Visual Block-based Programming for ICT Training of Prospective Teachers in Morocco
Автор: Ibrahim Ouahbi, Hassane Darhmaoui, Fatiha Kaddari
Журнал: International Journal of Modern Education and Computer Science @ijmecs
Статья в выпуске: 1 vol.14, 2022 года.
Бесплатный доступ
We conducted a training experimentation on computer coding whose aim is to probe ICT skills enhancement of pre-service teachers in Morocco. For that, we have developed and implemented training sessions using a visual programming tool (Scratch) targeting 63 prospective teachers at the Faculty of Educational Sciences (FSE) and the Regional Center for Education and Training Professions (CRMEF) in Nador, Morocco. During these sessions, trainees were introduced to algorithmic thinking where they implemented teaching sequences in their specialty subjects using Scratch. Pre and post surveys were conducted to measure the evolution of the trainees’ perceptions towards the integration of computer coding in the teaching and learning of their specialties. The analysis of the surveys showed the potential of integrating computer coding in the development of learners’ transversal skills. The training revealed different possibilities of exploiting visual block-based programming environments in the teaching and learning process.
ICT, Teacher Training, Computer Science in Morocco, Informatics teaching, block-based programming environments, Scratch
Короткий адрес: https://sciup.org/15018369
IDR: 15018369 | DOI: 10.5815/ijmecs.2022.01.05
Текст научной статьи Visual Block-based Programming for ICT Training of Prospective Teachers in Morocco
Data security has gained momentum in the last few years given the volume of data that gets generated every second. Collaborative security is an abstract concept, where collaboration between different technologies and their compatibility with each other is a significant determinant of their success. Security is often centrally managed and emerging trends such as Artificial Intelligence (AI), Blockchain (BC) and Deep Learning (DL) are used in collaboration to provide high-end security through technology [1]. Implementation of security systems poses challenges related to complexity and compatibility of technologies, sometimes leading to artificial stupidity. Ethical and Legal aspects related to Privacy/Security/Safety of data while implementing Artificial Intelligence (AI), Blockchain (BC) and Deep Learning (DL) are also an increasing cause of concern.
Artificial Neural Networks (ANN) started in the 1950s with the basic programming of machines and it was by the 1990s that the machines had started using explicit programs to evolve their processes and become agile and smart [37]. By the end of the first decade of the 21st Century the concept of Deep Learning had already gained momentum. A collaborative security system recommends the best use of technology such as AI, BC and DL together. Many secure systems offer the security services such as user authentication, use of anti-virus, anti-malware/spyware, intrusion detection etc. The databases used in the organisation and business information can be extracted from these data stores for decision making concerning customer transaction behavior patterns. The organisation is facing increased competition for different reasons, including the user entrance in various applications such as online shopping, banking systems etc. In various online transactions is based on a wide range of offered products and services to the public. As a consequence, the online industry strives to succeed by putting the topic of rapid and changing customer needs on their agenda.
The objectives of corporate security include increased security that leads to gain trust and have better customer response that will improve customer loyalty. The potential areas of application of data-mining techniques are wide. In services, a wide variety of data analysis solutions are provided by the organistaion using computer service personnel and their Software systems implemented such as ERP and MIS depending on the type of data analysis problems encountered. Examples are observed in comprehensive solutions to address the needs of customer/user ever-evolving business scenarios with different frameworks to enable services to critically analyze and evaluate various factors affecting their business transactions, thereby optimizing and enhancing the overall reporting capabilities of their composite application suites.
There are many applications where the authenticity of the user has to be examined thoroughly and it also helps to identify their best customers, implement and measure strategies to retain them, cross-sell and up-sell to them, and make the most effective use of all available assets and channels. Once the correct user login the system, then there are many applications that will help the industries to trap the customer and offer them various services based on its interest and likings such as customer segmentation, profitability, prospecting and acquisition, affinity and cross-sell, retention and attrition, channel utilization, and risk analyses. Customers are distinguished in terms of their profitability. For any business the organisation can build predictive churn models to select the right customer and retain their best customers by identifying symptoms of dissatisfaction and churning. AI can be bitterly used for the same and BC and Deep learning can be looked forward to for the implementation in organization.
The impact of Artificial Intelligence (AI), Blockchain (BC) and Deep Learning (DL) on physical security as shown in Fig.1. Artificial intelligence is the engineering of making astute machines and programs. Artificial intelligence is a superset of many new techniques such as Machine Learning and Deep Learning [2]. Machine learning is defined as the ability of the machine to grasp processes and thus learn without being explicitly programmed for learning. Deep Learning is based on Artificial Neural Networks.
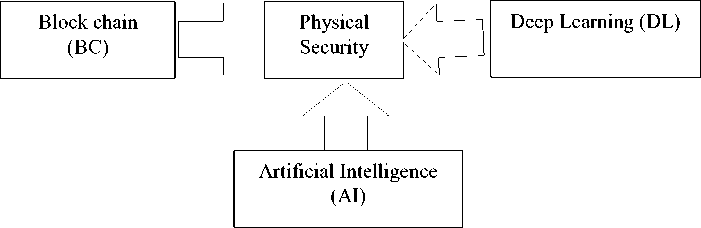
Fig.1. Security Influencer
A new dimension to data security commenced in 2004 in the form of Blockchain. This technology allowed the machines to maintain user audit trails which are one of the most crucial elements of security. The scope of this paper is thus limited to Artificial Intelligence implementation as an element of digital security systems. This disruptive technology together will help in providing secure information systems.
The objectives of the study are
(a) The relationship between blockchain (BC) and deep learning (DL) with Artificial Intelligence (AI)
(b) Mapping of various technologies in collaborative secure information system
(c) To determine the fitness and validation of the model for authentication
2. Background
This research study is organized in the following way. Section 2 produces the background of the work, which contains the related study, introduction to AI and ANN, and its relation to collaborative security systems. The research design and proposed Model are given in Section 3 and 4. The conclusion drawn is given in Section 5.
In 2008, the Blockchain technology was introduced by the name of Bitcoin, by Satoshi Nakamoto.[35] Blockchain is a specific type of database which was initially commenced for Bitcoin. This technology manages data which is received in blocks and assists in tracking transactions in public ledgers between different users. BlockChain technology is used for storing digital information commercially for all applications which use digital assets and virtual records [3, 39]. This information is in encrypted and distributed form which helps to create an extremely secure database.
Technologies like Artificial Neural Networks, work with humans and develop human intelligence. Deep Learning or deep structured learning or hierarchical learning use Machine Learning based methods and are dependent on representations of learning data [4].
Artificial Intelligence can be used in marketing areas where the data and AI create a machine learning system which helps the business in anticipating the customer’s reaction and thus helps the business predict and generate profit [9]. The progression of AI to the next level will enable it to provide big data solutions using analytical tools and techniques. Learning can be of three types supervised, semi-supervised or unsupervised. Machine learning is driven by the learning model of human beings. Blockchain is a trusted technology used for the setting up of digital infrastructure which uses the past data to ascertain patterns of behavior that assists in decision making [7]. Human reactions help the system to create machine patterns which then help in the implementation of Artificial Intelligence in systems.
Humans help in creating neural networks to form an artificial network called Artificial Neural Network. This is based on experiences of the human and also helps them build a machine-learning algorithm [3]. The developers of the algorithm are not comfortable in forecasting but they are able to describe the thinking process that has been followed for decision making. The AI-systems operate on the basis of using complex patterns and complex decision trees which provide the results through a black box and match it with human decision. AI uses historical data to give the input to the Blockchain and then AI and Blockchain together work for better decision making. Computers analyze huge amounts of data with the help of technology but the memory used in the machine has no comparison with the brains of the most intelligent people in the world [2]. The data increases exponentially everyday due to increased modes of collection of data from increased number of sources and also in various structures. The algorithms are then developed based on the data and the instructions provided.
Businesses have started using these technologies directly or indirectly to support the ecosystem of business. Artificial intelligence is considered to be a discipline of computer science which uses and imitates the intelligence of humans. The application of AI can be in perception of visuals and recognition of speech that helps in faster and better decision-making. It also helps in translation and creation of machines that use repetitive tasks called machine intelligence. Machines thus are capable of eventually taking care of all repeated human behaviors that have been used to build a system.
Human beings create computer-based systems using past information and enable computers to study the learning pattern from the data stored to use them. The data stores and structures evolve procedures ensuring the correct and accurate use of the data and information.
A blockchain is an immutable, open, append-only transaction log replicated among a network of nodes [15]. One node is connected to the other and assuring through proof- of- work as it gets acknowledged by other participants. Blockchain technology records every transaction in the database. The blockchain is a chain of blocks where any change in any two entities get recorded in a database. Thus, it contains a confirmable recorded history which offers improved transparency and reliability. All the transactions are available for public view over the network. [13]. If there is any communication or transaction between two parties and either of them does not update their records, the corresponding records will not match and it could be considered as fraud. The data thus needs to be updated from moment to moment in time. The blockchain also maintains privacy and transparency.
With evolution of Blockchain, Enterprise Resource planning (ERP) may be outdated and the new technology will define the new market needs and requirements. Many developed countries have already started using the concept of blockchain in their businesses and organization. Blockchain uses distributed databases and the ledger entries are updated in local databases, given the lack of centralized database servers. The real-time update helps the system to minimize the frauds in the businesses. There will be a great shift for e-commerce companies as they shift to Blockchain technology in future. The blockchain can be easily fitted to any business scenario and filtered to any industry. If businesses do not evolve themselves, they will not be able to sustain the challenges posed by other businesses using advanced technologies.
The renowned concept of Deep Learning is defined as the slicing and dicing of data which is studied to create the patterns for machine learning. ML is associated with Deep Learning which creates neural networks which help to create the AI patterns finally translating to machine learning algorithms used for decision making. These networks of Deep Learning study in depth and detail, anything that is extending in layers [14]. The cloud-based implementation uses blockchain and Deep Learning in great extent.
Cloud technology and ontology-based system for security offers a great benefit to the user i.e cost reduction of infrastructure and maximization of profits for an enterprise [10,11]. These compliances help the enterprises to identify and use the best practice for their processes [10]. Model-based ontology attempts to identify the intrusion detection and countermeasures which are immensely useful for administrator, system management, managers and Information Systems [11]. The implementation of ontology and cloud application will give a new dimension to the study considered for security.
3. Literature Review
The relationships between technologies play an important role in improving understanding and use of these technologies. Based on the research paper studied using this technology it was found that AI has a relationship between Deep Learning, Blockchain. The study based on objective-(a) the relationship is as under:
The information layer AI and Blockchain is used in collaboration of various tools. Blockchain makes information available to all the blocks of various businesses. Deep Learning is machine learning applied with AI, which build neural networks where they make their own decisions. Deep works in the concept of layers which emphasize neural networks.
It is based on gaining knowledge based on the experience and experiment. It is also known as hierarchical learning or deep structural learning as shown in the network diagram as shown in Fig.2.
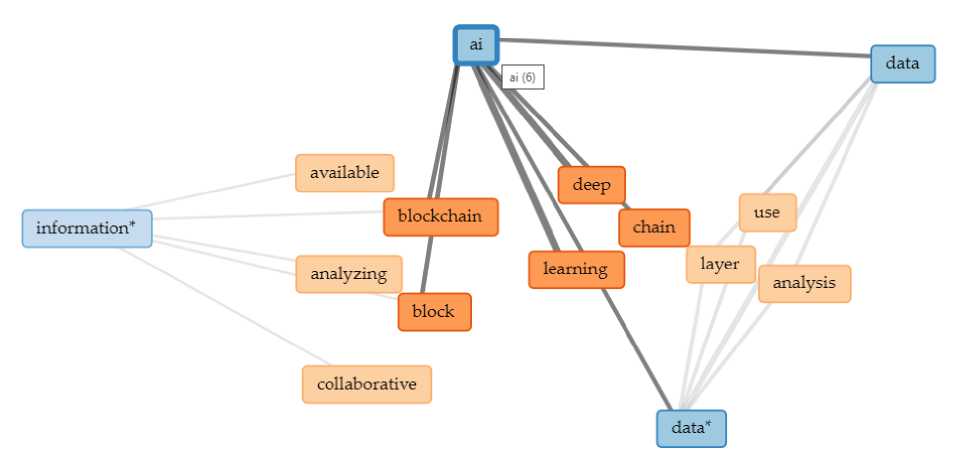
Fig.2. AI relationships with Deep Learning
The relationship between all three has emerged stronger in increasing data security and information security. The collaborations AI, Deep Learning and Blockchain use Content-based Filtering, which matches knowledge of a single user with the knowledge of available items. The above discussed relationships between AI, Deep Learning and Blockchain are thus useful for the enhanced security of the system.
The data is input into the AI system, which uses the transparent layer where non genuine users are not allowed to enter the system. The filtered data input thus flows for Deep Learning, which works on hierarchical study, which further confirms the genuinity of the user. The data transactions verify and acknowledges the same. The blockchain starts using the chains for validating connection and authorization [1]
Learning in depth means the acquisition of knowledge and skills through study and experience that are used in making and building the machine learning patterns. Learning can be in different forms; it can be unsupervised, partially supervised and supervised. The supervised learning can be a subset of Machine Learning (ML) in Artificial Intelligence that is based on defined patterns with labels. These labels create a hierarchy which are useful for creating a hierarchy for the machine pattern which assists in taking a decision.
Collaborative security systems
The use of AI helps in efficiency of data/information of the blockchain technology. All the transactions are verified/authenticated by the miners and AI trains the machine algorithm thereby helping in efficient ways for taking decisions. The decision making is efficient because while using blockchain technology, every piece of information is secure and transparent and recorded over the network. As the data storage and the number of blocks increases every moment the chain becomes heavier. The Blockchain with the use of machine learning algorithms thus optimizes the data storing methods. The integration of various technologies where AI is decentralized and allows parallel computing is Blockchain. Machine learning uses all the computation power to the highest degree and it also analyzes huge amount of data quickly [7].
The different uses of technique in securing business systems have mapped and over the objective- (b) are shown in Table 1.
Table 1. Summary of Related work on used for Collaborative security systems
|
Technology Used |
Description Referenc e |
|
Blockchain and Artificial Intelligence |
AI is used as intelligence tools and decision-making capabilities for machines and [3, 5, 36] emerging blockchain applications, platforms, and protocols specifically targeting the AI area. It can be used as a potential capacity in the fields of international payment, secure data sharing and marketing, and supply chain management. Artificial Intelligence is used to develop the creation of machines capable of performing tasks that need intelligence. Blockchain, IoT and Artificial Intelligence can influence future cloud computing systems and provide security as well. |
|
Artificial Intelligence, Deep Learning, Internet of Things, cloud computing, and blockchain, in the new generation of big data and Industry 4.0. |
Used for multifaceted systematic analysis of AI in practical applications. Artificial neural networks (ANN) predict new customer behavior from previously observed customer behavior after executing the process of learning from existing data. An evaluation process determined that it performed. |
[6,37] |
|
Big data, Artificial Intelligence and IOT |
Block IoT Intelligence architecture on device, fog, edge and cloud intelligence use parameters such as accuracy, latency, security and privacy, computational complexity and energy cost in assessing IoT applications. |
[4] |
|
Artificial Intelligence, Deep Learning IOT and Blockchain |
Blockchain and AI technologies help form a sustainable smart society. Blockchain can be used as security enhancement solutions, blockchain-AI based intelligent, transportation systems are an example. An integrated solution using the edge computing frameworks to build intelligent edge for dynamic, adaptive edge maintenance and management. These techniques are used in applications to solve security and privacy issues. |
[8,2,7] |
Logistics model and its interpretation
The past papers on logistics and its interpretation in various models [26] show that there are many industries where logistics regression is used as a predictive model, such as real estate, banking, insurance industry, retail industry etc. Please refer to Table 2.
Table 2. Literature Review
|
Model Discussed |
Dataset/Description |
Reference |
|
Regression model was used to find out the relationships |
Financial ratios and corporate governance |
[27] |
|
Empirical paper on financial ratios |
Financial ratios of three companies in UK |
[28] |
|
Implementation of Linear Regression Model and was used for the predictive model. Explanatory variables (EV) were analyzed. Regression coefficient was observed |
Residential energy and Forest dataset |
[29, 30] |
|
Regression and multiple regression models were applied. The spatial predictive modeling was made and Multivariate analysis. |
Spices dataset, Sugar and acid content from Citrus fruits |
[31, 32] |
|
k-Nearest Neighbor performance in Simulated using Annealing, a metaheuristic search algorithm |
Realtime dataset used |
[37] |
4. Result Analysis and Discussion
The open source Voyant tool has been used for visual analytics for the purpose of research. A network diagram was created for the analysis and it was found that the data and information bifurcate the use of technology. Both AI and Deep Learning use historical data and store it for future use in analysis and reporting purposes.
Deep Learning is also called deep structured learning or hierarchical learning used for creation of machine learning patterns. The objective of this paper is to validate the user based on the entries already available in the table and find out the correct entries through a prediction model creation with its validation. The objective estimate of the probability of user validation from user log enables data to validate the correct user with greater precision. The best measure of the predictive power of an equation is destination of packet, size of packet and the source of the packets. A simple equation is formed to identify the relationship with the valid user. The training dataset was thus created and the logistic regression model was applied.
Logistics regression is used and can be applied to a big dataset to create a model for authentication of users from a security point of view. This can be used to identify the valid users. As a new user enters the system, it identifies the parameters whether the class of the user is valid or not. This then helps the system to be alert and if there is a suspicious entry done by the user in the system, it immediately blocks the entry and does not allow the user to do further transactions. This will be considered as an application of AI as the prediction model based on the history data and thus helps as an application to enhance the security of the system.
Data Model Used
AI implements the use of attack models and security protocols for the implementation of security. It tries to automate the system and uses the directed graphs for the implementation of the model.[21].
Captcha has been introduced as an automatic test to bypass human and solution of AI problems. Captcha may be used in many applications and it can enhance the security. Captcha based voice not picture recognition helps to identify the correct user [19] It is also considered to be the best fit model currently used [20].
A past research article has discussed various types of logit options available for modelling [21]. This has helped to explore the different options which have been examined and used for the category wise predictive modelling. There are many researchers that have used these types of regression for their study. The generalized linear model (GLM) is a more flexible generalization of ordinary linear regression that allows for response variables used for training dataset.
They have used commands such as GLM, it has been used with class, Analysis Of Variance(anova) etc. They further describe the details about the model and also the model parameters to be studied for the interpretation [22, 23]. Poisson regression data has also been applied to the real estate data and the array of applications from the social to the physical sciences has been examined and analyzed [24].
The research examines the risk factors of victims of cybercrime and the analysis is done at the dataset that shows that a logistic GLM, where the conventional methods using the Wald test have been applied, the deviance of change can be examined [25]
The model is proposed using the data and information layer. The Information layer uses summarization, analysis and collaboration of data using blockchain and AI. The data layer enables Deep Learning and AI, which makes a very secure use of data and information in different layers. This mitigates the risk and increases the trust and security in the system. The privacy/ personal data threats are taken care of.
The model discussed in this paper analyzes a major concern of protection and the storage of data. The collaborative system designed is based on the three futuristic techniques i.e AI, Blockchain and Deep Learning. We have divided our model in five stages- Stage 1: AI; Stage 2: Deep Learning; Stage 3: Blockchain; Stage 4: Clustering; and Stage 5: Mainframe. Stages 1 to 3 work as the Data layer and stage 4 and stage 5 work as the information layer.
Stage 1, 2 and 3 use and analyze the data and work confidently in AI and Deep Learning and Block chain. The input data is from different sources and is in the form of structured and unstructured data used for the item of interest. The data can be used with AI for creating patterns, which flows into the data layer. AI approach is used to check for any robotic interference and the filters are analyzed for making of a pattern.
The stage AI gathers the data and passes on to Deep Learning, which analyzes the data to identify filters for the consideration of different categories. Genuine data is thus passed on for Deep Learning. This stage filters the pattern as per the requirement and based on the filters the pattern is designed. The AI further connects to the block chain where the information is required for analysis, summarizing and collaboration of the information.
The remaining data is passed to stage 3 for block chain formation where blocks of users are created which help to accommodate all data without revealing an individual's identity as shown in Fig.3. In this whole model the security and privacy of data is ensured.
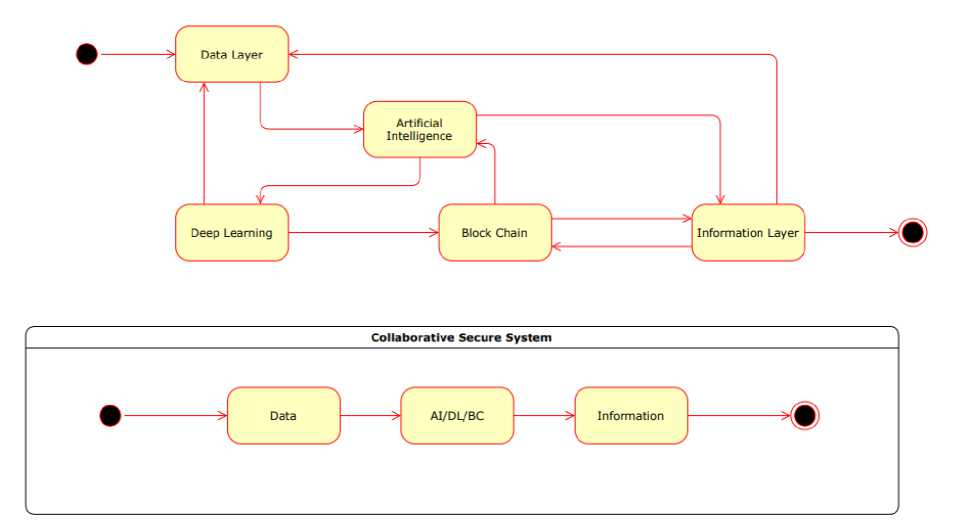
Fig.3. Proposed Security Model
-
4.1 Logistic Regression Model
-
4.2 Data collection
In the collaborative secure system this paper discusses the AI, DL and BC. In the present study, this paper considers only AI implementation for a collaborative secure system. The DL and BC for collaborative secure systems will be considered in future. This research paper only discusses the implementation of AI to the system to make it secure. In the present logistic model, study, dependent or response variable is categorical. Hence, a logistic panel is suitable to predict the authenticity of the user. In a logistic model, the response variable is identified as integer’s values. It means a logistic model contains qualitative dependent variables. When the response variable (y) is quantitative, its objective is to estimate expected or mean value but if it qualitative in nature, its objective is to find the probability of something happening. Therefore, it is known as probability models.
The Logistic Regression defines a regression model where the response variable has a categorical value such as True/False or 0/1 i.e., dependent variable. The measure of the probability of a response which is binary i.e. normal, suspicious and unknown under the variable “class”. The probability of a binary response actually measures the value of the response variable defined in a mathematical equation involving the predictor variables. The general mathematical equation for logistic regression is – y = 1/(1+e^-(a+b1x1+b2x2+b3x3+...)) (1)
Where the use of the parameters is as under. The response variable y = 1/(1+e^-(a+b1x1+b2x2+b3x3+...))
Where the use of the parameters is as under. The response variable i.e “y”, predictor variable i.e x and the coefficients which are numeric constants i.e. a and b. The function used to create the regression model in using the R statistical software using the glm() function. In the logistics panel the p value plays an vital role in estimation and creation of the model [33,34].i.e “y”, predictor variable i.e x and the coefficients which are numeric constants i.e. a and b. The function used to create the regression model in using the R statistical software using the glm() function. In the logistics panel the p value plays a vital role in estimation and creation of the model [33,34].
The basic objective of this research paper is to create the corrected model for the determination of a valid user. This will help in establishment of the security systems in the implementation of AI, as it will be creating a model for predicting the validity of users. The dataset for the experiment was downloaded from the kaggle data warehouse website. The data columns are Date.first.seen, Duration, Proto, Src. IP.Addr, Src.Pt , Dst.IP. Addr,Dst.Pt, Packets, Bytes, Flows, Flags, Tos, class. The columns which contain a numeric value want to be a part of creating the model and it was found that the Duration, Dst.Pt, Packets, Src.Pt and class are used. Also, the columns which are not useful can be removed from the dataset. The csv file is imported in a dataset and the dataset named user_log was created.
The column details are the sample data of all the columns are as under:
|
'data.frame': 172838 obs. of 16 variables: |
|
|
$ Date.first.seen : Factor w/ 29659 levels "00:00.0","00:00.1",..: 21572 |
|
|
$ Duration |
: num 81413 81413 81505 81505 82101 ... |
|
$ Proto |
: Factor w/ 4 levels "GRE ","ICMP ",..: 3 3 3 3 3 3 3 3 3 |
|
$ Src.IP.Addr |
: Factor w/ 10539 levels "10000_214","10001_101",..: |
|
$ Src.Pt |
: int 8082 56978 8082 56979 8082 51649 8082 37039 |
|
$ Dst.IP.Addr |
: Factor w/ 10478 levels "10000_214","10001_101",..: |
|
$ Dst.Pt |
: num 56978 8082 56979 8082 51649 ... |
|
$ Packets |
: int 3057 4748 8639 12024 11012 14186 9974 16476 |
|
$ Bytes |
: Factor w/ 4695 levels " 1.2 M"," 1.4 M",..: 4 6 25 29 |
|
$ Flows |
: int 1 1 1 1 1 1 1 1 1 1 ... |
|
$ Flags |
: Factor w/ 25 levels " 0x53"," 0xc2",..: 21 21 21 21 22 |
|
$ Tos : |
int 0 0 0 0 0 0 0 0 0 0 ... |
|
$ class : |
Factor w/ 3 levels "normal","suspicious",..: 1 1 1 1 1 1 1 |
|
$ attackType |
: Factor w/ 1 level "---": 1 1 1 1 1 1 1 1 1 1 ... |
|
$ attackID |
: Factor w/ 1 level "---": 1 1 1 1 1 1 1 1 1 1 ... |
|
$ attackDescription: Factor w/ 1 level "---": 1 1 1 1 1 1 1 1 1 1 ... |
|
Source: Authors own calculation
The columns which are of not use can be removed from the dataset the command run to remove the column are
-
4.3 Results of Descriptive Statistics
The descriptive /summary statistics are as under refer to Table 3.
Table 3. descriptive /summary statistics
|
Duration |
Dst.Pt |
Packets |
Src.Pt |
class |
|
|
Min |
0.0 |
0 |
1 |
0 |
normal: 49606 |
|
1 Qrt |
0.1 |
23 |
5 |
23 |
supcious:107344 |
|
Median |
5.9 |
8000 |
7 |
8000 |
Unknown:15888 |
|
Mean |
136.3 |
23310 |
13.81 |
22445 |
|
|
3 Qrt |
16.8 |
49002 |
17 |
49145 |
|
|
Max |
519611.2 |
65535 |
34136 |
65535 |
Source: Authors own calculation
Data slicing done for creating the training data and it helps in dividing the records in the ratio of 60% and 40%, where the 60% records are used for the training the model and 40% is used for applying the test and compare with the actual values used for calculating the success rate of model defined.
The command used for creating the logistics regression model is as under:
-
> myModel <- glm(class~ Dst.Pt+Packets+Src.Pt,data=train,family = 'binomial')
-
> summary(myModel)
Results of the logistics Model refer to Table 4. is as under
Table 4. Results of Logit Model
|
Coefficients |
Estimate |
Std.Error |
z value |
Pr(>|z|) |
Sig |
|
(Intercept) |
1.595e+01 |
1.217e-01 |
0.7430 |
131.088 |
*** |
|
Dst.Pt |
2.028e-06 |
-130.927 |
-2.656e-04 |
< 2e-16 |
*** |
|
Packets |
-2.749e-04 |
8.831e-05 |
-3.113 |
0.00185 |
** |
|
Src.Pt |
-2.654e-04 |
2.027e-06 |
-130.936 |
< 2e-16 |
*** |
|
Signif. codes: 0 ‘***’ 0.001 ‘**’ 0.01 ‘*’ 0.05 ‘.’ 0.1 ‘ ’ 1 (Dispersion parameter for binomial family taken to be 1) Null deviance: 124559 on 103763 degrees of freedom Residual deviance: 53510 on 103760 degrees of freedom AIC: 53518 Number of Fisher Scoring iterations: 8 |
|||||
Source: Authors own calculation
The results suggest that the greater number of stars defines the significance. It means that Dst_Pt, Src_Pt give the more significant contribution in measure. Also, the z value is less than .05 as depicts that they are more significant in the contribution of model reliability. The balance model is more reliable.
Selection of Variables The best measure of the predictive power of an equation is the Destination of the Packet, size of packet and the source of the packets. A simple equation is formed to identify the relationship with the valid user. The training a dataset was thus created and the logistic regression model was applied with these variables. The dataset was chosen specifically for the purpose of defining a model to determine the authenticity of the user. The column that specifies the same is class. This dataset defines whether the class is normal, suspicious or unknown. There are 16 variables and found that as per the user, suspicious activity can be in terms of following: source of packet- their origin, packet- size of data used and destination of packet-their destination. These variables are considered for the model for testing the activity of the user. This will analyse whether the user is normal or not.
The identification of the variables for the model are the dependent variable whether the class will be normal or suspicious or unknown. Also, all the numerical variable with wide ranges of values is considered as the independent variables for the model. They are Src.Pt, Dst.Pt and the Packet size. That is the sources and destination of packets and also the size of packets.
G2 = -2 logL is used to calculate the Residual deviance, which is the difference in a maximal model. These are the separate parameters for each cell in the model and the built model. The Changes in the deviance (the difference in the quantity -2 logL) for two models will be calculated by chisquare. χ 2. The distribution with degree of freedom value is equal to the change in the number of estimated parameters. Thus the difference in deviances can be tested against the χ 2 distribution for significance.
The predictor used for testing the model is the use of test and train data which is useful for the testing the model using training dataset
-
# testing of model with the test dataset
res <- predict(myModel,test,type="response")
res
-
# testing of model with the train dataset
res <- predict(myModel,train,type="response")
res
The use of actual and predicted value the dataset is created with response more than 50%
>confmatrix <- table(Actual_value=train$class, Predicted_value = res > 0.5)
-
> confmatrix
Predicted_value
Actual_value
FALSE
TRUE
normal
23639
6228
suspicious
5458
58895
unknown
719
8825
Source: Authors own calculation
The accuracy has been calculated as 79%. This model is used to check the user authentication.
-
> (confmatrix[[1,1]]+confmatrix[[2,2]])/sum(confmatrix)
[1] 0.7954011
The predictive accuracy is 79.5%, which is considered for the fitness of the model and further validates the model for its further use. As the value is 79.5%, there are more hidden correlations in this model needed to make it 98% accurate. But still the normal user can be judged based on the selected parameters used in the model. There may be hidden correlations which have not been considered to be present in the model. The validity of the model can be determined by the use of predictive accuracy. As the accuracy is 79.5% it means the model is accurate and also validate.

Fig. 4. Word Cloud
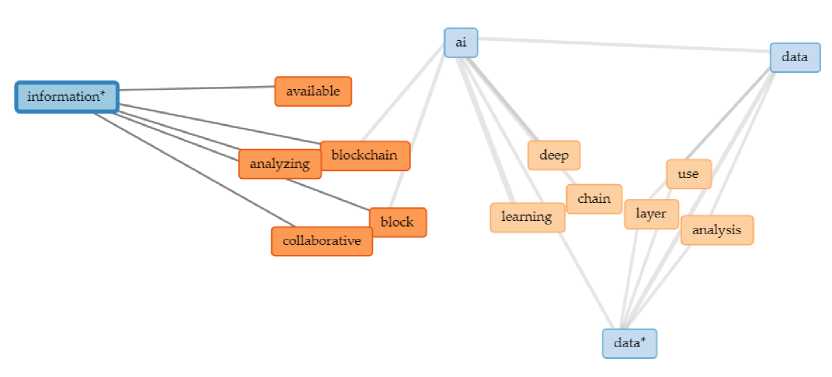
Fig.5. Information based connections
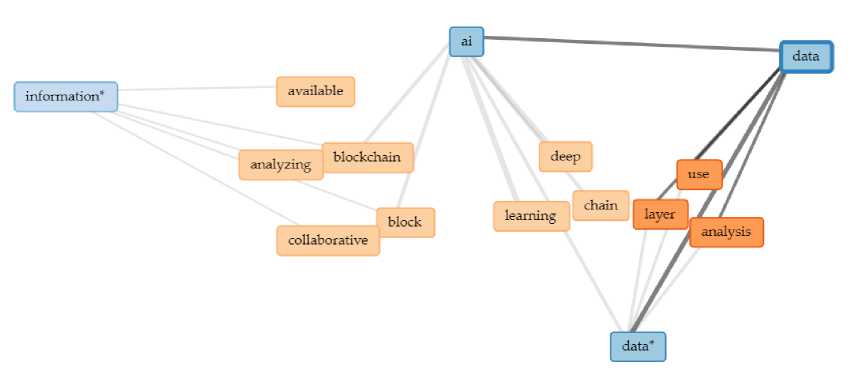
Fig.6. Data based connections
5. Conclusion and Future Recommendation
AI for security was implemented as the user authentication for security systems. The training data was tested and accuracy was calculated as 79%. It used a training set in the model, to check the feasibility of study. While conducting the experimental study, an AI approach was used as the first level of security wherein only the relevant and genuine data was passed to the next level, i.e., Deep Learning for hierarchical study.
This study was limited to AI used in the transactions of user log and was not applied to Deep Learning & Blockchain. The data collected was collected from open source for testing purposes. We recommend, the dataset to be collected physically real-time transaction for purpose will provide a solution of implementation, setting up model programs; and design of Enterprise into controllable portions. All business units or departments of the organization should be integrated in a small, adjustable method. Thus, for an effective business solution, should consider blockchain technology and Deep Learning.
With both AI and blockchain technology together in one place, data usage could be controlled. With all the emerging technologies used in combination they are able to provide a different edge to the business processes. This research has also redefined the parameters of data security and attempts to provide a solution for the same for the future. The extension of model has been discussed as follows:
The dataset has other parameters in the security system which have not been explored and this will define the future scope for research in this area. Other techniques to enhance security of data and information can be also identified and analyzed further for future studies. The world cloud depicts the use of bigger words as compared to small words. The most occurrences of the words discussed in the Fig.4. are as follows:
Data, chain, Deep Learning, Block chain, AI, information etc
Based on the popularity of different words in the document. The use of the words and the network diagram will help us to create a flow chart. This proposed model will finally help in the implementation of the project as shown in figure defining in Fig.5. and Fig.6. Fig.5. discusses the involvement of information in AI, Block chain and Deep Learning. Fig.6. discusses the involvement of data in AI, Blockchain and Deep Learning.
-
Fig.5. discusses that the information is dependent on blockchain directly and connected to AI indirectly through blockchain and Further AI is linked to Deep Learning and is directly linked to the data.
-
Fig.6. discusses the data connection which is directly connected to AI and Deep Learning. Further the AI is connected to blockchain and finally linked to the information.
All the three technologies are important but it has been seen that these originate from AI. Thus, AI can be broadly used for the user authentication for the check whether the user is valid or not. This will be at the very first stage where one can stop the user from entering the system making it a very secure system. The tracking of the data filled by every user can be checked and validated. For the experiment, the sample dataset was considered and logistic regression was applied.
Список литературы Visual Block-based Programming for ICT Training of Prospective Teachers in Morocco
- Hassan, M. M., & Mirza, T. (2020). The Digital Literacy in Teachers of the Schools of Rajouri (J&K)-India: Teachers Perspective, International Journal of Education and Management Engineering (IJEME), Vol.11, No.1, pp. 28-40, 2021. DOI: 10.5815/ijeme.2021.01.04.
- Al-Samawi, Y. (2019). Digital Firm: Requirements, Recommendations, and Evaluation the Success in Digitization, International Journal of Information Technology and Computer Science (IJITCS), Vol.11, No.1, pp.39-49, 2019. DOI: 10.5815/ijitcs.2019.01.05.
- Arcos, G., Aguirre, G. L., Hidalgo, B., Rosero, R. H., & Gómez, O. S. (2018). Current Trends of Teaching Computer Programming in Undergraduate CS Programs: A Survey from Ecuadorian Universities. KnE Engineering, 253-275.
- Kanemune, S., Shirai, S., & Tani, S. (2017). Informatics and Programming Education at Primary and Secondary Schools in Japan, Olympiads in Informatics, Vol. 11, 143–150.
- Webb, M., Davis, N., Bell, T., Katz, Y. J., Reynolds, N., Chambers, D. P., & Sysło, M. M. (2017). Computer science in K-12 school curricula of the 2lst century: Why, what and when?. Education and Information Technologies, 22(2), 445-468
- Ouahbi, I., Darhmaoui, H., Kaddari, F., Bemmouna, A., Elachqar, A., & Lahmine, S. (2015). Un aperçu sur l’enseignement de l’informatique au Maroc: Nécessité d’une réforme des curricula An overview of teaching informatics in Morocco: The need for a curriculum reform. Frantice.net, (11), 51-66.
- Ouahbi, I., Darhmaoui, H., Kaddari, F., & Bemmouna, A. (2019). Computer Science Program in Moroccan Secondary Schools: Curricula Analysis", International Journal of Modern Education and Computer Science (IJMECS), Vol.11, No.3, pp. 10-15,2019. DOI:10.5815/ijmecs.2019.03.02.
- Dogan, A. (2020). Algorithmic Thinking in Primary Education. International Journal of Progressive Education, 16(4), 286-301.
- Duch, P., & Jaworski, T. (2018). Enriching Computer Science Programming Classes with Arduino Game Development. In 2018 11th International Conference on Human System Interaction (HSI) (pp. 148-154). IEEE.
- Ouahbi, I., Kaddari, F., Darhmaoui, H., & Elachqar, A. (2018). L’intégration des serious games dans les cours d’introduction de l’algorithmique et de la programmation : Integration of serious games in teaching an introductory course on algorithmic and programming. frantice.net, 14(1).
- Adhikari, K. (2019). Exploring girls' perception on Computing careers via educational quiz-application (Master's thesis, NTNU).
- Maloney, J., Resnick, M., Rusk, N., Silverman, B., & Eastmond, E. (2010). The scratch programming language and environment. ACM Transactions on Computing Education (TOCE), 10(4), 16.
- MEN (2005a). Ministère d’Education Nationale, Programme et instructions officielles pour l’enseignement de l’informatique aux troncs communs.
- MEN. (2020). Ministère d’Education Nationale, Programme de l’enseignement au cycle primaire.
- Bemmouna, A., Chetouani, A., & El yacoubi, T. (2013). L’informatique pas à pas. Collection de l’enseignement de l’informatique au primaire (du 3ème au 6ème). Rabat : Dar Nachr Almaarifa.
- MEN. (2009). Ministère d’Education Nationale, Programme et instructions officielles pour l’enseignement secondaire collégial.
- MEN. (2005b). Ministère d’Education Nationale, Programme et instructions officielles pour l’enseignement en 1ère année du baccalauréat sciences économiques et sciences de gestion comptable.
- MEN. (2007). Ministère d’Education Nationale, Programme et instructions officielles pour l’enseignement en 2ème année du baccalauréat sciences économiques et sciences de gestion comptable.
- MEN. (2012). Ministère d’Education Nationale, Guide des modules transversaux aux CRMEF, unité centrale de la formation des cadres.
- Earp, J., Dagnino, F., Kiili, K., Kiili, C., Tuomi, P., & Whitton, N. (2013). Learner Collaboration in Digital Game Making: An Emerging Trend. Learning & Teaching with Media & Technology, 439.
- Daher, W., Baya’a, N., Jaber, O., & Awawdeh Shahbari, J. (2020). A Trajectory for Advancing the Meta-Cognitive Solving of Mathematics-Based Programming Problems with Scratch. Symmetry, 12(10), 1627.
- Papadakis, S., & Kalogiannakis, M. (2019). Evaluating a course for teaching introductory programming with Scratch to pre-service kindergarten teachers. International Journal of Technology Enhanced Learning, 11(3), 231-246.
- Romero, M., & Barma, S. (2015). Teaching pre-service teachers to integrate Serious Games in the primary education curriculum. International Journal of Serious Games, 2(1).
- Kim, H., Choi, H., Han, J., & So, H. J. (2012). Enhancing teachers' ICT capacity for the 21st century learning environment: Three cases of teacher education in Korea. Australasian Journal of Educational Technology, 28(6), 965-982.
- Baron, G. L., & Voulgre, E. (2013). Initier à la programmation des étudiants de master de sciences de l'éducation? Un compte rendu d'expérience. In Sciences et technologies de l'information et de la communication (STIC) en milieu éducatif.
- Agbo, F. J., Oyelere, S. S., Suhonen, J., & Adewumi, S. (2019). A systematic review of computational thinking approach for programming education in higher education institutions. In Proceedings of the 19th Koli Calling International Conference on Computing Education Research (pp. 1-10).
- Almeida, R., & Pessoa, T. (2017). Scratch software in higher education: pedagogical experience in educational science. International Symposium on Computers in Education (SIIE) (pp. 1-5). IEEE.
- Butler, D., & Leahy, M. (2021). Developing preservice teachers' understanding of computational thinking: A constructionist approach. British Journal of Educational Technology.
- Ouahbi, I., Kaddari, F., Darhmaoui, H., Elachqar, A., & Lahmine, S. (2015b). Learning basic programming concepts by creating games with scratch programming environment. Procedia-Social and Behavioral Sciences, 191, 1479-1482.
- Bandura, A. (1977). Self-efficacy: toward a unifying theory of behavioral change. Psychological review, 84(2), 191.
- Ouahbi, I., Darhmaoui, H., Kaddari, F., Elachqar, A., & Lahmine, S. (2016). Pre-service Teachers' Perceptions and Awareness toward Serious Games in the Classroom-Case of Morocco. In 2016 13th International Conference on Computer Graphics, Imaging and Visualization (CGiV) (pp. 431-436). IEEE.


