Survey of primary methods of fingerprint feature extraction
Бесплатный доступ
Proving the identity of the individual today is an urgent need in many areas, including social security, financial, criminal and other fields. Biometrics is interested in identifying individuals through personality traits, eye color, fingerprints, height, facial appearance, and signature. Image processing technology supports most of the techniques used in biometrics, by improving images and matching images, to identify the individual identity. Fingerprint recognition is some of the most well-known biometrics, and it the best the used biometric result for confirmation on computer systems. Technic fingerprinting has a great popularity for simplicity of acquisition, the use and approval when compared to other systems. Fingerprint Recognition System consists of four steps: firstly, Image acquisition (image fingerprint) through sensors.Secondly, processing the image so that it obscures the noise that exists, clarifying the hills. Thirdly, Extracting features of injury fingerprints. Fourth, compare the acquired features with features of fingerprint fingerprints in databases. The aim of this paper is to present the latest research in the applications of fingerprint recognition systems.
Fingerprint, methods of recognition, correlation comparison, a comparison of the pattern, equalization, gabor filter
Короткий адрес: https://sciup.org/147155238
IDR: 147155238 | УДК: 004.93.1 | DOI: 10.14529/ctcr180117
Текст краткого сообщения Survey of primary methods of fingerprint feature extraction
Nowadays, with the development of computer technologies, one of the main fields of research becomes the identification (recognition) of objects’ images, including identification of fingerprints. The availability of the method and the wide range of techniques on the one hand, and the complexity of objects on the other hand, make the task of identification especially interesting and trying. New technologies allow to recognize a person by various characteristics – physiological, psychological etc. Recently, the processes associated with the identification by fingerprints, have had various reasons for being studied and approaches to do so, as the latter depend on a number of factors. It is obvious, that in the future, biometric technology will be widely applied. The paper is structured as follows. Section 1 describes the fingerprint pattern feature and characteristics. Section 2 is dedicated to receiving an image from a scanner and image enhancement. Section 3 provides a convergence between of two fingerprint images. In conclusion, the results are summed up.
Fingerprint
A fingerprint pattern feature is shown in Fig. 1, formed by a sequences of lines, matching to ridges

Fig. 1. Fingerprint
and valleys on the Surface of the fingertip, each fingerprint has a unique pattern. They are called minutiae (features or singular points) that is unique for each fingerprint characteristics defining the points of changes in the structure of papillary lines (ending, bifurcation, break, etc.), the orientation of papillary lines and the coordinates of these points and the characteristics of fingerprints [1]. They do not change along the life.
In Table 1 shows the terms and definitions of fingerprint structure [3].
Table 1
|
No. |
Term |
Definition |
|
1 |
Ending |
The location where a ridge comes to an end |
|
2 |
Bifurcation |
The location where a ridge divides into two separate ridges |
|
3 |
Binarization |
A process to transform the image from 256 levels to two levels (0, 1) refers to (black and white) respectively |
|
4 |
Thinning |
The process of reducing the width of each ridge to one pixel |
|
5 |
Ending Angle |
Considered as angle between the direction of the ridge and the horizontal |
|
6 |
Bifurcation Angle |
Which Considered as the angle between the direction of the valley ending between the bifurcations and the horizontal |
|
7 |
Matching Score |
It is the measure of similarity between the input and template data |
|
8 |
False Non-Matching Ratio |
The system fail to detect a match between input and template in database |
Fingerprint Recognition
It is important to have fingerprints done properly, so that to be able to choose the appropriate research method for identification image. When the image has distortions, it is important to find the right algorithm that can reduce or even remove inaccuracies. Fingerprint contact ridge details are normally styled in a classified order at three levels, namely,
First Level (pattern), Second Level (minutiae points), and Third Level (pores and ridge contours) [5, 14]. Traditionally, they distinguish general and individual features. Global characteristics are those that are visible to the eye: the papillary pattern, hills and valleys, centration (core) [6], delta region etc. In practice fingerprinting papillary patterns of the fingers are divided into three main patterns: Arc (about 5 % of all fingerprints), loop (65 %) and a whirl (30 %) is shown in Fig. 2.

Fig. 2. Fingerprint patterns
Basic patterns of fingerprints in the order of natural distribution: a) Left loop, b) Right loop, c) Whorl, d) Arc, e) Accidently.
Individual features include such items that make the pattern unique. These may include alternations in the structure of papillary lines (ending, bifurcation, break, etc.), the orientation of papillary lines and the coordinates of these points. Each print may contains up to 150 details, especially rolled fingerprints [7].

a)
c)
b)
Fig. 3. Sample details
The fingerprint image in Fig. 3 displays the following details: endpoint (end of projections) – the point at which “clearly” over the ledges as shown in Fig. 3а, branch points – the point at which the divergence of the lines of projection as Fig. 3b. Pores also be detected on the ridges, pores are often divided into two types: open and closed. The closed pores are a closed content by the ridge, while an open pore intersects with the valley as in Fig. 3c [5]. As you know, the fingerprints of some people to match up and have some damn global features. But exactly the same parts of the pattern of the fingerprint is not found [8]. Currently, in order to discern the details of the pattern and subsequently identify the fingerprint, electronic scanning is widely used [4].
Recognition Rate
The final criterion of the feasibility of the fingerprint system for application, is the recognition rate. This can be assessed by two criteria: The false acceptance rate: is the ratio of the number of cases of couples of dissimilar fingerprints found to (mistakenly) match to the full number of match attempts. This value is called (FAR) .The false rejection rate: is the Average of the number of cases of couples of the same fingerprint are detected not to match to the full number of match attempts .This value is called (FRR). FAR and FRR are incompatible with each other. Where the system can be adapted to change these two values for the performance of a specific application, although increasing one of them decreases the other and vice versa, Where the ATM (which need a very low rate of false refusal), and military installations (which need a very low rate of false acceptance) [9].
Image processing
There are a number of image processing algorithms. The aim is to make some improvements to the fingerprint image for the purpose of detecting its features. Receives an input fingerprint image, applies a set of intermediate steps on the input image, and finally outputs the enhanced image.
Image acquisition
When receiving an image with a scanner 300–500 dpi, the image shows some details which in automated system are considered to be the details of the pattern (special points): endpoint – the point at which clearly see the papillary lines, the branch point is defined as a point with double papillary lines. In Fig. 4 we can see end points and branch points.
When receiving an image at 1000 dpi it is possible to recognize the structure of papillary lines, namely the pores of the sweat gland Fig. 5, the data obtained this way [10], can be surely used for identification. This technique is not widely practiced because of the complexity in obtaining images in such format.
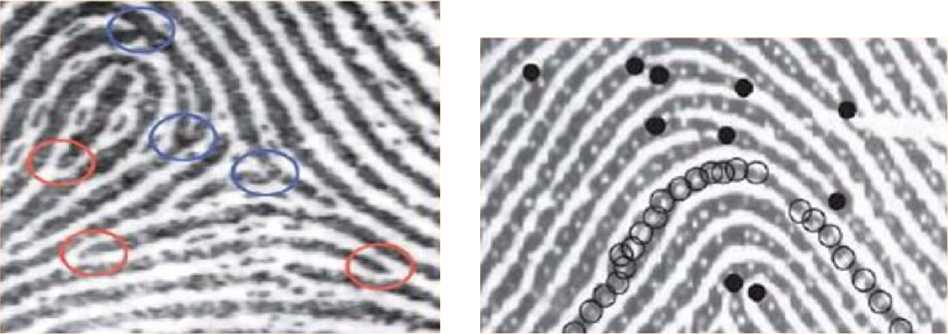
Fig. 4. Endpoint and branch point Fig. 5. Pores of the sweat glands
Image Enhancement
Studying the practical experience of working with various images, including fingerprints, one can notice that the processing usually takes several stages. Initially it is necessary to measure the histogram of the original image. The brightness of the image should be in the range of 0…255.
The histogram is presented by 256 values. Each value represents the point in the table that have the same level of brightness. Tabular data is divided into the total sample size, which is equal to the number points of used in the image, that in the subsequently describe the probability of brightness distribution in the image.
The second stage is to perform nonlinear transformations, which ensure the required properties of the output image. Histogram held in the first stage allows the use of estimated data, while not using the unknown true distribution.
Equalization (leveling) of the histogram is change, improving the output of the digital image. Histogram methods are used in the cases when it is necessary to conduct a qualitative alternation of the input image [11].
In equalization of the fingerprint image the most important remains a visual change of the image. This will allow in future economizing efforts on the decision algorithm and choosing a particular method, and made more efficient work of identification by fingerprints Fig. 6.

a) b)
Fig. 6. Equalization (leveling) of the histogram
A characteristic feature of this image is lack of brightness, the predominance of dark colors in the image Fig. 6a, b. We can clearly see the improvement in visual perception. Filtering another one of the methods that allows you to handle any image, including fingerprints. This method receives the same image as the input, only the amended version [12].
It was stated in the works of many authors that the filtration technique is currently considered to be the most perspective, we can say that when analyzing one or another image you need to acquire the algorithm of the method of image processing, in order to receive the most precise result in the end. Let us consider the Gabor filter, which has a frequency selection and orientation qualifying properties that give the optimal combined response, in both location and frequency. There are so-called band pass filters to eliminate noise and retain the fine structure of the projections and depressions.
Directly symmetric Gabor filter can be described by the formula:
h ( x , у : 0 , f ) = exp J- 1 ^ + yA I cos ( 2 Л fx 0 ) , 2 L 5 x 5 у J
Modulation and transfer function (MTF) of Gabor filter can be represented in a formula as follows:
H ( U , V : 0, f ) = 2n 5 x 5 у eXP ^ -
( u 0 u 0 ) . ( v 0 v 0 )
5 2 5 2
H
+ 2n 5 x 5 у exp <
—
( u 0 + u 0 ) . ( v 0 + v 0 )
5 2 5 2
When working with Gabor filter, we set specific data: frequency of the sinusoidal plane wave, f; the direction of the filter 5 x and 5 y , and standard deviations by Gauss.
It is known that a sinusoidal plane wave, f , is determined by the local frequency of protrusion and the direction of the local orientation of the ridge. The selection of variables and it is not unique. It is possible that the filter will form about the protrusions and depressions.
If the magnitudes 5x and 5y are lower, the probability that the filter will show false the protrusions and depressions is rather small. On the other hand, the less the filters create false protrusions and depres- sions; the less efficient it is in removing image noise, Fig. 7 illustrates the Gabor filter processing. Indistinct is the input fingerprint image but in the output image we can see clear lines.

Fig. 7. The Gabor filter image processing
The r esul t s sho w ed t h at t he methods of filtering with the Gabor filter to adm i n ist er be c a us e of t h e ne e d t o sp end a lot of co m p uti ng. F o r e xa mp l e , wh e n t he smoo t hing effect of the papillary lines are blurr e d o n t h e gro un d s, an d t hi s adversely affects the recognition by fingerpri nt. Spati al filte ri n g i s t h e m o st su it ab l e me t h od , i t i s the absorption and reflection of light by the surfac e . I n Fig. 8 improved image of th e f inge rprin t , w hi c h i s obtained after processing the alternative algorit h m .

Fig. 8. The result of the fingerprint alternative algorithm image processing
In the pr oce s s o f a ut oma t i on a n d c omp ut er i zati o n t h ere is a ne w i ss u e fo r study and development, t h at i s , id e n ti fi c a ti o n b y fing erp ri nts. It is impossible to determine the best method f or i d ent i fi catio n.
We sh o uld u se t h e co m b i n ation of techniques, it is necessary to combine metho d s f or r el i a bility a n d e f f ici e n c y . I t i s il lu str a ted t ha t a pplying the splitting fingerprints into subclasses w h i c h a re def i ne d u si n g dis t i nc tiv e si gns that b el o n g t o a pa rtic u la r class, then the subclass need to do search for a specific fin ge rp rin t us i n g any of t he me t h ods desc ribe d a bo v e .
I t is im p oss i b l e to pr ev ent d istortion of the fingerprint image. Upon receipt of th e i m a ge s h ou ld de te r m ine t h e al g o rit h m t o iden t ify all m eth ods of research, and you may have to use them in complex [12]. T hes e ac t io ns w i ll ensu re th e m o s t accurate and faster to identify fingerprints for bi om etric ch a r ac t eri s t ic s.
Fingerprint matching
Mo der n r e se a rch e rs d isti n g uish three types of algorithms for the comparison of fingerprints. Corre l a t i o n c ompa ris o n i s m a d e b y t h e convergence of two fingerprint images, which sho ul d be pu t on e ach other . The n w e c omp ut e t he c orrelation on the basis of the intensity level of th e c o rre spondi n g pixel , which is computed for different alignments of the image. When we obtain the coefficient, it is possible t o make a c e rtai n de c i s i o n o n fi ngerprints identification. But, the method is cons i de r e d t o be i ne ffici e nt , a n d no t wi de l y u se d be cau se pe rfo rmi n g t h e a lg o ri t h m fo r t h is me tho d as we ll as correlation and comparison take too much time [2].
The c ompari son m e tho d is m ost common, it is used quite often and has som e li k ene ss w i t h t h e me t h od des c r ibe d a b ove a s co mpa r ative correlation. This method implies obtaining two s cann e d i ma g e s o f fing e r p r i n ts, thi s i s t h e f ir s t s t a g e, forming a general pattern, where we mark th e e nd poi n ts and bra n ch points [13, 15].
The comparison is performed when the image passed the scanning. Mark the points on the print, then compare them with the general pattern. Decision on identification of fingerprint are taken after comparing the points on the template. This method is displayed in Fig. 9.
There exist one more algorithm – comparison by the pattern. This method implies the comparison of papillary patterns on the fingers. The scanned image is divided into small cells (segments) Fig. 10.
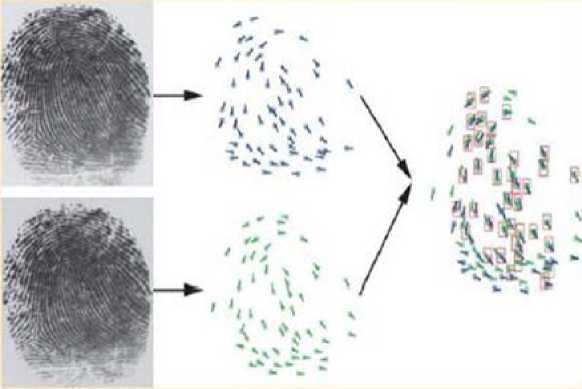
Fig. 9. Comparing the points on the template

Fig. 10. Image divided to small cells
The lines in each segment are described by the parameter of the sine wave Fig. 11, that is, we should assign the starting phase shift (δ), wavelength (λ) and the direction of propagation (θ).

Fig. 11. Sine wave
Receiving a fingerprint for a comparative study, one should transfer it to the same standard as the template. Then compare the boundaries of the wave representations in the corresponding segment. This algorithm is the easiest to use, because does not require a high-quality image.
Conclusion and future work
Through this paper we come out with the conclusion that, for the purpose of verifying the identity of an individual using a fingerprint, the algorithm must pass through several stages, first one Image acquisition (image fingerprint) through sensors. then, Image Processing improving the image like, Gabor filter image processing and fingerprint alternative algorithm image processing, after that fingerprint identification Fingerprint Matching comparing the points on the template, implies obtaining two scanned images of fingerprints, the comparison is performed when the image passed the scanning. Mark the points on the print, then compare them with the general pattern. Decision on identification of fingerprint are taken after comparing the points on the template, thus we obtained the algorithm to prove the identity of the individual using a fingerprint. The next investigation it will be to prepare a study on some of the problems that hinder fingerprint recognition.
Список литературы Survey of primary methods of fingerprint feature extraction
- Ali M.H., Mahale V.H., Yannawar P., Gaikwad A.T. Overview of Fingerprint Recognition System//International Conference on Electrical, Electronics, and Optimization Techniques, ICEEOT, 2016, pp. 1334-1338 DOI: 10.1109/ICEEOT.2016.7754900
- Ross A., Jain A., Reisman J. A Hybrid Fingerprint Matcher//Proceedings of International Conference on Pattern Recognition, 2003, pp.1661-1673 DOI: 10.1016/s0031-3203(02)00349-7
- Bazen A.M. Fingerprint Identification -Feature Extraction, Matching, and Database Search. Univ. of Twente, Enschede, The Netherlands, 2002. 187 p.
- Chen Y., Jain A.K. Beyond Minutiae: A Fingerprint Individuality Model with Pattern, Ridge and Pore Features//International Conference on Biometrics, 2009, pp. 523-533, DOI: 10.1007/978-3-642-01793-3_54
- Coetzee L., Botha E.C. Fingerprint Recognition in Low Quality Images//Pattern Recognition, 1993, vol. 26, no. 10, pp. 1441-1460 DOI: 10.1016/0031-3203(93)90151-l
- Dodds G.H. Identification by Fingerprints//Aust. J. Forensic Sci, 1986, vol. 18, no. 3-4, p. 136 DOI: 10.1080/00450618609411204
- Ferris S., Powers R.L., Lindh T. Hyperladder Fingerprint Matcher, 1997. 36 p.
- Germain R.S., Califano A., Colville S. Fingerprint Matching Using Transformation Parameter Clustering//IEEE Computational Science and Engineering, 1997, vol. 4, iss. 4, pp. 42-49 DOI: 10.1109/99.641608
- Gonzalez R.C. Woods R.E. Digital Image Processing. Editors. A. Dworkin, J. McDonnell. Tom Robbins Pub., 2002. 812 p.
- Gorman L.O. Fingerprint Verification//Springer, Boston, MA, 1998, vol. 3, no. 1, pp 43-64.
- Jain A., Chen Y., Demirkus M. Pores and Ridges: Fingerprint Matching Using Level 3 Features//Engineering, 2006.
- Maltoni D. Maio D., Jain A.K., Pra. S. Handbook of Fingerprint Recognition. USA, Springer Science & Business Media, 2009. 417 p.
- Cynthia D.N., Rodrigues L.J., Nausheeda B.S. A Survey on Fingerprint Recognition Techniques//International Journal of Latest Trends in Engineering and Technology, 2016, pp. 441-447.
- Mahadik S., Narayanan K., Bhoir D.V., Shah D., Access Control System Using Fingerprint Recognition//International Conference on Advances in Computing, Communication and Control, 2009, pp. 306-311 DOI: 10.1145/1523103.1523166
- Yang J., Shin J. W., Min B., Park J. B., Park D. Fingerprint Matching Using Invariant Moment FingerCode and Learning Vector Quantization Neural Network//IEEE Conference Publications on Computational Intelligence and Security, 2006, Vol. 1, pp. 735-738, DOI: 10.1109/ICCIAS.2006.294231


