Vehicle Theft Alert and Location Identification Using GSM, GPS and Web Technologies
Автор: Garba Suleiman, Ibrahim S. Shehu, Olumide S. Adewale, Muhammad B. Abdullahi, Solomon A. Adepoju
Журнал: International Journal of Information Technology and Computer Science(IJITCS) @ijitcs
Статья в выпуске: 7 Vol. 8, 2016 года.
Бесплатный доступ
Insecurity is one of the major challenges that the entire world is facing now, each country having their peculiar security issues. The crime rate in every part of the society these days has become a threatening issue such that vehicles are now used for committing criminal activities more than before. The issue of vehicle theft has increased tremendously, mostly at gunpoint or car parks. In view of these, there is a need for adequate records of stolen, identified and recovered vehicles which are not readily available in our society and as such very important. The development of a vehicle theft alert and location identification system becomes more necessary for vehicle owners to ensure theft prevention and a speedy identification towards recovery efforts in situations where a vehicle is missing, stolen or driven by an unauthorized person. The theft alert function makes use of a GSM application developed and installed in a mobile phone device which is embedded in the vehicle to communicate with the vehicle owner's mobile phone. The communication is established via SMS (i.e. between the installed mobile phone device and that of the vehicle owner). The communications established include; (i). Sending an SMS alert from installed mobile phone device to vehicle owner mobile phone when the car ignition is put on. (ii). Sending an SMS from the vehicle owner's mobile phone to start and stop the installed mobile phone device application. The location identification function makes use of a web application developed to; (i). Determine the real time location of a vehicle by means of tracking using GPS. (ii). Broadcast missing or stolen vehicle information to social media and security agency. The implementation of the installed mobile phone device application was done using JAVA because of its capabilities in programming mobile applications while PHP and MySQL was used for the web application functions. Integration testing of the system was carried out using simple percentage calculation for the performance evaluation. Fifty seven (57) vehicle owners were sampled and questionnaires were distributed to them in order to ascertain the acceptability and workability of the developed system. The result obtained shows the effectiveness of the system and hence it can be used to effectively monitor vehicle as it is been driven within or outside its jurisdiction. More so, the system can be used as database of missing, identified or recovered vehicles by various security agencies.
Vehicle, Theft alert, Location identification, Tracking, GPS
Короткий адрес: https://sciup.org/15012502
IDR: 15012502
Текст научной статьи Vehicle Theft Alert and Location Identification Using GSM, GPS and Web Technologies
Published Online July 2016 in MECS
Insecurity is among the challenges that the entire world is battling with, each part of the world with different security issues. Crime rate in our society these days is becoming frightening as vehicles are been used for committing crime and research shows that perpetrators of this acts make use of stolen vehicles snatched at gun points which is causing damages to live and properties [3].
The issue of vehicle theft is increasing day by day in our society and despite the efforts of the security agencies, not all the stolen vehicles are always identified, found or recovered. Also, a lot of stolen vehicles used to be identified and recovered in another jurisdiction different from where they were stolen either by police or civil society but due to lack of up-to-date information system where history (i.e. profile) or information of stolen vehicles can be checked or accessed. Those identified or recovered vehicles could not get to their owners on time. In addition to the importance attached to issue of recovered vehicles identity, [13] maintained that Identity Management Systems (IdMS) provides support for security efforts while lowering costs related to managing users and their identities.
According to [7] there is assumption that vehicle theft only occurs in seedy areas, but vehicle theft can also occur anywhere in any area of a town. The researchers also asserted that theft is among the common attitudes exhibited by people where the ownership of property such as vehicle, land, and other physical properties can be altered without the knowledge of the owner.
Recently, the role of mobile phones in the society is largely still unexplored [14]. This was collaborated by [15], that because of the fast improvements in mobile phone technology, it seem that in future mobile phones would replace computers. Also, new innovative vehicle tracking systems have been developed with the capabilities of operating vehicle controls such as locking the door, stopping and starting the vehicle engine, switching fuel tank off, locking of steering and disabling the vehicle brake and clutch. All these can render the thief or unauthorized user useless with very few options while trying to steal or use the vehicle.
Though, vehicle tracking system has always been helpful in this area over the years, but it is less effective at times due to some challenges such as lack of Global System for Mobile Communication (GSM) network coverage, Global Positioning System (GPS) signal distortion and lack of power source to the trackers in the vehicle, which is still occurring. Also, most of these systems lack the functionality of reporting stolen, identified or recovered vehicles which results to delays in searching for vehicle or vehicle not getting to the real owner at the right time when found.
In view of the challenges, this paper proposes a wider spread of functionalities (such as profile on missing, identified and recovered) on the web application and the use of the vehicle battery as a secondary source of power to the vehicle installed mobile phone as described in section III.
-
II. Related Works
[9]designed a vehicle tracking and locking system based on GSM and GPS using GSM Modem SIM300 V7.03 as the technology. This GSM modem was designed such that it can accept SIM card. The paper further stated that the designed system is sets such that it will go into sleeping manner when the vehicle is being driven by the vehicle owner, otherwise, it will be in active status. Also, the system has the capacity such that when SMS message is sent to the controller, it has the features of sending signals to the vehicle engine motor which enable the engine of the vehicle to decreases steadily and then off, thereafter, it will locked all the doors and the engine which has to be restarted again before the door can be opened by entering the password given to the rightful owner of the vehicle.
-
[10] proposed the design and development of Global positioning system and Global system for mobile communications based vehicle tracking in a real time. The designed system gives an alert which is used for reporting any events that happens to the vehicle as it moves. The proposed system also consists of an embedded system with ARM processor which is installed in the vehicle. The system has the ability to send an SMS which consist of latitude and longitude of the vehicle by using AT commands after pressing the emergency key if there is any problem that is associated with the vehicle.
Also, [6] designed a car authentication and accident intimation system using GPS and GSM which is used to save lives. The design of the system has three modules. The first module is used to send the vehicle numbers and the coordinates to a nearby hospital, the second module is used to send message to the vehicle owners whenever the vehicle got crank such that it will notify the status of the vehicle for the owner to take action while the third module is used to notify the nearest service centre for action based on the error signals and coordinates that shows on the dash-board of the vehicle
-
[8] developed a massive vehicle security system which uses embedded and mobile technologies. In this research, two modules was used; the first one is an android module that uses GPS system to get the coordinates of the vehicles which assist the owner to track the vehicle while the other module is used to interact with the vehicle owner by using SMS for receiving and sending messages which uses GSM as a communication channel in helping the owner in tracking the vehicle.
According to [2], the researchers presented a method that gears towards the designing and development an embedded vehicle intrusion and theft control system using GSM and GPS. The system uses a GSM technology whereby a GPS module Holux GR89 was used to locate the coordinates position of the vehicle. In this case switches are used to collect analogue data for any incursion during the readings by the sensors. The sensor used was concealed in a safer place to prevent non vehicle owner or unauthorised person from having access to it. The system was designed in such a way that it uses GSM and GPS for sending signals to the vehicle owner which it will be used to blocked the vehicle after which an SMS will be sent each 30 seconds which will disable the system.
-
[4] designed a vehicle tracking system which consists of fixing of an electronic device in a vehicle which uses specialized software for the tracking of the vehicle by the owner and as such it collect data which is send to through the Radio Frequency (RF) transmitter. The GPS was used so as to be able to send the coordinates and then send it to the microcontroller. The system also enables the vehicle to be viewed through map. The advantage of this designed is that it enables a vehicle to automatically send the location of the vehicle to the owners by an SMS which is sent to the GSM modem if the vehicle is theft, otherwise, if it is the owner that sends a password, the vehicle automatically stopped. This system also has advantage of been simpler and the cost of design is low compare to other system.
Vehicle identification and authentication system was developed by [1] for traffic monitoring. This system prevent unauthorized vehicles from gaining access to restricted areas, such that when a vehicle entered a particular state it need to be verified by using registered number plate which the vehicle owner has already registered earlier. The number is searched from their database to ascertain the genuineness of the vehicle and if actually it belongs to that state or area entrance is guaranteed.
According to [11], traffic accidents are one of the leading causes of fatalities in most of the countries. Since the rate at which vehicle increase so also the rate of road accidents increase, in view of this and to find measure to reduce road accidents and find means of attending to road accident victim, the researcher look at how accident can be notified automatically whenever it occurs by using a sensors which look at the health condition of the passengers and then sent as a video through the GSM to the nearest Police station for urgent response and rescue.
Multi-tracking system for vehicle using GPS and GSM was designed by [12]. It is a real time tracking platform which uses integration of technologies such as GPS and GSM. The GPS device is installed in the vehicle. As the vehicle continuously moves it calculates the co-ordinates with other related information at each position the vehicle reaches and then transmits the information to the GSM server for storage in the database. The system has ability to send SMS to turn the vehicle ignition ON and the information sent to the server that is the coordinates of the vehicle status which helped in viewing the location of the vehicle through map.
According to [5], the researchers used the technology of GPS and Radio Frequency Identification (RFID) for the design and implementation. RFID was used because of its usage in various applications of endeavours such as tools for gate system in railway enquiry to identify the vehicle locations. The aim of the research is to develop a system whereby it uses techniques of GPS and RFID to track a vehicle. It consists of buzzer which was used to locate the vehicle position and also gives the alert notification to the vehicle owner. To improve on the alert system of this design, GSM was used for the communication purpose for sending messages.
-
III. Proposed Methods
The proposed method presents the researchers framework for achieving a more cost effective vehicle theft alert and identification system. The framework proposes the use of the GPS, GSM and the web technologies.
Fig. 1 represents a physical working scenario showing the communication established in actualizing the theft alert functionality. The Global System for Mobile communications (GSM) uses a network carrier by examining mobile phone masts in the vicinity to transmit information from one mobile phone to another. The GSM cell tower (i.e. mast) enables the Short Message Service (SMS) to be sent from one mobile phone to another or from a web application to a mobile phone.
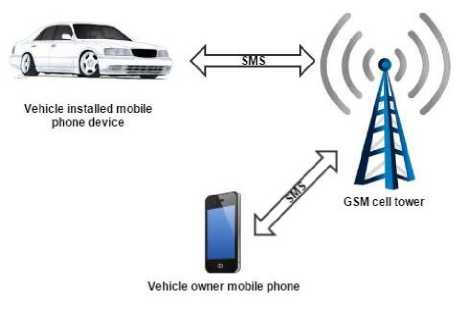
Fig.1. Physical architecture of the theft alert function
Fig. 2 represents a physical working scenario showing the communication established in actualizing the location identification function. The GPS (Global Positioning System) a navigational phenomenon by assemblage of satellites such that it sends signals which makes GPS receiver to find the exact location of an object. The Google map is a web application based GPS receiver used in the implementation of this function. The vehicle owner mobile phone or personal computers (PC) are medium through which the web application GPS receiver is accessed for the location information or data. The GPS receivers identify, decode and process the signal received from the satellites.
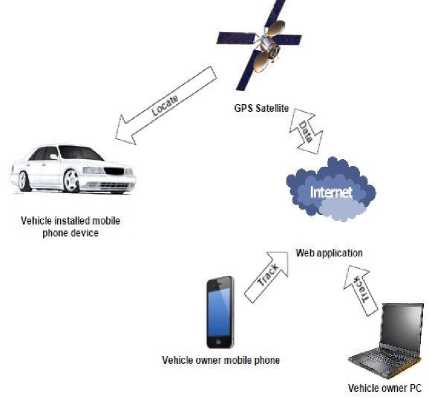
Fig.2. Physical architecture of the location identification function
The block diagram of the system developed is depicted in Fig. 3. It consists of all the components of the developed system as described as follows;
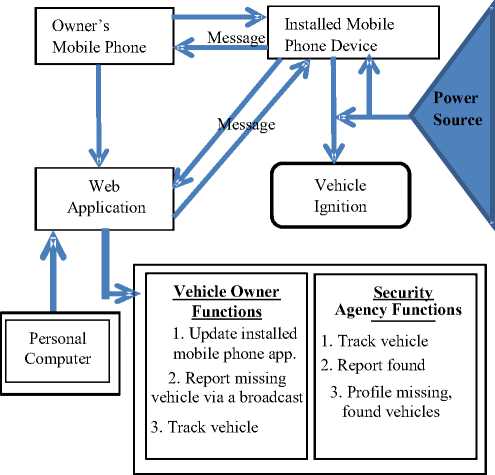
Fig.3. Block diagram of the developed system
-
A. The power source
The primary source of power to the installed mobile phone device is the installed mobile phone device battery. The secondary source of power supply to the installed mobile phone device and the vehicle is the vehicle battery.
-
B. Installed mobile phone device
The installed mobile phone device has a built in application. The application is built in a mobile phone because it is a specialized device that allow Subscriber Identity Module (SIM) card to be used which can respond to mobile subscribers, in this case whenever the vehicle ignition is ON, it sends SMS to the vehicle owner’s mobile phone.
The installed mobile phone device has to be configured by registering the profiles of the vehicle owner which it will use to communicate with the owner’s mobile phone and the web application. The information needed for registration are, name, username, password, vehicle chassis number, VIN, colour, model, email address etc. After all this information is entered, the application saves them on the installed mobile phone device. The installed mobile phone device is then hidden in the vehicle with a connection to the power source for constant charging of the battery.
The application works in two modes, the start and the stop mode. The start mode is to enable the device if not started to be at ready state to send SMS whenever the ignition is ON and for the vehicle owner to communicate with it. The stop mode is to disable the application from responding to any messages either when the ignition is ON or not.
-
C. Owner’s mobile phone
In this component three categories of owners are taken into consideration based on the capabilities of their mobile phones and their personal computers (PC).
Table 1. Showing category of owner’s devices and their functional capabilities .
|
S/N |
Category of owner’s devices |
Capabilities with regards to the application |
Action performed |
|
1 |
Ordinary phones |
SMS based SMS based |
Start and stop installed mobile phone device Track vehicle |
|
2 |
Smart phones |
SMS based Web based Web based |
Start and stop installed mobile phone device Report missing vehicle via a broadcast Track vehicle |
|
3 |
Personal Computer |
Web based |
Report missing vehicle via a broadcast |
|
(PC) |
Web based |
Track vehicle |
As described in the Table 1, the first category are those that uses ordinary mobile phone where they can only use SMS to communicate with the installed mobile phone device, the second category are those that uses smart phone whereby they can perform dual functions of communicating with the installed mobile phone device and the web application. The third category which is the personal computer allows owners to perform the web application functions.
To start the installed mobile phone device, the vehicle owner uses his/her mobile phone to send “START” as SMS to the installed mobile phone device subscriber identity module (SIM) number. This is done to enable the installed mobile phone device respond to vehicle ignition start up. To disable the installed mobile phone device from responding to ignition start up, “STOP” is sent as SMS from vehicle owner’s mobile phone to the installed mobile phone device SIM number.
For the location identification of a missing or stolen vehicle using an ordinary phone, the vehicle owner sends “LOCATION” as an SMS to the installed mobile phone device SIM number. A responding SMS is received on the owner’s mobile phone containing coordinates of the current location of the vehicle.
-
D. The web application
The web application functions are to help the vehicle owner identify and report his/her missing or stolen vehicle by means of tracking and broadcast to social media and the security agency. The web application establishes a connection with the installed mobile phone device hidden in the vehicle at the point of logging in. The vehicle owner logs into the web application using the same registered identification (ID) saved to the installed mobile phone device application at the point of registering the vehicle information. If authenticated, the vehicle owner is able to perform all web application function as described in Fig. 3. The report missing or stolen vehicle through a broadcast to social media and security agency function is an assisted effort towards recovery.
Security agency on their own part on receiving missing or stolen vehicle information could perform all the functions assigned to them as described in Fig. 3 using the web application component that will be deployed to them for appropriate actions towards recovery.
-
IV. System Integration Testing
System integration testing was done in order to ascertain the workability and functionalities of each component that made up the vehicle theft alert and location identification system. This test show how each component responded to an events, identify specific functions of the design if they correspond to action expected. The analysis of the system integration testing is shown in Table 2.
Table 2. Analysis of integration test of the developed vehicle theft alert and location identification system
|
Test case |
Test event |
Description of test |
Expected result |
Result in Percentage |
|
01 |
Owner’s |
Send SMS to |
Sending |
77.19% sent |
|
mobile |
start, stop, |
and |
and received. |
|
|
phone |
report, track |
receiving |
22.81% not |
|
|
send and |
and receive |
SMS |
sent and |
|
|
receive SMS |
tracking coordinates |
message |
received |
|
|
02 |
Installed |
Whenever |
When a |
64.91% |
|
mobile |
SMS is sent to |
“start” |
responded to |
|
|
phone |
the installed |
SMS is |
device SMS. |
|
|
device |
mobile phone |
sent the |
35.09% did |
|
|
respond to SMS |
device, it should respond |
installed mobile phone device should start and when “stop” is sent the installed mobile device should stop |
not respond |
|
|
03 |
Login to |
Authenticate |
Vehicle |
100% vehicle |
|
web applicati on |
vehicle owner |
owner have access to web application functions |
owners were able to login to the web |
|
|
04 |
Tracking |
Track missing vehicle |
Vehicle owner should see a real time vehicle location on smart phones, PCs and location coordinate on ordinary phones. |
85.96% vehicles were tracked on smart phones, PCs and ordinary phones. 14.04% were not |
|
05 |
Report |
Profile of missing and found vehicle |
Send notification of missing or found vehicle |
82.46% report of missing and found vehicle were profiled while 17.54% were not |
Table 2 shows the analysis of the integration test carried out on the Vehicle theft alert and location identification system in order to see how those systems respond to command or messages sent. Test case 01 show that 77.19% were able to send and receive SMS to stop, report, track and receive coordinates of the vehicle, while 22.18% were unable to do so. Test case 02 shows that 64.91% of the SMS sent to the installed mobile phone device responded while 35.09% did not respond.
On Test case 03, all the vehicle owners (100%) that login to the web application were authenticated and granted access to the web application functions. Test case 04 shows that 85.96% of vehicles reported as either missing or stolen were able to be tracked by owners and security agency while 14.04% were not. Test case 05
shows that 82.46% of either missing or stolen or found vehicles were profiled while 17.54% were not.
-
V. Evaluation and Acceptance Analysis of the Developed System
The evaluation of the developed system was done in order to achieve the objectives of this work and to have a thorough understanding of how it will work.
In other to ascertain the effectiveness and capability of the developed system, data were collected from end user (i.e. vehicle owner’s) that used the system. The developed mobile phone device application was installed in sixty two (62) vehicle selected within Abuja, Lagos, Minna and Ilorin to know how effective it is in the effort of ensuring vehicle are prevented from theft by alert and is identified as means towards recovery.
In view of this, some questions were asked. The sampled vehicle owners responses were collected instantly while some were send through email since they are far from where the research was carried out.
Table 3. Results of system evaluation analysis
|
S/N |
Items |
Response (in number and %) Yes/Satisfied |
Response (in number and %) No/Unsatisfied |
|
1 |
Have you heard about vehicle tracking system? |
57 (100%) |
0 (0%) |
|
2 |
What is your perception or level of awareness about vehicle tracking system in identifying locations of vehicles? |
13 (23% ) |
44 (77%) |
|
3 |
Is your vehicles secured with the existing security system? |
17 (30% ) |
40 (70% ) |
|
4 |
Do you have another means of securing vehicles that you have experienced? |
0 (0% ) |
57 (100%) |
|
5 |
Are you aware of any vehicle theft alert and location identification system in ensuring your vehicle safety or recovery when missing or stolen? |
0(0% ) |
57 (100% ) |
|
6 |
Is vehicle tracking system cheap and affordable? |
23 (40%) |
34 (60%) |
|
7 |
What is your opinion on the developed system “vehicle theft alert and location identification system? |
48 (84%) |
9 (16% ) |
Simple percentage method was used for the calculations of the system evaluation analysis as shown in Table 3. Out of the sixty two (62) numbers of questionnaires distributed only fifty seven (57) were filled and returned. The questions asked were:
-
1. Have you heard about vehicle tracking system?
-
2. What is your perception or level of awareness about vehicle tracking systems in identifying locations of vehicles?
-
3. Is your vehicles secured with the existing security system?
-
4. Do you have another means of securing vehicles that you have experienced?
-
5. Are you aware of any vehicle theft alert and location identification system in ensuring your vehicle safety or recovery when missing or stolen?
-
6. Is vehicle tracking system cheap and affordable?
-
7. What is your opinion on the developed system “vehicle theft alert and location identification system”?
Results from the evaluation of the usage of the developed system shows that; 57 (100%) of sampled vehicle owners have heard about vehicle tracking system. 13 (23%) have knowledge and awareness of vehicle tracking system and the recovering methods while 44 (77%) were not aware or have knowledge of it.
Also, 17 (30%) of sampled vehicle owners believed that their vehicle are adequately secured with the existing system of security they are using while 40(70%) were of the opinion that the existing system cannot adequately secured their vehicle; hence, there is need for other security systems. 57 (100%) of vehicle owner’s sampled do not have another system or experienced another means of securing their vehicle apart from the existing one they are using (mostly the basic key and lock).
On a system providing vehicle theft alert and location identification functionalities, 57(100%) have never experienced or seen a system of such. In view of the cost of procuring and installing a tracking system, 23(40%) believe that the cost of buying and installing a tracking system is cheap while 34(60%) believes it is otherwise (i.e. too costly).
Meanwhile, 48(84%) of the sampled vehicle owners are satisfied with the functionalities of the developed vehicle theft alert and location identification system while 9(16%) were unsatisfied.
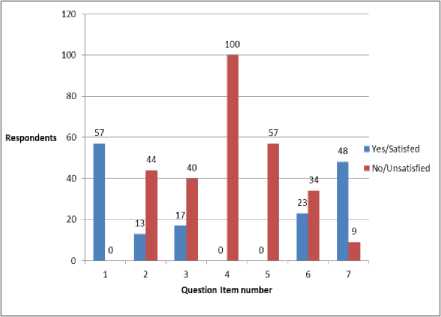
Fig.4. Showing respondents analysis
Fig. 4 represents system evaluation analysis of respondents on the acceptability and effectiveness of the developed vehicle theft alert and location identification system based on satisfaction and dissatisfaction of 57 sampled vehicle owners.
-
VI. Conclusion
This paper works on vehicle theft prevention by means of alert and location identification as effort towards recovering missing, stolen or unauthorized use of vehicles. Several literatures reviewed shows how various technologies (e.g. Sensors, GPRS, GPS, GSM, RFID etc.) have been used in this area over the years. Most of these technologies have been helpful but fails at times due to signals distortion and lack of network coverage. This paper proposed the use of GSM, GPS, and the Web technologies to achieve the implemented system.
The system integration testing was carried out on the implemented system in order to ascertain the workability and functionality of each component that makes up the system. System acceptance evaluation was also carried out to ascertain acceptability and effectiveness of the developed system. Results analysed from both the system integration testing and acceptance evaluation shows the implemented system can be deployed and used as a cheaper means of preventing vehicle theft and as a recovery tool for missing or stolen vehicles.
The implemented system realizes the architectural framework herein proposed. A future research recommends a non- network based communication between applications developed.
Список литературы Vehicle Theft Alert and Location Identification Using GSM, GPS and Web Technologies
- Anusha, T., & Sivakumar, T. (2012). Vehicle Identification and Authentication System. International Journal of Engineering Science and Advanced Technology (IJESAT), 2 (2), 222-226.
- Ashad, M., Hassan, J., Mohtashim, B., Rameez, A. K., Zeeshan, M. Y., Zeeshan R. & Safdar, K. (2012). Vehicle Intrusion and Theft Control System using GSM and GPS: An Advance and Viable Approach. Asian Journal of Engineering, Science and Technology (AJEST), 2 (2), 102- 105.
- Awotunde, J.B., Adewunmi-Olowabi, F.T., Owolabi, A.A. & Akanbi, M.B. (2014). Automated Global System for Mobile-Based Vehicle Inspection Using Short-Code: Case study of Nigeria. Computing, Information Systems, Development Informatics & Allied Research Journal, 5 (3), 45 -50.
- Baburao, K., Raju, V. K., Srinivasa, S. R., Prabu, A.V., Rao, T. A., & Narayana, Y. V. (2013). GSM and GPS Based Vehicle Location and Tracking System. International Journal of Engineering Research and Applications (IJERA), 1(3), 616– 625.
- Kumar, C. R, Vijayalakshmi, B., Ramesh, C., & Pandian, S.C. (2013). Vehicle Theft Alarm and Tracking the Location using RFID and GPS. Journal of Emerging Technology and Advanced Engineering (IJETAE), 3 (12), 525 – 528.
- Monisha, R., Joseph, J. L., & Tharani, B.T. (2014). Car Authentication and Accident Intimation System using GPS and GSM. International Journal of Innovative Research in Computer and Communication Engineering. Special issue 2(1), 219-225. Retrieved on 15th January 2015 from: http://ijircce.com/upload/2014/icgict14/219_832.pdf
- Pranesh, S.I., & Saravana, K. P. (2014). A Massive Vehicle Theft Control System using Embedded and Mobile Technologies. International Journal of Advanced Research (IJAR), 2 (4), 53-59.
- Powale, P. K., & Zade, G.N. (2014). Real Time Car Antitheft System with Accident Detection using AVR Microcontroller: A Review. International Journal of Advance Research in Computer Science and Management Studies (IJARCSMS), 2(1), 509-512.
- Ramani, R., Valarmathy, S., Sutanthira, V. N., Selvaraju, S., Thiruppati, M., & Thangam, R. (2013). Vehicle Tracking and Locking System based on GSM and GPS. International Journal for Intelligent Systems and Application (IJISA), 9, 86-93. DOI: 10.5815/ijisa.2013.09.10
- Shaikh, J.A. I., & Subhangi, A. M. (2014). Advanced Authentication and Security System for Call Centre Employee’s with Live GPS Tracking. International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering (IJAREEIE), 3 (7), 10533 – 10536.
- Sriram, A. & Ramya, P. (2013). Automatic Accident Notification System using GPS and GSM with 3G Technology for Vision Monitoring. International Journal of Emerging Trends in Electricals and Electronics (IJETEE),1(2), 11–13.
- Yuvraj, K., Suraj, G., Shravan, G., & Ajinkya, K. (2014). Multi-Tracking System for Vehicle using GPS and GSM. International Journal of Research in Engineering and Technology (IJRET), 3 (03), 127 – 130.
- Ali, A. & Suleiman, A. (2015). A Security-Trust based Model for Identity Management Systems Adoption. Conference Proceedings Published by Institute of Information System and Research Center ( IISRC ) for 4th ICHCEIMS 2015 & 4th ICCSISCT 2015 – Sydney, Australia. 19(2), 51-61.
- Misbahu, N. K. & Abubakar, A. (2012). Use of Mobile Phones among Informal Microenterprises in Katsina, Nigeria. Paper presented at International Conference on Computing Management ( ICCCSIM, Communication System and Informatics,. Bur Dubai, UAE, 29 – 30 July, 2012. Published by International Journal of Information Technology & Computer Science ( IJITCS )
- Maryam, J. (2014). Learning Vocabulary Via Mobile Phone. Paper presented at International Conference on Computer Supported Education & Information Technology ( ICCSEIT 2014 ), Published by International Journal of Information Technology & Computer Science ( IJITCS). 14(2), 26-29


