS) @ijitcs
Статья в выпуске: 4 Vol. 8, 2016 года.
Бесплатный доступ
This paper presents secure and high capacity watermarking technique using novel approach of Image Partitioning-Merging Scheme (IPMS). The IPMS is used as reduction method to reduce the size of watermark logically and increases security levels of proposed watermarking technique. The technique effectively uses special properties of Discrete Wavelet Transform (DWT), Fast Walse Hadamrd Transform (FWHT), Singular Value Decomposition (SVD) and proved strongly robust to 14 noise addition and filtering attacks. Fibonacci Lucas Transform (FLT) is used as effective scrambling technique to scramble the watermark to provide additional security in embedding process. Many researchers failed to achieve imperceptibility and robustness under high watermark embedding scenario with strong security provision as these quality parameters conflict each other. The novel technique presented here archives imperceptibility, high capacity watermark embedding, security and robustness against 14 noise addition and filtering attacks. The technique is non-blind and tested with grey scale cover images of size 512x512 and watermark images of size 512x512. The experimental results demonstrate that Lena image gives 75.8446dBs imperceptibility which is measured in terms of Peak signal to noise ratio. The robustness is measured in terms of normalized correlation (NC) equals to 1 showing exact recovery of watermark. The method is found strongly robust against noise addition and filtering attacks with compared to existing watermarking methods under consideration.
IPMS, Fibonacci-Lucas transform, Singular Value Decomposition, Hadamard transform
Короткий адрес: https://sciup.org/15012478
IDR: 15012478
Текст научной статьи Robust, Secure and High Capacity Watermarking Technique based on Image Partitioning-Merging Scheme
Published Online April 2016 in MECS
Digital communication has become the daily need in all over the world in 21st century. The billions of bits of multimedia information such as text, images, audios and videos are transmitted at every fraction of seconds. This takes sensitive and important digital data and owners’ rights in risk zone. The multimedia information protection techniques include steganography techniques, watermarking techniques, encryption techniques and other information hiding techniques. Digital image watermarking provides copyright protection to digital data by hiding owner’s rightful information in original image data without degradation of perceptual quality. Imperceptibility, robustness, security and capacity are major quality metrics used worldwide for evaluation of watermarking scheme under consideration [1]. Imperceptibility is measured in terms of peak signal to noise ratio measures perceptual quality of image. The quality of host image should not be destroyed after embedding watermark into it. Robustness is measured by normalized correlation. Watermark should be difficult to remove or destroy because of intentional or unintentional attack. Capacity measures amount of watermark information that can be embedded into cover image. Security implies that watermarking technique should be designed so that it cannot be easily detected. The great challenge in digital image watermarking is to achieve imperceptibility, robustness and security under high capacity watermark hiding because these quality parameters conflict each other. The watermarking based security solutions are used in all application areas of human life. The candidate example include image copyright communication for right management and protection, central bureau investigations (CBI) and other crime investigation agencies, multimedia message service (MMS) in mobile phones, android based applications used in mobile phones using Java programming language, nationwide and worldwide E-voting systems used in parliamentary, presidential or municipal, nationwide and worldwide distance education, health insurance companies, car insurance companies for decisions for accidental medical allowances, accidental damaged vehicles and secured passport identifications, e-health technology with telepathy, teleradiology, telecare, teleneurology, telesurgery, medical images. Obama administration is offers $44,000 to $ 64,000 for promoting Electronic Medical Record (EMR) based systems by physicians in medical practices [2]. Hence, secure, robust and high capacity watermarking is need of time in digital era. The rest of the paper is organized into different sections. Section II elaborates related work of existing watermarking techniques. Section III gives mathematical background including IPMS, DWT, FWHT, SVD and FLT. In Section IV, proposed IPMS based methodology in DWT-FWHT-SVD domain with watermark embedding algorithm and watermark extraction algorithm is elaborated. The experimentation and results are presented in section V which explores performance evaluation metrics, details of IPMS based scheme in DWT-FWHT-SVD domain, relative impact of imperceptibility and robustness, robustness of proposed method, comparative imperceptibility and watermark embedding capacity, comparative robustness with existing methods. The conclusions are drawn in section VI and future scope is presented in section VII.
-
II. Related Works
The survey presented here is broadly categorized based on types, special properties, scope and application areas of watermarking techniques.
-
A. Fragile and semi fragile image watermarking
The robust lossless semi-fragile watermarking techniques are given in [3][4]. The fragile techniques fail to extract exact watermark from watermarked image in case if changes are made to watermarked image. Thus, Fragile watermarking techniques are sensitive to intentional or unintentional attacks to image modifications.
-
B. Blind and non-blind watermarking techniques.
The non-blind watermarking techniques are popular but they require original cover image during watermark extraction process. The blind techniques do not require original cover image during watermark extraction process. A blind watermarking technique for 3D images is presented in [5].
-
C. Spatial and transform watermarking techniques
Least significant bit [LSB] and most significant bit [MSB] based insertions are examples of spatial domain techniques. The LSB based technique is presented in [6]. These techniques are simple in implementation but they can be easily detected. They are less secured and support low payload hiding capacity, less perceptual quality of watermarked image and provide less correlation between embedded and extracted watermark. In transform domain, the watermark is spread to entire cover image. These techniques provide more robustness against various attacks and support more watermark information hiding capacity. Most of the researchers focus on transform domain watermarking techniques. The example of such techniques are presented in [1][7].
-
D. Spread Spectrum (SS) and Quantization based Watermarking Techniques
The quantization based method proposed in [8] embeds watermark bits in specific direction according to angle of significant gradient vectors with multiple wavelet scales. The spread spectrum communication use narrow band signal to transmit over much larger bandwidth as given in [9]. In SS based techniques, the transform domain is considered as communication channel whereas embedding watermark is considered as signal. The process of spreading the watermark through spectrum of image indirectly gives security provision. The SS based watermarking techniques support robustness against many attacks.
-
E. Reversible and irreversible Watermarking Techniques
These are special data hiding techniques. In reversible watermarking original digital content can be completely restored after data extraction [10][11].
-
F. Invisible and visible Watermarking techniques
The visible watermarking techniques are used in limited application areas. They convey rightful ownership information directly on image and avoid attempts of copyright violations. The visible watermarking with lossless recovery of cover image is presented in [12]. Majority watermarking techniques are developed as visible techniques.
-
G. Loosy and Lossless Watermarking Techniques
Only few watermarking techniques support lossless data embedding. These types of techniques are presented in [13][14].
-
H. Medical Image Watermarking Techniques
The telemedicine field demands strong security based medical image watermarking methods which are required in telecare, telesurgery, teleradiology, telepathy, teleneurology. The medical image data need confidentiality and safety of medical images for handling, transmission and processing. The critical judgment of patient diagnosis is done based on information provided by medical images. The region of interest (ROI) of medical images must be preserved because sensitive information is referred by physicians. The telemedicine based watermarking techniques are given in [2][15][16].
-
I. Watermarking Techniques based on Special properties of transforms
Most of watermarking methods use transform domain. The commonly used transforms by various researchers include discrete Fourier transform (DFT), discrete discrete Cosine transform (DCT), Laguerre transform (DLT), discrete Hadamard transform (DHT), discrete Wavelet transform[17].
The DWT is closer to theoretical model of human visual system (HVS) and provides multi-scale, multiresolution representation of image also gives perfect reconstruction of decomposed image. The DWT based watermarking is presented in [18-22] whereas Fourier transform based watermarking methods are given in [17][23][24]. The SVD based methods are given in [7][25]. The most of visually significant information of the image is concentrated in just a few coefficients of the DCT. This is energy compaction property of DCT. The DCT based method is given in [26][27].
-
J. Scrambling Based Watermarking Techniques
The scrambling methods are used to transform watermark information into disorder meaningless unsystematic patterns to hide real meaning. Fibonacci transformation [28], Modified Fibonacci transform [28], Generalized Fibonacci Transform [29], Arnold Transform[30], Grey Code Transformation[31], Affine Modular Transform[32] and other scrambling based methods presented in[33] are used for watermark scrambling.
-
K. Watermarking Techniques based on multiple transforms
Some of the researchers combined special properties of specific transforms to improve performance of watermarking techniques. The combine DWT-DCT approach is used in [34], DWT-SVD approaches used in [35][36][37][38] and Redundant DWT-SVD in [39] [40] are examples of combined techniques.
-
L. Optimization based watermarking techniques
The optimization based techniques are developed to optimize perceptual quality and robustness under high capacity watermark embedding. It is major challenge to design optimization based techniques. The wavelet based oblivious watermarking methods using genetic algorithms (GA) is presented in [41]. But GA based methods are relatively slow as they include iterative procedures.
-
III. Mathematical Background
This section elaborates the mathematical background of IPMS, DWT, FWHT, SVD and FLT. Their special properties are also presented in this section.
-
A. Image Partitioning-Merging Scheme (IPMS)
The image sharing methods can be effectively used in secured image watermarking techniques. The watermark can be embedded in shuffled images in transform domain to improve imperceptibility under high payload. Original image I is divided into two shares S1 and S2.
Image(I) =
Share (S1) =
|
2 |
10 |
18 |
26 |
34 |
42 |
50 |
58 |
|
3 |
11 |
19 |
27 |
35 |
43 |
51 |
59 |
|
4 |
12 |
20 |
28 |
36 |
44 |
52 |
60 |
|
5 |
13 |
21 |
29 |
37 |
45 |
53 |
61 |
|
⎜6 |
14 |
22 |
30 |
38 |
46 |
54 |
62 |
|
⎜7 |
15 |
23 |
31 |
39 |
47 |
55 |
63 |
|
8 |
16 |
24 |
32 |
40 |
48 |
56 |
64 |
|
9 |
17 |
25 |
33 |
41 |
49 |
57 |
65 |
|
2 |
0 |
18 |
0 |
34 |
0 |
50 |
0 |
|
0 |
11 |
0 |
27 |
0 |
43 |
0 |
59 |
|
4 |
0 |
20 |
0 |
36 |
0 |
52 |
0 |
|
⎜0 |
13 |
0 |
29 |
0 |
45 |
0 |
61 |
|
⎜6 |
0 |
22 |
0 |
38 |
0 |
54 |
0 |
|
⎜0 |
15 |
0 |
31 |
0 |
47 |
0 |
63 |
|
8 |
0 |
24 |
0 |
40 |
0 |
56 |
0 |
|
0 |
17 |
0 |
33 |
0 |
49 |
0 |
65 |
⎠
The Share s2 is
further merged to give Merged (M).
This M is used for embedding [42]. During separation of
S1 and S2 from I, first read number of rows and columns of image I. If rows are odd, then read only odd columns. If rows are even then read even columns. The shares S1 and S2 will be as given in equation(3) and equation(4).
|
0 |
10 |
0 |
26 |
0 |
42 |
0 |
58 0 |
|
|
3 |
0 |
19 |
0 |
35 |
0 |
51 |
||
|
0 |
12 |
0 |
28 |
0 |
44 |
0 |
60 |
|
|
⎜ Share(S2) = ⎜ |
5 0 |
0 14 |
21 0 |
0 30 |
37 0 |
0 46 |
53 0 |
0 ⎟ ⎟ 62⎟ |
|
⎜ |
7 |
0 |
23 |
0 |
39 |
0 |
55 |
0⎟ |
|
0 9 |
16 |
0 |
32 |
0 |
48 |
0 |
64 0 |
|
|
0 |
25 |
0 |
41 |
0 |
57 |
|||
The Merged (M) share can be generated by adding first row with last row, second row with second last row, third row with third last row and so on.
|
9 Merged(M) = 3 5 |
10 |
25 |
26 |
41 |
42 |
57 |
58 64 ] 60 62 |
|
16 12 |
19 23 |
32 28 |
35 39 |
48 44 |
51 55 |
||
|
14 |
21 |
30 |
37 |
46 |
53 |
||
|
(4) |
The recovered share R can be constructed back from M
|
by comparing with S2 |
||||||||
|
0 |
10 |
0 |
26 |
0 |
42 |
0 |
58 0 |
|
|
3 |
0 |
19 |
0 |
35 |
0 |
51 |
||
|
0 |
12 |
0 |
28 |
0 |
44 |
0 |
60 |
|
|
⎜ Recovered(R) = |
5 0 |
0 14 |
21 0 |
0 30 |
37 0 |
0 46 |
53 0 |
0⎟ 62⎟ |
|
⎜ |
7 |
0 |
23 |
0 |
39 |
0 |
55 |
0⎟ |
|
0 9 |
16 |
0 |
32 |
0 |
48 |
0 |
64 0 |
|
|
0 |
25 |
0 |
41 |
0 |
57 |
|||
-
B. Selection of Sub bands of DWT
International Standard Organization(ISO) has developed and generalized still image compression standard JPEG2000 in which DCT is replaced by DWT. DWT offers muti-resolution representation of image and gives perfect reconstruction of decomposed image.
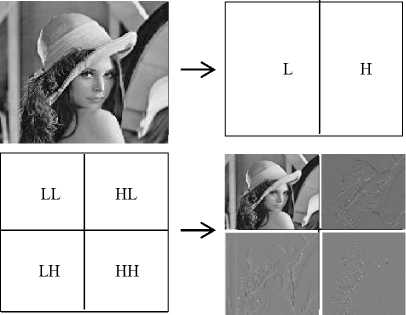
Fig.1. One Level DWT decomposition of image
DWT decomposes the image into sub bands of different resolutions when image is passed through series of low pass and high pass filters[43]. Fig. 1 shows, one level decomposition of image by DWT. At first level, DWT decomposes image into four non-overlapping multi-resolution sub bands namely LL (Approximate sub band), HL (Horizontal sub band), LH (Vertical sub band) and HH (Diagonal Sub band). Here, LL has low frequency coefficients whereas HL, LH and HH are high frequency (detail) coefficients. Mathematically, DWT can be represented as [6], v^ ,к(t)=а0!/Ч(aj I -kb0) (6)
Where, гр , is mother wavelet, a is scale parameter, b is translation parameter. For dyadic wavelets a0 =2 and b0 =1, Hence we have,
Ф] , к ( t )=2 / 2ф (2 "jt - к ) j, k eZ (7)
Embedding watermark in low frequency coefficients can significantly increase the robustness but maximum energy of most of the natural images is concentrated in approximate (LL) sub band. Modification in this low frequency sub band will degrade the image quality severely. Hence watermark is not embedded in LL sub band. The better choice for sub band selection is high frequency sub bands (HL, LH and HH), because human naked eyes are not sensitive to these sub bands.
-
C. Fast Walse-Hadamard Transform (FWHT)
The Walsh-Hadamard transform decomposes a signal into a set of basis functions and it is non-sinusoidal, orthogonal transformation technique. These basis functions are rectangular or square waves with values of +1 or –1.
Table 1. Walse Function Values
|
Index |
Walsh Function Values |
|
0 |
1 1 1 1 1 1 1 1 |
|
1 |
1 1 1 1 -1 -1 -1 -1 |
|
2 |
1 1 -1 -1 -1 -1 1 1 |
|
3 |
1 1 -1 -1 1 1 -1 -1 |
|
4 |
1 -1 -1 1 1 -1 -1 1 |
|
5 |
1 -1 -1 1 -1 1 1 -1 |
|
6 |
1 -1 1 -1 -1 1 -1 1 |
|
7 |
1 -1 1 -1 1 -1 1 -1 |
They are also called Walsh functions [44]. The first eight Walsh functions have values as shown in table 1. The Walsh-Hadamard transform returns sequency values which are generalized forms of frequency. These sequency values of walsh functions are used to estimate the signal frequencies in the original signal. Walsh-Hadamard transform is used in variety of applications, such as image processing, filtering, speech processing and power spectrum analysis. FWHT is the fast version of Walsh-Hadamard transform. FWHT requires less storage space and it is faster with compared to FFT. The FWHT is able to represent signals with sharp discontinuities more accurately using fewer coefficients than the FFT. The FWHT and IFWHT for a signal xi of length N are defined as [44]:
yn= ∑i^Q1 хi WAL(n, i) (8)
xi =∑i^Q1 уn WAL(n, i) (9)
Where i = 0, 1,...... N-1 and WAL (n,i) are Walsh functions. FWHT coefficients are calculated by first evaluating across the rows and then evaluating down the columns for 2-D images.
-
D. Singular Value Decomposition (SVD)
SVD is used for variety of image processing applications such as image watermarking, image steganography, image compression, noise reduction. SVD is important linear algebraic technique that used to solve many mathematical problems. The SVD digitalizes given matrix into three matrices. SVD of an image A with size MxN is represented as A=U∑VT , where U and V are orthogonal matrices such that, UUT =I and VVT = I , ∑ is summation of diagonal entries λ1, λ2…..gives the singular vectors of A. These diagonal entries are called as singular values of A and the decomposition is called as ‘singular value decomposition’. Thus we have [25],
A=λ ! U ! V 1T +λ2U2V 2T + ⋯․․+λrUrV rT (10)
Where, r is rank A. The columns of U and V are called left and right singular vectors of A. Singular values have following properties:
-
1. Singular values correspond to brightness and left singular as well as right singular vectors reflect geometric characteristics of image.
-
2. Singular values of an image have very good stability. Slight variations in singular values do not affect much visual perception.
-
3. The largest of singular values changes very little for most common geometric attacks.
-
4. Singular values have important properties related to rotation, flipping, and translation.
-
a) A and Лг (A rotated by certain degree) have same nonzero singular values.
-
b) The row flipped ^yf and column flipped A^j forms of A have same nonzero singular values.
-
c) If Лу is expanded by adding rows and columns of black pixels, the resulting Лу has same nonzero singular values of A.
Because of these attractive properties of SVD, most of watermarking method use singular values for watermark embedding.
-
E. Fibonacci-Lucas Transform(FLT)
The ‘security provision’ by given watermarking technique is important quality parameter. The use of ‘watermark scrambling methods’ is one of the better options to implement security in underlying watermarking technique. Watermark scrambling methods transform meaningful watermark information into disorder and unsystematic pattern so that watermark extracted by hacker should hide its real meaning because of meaningless order of patterns. Fibonacci-Lucas Transform is used as image scrambling method used in data hiding and secret communications. Fibonacci-Lucas Transform is robust against statistical attacks such as format changes attacks including tiff format to png, tiff to JPEG, tiff to BMP. It is also robust to noise addition attacks, cropping and compression attacks. This scrambling method can be effectively used for watermarking techniques to increase the security by scrambling the watermark in spatial domain. Basic Fibonacci Transform is given by[45]:
(S = 11 ОО™") (11)
Where, (x1, y1) ϵ {0, 1,.....N-1}: original image.
(x2, y2): Fibonacci-Transformed Image
N: Size of digital Image
The Lucas series is given by:
Г 2 if n = 1
L, = ] 1 if n = 2 (12)
(L„ _ t + Ln_2 0 therwiee
Resulting sample sequence:: 2, 1, 3, 4, 7, 11, 18, 29, 47 ,…..
Considering seed values of Fibonacci-series as 1,1 instead of 0,1. we have,
Fibo11=1, 1, 2, 3, 5, 8, 13, 34, 55,….
Fibo41=4, 1, 5, 6, 11, 17, 28, 45,….
Fibo51=5, 1, 6, 7, 13, 21, 34, 55,….
The Fibonacci-Lucas transform can be defined as[3],
( 0 if n = 0
Fn = { 1 if n = 2 (13)
(Fn _! + Fn_2 0 therwise
Where, (x1, y1) ϵ {0, 1,.....N-1}: original image.
(x2, y2): Fibonacci-Lucas transformed Image.
Ft is the i£h term of Fibonacci series Fiboll.
-
IV. Proposed IPMS based Methodology in DWT-FWHT-SVD
This section describes proposed IPMS based secure and robust digital image watermarking technique supporting high capacity watermark embedding. The watermark embedding algorithm and watermark extraction algorithm are presented here. The watermark embedding algorithm uses novel approach of IPMS reduction scheme where the IPMS effectively reduces watermark of size 512 x512 to 256x256. It also increases the security of embedding process. As the method is nonblind, it assumes that ‘cover_image’ will be available in extraction process.
-
A. Watermark Embedding Algorithm.
Input: cover image, watermark W.
Output: watermarked_image.
Steps:
Step-1: Read grey scale ‘cover_image’ of size 512x512.
[Mc,Nc]=size(cover_image)
Step-2: Apply one level DWT to ‘ cover_Image’ using ‘Haar’ wavelet to give four non overlapping sub bands:
[LL1,HL1,LH1,HH1]= dwt2(cover_image,'Haar'); Step-3: Apply ‘Fast Walse-Hadamard Transform’ to ‘HL1’ sub band.
temp=fwht (HL1)
Step-4: Apply ‘Singular Value Decomposition’ (SVD) to ‘temp’.
[U,S,V]=SVD (temp)
Step-5: Read grey scale watermark of size 512x512 say ‘Watermark1’
Step-6: Generate two shares from Watermark1 to give S1 and S2 as shown in Section III-A. The size of both S1 and S2 will be of size 256x512.
Step-7: Select S2 and generate further shares S3 and S4 of size 256x256.
Step-8: Now select Share S3 as Watermark W. Select share S4 to generate Pseudorandom
Number (PN) sequence to give watermark scrambling key ‘K1’.
Step-9: Apply ‘Fibonacci-Lucas transform’ using key ‘K1’ to give scrambled watermark ‘W1’.
Step-10: Perform embedding of ‘scrambled_watermark’ W1 with cover_image.
S1=S+K*W1
Where, K is scale factor also called flexing factor or amplification factor.
Step-11: [U1,SS,V1]=SVD (S1)
CW1=U*SS*V’
Step-12: Apply inverse SVD to get ‘New_HL1’ as: New_HL1=ifwht(CWI)
Step-13:Perform one level inverse DWT with ‘New_HL1 ‘component to form ‘watermarked_image’ as: watermarked_image = idwt2(LL1, New_HL1, LH1,HH1, 'Haar', [Mc,Nc]);
Step-14: Display ‘watermarked_image’.
-
B. Watermark Extraction Algorithm
Input: watermarked_image ,cover image, shares S1, S4. Output: Final _Watermark.
Steps:
Step-1: Read ‘watermarked_image’ of size 512x512.
Step-2: Apply One level DWT to ‘watermarked_image’ to separate ‘Recovered_HL1’ component as:
[LL1, Recovered_HL1,LH1,HH1] = dwt2(watermarked_image,’Haar’);
Step-3: Apply ‘ Fast-Walse-Hadamard Transform’ :
NCWI=fwht(Recovered_HL1)
Step-4: Apply Singular Value Decomposition [UU,S2,VV]=SVD(NCWI )
Step-5: Read grey scale ‘ cover_image’ of size 512x512.
[Mc,Nc]=size(cover_image)
Step-6: Apply one level DWT to ‘ Cover_Image’ using
‘Haar’ wavelet to give four non overlapping sub bands: [LL1, HL1, LH1, HH1]= dwt2(cover_image,’Haar’);
Step-7: Apply ‘Fast Walse-Hadamard Transform’ to ‘HL1’ sub band as, temp=fwht (HL1)
Step-8: Apply ‘Singular Value Decomposition’ (SVD) to ‘temp’ as,
[U,S,V]=SVD (temp)
Step-9: Find SN using component: S2 in step 4 and components: U1 and V1 in step 8 of watermark embedding process as,
SN=U1*S2*V1’
Step-10:‘scrambled_watermark’ can be found as follows: scrambled_watermark=(SN-S)/K;
Step-11: Apply ‘Fibonacci-Lucas Transform’ with key used in embedding algorithm to give
‘recovered_watermark’ say ‘S3_New’.of size 256x256.
Step-12: Combine ‘S3_New’ and S4 to regenerate share ‘S2_New’ applying reverse logic presented in section III-A.
Step-13: Further combine share ’S2_New’ with S1 to generate ‘Final _Watermark’ by applying logic presented in section III-A. Display ‘Final_Watermark’ as extracted watermark.
-
V. Experimentation and Results
The proposed system is implemented using Matlab version 8.0.0.7837(R2012b). The experimentation is carried out on personal computer with Intel(R), Core(TM) i3-2310M, processors rated at 2.10 GHz, main memory of 4 GB and 32 bit Microsoft Windows 7 operating system. The variety of tests are carried out to evaluate imperceptibility, robustness against 14 noise addition, filtering attacks, high payload capacity. The proposed system has been tested with online database [46] and [47] considering grey scale cover images of size 512x512 and watermark of size 512x512 as shown in fig.2.
-
A. Performance Evaluation Metrics
Here objective is to test two major quality parameters of watermarking technique namely perceptual transparency and robustness with given grey scale watermark. Perceptual transparency also called as imperceptibility is very important benchmark for assessing quality of digital image watermarking technique under consideration. Perceptual transparency implies that perceived quality of original cover image should not be destroyed by presence of watermark. PSNR is major attribute to measure perceptual quality of watermarked image. The bigger PSNR implies better quality of watermarked image. Initially, the Mean Square Error (MSE) is computed and PSNR is calculated using MSE. Mean Square Error of grey scale image is defined as [25],

(a)

(b)


(c)






(d)

(e)
Fig.2. Cover images of size 512x512 a) Lena b) Peppers c) Baboon d) Lake e) Plane and f) Grey scale Watermark cameraman of size 512x512.

(f)
MSE = ^^ ^JX1( i, ) - X2(i J-)]2 (15)
Where, M x N : size of image ,
X 1(i, j ): Pixel values of original image,
X 2( ij): Pixel values of watermarked image,
The PSNR for grey scale image is given as[25],
PSNR (db ) = 10loglo -— ттл^^------ ^^Цхжп^ (U)F
Where, M x N: size of image ,
MaX] is 255 for grey scale image,
X 1( 1,7): Pixel values of original image,
X 2( ij): Pixel values of watermarked image.
PSNR can also be defined as [25][26],
PSNR №) = 1Glog10 P™221] (17)
Where, ‘MSE’ is computed using equation (15)
Where, Maxi is 255 for grey scale image.
Robustness is measure of immunity of watermark against removal or destroying it due to intentional or unintentional attacks like noise addition, filtering, cropping, compression, histogram equalization, gamma correction, contrast adjustment, rotation, scaling and translation. The normalized correlation (NC) is important attribute for measuring robustness of underlying watermarking technique against various attacks. NC measures the similarity between ‘original watermark’ and ‘extracted watermark’. The value of NC is between 0 to 1. If NC equals to 1, then extracted watermark matches exactly with original watermark. Normalized correlation (NC) is defined as [36],
NC (P) = ^^ 1 ^1 wdiaWdiJ) (18)
Where, M x N: size of watermark, w1(i,7): Pixel values of original watermark, w2 (, > 2): Pixel values of original watermark.


(k)

(l)
Fig.3. Step by step implementation of proposed method a)Original Cover peppers b)Selected HL1 c)Forward FWHT of HL1 d)Forward
SVD after forward FWHT of HL1 e)Inverse SVD f)HL1:Inverse FWHT g)Original Watermark h)Scrambled Watermark i)Watermarked Image j)Watermarked image peppers under pepper-salt attack k)Extracted Watermark l)Recovered Watermark
C. Relative impact of imperceptibility and robustness
B. Details of IPMS based scheme in DWT-FWHT-SVD domain
The step by step implementation of proposed IPMS based scheme in DWT-FWHT-SVD domain is shown in fig.3. The images are resized for display purpose.

(a)

(b)

(c)

(d)

(e)

(f)
(a)
(b)
Fig.4. Comparative performance of images–Scale Factor(K) versus Peak Signal to Noise Ratio(PSNR) b) Scale Factor(K) versus Normalized Correlation (NC)



(i)
(g) (h)
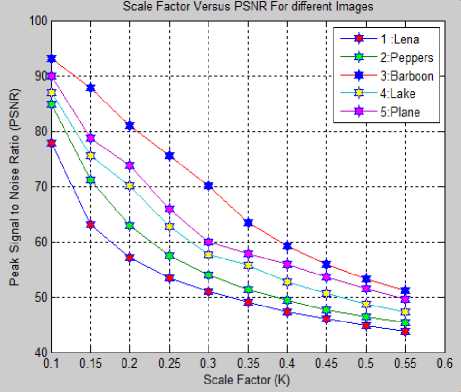
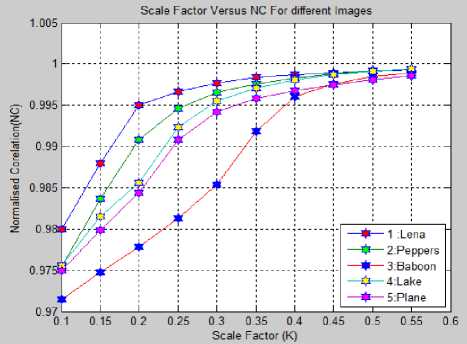
The tests are carried out for all candidate images of size 512x512. The scale factor K is varied from 0.10 to 0.55. The values of PSNR and NC are noted. As shown in fig. 4, with scale factor K as 0.10, Lena image gives PSNR as 75.8446dBs and NC as 0.9800, peppers image gives PSNR as 82.8343 dBs and NC as 0.9755, baboon image gives PSNR as 94.0575 dBs and NC as 0.9715, lake images gives PSNR as 86.9526 dBs and NC as
0.9756, plane image gives PSNR as 89.9170 dBs and NC as 0.9750. As K increases from 0.25 to 0.55, for all 5 candidate images, NC is greater than 0.99 rounded to 1, indicating exact recovery of watermark from watermarked image. As PSNR increases, NC decreases. Thus baboon image shows highest PSNR values while lowest NC values. Similarly, Lena image shows lowest PSNR values but highest NC values.
The comparatively, baboon image gives better performance with compared to candidate images under consideration as quality factor (QF) of baboon image is better. The experimental demonstrations proves that PSNR and NC are inverse of each other. Thus, as imperceptibility all candidate cover images in proposed method increases, the robustness get decreased.
D. Robustness of proposed method
Density Density Density 0.01 0.1
0.001 0.005
(a)
-
■ Lena ■ Peppers Barboon ■ Lake ■ Plane
0.99
0.97
0.95
0.93
0.91
0.89
0.87
0.85
1.01
Speckle Noise Density 0.001
Speckle Noise Speckle Noise 0.4
Density 0.04
(b)
Fig.5. Robustness of proposed technique to a)Pepper and Salt Noise b) Speckle Noise attack
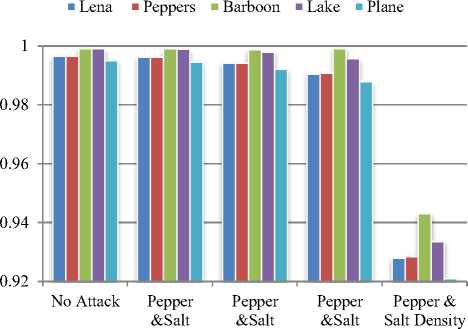
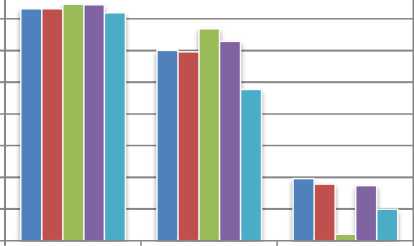
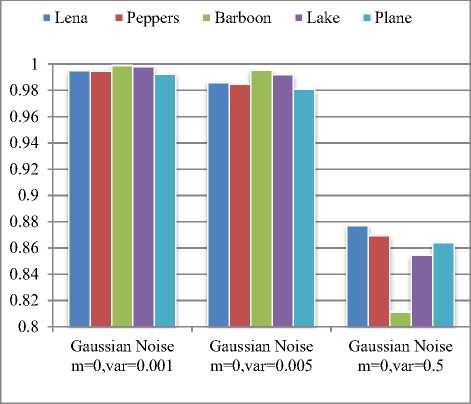
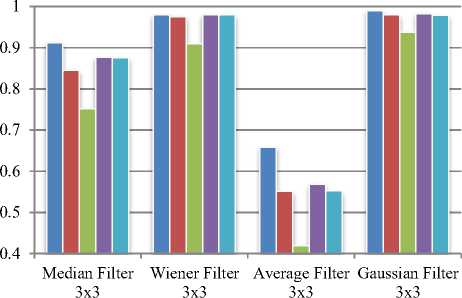
Fig.5 and Fig.6 show robustness of watermarked images under noise addition and noise filtering attacks.
Baboon image gives best performance for all noise attacks with density 0.001 to 0.1 and for speckle noise with density 0.001.
But, it shows poor performance against filtering attacks inclusing median filtering, wiener filtering and gaussian filtering while Lena image gives better performance against filtering attacks. The proposed technique found robust against all noise addition and noise filtering attacks under consideration.
(a)
■ Lena ■ Peppers ■ Barboon ■ Lake ■ Plane
(b)
Fig.6. Robustness of proposed technique to a) Gaussian Noise b) Filtering Attacks
-
E. Comparative Imperceptibility and Watermark Embedding Capacity
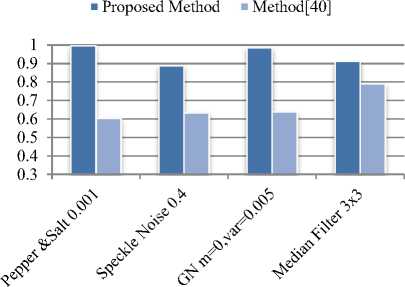
The imperceptibility of proposed IPMS based watermarking technique in DWT-FWHT-SVD domain found superior than method [39], method [40] and method[41] as shown in fig.7. Table 2 shows comparative watermark hiding capacity with cover image Lena. It shows that the proposed method also supports better watermark hiding capacity.
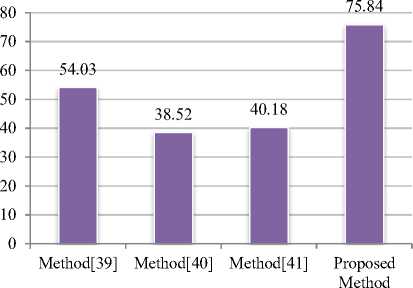
Fig.7. Comparative of imperceptibility
Table 2. Comparative watermark hiding capacity
|
Methods |
Method [39] |
Method [40] |
Method [41] |
Proposed method |
|
Embedding Domain Used |
RDWT-SVD |
RDWT-SVD |
GA- DWT |
DWT-FWHT-SVD |
|
Cover Type used |
Grey Scale |
Grey Scale |
Grey Scale |
Grey Scale |
|
Subbands Used |
LL, LH, HL, HH |
LL, LH, HL, HH |
LH |
HL |
|
Cover Size |
Lena 512x512 |
Lena 512x512 |
Lena 512x512 |
Lena 512x512 |
|
Watermark Size Used |
512x512 |
512x512 |
64x64 |
512x512 |
F. Comparative Robustness with existing methods
■ Proposed Method ■ Method[39]
(a)
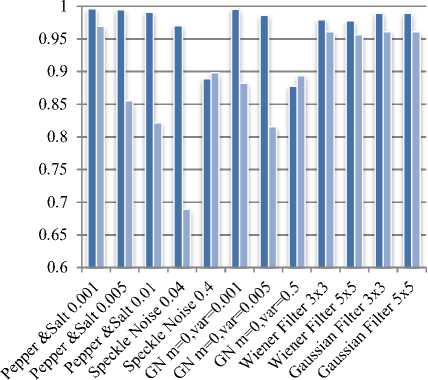
The robustness of proposed technique is compared with three different existing DWT based methods namely method [39], method [40], method [41]. The tests are carried out with cover images of size 512x512 in HL region. The out coming results of proposed method is compared with robustness of watermarked ‘Lana’ image of method[39] as shown in fig.8-a and found more robust for 12 various noise addition and noise filtering attacks except for speckle noise with density 0.4 for Lena image, where both methods show almost same performance.
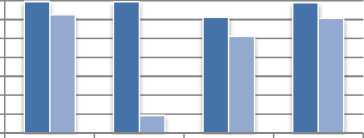
The robustness of proposed method is compared with method [40] and method [41] as shown in fig.8-b and fig. 8-c and found superior than these methods.
(b)
1 0.9 0.8 0.7 0.6 0.5 0.4 0.3
■ Proposed Method ■ Method[41]
(c)
Fig.8. Comparative performance of proposed method with :a) method[39] b) method [40] and c) method[41]
-
VI. Conclusions
i.The proposed novel IPMS based watermarking technique in DWT-FWHT-SVD domain combines individual properties of DWT, FWHT and SVD to achieve imperceptibility, robustness, high watermark embedding capacity and more security in embedding process using FLT.
-
ii .The achieved imperceptibility in terms of PSNR is 75.8446dBs for Lena image, 82.8343 dBs for peppers image, 94.0575 dBs for baboon image, 86.9526 for dBs for Lake Image and 89.9170 dBs for plane image.
-
iii .The robustness in terms of NC equals to 1 for all cover images of size 512x512 under consideration and watermark cameraman of size 512x512 proving exact recovery of watermark.
-
iv .The proposed method is compared with method [39], method [40] and method [41] for robustness, imperceptibility and watermark hiding capacity and proposed method found superior than these methods.
-
v . Both FLT and IPMS increase security levels in watermark embedding process.
-
VII. Future Scope
The proposed technique is flexible and can be extended for color image watermarking in different color spaces such as red-green-blue(RGB), KarhunenLoeve average (KLA), YUV, YIQ, XYZ, UVW, YCbCr, RcGcBc and RsGsBs. As per scope of this work, DWT has been focused as central transform. Instead of DWT, either complex wavelet transform (CWT), Multi wavelet or complex and rotated wavelet transform can be used to make the system more robust and secure. The proposed watermarking technique can be extended for video watermarking.
Acknowledgement
The author expresses deep sense of gratitude and hearty thanks to her Ph.D supervisor Dr. Suresh N. Mali, Principal, Sinhgad Institute of Technology and Science (SITS), Narhe, Pune, MS, India for his valuable guidance, motivation and support for this research work. The author would also like to thank to Dr. G.J. Vikhe Patil, Principal Amrutvahini College of Engineering(AVCOE), Sangamner, Ahmednagar, Maharashtra, India for his constant support.
Список литературы Robust, Secure and High Capacity Watermarking Technique based on Image Partitioning-Merging Scheme
- Lihong Cui and Wenguo Li,” Adaptive Multiwavelet-Based Watermarking Through JPW Masking”, IEEE Transactions on Image Processing, Vol.20, No.4, pp. 1047-1060, Apr. 2011.
- M. Kamran, and Muddassar Farooq, “An Information-Preserving Watermarking Scheme for Right Protection of EMR Systems”, IEEE Transactions on Knowledge` and Data Engineering, Vol. 24, No. 11, pp. 1950-1962, Nov. 2012.
- S. Nadarajah, “A generalized normal distribution,” J. Appl. Statist., vol.32, pp. 685–694, Sep. 2005.
- K. Krishnamoorthy, “Handbook of Statistical Distributions With Applications”, London, U.K.: Chapman & Hall, 2006.
- Yu-Hsun Lin and Ja-Ling Wu, “A Digital Blind Watermarking for Depth-Image-Based Rendering 3D Images”, IEEE Transactions on Broadcasting, Vol.57, No.2, pp. 602-611, Jun.2011.
- R. Agrawal, P. Haas, and J. Kiernan, “Watermarking Relational Data: Framework, Algorithms and Analysis,” The VLDB J., vol. 12,no. 2, pp. 157-169, 2003.
- Chih-Chin Lai, and Cheng-Chih Tsai, ”Digital Image Watermarking Using Discrete Wavelet Transform and Singular Value Decomposition”, IEEE Trans.on Instru. and Measurement, Vol. 59, No. 11, pp. 3060-3063, Nov. 2010.
- Ehsan Nezhadarya,, Z. Jane Wang, and Rabab Kreidieh Ward,” Robust Image Watermarking Based on Multiscale Gradient Direction Quantization”, IEEE Transactions on Information Forensics and Security, Vol. 6, No. 4, pp.1200-1213, Dec. 2011.
- Fan Zhang, WenyuLiu, WeisiLin, and King NgiNgan,” Spread Spectrum Image Watermarking Based on Perceptual Quality Metric”, IEEE Trans. on Image Processing, Vol. 20, No. 11, pp. 3207-3218, Nov. 2011.
- Xiaolong Li, Bin Yang, Tieyong Zeng, “ Efficient Reversible Watermarking Based on adaptive Prediction error Expansion and pixel selection”, IEEE Transactions on Image Processing, Vol.20,No.12, PP:3524-3533, Dec. 2011.
- Gouenou Coatrieux,Wei Pan, Nora Cuppens-Boulahia, Frederic Cuppens and Christian Roux, "Reversible Watermarking Based on Invariant Image Classification and Dynamic Histogram Shifting",IEEE Trans. on Info. Forensics and Security, VOL. 8, NO. 1, pp:11-120, Jan. 2013
- Tsung-Yuan Liu, and Wen-Hsiang Tsai,” Generic Lossless Visible Watermarking-A New Approach”, IEEE Transactions on Image Processing,Vol.19,No.5, pp. 1224-1235, May 2010.
- Y.Q.Shi, Z.Ni,D.Zou,C. Liang, G.Xuan, “Lossless data hiding :Fundamentals, algorithms and applications”, Proc. IEEE ISCAS, vol.2, pp: 33-36,2004.
- M.U.Celik, G. Sharma, A.M. Tekalp, “Lossless watermarking for image authentication: A new framework and an implementation”, IEEE Tans. Image Process.,Vol 15,no.4, pp:1042-1049, Apr. 2006.
- Dalel Bouslimi, Gouenou Coatrieux, Michel Cozic, and Christian Roux, “A Joint Encryption/Watermarking System for Verifying the Reliability of Medical Images”, IEEE Trans. on Information Technology in Biomedicine, Vol.16, No. 5,pp.891-899, Sep. 2012.
- Gouenou Coatrieux, Hui Huang, Huazhong Shu,Limin Luo and Christian Roux,"A Watermarking-Based Medical Image Integrity Control System and an Image Moment Signature for Tampering Characterization", IEEE Journal Of Biomedical and Health Informatics, vol. 17, No. 6, pp:157-1067, November 2013.
- Tsz Kin Tsui, Xiao-Ping Zhang, and Dimitrios Androutsos, “Color Image Watermarking Using Multidimensional Fourier Transforms”, IEEE Transactions on Information Forensics and Security, Vol. 3, No. 1, pp.16-28 Mar. 2008.
- Chuntao Wang, Jiangqun Ni and Jiwu Huang,"An Informed Watermarking Scheme Using Hidden Markov Model in the Wavelet Domain", IEEE Transactions on Information Forensics and Security, Vol. 7, No. 3, pp.853-867,Jun. 2012.
- Baisa L. Gunjal, Suresh N. Mali, "Strongly Robust and Highly Secured DWT-SVD Based Color Image Watermarking: Embedding Data in All Y, U, V Color Spaces", International Journal of Information Technology and Computer Science, Vol. 4, No.3, pp.1-7, Apr. 2012.
- D. Kundur and D. Hatzinakos, “Digital watermarking for telltale tamper proofing and authentication,” Proc. IEEE, vol. 87, no. 7, pp.1167–1180, Jul. 1999.
- Mohsen Zareian, Hamid Reza Tohidypour,"Robust quantization index modulation-based approach for image watermarking", IET Image Processing , Vol. 7, Iss. 5, pp. 432–441,2013.
- V. Senthil and R. Bhaskaran, “Digital image watermarking using edge detection and wavelets with robustness analysis against jpeg compression attacks,” in Int. Conf. Innovations in Inf. Tech., pp. 583–587,16–18 Dec. 2008.
- T. Tsui, X. Zhang, and D. Androutsos, “Color image watermarking using the spatio-chromatic fourier transform,” in Proc. ICASSP,Toulouse, France, pp. 305–308, May 2006.
- T. Tsui, X. Zhang, and D. Androutsos, “Quaternion image watermarking using the spatio-chromatic fourier coefficients analysis,” presented at the ACM, Santa Barbara, CA,Oct 2006.
- Chih-Chin Lai, and Cheng-Chih Tsai, “Digital Image Watermarking Using Discrete Wavelet Transform and Singular Value Decomposition”, IEEE Transactions on Instrumentation and Measurement, Vol. 59, No. 11, pp. 3060-3063, Nov. 2010.
- Zhenyu Wei, and King N. Ngan, “Spatio-Temporal Just Noticeable Distortion Profile for Grey Scale Image/Video in DCT Domain”, IEEE Transactions on Circuits and Systems for Video Technology, Vol. 19, No. 3, pp.337-346,Mar. 2009.
- A. Ahumada and H. Peterson, “Luminance-model-based DCT quantization for color image compression,” in Proc. SPIE Human Vision,Visual Process., Digit. Display III, vol. 1666, pp. 365–374, 1992.
- J. Zou, R.K.Ward, and D. Qi, “A new digital image scrambling method based on fibonacci numbers,” in Proc. Int. Symp. Circuits and Syst.,.3, pp. 965–968,2004.
- Zou, J.C., R.K.Ward and Q.D. Qi, “The generalized Fibonacci transforms and application to image scrambling”, Proceedings of IEEE international conference on Acoustic , Speech and Signal Processing, Canada,2004, pp. 385-388,2004.
- Na Li; Xiaoshi Zheng; Yanling Zhao; Huimin Wu; Shifeng Li ,”Robust Algorithm of Digital Image Watermarking Based on Discrete Wavelet Transform”, Electronic Commerce and Security, International Symposium , pp.942 – 945,2008
- Cheng-qun Yin, Li Li, An-qiang Lv, Li Qu, “Color Image Watermarking Algorithm Based on DWT-SVD”, Proceedings of IEEE International Conf. on Automation and Logistics, Jinan, China,pp.2607-2611,2007.
- J. Zou, X. Tie, R. K. Ward, and D. Qi, “Some novel image scrambling methods based on affine modular matrix transformation,” J.Inf.Comput. Sci.,Vol.2, No.1, pp. 223–227,2005.
- J. Zou and R. K. Ward, “Introducing two new image scrambling methods,” in IEEE Pacific Rim Conf. Comm., Comp. and Signal Proces., vol. 2, pp. 708–711 Aug. 2003.
- A. Nikolaidis and I. Pitas, “Asymptotically optimal detection for additive watermarking in DCT and DWT domains,”IEEE Trans.Image Process., vol.12, no.5, pp.563–571, May 2003.
- Cheng-qun Yin, Li Li, An-qiang Lv, Li Qu, “Color Image Watermarking Algorithm Based on DWT-SVD”, Proceedings of IEEE International Conference on Automation and Logistics, Jinan, China, pp:2607-2611, 18-21 Aug. 2007.
- Priyanka Singh, Suneeta Agarwal, Akanksha Pandey, “A Hybrid DWT-SVD Based Robust Watermarking Scheme for Color Images and its Comparative Performance in YIQ and YIV color Spaces”, 3rd IEEE International Advance Computing Conference (IACC), pp:1213-1218, 22-23 Feb. 2013.
- Na Wang, Chung-Hwa Kim , “Tamper Detection and Self Recovery Algorithm of Color Image Based on Robust Embedding of Dual Visual Watermarks using DWT-SVD”, IEEE Int.Sympo. on Communication and Information Technology, pp: 157-162, 28-30 Sep.2009.
- Liu Liang and Sun Qi, “A new SVD-DWT composite watermarking", Proceedings of 8thIEEE International conference on signal processing (ICSP), pp: 645-650,2006.
- Nasrin M. Makbol, Bee EeKhoo, “Robust blind image watermarking scheme based on Redundant Discrete Wavelet Transform and Singular Value Decomposition”, Elsevier International Journal of Electronics and Communications, AEU-67,pp.102-112,2013.
- Samira Lagzian, Mohsen Soryani, Mahmood Fathy, “Robust watermarking scheme based on RDWT-SVD: Embedding Data in All sub bands”, IEEE, pp. 48-52,2011.
- K.Ramanjaneyulu, K. Rajarajeswari, “Wavelet-based oblivious image watermarking scheme using genetic algorithm”, IET Image Processing,vol. 6, no.4, pp. 364–373,2012.
- Sridhar B., Arun C., “A wavelet based image watermarking technique using image sharing method", IEEE international conference on Information Communication and Embedded Systems (ICICES), pp.629 - 633, 21-22 Feb. 2013.
- K.P. Soman, K.I. Ramchandran, “Insight into Wavelets: From Theory to Practice”, 2nd Edition, Prentice Hall of India, ”,pp.48-71, 2008.
- Md. Iqbal H. Sarker, M. I. Khan, “An Improved Blind Watermarking Method in Frequency Domain for Image Authentication”, IEEE International Conference on Informatics, Electronics & Vision (ICIEV), pp.1-5, 17-18 May 2013.
- Minati Mishra, Priyadarsini Mishra, M.C. Adhikary and Sunit Kumar, “Image Encryption Using Fibonacci-Lucas Transformation”, International Journal on Cryptography and Information Security (IJCIS), Vol.2, No.3, pp. 131 -141, Sep. 2012.
- CVG-UGR Image Database [Online]. Available: http://decsai.ugr.es/cvg/dbimagenes/index.php
- OsiriX [Online]. Available: http://www.osirix-viewer.com/Downloads.html


