Semantic Enabled Role Based Social Network
Автор: Fausto Giunchiglia, Md. Saddam Hossain Mukta, Mir Tafseer Nayeem, Khandaker Tabin Hasan
Журнал: International Journal of Intelligent Systems and Applications(IJISA) @ijisa
Статья в выпуске: 12 vol.4, 2012 года.
Бесплатный доступ
Communication is the most common but an intricate activity that we perform every day. Sender sends message, discussions, greetings, gestures, emotics and texts through numerous channels, (e.g. e-mail, messengers, social networks and so on) intending the receiver to understand. The means of personal or group communication has been radically changed over last decade. Geographical, ethnicity, nationality, race, religion are no more hindrance for the sake of social communication. Forms of communication, event, gathering, greetings almost have altered into virtual society. But this hi-tech society has still yet enough room to strengthen its semantic nature. We have made an endeavor to conglomerate the socio-psycho-technical aspect of so-called social networks which could be more realistic, logically inferable and convincible towards people to claim its analogousness with real society. Our devised SN is able to eliminate some weird problems that we face in current SNs, imperfect relationship assignment policies and possibility of data interference among desired and intruder groups.
Semantic, Role, Ontology, OWL, Description Logic
Короткий адрес: https://sciup.org/15010339
IDR: 15010339
Текст научной статьи Semantic Enabled Role Based Social Network
Published Online November 2012 in MECS
In recent times, people have two types of existence on the society- one is bodily appearance before all while other is intangible presentation about self to others. The latter is nothing but virtual representation by means of power of web 2.0 technology in the form of social networks. In current days, it is observed that usage of different ways of communication (e.g. email, chatting, voice mail and so on) via internet dropped significantly, specially for single platform service (e.g. yahoo mail , google chat) , for the sake of strong affinity of people towards emerging contemporary social networks (i.e. facebook, google plus, myspace, twitter and many more). Because people tend to share his/her views, exchange greetings, photo, message, eventually passing time with kin, friends and acquaintances. So, social network is such a solution which suffices to serve multidimensional services affixing into a single application.
However considering the advantages, still there is a little consensus about how genuine and unadulterated the content and easiness of the communication by SNs. Furthermore, there are rooms to improve the cognitive aspect while communicating with an entity. And question arises at the point how profoundly [34] they are representing the social role, morality, degree of intimacy and environment in their sites. Considering two major social networks of this time according to users demand, Facebook and MySpace, we will try to analyze about their social environment for the user. MySpace has numerous flamboyant features for its user and all who are using this site are accustomed with its facilities. But we have some arguments at their environment regarding the user’s confidentiality; they can provide privacy layers for friends, friends of friends and anyone over 18 years, even everyone. But scope and restriction of visualization [34] is not well defined and no system for relationship assignment. However Facebook eliminates some of the limitations yet some spaces to improve to mimic true society. Facebook has different user privacy layers depending on the users interest and it has option for relational operation but does not have adequate semantic power to escape [34] from assigning weird relationship( e.g. at the same time same person husband and brother, at Fig. 1.). Moreover Facebook cannot provide proper social role based person addressing, (e.g. my brother treated as an ordinary friend, instead of calling him brother) neglecting this social role, a WBSN is only a site capable of communication but fails to provide social platform and environment on the web. Another WBSN Google+ [23] is becoming famous now-a- days which is very similar to Facebook but also fails to provide role based social networking. It uses the terms Family, Friends, Acquaintance, Follow. to cluster between people, but not extra ordinary than Facebook’s friend group. In this paper, we have proposed a concept for a social network based on individual role inspired by identity theory [21] and social relations model (SRM) [22] which are two of the major fundamental models in social psychology. In our system we have used semantic web technologies, i.e. OWL [15], this is why our system has more expressive power as a result it can overcome the failure of semantic consistency.
The rest of the paper is organized as follows. We make a brief focus on terminologies used in our paper i.e. evolution of some contemporary SNs (Social Networks), definition and concepts of role, identity theory, social relational model and ontology. Afterwards, a literature review about the usage and necessity of description logic in numerous semantic applications in section III. Some erroneous contexts and their negative reflections on the society and family are closely portrayed in Section IV . In section V, we first describe a conceptual solution, relevant role and object ontologies, formalization of different social network pertinent rules, boundaries among different users and lastly technique of using semantic tool to manipulate and extract role and corresponding objects.
-
II. Related Work
Members are motivated [13] to use SN to perform multi-dimensional communication and interaction facility in a single platform. Main reasons are preserving relationship [13], update activities to others and to be informed about them, sharing photos and events, sharing message to group and private. Major social networking sites launch in different times aiming different aspiration [13], i.e. sixdegree.com (97), AisainAvenue(99), LiveJournal(99), BlackPlanet (99), MiniGente (00), Fotolog, FriendSter, skyblog(02), LinkedIn, Tribe.net, Myspace, Hi5 (03), Yahoo!360, Ning, youtube, Xanga, Bebo, facebook (05) and so on. In most of the SNS, neither people are interested on ”Networking” [1] nor they search for new people, rather they are curious of interacting with known people. Most of the SNS have different eye catching and fabulous technical features. Being connected to the SNS, people are asked to fill out form with some questions [1], (e.g. age, locations, interest, relationship status, employer, activities, contact info and so on). Some sites asked to upload profile photo. Users can join each other with multiple relationships but system needs bidirectional confirmation. Publicly exposing a connection is very sensitive because strangers can get access to friends list, contact information and general page (i.e. wall) unless adequate measures have not been taken by SN designer. Most SNS keep mechanism to drop message [12] towards their friend and some has email like similar service [12] or wall messaging. But there are also some exception as well QQ initiated as instant messaging [12], some SNS launched forum, some other made directory of school associates. Photo and video sharing [6] is another technique and some SNS has targeted group such as religion, location based community, ethnicity, nationality and so on. Numerous researches have been accomplished with social network. Some are highlighted here which are relevant to our task. Authors [9] describe a social network SCHOLAT for scholars, because currently organizations, professionals tend to launch dedicated social network to a specific targeted group. Authors targeted user groups are scientific researchers and teams with academic professionals, research organization. SCHOLAT [9] has an architecture which consists of four types of entities, i.e. profile, activity, resource and relationship. Beato, Kohlweiss and Wouters [20] proposed in their model not to use any dependency of third party and they allow access control for a selective user group. Social networking community represents a large directed graph and to manage the role based access control over private data authors designed a tree-like structure. Authors [20] defined two types of classes based on user profile, such as connections and content classes. They make one lattice of the user’s connection with the defined classes.
Roles [10] are not rigorous and precise in nature; rather it vacillated in course of time or respect to person. According to Bachman [3], role is concept of an ontological primitive, Steimann [14] described, The word ”role” is so universal that determining its accurate meaning is too intricate. ”role” originates from Latin ”rotula” (small wheel), which is also the root of English ”roll” and German ”Rolle”. A role can be played by different players at the same time, to illustrate- member of the panel refused the proposal. A role can be described as lifetimes while some other roles for a certain span of time. As for example, head of a faculty only 3 years while a citizenship of a country to a people is life lasting.
Social identity theory [21] highlights the social nature of self as constituted by society. It is regarded the self as distinguished into multiple identities that influenced by social practices (e.g. norms, roles). Furthermore, it portrays social behavior [21] in terms of reciprocal relation between self and society. It is strongly correlated with the symbolic interactionist view that society changes behavior pattern through its influence on self. Identity theory formulated by Stryker [21], he observed links between a multifaceted notion of self and the wider social constructs. He also proposed that we have numerous components of self called role identities, for each role positions in society that we occupy. To illustrate, a person’s role identity may include the fact that she is mother, wife, a daughter, a social worker, a teacher and a blood donor. Role identities are self view, self perception or self definition that people may apply to them. The social relations model [22] (SRM; Kenny, 1994) is a statistical model for analyzing interpersonal perception and behavior that can be significantly applied to the group therapy situation. It comprise of four basic components that correspond to (a) common emotional atmosphere of the group, (b) the point of view of the perceiver providing the reaction, (c) the group’s consensual approach of the target who receives the feedback, and (d) the single and multiple relationships between the perceiver and the target. The basic attribute of the SRM is that interpersonal perception may be partitioned into four fundamental [22] components, such as- constant, perceiver, target, and relationship, plus an error component. For instance, if Jony dislikes Rony who is a member of his therapy group, each of these components may add to his dislike. Jony and Rony may be members of a very antagonistic group in which the group members generally dislike one another. In SRM terms, the constant reflects this group effect.
Ontology [11] is a formal unambiguous explanation of concepts in the field of discourse (classes), criteria of different attributes of the classes are called roles and limitations/restrictions of those classes are called facets [16]. When a set of instances of those classes are constructed, this is called knowledgebase. For example, classes of person represent every type of persons; they can be doctor, researcher, teacher, politician and so on. A concept of subclass refers more specific than its superclass in its tree hierarchy. Finally constructing ontology includes- declaring the class, make the tree/hierarchy of the taxonomy, mentions the properties and finally insert instances based on respective classes.
-
III. Description Logic
Description Logics (DLs) [30] is the most competent name for knowledge representation (KR) formalization that describes the knowledge of an application domain (the “world”) by first defining the related concepts of the world (its terminology), and then using these concepts to specify properties of objects and individuals occurring in the domain (the world description). Another distinguished [30] feature is preserving the service of reasoning as a central: reasoning allows one to infer implicitly represented knowledge from the knowledge that is explicitly contained in the knowledge base. Description Logics support inference and deduction reasoning that occurs in many applications of intelligent information processing systems.
DL has dissimilarities [33] from their predecessors, such as semantic networks and frames, in that they are constructed with a formal, logic-based semantics. A standard example can be given from the following statement: “A woman that is married to an engineer, and at least one of whose children are architect.” This concept can be described with the following concept description:
Human П male П (∃married.․ Engineer)П(ℎasCℎlid․ arcℎitect)
Concept description builds statements in a DL knowledge base, which can be divided in two parts: terminological and assertional . The terminological [33] part is known as TBox, it can be described the relevant ideas of an application domain declaring the properties of concepts and roles, and relationships between them. Precisely a TBox statement can be introduced a name for a complex description. For instance, an individual Anna, belongs to married.Engineer if there exists an individual that is married to Anna and is an Engineer.
Classification [30] of concepts determines subconcept/superconcept relationships (called subsumption relationship) between the concepts of a given terminology, and eventually construct a structure the terminology in the form of a subsumption hierarchy. This tree structure provides useful information linking among different concepts and it can be used to accelerate inference services. Classification of individuals describes whether a given individual is always an instance of a certain concept. It thus provides useful information on the properties of an individual.
-
IV. Common Errors in Traditional SNs:4.1 Fail to represent true social structure:
-
4.2 Inappropriate relational semantics
-
4.3 Offering obscure suggestion
In recent times, confidentiality [2] is highly concern in any SNS, e.g. childhood friends of Dan call him up with satiric nick name in SN wall which may be beginning of mocking inside the circle of his present colleagues, eventually might bring an unexpected situation. In social network, the way we interconnected [32] with each other would be a real fun, if we could speak softly with someone, love to my child with my informal argot and maintaining formal relationship to my acquaintances without informing people of other levels in my member list not analogous to facebook wall page. And lot more disgraced examples can be provided [32] in our social network which might discomfit the group. Although Facebook group can classify the people who want to attend into customized interaction, yet they are in a generic relationship [32] (e.g. group member role) with each other instead of individual role (e.g. in a family group of Facebook are members, rather it would be more touching when wife can view his spouse as “Husband” and vice versa). In these cases, the typical social networks like facebook, myspace [26], orkut [25], google+ don’t have adequate measures.
At current times, it is observed that some well accepted social networking (e.g. facebook [24]) site has been started relationship mechanism in their web, but it exposes social constraint during multiple assignment of relationships at the same time. Lack semantics and inference of background knowledge [32], any social network may falter and eventually exposed to incorrect consequences.
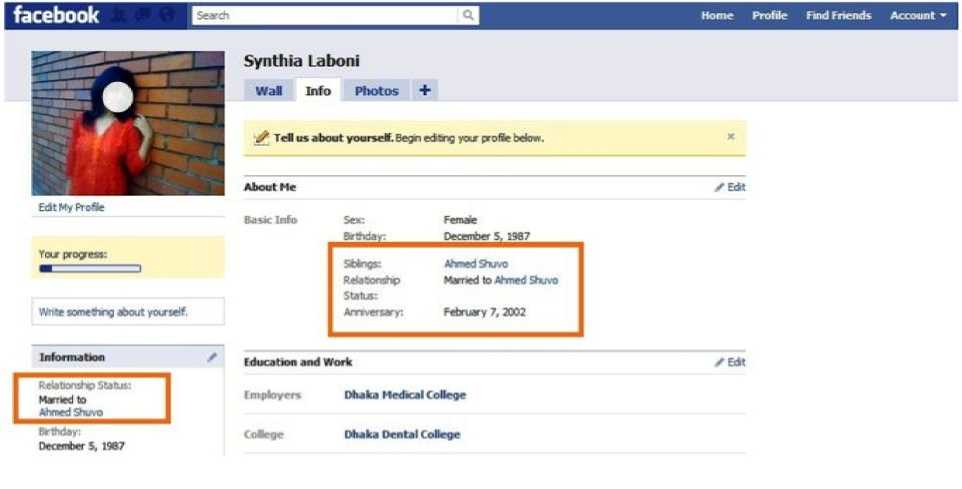
Fig. 1: Husband can be set as sibling
Fig. 1 shows the inability of facebook to preserve the relationship integrity among members. It is a profile of one female user named”Synthia Laboni”. Some experiments have been carried out on her account with her proper consent. She is married to”Ahmed Shuvo” which is showed in Fig. 1. It elucidated inconsistency that “Ahmed Shuvo” can be set as siblings while he is husband of her at the same time. System has no spontaneous restriction [32] checking to assign any relationship with the opponent user. Facebook system hardly uses automatic reasoning power to handle these erroneous contexts.
Some banal terms, just as “friend/fellow”, we are using in our contemporary social networks. Sometimes it misguides the communication instead of exchanging original meaning. These terms are obscure and generic [32]. Because David can be friend of Jac, Jac is friend of Paul and this does not mean David is friend of Paul, reverse (foe) might be true. But these SNS anticipate and send random suggestions towards member of the network. This type of indiscriminate suggestion often makes irritating situations to the users. Our conventional social networks impute us to be in a common platform of our relation which does not bring out significant and accurate senses in all cases. It would [32] be more rational if a suggestion appears with proper social role name e.g. my brother’s profile is suggested like “he might be your brother”.
-
V. Proposed Approach5.1 Conceptual Solution
While working with the set of objects (e.g. image, message, role based wall page, role based streaming and so on), field of classification [16] contribute to formulate into a small number of classes. Every component we are dealing in role based social network (RBSN) [32] is treated as entity [16] (e.g. person, organization, homepage, wall page, event, image, documents, audio or video.) and they belong to specific types of concept [16]. As we are stepping forward to perform our whole task, our main focus are following three issues- reciprocal connection creation (relationship can be two types- one is symmetric relationship pair, for instance- colleague-colleague, brother-brother. Alternatively, asymmetric relationship pairs could be father-son, husband-wife and many more ), removing the scope of bizarre relationship assignment (explained in 4.2) and role based data exposing upon the roles wall (explained in sec 4.1) [32], To begin with , while one person instance is connected with other person instance, that must be linked through via reciprocal roles of ontology. Henceforth, Identity theory [21] explains the bi-directional relations between self and society which is our main underneath tool behind exposing individual wall, based on role.
We have Classified the role as a rooted tree [27], Role =
, where P is the set of persons[32] and C is the context in which situation the person set P is associated with the relation, Rel. To illustrate, my wife could be my colleague and spouse at the same time but in different context. So Pi person can be mapped by Reli to Person Pj with context Ci. Roles [10] are the functional and dynamic properties of a person that characterizes him/her identity in a particular social setting and time.
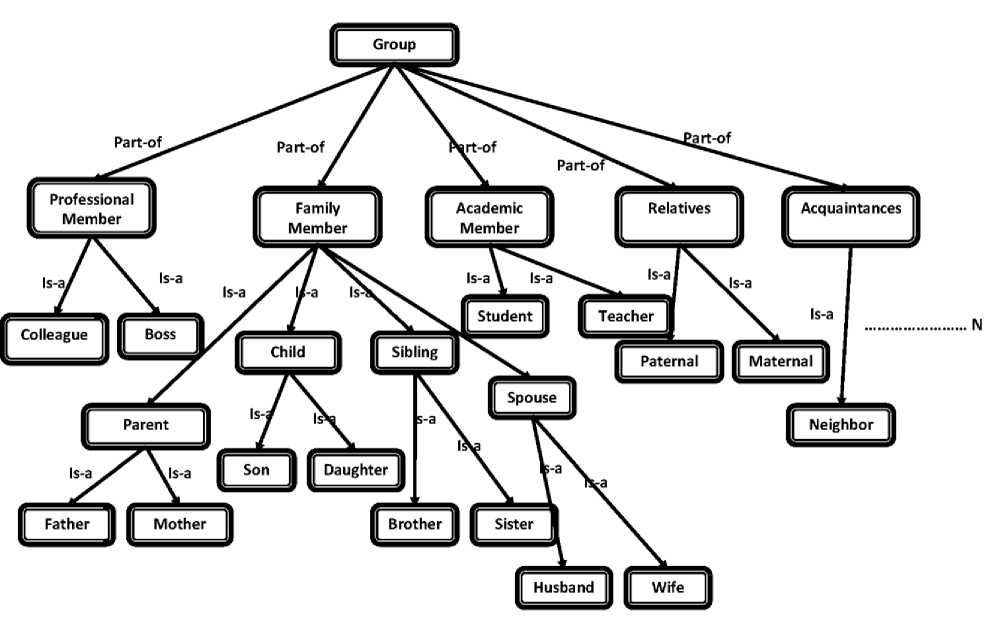
Fig. 2: A Limited sample role ontology for RBSN
In our limited role ontology in Fig. 2 . , in the top of the hierarchy/tree [16], we put “group” which is super class of all role concepts [16] and other social roles are kept as “part-of” and “is-a” relationship. Under the part of relationship, we have kept major types, such as-professional, family, academic, relative and acquaintances members. Some roles in the tree are general [16] (i.e. academic member) while others are specific [16] (i.e. boss or colleague). Our constructed ontology [11] includes hierarchy of the role taxonomy, their individual properties. Lastly, we have inserted the person instances in the respective classes pertaining to their roles. Understanding the sharing of knowledge, reusing the taxonomy by any group, to keep an opportunity to integrate ontologies [5] developed by others are main objective of our semantic base approach.
Another social physiological model SRM [22] which unveils four components regarding interpersonal perception and behavior significantly implement to group setting The components which are relevant towards our work are as follows, general attitude towards group, group view of the perceiver feedback and unique relationship between perceiver and target. We are inspired [32] from SRM [22] model having specification and generalization within the role based members which is the indicator the degree of intimacy among group members. Another issue- error factor has been mentioned in SRM model, we have made a barricade to gain access towards the therapy group unless he is an expected person. Any feedback (positive/negative) by the perceiver should be reachable towards the sender if he is the member of that group.
-
5.2 Formalization of RBSN using description logic
-
5.2.1 Possible multiple roles among subjects (users):
Description logic is a familiar language to represent knowledge; it is prominent for more expressiveness rather than Propositional and first order logic. We have described and formulated [28][29] different semantic features of RBSN by DL in the following subsection.
We can observe from facebook that already connected people can assign more relationship among them as described in the section IV(A). Even google+ plus has introduced the provision of adding to circle. Both of the cases, the system fail to preserve the social constraint and restriction. But RBSN is able to deal with these bizarre and wrong contexts with DL proficiently. We could exploit and dilate the equality rule according to our social context; we have only formalized and constructed the rules [28][29] with very basic role names. Some examples are provided below in respect of our network:
-
a)
Brot ℎ er ≡ ( Family Member
⊔ Professional Member
⊔ Academic Member
⊔ Neig ℎ bor ) П ⌐ ( Fat ℎ er
⊔ Son )
Brother can be linked with brother with not only specific role name but also can be connected with some other roles at the same time which raise no controversy according to society, e.g. brother is a Family member, be colleague or boss as well, might be teacher or student, on the contrary, he cannot be father or son of that person.
-
b)
Daug ℎ ter ≡ ( Family Member
⊔ Professional Member
⊔ Academic Member
⊔ Neig ℎ bor ) П ⌐ ( Mot ℎ er
⊔ Wife ⊔ Sister )
Any person is permitted to connect with his daughter with multiple roles and those very roles must be validated through the aforementioned rule of RBSN to avoid peculiar behavior.
-
c)
-
5.2.2 Disjoint role members of a family group:
Spouse ≡ ⊔ Cousin
⊔ Academic Member ⊔ Neig ℎ bor
Spouse role member is allowed to tie with his/her counter person by multiple roles.
Disjoint relationship can be depicted when two or more sets having no members in common and produce an empty set after making an intersection operation among them. Disjoint role member provision should be kept in RBSN to make it more powerful to enhance its semantic power. As we have described in section V that two knotted persons can establish multiple role names between them, but those roles should compatible with our social structure. Following three rules clearly depict about specific cases how they are disjoint in nature with their role members
Spouse ≡ ⌐( Parent П Siblings П c ℎ lid )
Parent ≡ ⌐( Spouse П Siblings П c ℎ lid )
C ℎ lid ≡ ⌐( Spouse П Siblings П parent )
-
5.2.3 Major Rules which is going to be used by RBSN are formalized By DL as follows:
Some of the major rules for any social network are common in nature, for instance, the diffusion process to interact among users need to start from any point. And our role based network has some more fascinating features. All of the generic and special features, we have logically construed by DL in the following texts.
-
1) User can be search a person by name/partial name.
FamilyMember ⊑ Searc ℎ: byname ⊔ byPartialName
-
2) While someone intends to connected with others by role, can send a request by “ add role member ”
ProfessionalMember ⊑ SendRequest ∶
-
3) Receiver can be connected [28][29] with sender more than one roles, but the roles should not fall any of the disjoint set.
Jack ⊑ ≥ 1 Connect ․ role ( User1 \( Parent П Sibling П C ℎ lid )
To illustrate the context, Jack wants to link with any user from his group member list with spouse role, because he can possess more than one relationship with any person. So, the rule depicts that parent, sibling and child role are in the disjoint class of spouse role as described in5.2.2.
-
4) Every User has 2 types of wall pages, general & role based wall page which can be written in DL as follows,
User ⊑ ℎ asWallPage ( GeneralPage П Rolepage )
-
5) When any user writes on general page it automatically propagate to role page but not vice versa.
Oi ⊑ 02 but 02 ⊑ Oi not true
∃ WriteOnGeneralPage ․ data ( Mukta ) ⊑∀ ReadOnRolePage ․ data ( Mukta )
Oi is described as general page (e.g. wallpage like facebook and stream page like google+) whereas O2 is described as role based page. If someone shares a general information, i.e. just as, Bauer wants to share amessage that he is blessed with baby. But it is very much tedious and cumbersome to write on every role pages rather it is facile to access and write in only location, and it would be convenient if system could propagate the message among all the role members. But reverse is not true for this issue, as role base information should be confined inside the circle, contrary it may arise fatal inter-role domain data leakage. Our system will act in the similar way and written DL rule is described in such a manner so that system performs in the identical fashion.
-
6) To assign any role, recipient has precedence over sender because sender is interested to make connection. Link setting depends on the willingness of the receiver how he perceives and exploits the request sender.
Oi ≥ 02 iff 0. ⊑ O2
Ui ≥ U2 iff u. ⊑ иг
∃accept․ addRole(Y) ⊑ ( SendRequest ∶ ) (X)
In particular, X is interested to tie by a role with Y , thereby X sends a request to Y pressing with “add member” action. But supreme authority to adding to any of the role classes has been provided to accepting end. One counter example makes the context more understandable. If someone wants with malevolence attitude to connect any girl as “girl friend” role, (nonetheless we haven’t mentioned this role in the ontology, but it is obvious it can be expanded according to context requirement), this might lead to a awkward consequences. To overcome this problem, our precedence measure can afford strongly.
-
7) Already connected user can assign more than one role
Membership checking [28][29]:
{Sibling(Sam), Sibling⊑ familyMember, familyMember ⊑ roleTree} |
= ( Sam ) ⊑ ≥ 2 assign ․ role ( Sam )
Before making a new connection with any member, it is very primitive to check his/her membership inside my role tree, and DL provides such a nice tool to verify the existence of member. At the same time, if he already be presented in my role tree, he could be connected by more or two role names.
-
VI. Semantic Web Technologies Used in RBSN:
In an article written by Tim Berners-Lee, Jim Hendler and Ora Lassila [31] in Scientific American in May 200, they described that 'The Semantic Web will bring structure to the meaningful content of Web pages, creating an environment where software agents roaming from page to page can readily carry out
To motivate the Semantic Web is required to discover documents on the Web, not only from their textual content [31] like search engine does, but also from a meaning, context and description. To add and reuse these descriptions or annotations, it is fundamental to articulate what this additional description, called 'metadata', [31] should be, and how it should be perceived. Web consists of set of technologies, tools and standards which build basic components of a system that could support to realize the meaning. Roles and objects provide richer language for providing more intricate constraint and condition on the types of resources and their properties which they possess. If we think semantic web as layered architecture then top of the ontology technologies as there logics and proof layers embed which are capable of making inferences [31] and deduction of new rules. In our case we have chosen the DL most appropriate logic language and for converting the ontologies into usable format web ontology language (OWL).
Web page is in fact syntactic information on format while we are interested in modeling the semantics of what it means to be a general page or role page. A role page can be a virtual representation of an entity [32] (e.g. person, organization or event) which is a format to display information depends on role and relationship. Various pages would be a specification with some precodified style frames by an algorithm depending on roles. Frames are nothing but sub-components of general/role page, could in turn have some sub-frames as well. In synopsis, it could be said that general /role page can be seen as a tree [16] like structure made by frames and sub frames.
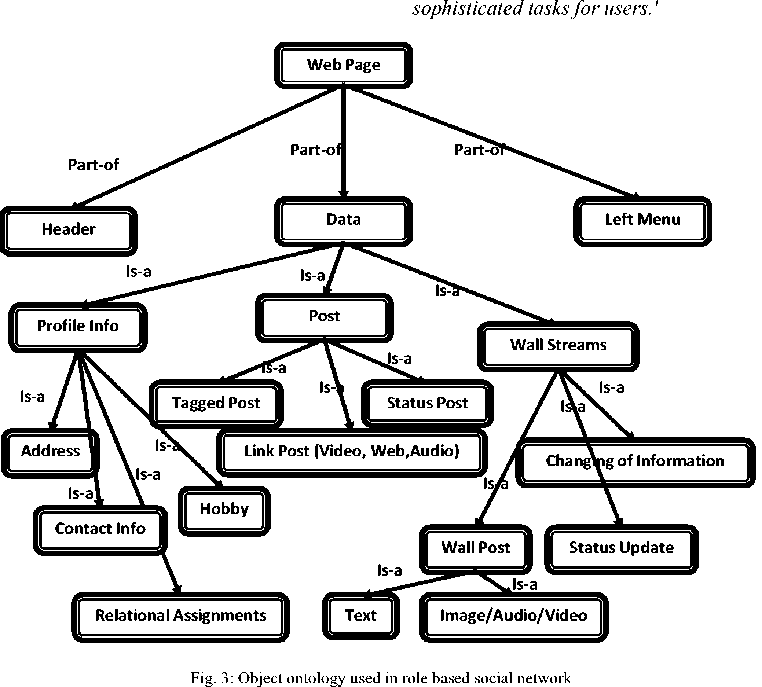
Fig. 3 describes about different types of object used in our RBSN on the format of the webpage. Webpage composed of left menu, right menu and centre panel where we are customizing the data subject to role. Simple and typical data ontology has been presented in object tree. Data is connected with webpage by part-of relationship like header and left menu. On the contrary, the dynamic information based on person to person varies is connected with data with is-a relationship because these data are specified version depending on roles. Data can be specified in three ways, personal information is called in RBSN profile info, posts by individuals with texture like tagged, status and link posting. Whereas wall streams might be by own or others, in this category graphic data might be existed as well. Since, we have discussed the purpose of ontology technologies, while accessing objects by role member can manage sophisticatedly in our subtle contexts.
Firstly, we can describe in Fig. 4, how do we access an individual object relating with role. For this reason, role and object ontology need to communicate with each other.
String image_type=”family_object”;
String queryString ="PREFIX rdfs: <> " + "PREFIX j.0:
<>”+ "select? y “+ " where {“+”
Fig. 4: A snap of SPARQL query to extract images which is only assigned to family role members from OWL
Secondly , as we are interested to deal with disjoint set by semantic web technology, OWL is the primary machinery to handle it delicately. OWL has three triples- user acts as subject, disjoint set property acts as attribute and object is the returning list of disjoint roles those who are prohibited with the inserted user role. Disjoint class [15] ensures that individual of one class cannot be instance of another class simultaneously.
Fig. 5: A subtree from the role ontology translated into OWL.SPARQAL [18] language has the power to make query from our OWL role which is shown in the Fig. 4 and 5.
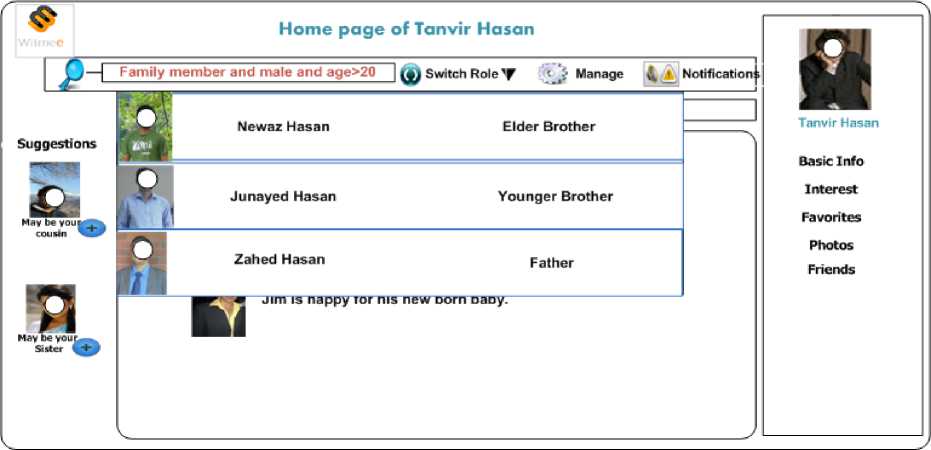
f ig . 6: r ole based semantic search from group member
Thirdly, to handle the deficiency of maintaining of original social structure, we have proposed to provide an opportunity through user customized wall/general page to interact with his targeted group subjecting to dynamics of social identity [10]. We are interested in general page (i.e. wall) but not in web page. Entity related values; attributes (i.e. name, email, info, educational background, favorites and so on) are kept, retrieved and manipulated in this platform. Fig. 3 shows “family” role general page where news stream of family members with their profile picture and role name. At the chat box online members belong to that role group will be displayed also. If it would be “spouse” role, then that role still belongs to family member but its preference of intimacy is supposed to be higher degree than others. These generalization [16] and specification [16] are maintained with ontology [15] technology. We have showed that a user will send a request for connection to another RSBN member who will accept and determine the. In this tree the terminals are more specific then the non-terminals. So when any information is shared on the terminal level is closed in that level where else the information shared in the nonterminal level is shared with its child nodes.
E.g. we shared any information in the family level will be shared with child, parent, siblings, spouse along with their nested terminals, but reverse propagation of preference of data is not allowed as they are more specific. We have the terminology of disjoint set that will help to prevent bizarre relationship assignment.
String subject_role=”Spouse”;
String queryString="PREFIX rdfs:
<> "+ "PREFIX owl:
<> "+"select ?uri "+"where { "+"?uri owl:disjointWith
Fig. 7: Query with SPARQL from the subtree in the Fig. 4. to elicit role names those who are disjoint with spouse role
When we want to add a new relation with an existing member, a disjoint set [15] of current role name will be returned from the system. If the requested relation belongs to that disjoint set then it will be refused to prevent bizarre relationship assignment. We have described the member’s suggestion technique, where family member will be suggested with proper social role addressing. Like Person assigned to my brothers as father will be suggested to me as father and person assigned to my sister’s husband will suggested to me as brother in law.
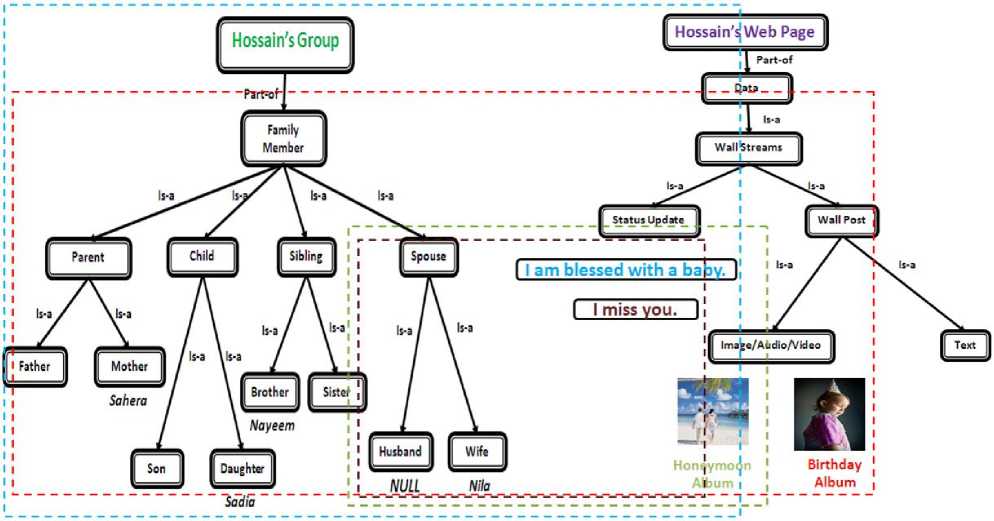
Fig. 8: Access boundaries for different objects from Hossain’s Webpage to Hossain’s role tree ( Boundary color indicates the boundary for specific object of that color. )
Lastly, RBSN is able to search role base members and their object semantically depending on their selected criteria. Sometimes we may need to filter down our search space among all the group members. Fig 6 describes the advance searching technique inside the group. To illustrate the context, user needs to find out family members who are male and age lies between 20 to 55 who are capable of outing for mountain trekking, so that one multicasting message could be send as invitation. We haven’t found this level of granular filtering in our so-called social networks. Fig 8 describes how to share images, text from the user’s role and resource ontology perspective. The Fig is marked with different color boundaries. Text propagation among the users depend on nature of the role, e.g Hossain is missing her spouse, so the message should be visualized by his wife only and at the same time he is blessed with a baby, this message should be disseminated to all of the group members in that group. So it is cogent how the network performs action from the Fig. 8.
-
VII. Conclusion
Since we want to exploit and desire to appease a harmonic interaction among users, henceforth our concentration on major three dimensions- social context as it is a virtual society, psychological aspect how the members are interacting and in what extent they are comfortable to interact with each other. So called social networks are called nominally because of its some limiting factors in compare with the original society.
Список литературы Semantic Enabled Role Based Social Network
- Danah M. Boyd and Nicole Ellison, “Social network sites: Definition, history, and scholarship.” J. Computer-Mediated Communication, 13(1):210–230, 2007.
- Catherine Dwyer, Starr Hiltz, and Katia Passerini, “Trust and privacy concern within social networking sites: A comparison of facebook and myspace.” Americas Conference on Information Systems, 2007.
- C. W. Bachman and M. Daya, “The role concept in data models”. In Proceedings of the Third International Conference on Very Large Data Bases (VLDB),IEEE Computer Society., (2):464476, June 1977.
- Linda Banwell and Graham Coulson,“ Users and user study methodology”:the jubilee project. Inf. Res., 9(2), 2003.
- T. Gruber, “A translation approach to portable ontology specifications”, Knowledge Acquisition, 5(2):199–220, June 1993.
- Saikat Guha, Kevin Tang and Paul Francis, “Noyb: privacy in online social networks”. In WOSP 08: Proceedings of the first workshop on Online social networks, New York, NY, USA, 2008. ACM., page pages 4954, 2008.
- PostgreSQL. See at http://www.postgresql.org/.
- Effie Law, Virpi Roto, Arnold P. O. S. Vermeeren, Joke Kort, and Marc Hassenzahl, “Towards a shared definition of user experience”. In CHI ’08: CHI ’08 extended abstracts on Human factors in computing systems, pages 2395–2398, New York, NY, USA, 2008. ACM.
- Jianguo Li, Yong Tang, Chengjie Mao, Hanjiang Lai, and Jun Zhu, “Role based access control for social network sites”. In Pervasive Computing(JCPC), 2009 Joint Conferences on, pages 389 –394, 2009.
- Claudio Masolo, Laure Vieu, Emanuele Bottazzi, Carola Catenacci, Roberta Ferrario, Aldo Gangemi, and Nicola Guarino, “Social roles and their descriptions”. In KR, pages 267–277, 2004.
- N.F. Noyn and Mcguiness D. L, “Ontology development 101: A guide to creating your first ontology”. In Stanford Knowledge Systems Laboratory Technical Report KSL-01-05 and Stanford Medical Informatics Technical Report SMI-2001-0880, 2001.
- Alexander Richter and Michael Koch, “Functions of social networking services”. In MultikonferenzWirtschaftsinformatik, 2008.
- Jasper A. Schelling, “Social network visualization”. PhD thesis, 2007.
- Friedrich Steimann, “The role data model revisited”. Applied Ontology, 2(2):89–103, 2007.
- OWL Web Ontology Language Guide, - See at http://www.w3.org/TR/2004/REC-owl-guide 20040210/#DisjointClasses
- Fausto Giunchiglia, Biswanath Dutta, Vincenzo Maltese, “Faceted Lightweight Ontologies”. Conceptual Modeling: Foundations and Applications 2009: 36-51.
- Jena A Semantic Web Framework for JAVA. See at http://jena.sourceforge.net/index.html.
- SPARQL Query Language for RDF. See athttp://www.w3.org /TR/rdfsparql-query/
- Spring Framework. See at http://static.springsource.org/spring/docs/2.0.x/reference/mvc.htm
- F. Beato, M. Kohlweiss, and K. Wouters. “Enforcing access control in social networks”. Hot Pets, (2):199–220, June 2009.
- Michael A. Hogg, Deborah J. Terry, Katherine M. White. “A Tale of Two Theories: A Critical Comparison of Identity Theory with Social Identity Theory”. Social Psychology Quarterly, Vol. 58, No. 4 (Dec., 1995), pp. 255-269
- David K. Marcus, “Interpersonal Feedback :A Social Relations Perspective.” International journal of group psychotherapy, 56 (2) 2006.
- Google+. See at http://www.plus.google.com
- Facebook. See at http://facebook.com
- Orkut. See at http://www.orkut.com/
- MySpace. See at http://www.myspace.com/
- Fausto Giunchiglia, Maurizio Marchese, Ilya Zaihrayeu: Encoding Classifications into Lightweight Ontologies. J. Data Semantics 8: 57-81 (2007).
- Fausto Giunchiglia, Rui Zhang, Bruno Crispo- “RelBAC: Relation Based Access Control”, Proceedings of the Fourth International Conference on Semantics, Knowledge and Grid. (SKG 2008) Beijing, China, December 2008, pages 3-11.
- Fausto Giunchiglia, Rui Zhang, Bruno Crispo, “Ontology Driven Community Access Control “, Proceedings of the Trust and Privacy on the Social and Semantic Web Workshop. (SPOT 2009) Heraklion, Greece, June 2009.
- See at http://www.inf.unibz.it/~franconi/dl/course/dlhb/dlhb-02.pdf
- Dr. Brian Matthews , “Semantic web technologies”. See at http://www.jisc.ac.uk/uploaded_documents/jisctsw_05_02bpdf.pdf
- Md. Saddam Hossain Mukta, Khandakar Tabin Hasan, Sazzad Hossain, “Ontology driven role based social network”, International Conference on Informatics, Electronics and vision, pp:908-913, May 17-18, Dahaka, Bangladesh.
- See at http://www.cs.ox.ac.uk/ian.horrocks/Publications/download/2007/BaHS07a.pdf


