Voynich manuscript - Analysis of the codification algorithm with the encryption methods known in the medieval time and results of the marginalies that were not encrypted
Автор: Alisa Gladyševa
Журнал: Revista Científica Arbitrada de la Fundación MenteClara @fundacionmenteclara
Статья в выпуске: 1, Vol. 5, 2020 года.
Бесплатный доступ
In the present study I describe and analyze two objectives, the first is about opposition and equivalence of the Voynich manuscript coding algorithm with the known in medieval period methods of ciphering. According to the results of my innovative research of the Voynich manuscript was written in medieval Galician (Galician-Portuguese). Its coding algorithm was influenced by the substitution cipher of using a polyalphabetic cipher for the most part of its text, as well as it was definitely influenced by transposition cipher for double ciphered alchemical text. However, it should be mentioned that there are significant differences between the codes that were used in the medieval period and the encoded algorithm of the Voynich manuscript. For the reason that made deciphering more complicated over the centuries, substitution encryption of a polyalphabetic cipher was used partly and simultaneusly with monoalphabetic cipher in addition to uncoded text at all. Therefore the main thing to take into consideration is that the second objective of the most interest in this particular article are parts of the Voynich manuscript texts – marginalies– that were not encrypted at all and their reading.
Voynich Manuscript, Marginalia, Medieval Galician, Calendar
Короткий адрес: https://sciup.org/170163680
IDR: 170163680 | DOI: 10.32351/rca.v5.128
Фрагмент статьи Voynich manuscript - Analysis of the codification algorithm with the encryption methods known in the medieval time and results of the marginalies that were not encrypted
1. Introduction
In medieval times it was very common to decipher how it was used since ancient times. The most important classical encryption techniques are transposition ciphers which rearrange the order of characters in a message therefore the letters are changed as well as substitution cipher where plaintext are replaced with cipher text. The word 'number' comes from the Hebrew word ' לִסְפּוֹר' as well as 'צוֹפֶן' code, cipher. Cryptographic examples can be found in some Hebrew biblical texts for e.g. 'Tehillim' (Gladyseva, 2019), furthermore as simple monoalphabetic substitution 'Atbash' cipher (500 BC). The Greek historian Polybius invented "Polybius square" cipher, where the letters of the alphabet were arranged left to right, top to bottom in a 5 x 5 squares, but similar squares were already had been used by Jewish scholars (Polybius, [146 a.C]1922).
Different kind of ciphering was used in occult hermetic texts of ancient Greece with cryptographic system based on homophonic substitution, understanding the meaning (Gladyseva, 2019) metaphors with another connotation of the text. The method currently known as César supposedly used by Julio César and known as César encryption or offset encryption.
However, these methods were used in part in the Voynich manuscript, with the method of encryption of different algorithms that was unknown in the medieval period in other manuscripts. Therefore, for more than half a thousand years no one could decipher it.
2. The methods of decoding in the medieval period and their connections with the decryption methods of the investigation of the Voynich manuscript
In the medieval period of Europe encryption was using not only due increased diplomatic activity for convey confidential information, but to conceal information especially in alchemical treatises where symbols were used instead of letters often. The research achievements of the Voynich manuscript indicate that the connotation of its text was influenced by medieval alchemical philosophy (Gladyseva, 2019).
The most important book that describing the use of cryptography in alchemy is the 13th century Roger Bacon's work 'The Message of the Monk Roger Bacon on the secret actions of art and nature and the Nobility of Magic' in Latin 'Epistola Fratris Rog. Baconis, de secretis operibus artis et naturae et null magitate' (1270), which describes the use of 7 methods for hiding a text. According to Roger Bacon: ' A man is a crazy who writes a secret in any other way than one which will conceal it from the vulgar.>'
The most interesting result in the encryption code of the Voynich manuscript that made decryption more complicated over the centuries was the use of polyalphabetic encryption that was used partially and simultaneously with monoalphabetic encryption (Gladyseva, 2019).
But according to the history of encryption, polyalphabetic encryption was invented by Leon Batista Alberti in 1467, who identified the idea of using polyalphabetic encryption: multiple encrypted alphabets with change in a few words, which is why he was called the 'father of Western cryptology'. The present study of the text of the Voynich manuscript and the translated information confirmed the current analysis that it was written after 1467 (Gladyseva, 2019).
The polyalphabetic system, which uses several monoalphabetic figures periodically, alternating between each of the three words. Depending on the position of the internal disk, 24 possible variations are defined. One of the disks of the different alphabet was used to represent the decryption method, and the other was from the alphabet with the numbers 1, 2, 3 and 4 (Hernández Gómez, 2010). But it is important to underline that the polyalphabetic system in Voynich manuscript was used partly (Gladyseva, 2019).
In analysing of the encryption methods that were used in the medieval period and their opposition and equivalence with the coding algorithm of the Voynich manuscript was very useful the first treatise of the medieval period, dedicated exclusively to cryptanalysis, the work of Francesco (Cicco) Simonetta (1410-1480), secretary of Sforza (Simonetta, 1474).
He established thirteen rules for decoding of replacement ciphers, which contain word delimiters. On the basis of his manuscript, the most important:
'… is to find out whether the document is written in Latin or in a local language, and this can be established as follows: find out if the words in this document have only five different endings, less or more …> if there are only five or less, you are justified in concluding that it is in the vernacular; if they are more than five you can assume your document to be in Latin.>' (Simonetta, 1474)
The first Voynich manuscript’s preluminal cryptanalysis of my research yielded results that it was not written in Latin, but in some language or its dialect. This method of decryption was possible only after deciphering some words and the names of the first flowers. (Gladyseva, 2019)
Important notes by Francesco (Cicco) Simonetta on words that consist of one, two or three characters that are repeated more frequently in vernacular than in Latin, where the words represented by a single character are four: 'the prepositions 'e' and 'a', the vocative adverb 'o' and the imperative verb 'i', but these one-letter words are rarely used, except the preposition 'a' (Simonetta, 1474).
Simonetta's thirteenth rule was about double letters that were easy to decipher and was well known in medieval times, therefore, in the Voynich manuscript, double letters were generally omitted (Gladyseva, 2019).
Simonetta's sixteenth rule included a known method of coding when the texts were partly in vernacular and partly in Latin, according to my research, this method was infrequently used in the Voynich manuscript, as well as the character method of text that had no meaning especially in the words of the alchemical lexicon (Gladyseva, 2019).
But the most encrypted text according to Simonetta had been encrypted with two completely different cipher alphabets, which in varying degrees this method was also used in the Voynich manuscript (Gladyseva, 2019). The implementation of the text, based on the binary coding of the letters of the alphabet, was very useful for an encryption. The way to encode two slightly different fonts in clear text was used not only in the Voynich manuscript that was written in the Cistercian monastery in northern Spain, but also by the German Benedictine abbot Trithemius.
A German Benedictine abbot Johannes Trithemius (1462 –1516) wrote the 'Steganographia' (1499) where invented the cipher 'Ave Maria' as well as a cipher built on the basis of a periodically shifted key and 'Polygraphia' (1518) with the 'cipher Trithemia'. He published the ‘tabula recta’ or ‘Trithemia table’ where the first letter of the text is encrypted on the first line, the second letter on the second, and so on, after using the last line, they return to the first line again. It was necessary to order the letters on the first line in an arbitrary order, preserving the cyclic change rule on the following lines that are written with letters of an ordered alphabet.
According to some researchers, for example Gordon Rugg, John Dee (1527 - 1608 or 1609) may have owned the Voynich manuscript, as well as 'The Book of Soyga' of the 16th-century codified Latin treatise on magic he was using. In 1564, Dee wrote the Hermetic work 'Monas Hieroglyphica' ('The Hieroglyphic Monad') that had methods of a secret symbolism as well (Rugg, 2004).
In 1582, he met Edward Kelley, who tried to reveal the Philosopher's Stone, interesting because, in addition, the theme of the Voynich manuscript is about the secret of transmuting base metals into gold (Gladyseva, 2019).
In alchemical treatises, the symbol of the philosopher's stone is a rebis, hermaphrodite, which appears as a result of the combination of the 'king' who is philosophical sulphur and the 'queen' who is philosophical mercury in an alchemical marriage. (Gladyseva, 2019) Therefore, the 'queen' in the Voynich Manuscript is a philosophical mercury, but not the Aragonese queen as Gerard Cheshire of the University of Bristol claims in his articles (Cheshire, 2019).
As mentioned in the manuscript of 'The Five Mystery Books' by Dee, on April 11, 1583 he was able to decipher the scroll that Edward Kelley found in Northwick Hill and codify it in Latin: '... abowt un certayne moniment de un boke y un skroll (escrito en caracteres extraños) fownd en Northwik.>' (Rugg, 2004).
Commensurate with 'Five Books of Mystery', he invented the coded alphabet, curious that the letters 'i'; 'and' or 'gon' also exist in the Voynich manuscript (Gladyseva, 2019).
Fig.1
It was believed by Giambattista della Porta (1535? - 1615) that if the topic of the coded text is known, the analyst can make knowing supposes regarding to words that are commonly used in a special context. In reason, each context is characterized by some common words that are using frequently. The same method of deciphering was successfully used in the Voynich Manuscript (Gladyseva, 2019). Porta invented methodology of deciphering the multi-alphanumeric ciphers. The multi-alphanumeric ciphers are difficult to decipher and sometimes they only succeeded in analysing and finding the correct key. For e.g. the word 'Lavender' in the Voynich Manuscript (Gladyseva, 2019).
Текст научной статьи Voynich manuscript - Analysis of the codification algorithm with the encryption methods known in the medieval time and results of the marginalies that were not encrypted
Artículos atravesados por (o cuestionando) la idea del sujeto -y su género- como una construcción psicobiológica de la cultura. Articles driven by (or questioning) the idea of the subject -and their gender- as a cultural psychobiological construction Vol. 5 (2020), enero-diciembre ISSN 2469-0783
In medieval times it was very common to decipher how it was used since ancient times. The most important classical encryption techniques are transposition ciphers which rearrange the order of characters in a message therefore the letters are changed as well as substitution cipher where plaintext are replaced with cipher text. The word 'number' comes from the Hebrew word 'niso?' as well as ’|£1Y code, cipher. Cryptographic examples can be found in some Hebrew biblical texts for e.g. 'Tehillim' (Gladyseva, 2019), furthermore as simple monoalphabetic substitution 'Atbash' cipher (500 BC). The Greek historian Polybius invented "Polybius square" cipher, where the letters of the alphabet were arranged left to right, top to bottom in a 5 x 5 squares, but similar squares were already had been used by Jewish scholars (Polybius, [146 a.C]1922).
Different kind of ciphering was used in occult hermetic texts of ancient Greece with cryptographic system based on homophonic substitution, understanding the meaning (Gladyseva, 2019) metaphors with another connotation of the text. The method currently known as César supposedly used by Julio César and known as César encryption or offset encryption.
However, these methods were used in part in the Voynich manuscript, with the method of encryption of different algorithms that was unknown in the medieval period in other manuscripts. Therefore, for more than half a thousand years no one could decipher it.
-
2. The methods of decoding in the medieval period and their connections with the decryption methods of the investigation of the Voynich manuscript
In the medieval period of Europe encryption was using not only due increased diplomatic activity for convey confidential information, but to conceal information especially in alchemical treatises where symbols were used instead of letters often. The research achievements of the Voynich manuscript indicate that the connotation of its text was influenced by medieval alchemical philosophy (Gladyseva, 2019).
The most important book that describing the use of cryptography in alchemy is the 13th century Roger Bacon's work 'The Message of the Monk Roger Bacon on the secret actions of art and nature and the Nobility of Magic' in Latin 'Epistola Fratris Rog. Baconis, de secretis operibus artis et naturae et null magitate' ( 1270), which describes the use of 7 methods for hiding a text. According to Roger Bacon: '< A man is a crazy who writes a secret in any other way than one which will conceal it from the vulgar.>'
The most interesting result in the encryption code of the Voynich manuscript that made decryption more complicated over the centuries was the use of polyalphabetic encryption that was used partially and simultaneously with monoalphabetic encryption (Gladyseva, 2019).
But according to the history of encryption, polyalphabetic encryption was invented by Leon Batista Alberti in 1467, who identified the idea of using polyalphabetic encryption: multiple encrypted alphabets with change in a few words, which is why he was called the 'father of Western cryptology'. The present study of the text of the Voynich manuscript and the translated information confirmed the current analysis that it was written after 1467 (Gladyseva, 2019).
The polyalphabetic system, which uses several monoalphabetic figures periodically, alternating between each of the three words. Depending on the position of the internal disk, 24 possible variations are defined. One of the disks of the different alphabet was used to represent the decryption method, and the other was from the alphabet with the numbers 1, 2, 3 and 4 (Hernández Gómez, 2010). But it is important to underline that the polyalphabetic system in Voynich manuscript was used partly (Gladyseva, 2019).
In analysing of the encryption methods that were used in the medieval period and their opposition and equivalence with the coding algorithm of the Voynich manuscript was very useful the first treatise of the medieval period, dedicated exclusively to cryptanalysis, the work of Francesco (Cicco) Simonetta (1410-1480), secretary of Sforza (Simonetta, 1474).
He established thirteen rules for decoding of replacement ciphers, which contain word delimiters. On the basis of his manuscript, the most important:
'<… is to find out whether the document is written in Latin or in a local language, and this can be established as follows: find out if the words in this document have only five different endings, less or more <…> if there are only five or less, you are justified in concluding that it is in the vernacular; if they are more than five you can assume your document to be in Latin.> ' (Simonetta, 1474)
The first Voynich manuscript’s preluminal cryptanalysis of my research yielded results that it was not written in Latin, but in some language or its dialect. This method of decryption was possible only after deciphering some words and the names of the first flowers. (Gladyseva, 2019)
Important notes by Francesco (Cicco) Simonetta on words that consist of one, two or three characters that are repeated more frequently in vernacular than in Latin, where the words represented by a single character are four: 'the prepositions 'e' and 'a', the vocative adverb 'o' and the imperative verb 'i', but these one-letter words are rarely used, except the preposition 'a' (Simonetta, 1474).
Simonetta's thirteenth rule was about double letters that were easy to decipher and was well known in medieval times, therefore, in the Voynich manuscript, double letters were generally omitted (Gladyseva, 2019).
Simonetta's sixteenth rule included a known method of coding when the texts were partly in vernacular and partly in Latin, according to my research, this method was infrequently used in the Voynich manuscript, as well as the character method of text that had no meaning especially in the words of the alchemical lexicon (Gladyseva, 2019).
But the most encrypted text according to Simonetta had been encrypted with two completely different cipher alphabets, which in varying degrees this method was also used in the Voynich manuscript (Gladyseva, 2019). The implementation of the text, based on the binary coding of the letters of the alphabet, was very useful for an encryption. The way to encode two slightly different fonts in clear text was used not only in the Voynich manuscript that was written in the Cistercian monastery in northern Spain, but also by the German Benedictine abbot Trithemius.
A German Benedictine abbot Johannes Trithemius (1462 –1516) wrote the 'Steganographia' (1499) where invented the cipher 'Ave Maria' as well as a cipher built on the basis of a periodically shifted key and 'Polygraphia' (1518) with the 'cipher Trithemia'. He published the ‘tabula recta’ or ‘Trithemia table’ where the first letter of the text is encrypted on the first line, the second letter on the second, and so on, after using the last line, they return to the first line again. It was necessary to order the letters on the first line in an arbitrary order, preserving the cyclic change rule on the following lines that are written with letters of an ordered alphabet.
According to some researchers, for example Gordon Rugg, John Dee (1527 - 1608 or 1609) may have owned the Voynich manuscript, as well as 'The Book of Soyga' of the 16th-century codified Latin treatise on magic he was using. In 1564, Dee wrote the Hermetic work 'Monas Hieroglyphica' ('The Hieroglyphic Monad') that had methods of a secret symbolism as well (Rugg, 2004).
In 1582, he met Edward Kelley, who tried to reveal the Philosopher's Stone, interesting because, in addition, the theme of the Voynich manuscript is about the secret of transmuting base metals into gold (Gladyseva, 2019).
In alchemical treatises, the symbol of the philosopher's stone is a rebis, hermaphrodite, which appears as a result of the combination of the 'king' who is philosophical sulphur and the 'queen' who is philosophical mercury in an alchemical marriage. (Gladyseva, 2019) Therefore, the 'queen' in the Voynich Manuscript is a philosophical mercury, but not the Aragonese queen as Gerard Cheshire of the University of Bristol claims in his articles (Cheshire, 2019).
As mentioned in the manuscript of 'The Five Mystery Books' by Dee, on April 11, 1583 he was able to decipher the scroll that Edward Kelley found in Northwick Hill and codify it in Latin: ' <... abowt un certayne moniment de un boke y un skroll (escrito en caracteres extraños) fownd en Northwik. >' (Rugg, 2004).
Commensurate with 'Five Books of Mystery', he invented the coded alphabet, curious that the letters 'i'; 'and' or 'gon' also exist in the Voynich manuscript (Gladyseva, 2019).
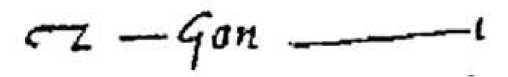
Fig.1
It was believed by Giambattista della Porta (1535? - 1615) that if the topic of the coded text is known, the analyst can make knowing supposes regarding to words that are commonly used in a special context. In reason, each context is characterized by some common words that are using frequently. The same method of deciphering was successfully used in the Voynich Manuscript (Gladyseva, 2019). Porta invented methodology of deciphering the multi-alphanumeric ciphers. The multialphanumeric ciphers are difficult to decipher and sometimes they only succeeded in analysing and finding the correct key. For e.g. the word 'Lavender' in the Voynich Manuscript (Gladyseva, 2019).
3. The protoromanic senselessness of hypothesis with incorrect significance
According to Gerard Edward Cheshire of the University of Bristol the Voynich Manuscript may be written in proto-Romance that arose from Vulgar Latin.
In his articles, especially in the conclusion of 'Linguistically dating and locating the origin of Manuscript MS408, Gerard Edward Cheshire states that: '< The version of the protoromanic language used in the MS408 manuscript ... >' p.36 (Cheshire, 2019).
According to my own research of the Voynich manuscript, it is an absolutely nonsense (Gladyseva, 2019).
This period of proto-Romance was lasting in the very early Medieval period following the collapse of the Roman Empire and subsequently evolved into the many Romance languages.
By the ninth century, Latin was used in legal documents, liturgical formulae and prayers only, and was transformed into a dead language in reason the Romanized people could no longer understand Vulgar Latin texts at all (Herman, 2000).
However, proto-romance as a form of Vulgar Latin, was preceding immediately, uncontrolled diffusion.
In reason, it was impossible to control all changes of all ancient forms separated from proto-romance to Old French, Old Spanish or Old Italian, and this diffusion into separate old forms of Romance languages had been already done much more earlier, long before the Voynich manuscript was written in the late XV century or even in the beginning XVI century (Gladyseva, 2019).
For example, a document from the Melon monastery of Galicia was written in Galician-Portuguese language in 1231.
Misapprehension of erroneous conclusion with the wrong interpretation of the wrong alphabet that Gerard Cheshire is using, except a few accidently right letters, and as a result there is only perpetual ‘misfortune’ to ‘read’ even a few words that ‘were written’ in Proto-Romance according to Gerard Cheshire research.
For e.g. on the page 5 of 'Linguistically dating and locating the origin of Manuscript MS408' (Cheshire, 2018), are the words that Gerard
Cheshire translated as 'man not a mouse', is to prove an incorrect translation with thoughtlessness.
In addition, a such words’ 'translation' with an incorrect alphabet give results as one word is 'translated' (Cheshire, 2019) into one language, the other word into different language, with the change of languages with each word.
The manuscript was written by a very educated friar using intellectual language about the hermetic work of the philosopher's stone in real (Gladyseva, 2019), could not be ignorant as in the absurd texts of Gerard Cheshire's 'translations', which are absolutely incorrect.
In addition, this friar was a famous author in the middle ages in Iberia (Gladyseva, 2019).
According to my research, however, the Voynich manuscript was not written in the proto-romance at all, but in a language that belongs to the Western romance subdivision, but not to Occitan-Romance language branch, but particularly to Iberian-Romance branch, Western group: the medieval Galician language -Galician-Portuguese- (Gladyseva, 2019).
The lexicon of medieval Galician -Galician-Portuguese- is predominantly of Latin extraction, although the Celtic tribes that settled in the northern part of the Iberian Peninsula in the third century B.C. and influenced the Galician language, as a linguistic substrate, as well as the words of Germanic origin (Ferreiro, 2001).
4. The results of uncoded marginalia of the voynich manuscript
This section summarizes some findings of unencrypted words that shed a new light on the text of the Voynich manuscript that was possible only after deciphering its algorithm, definition and analysis of the entire alphabet.
For example, in folia 66r there is marginalia that was not encoded at all. It is a note about the careful use of a plant that previously was described in the text as toxic. According to the Voynich Manuscript text, the two words mean treatments, which were useful in detoxification (Gladyseva, 2019):
| beu | - beuer (bever) is 'beber' in medieval Galician (Lorenzo, 1968)
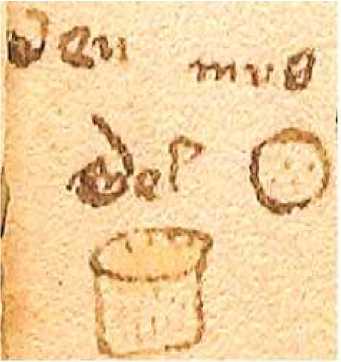
Fig.2 Ms.408. Folia 66r
mus(go) - 'a musk', derrived from lat. MUSOUS (Lorenzo, 1977)
mel - 'honey', derrived from lat.
MEL, MELLIS (Lorenzo, 1977)
“Deciphering of the WHOLE text of the Voynich Manuscript by Alisa Gladyseva” by Alisa Gladyseva ISBN 978-609-475-419-7
Copyright © (Gladyseva, 2019]
Copyright © 2019 Yale University. All Rights reserved.
Mel or 'honey' derrived from the ancient Greek name μέλι was known as a good treatment since ancient times and was described by Pedanio Dioscorides in his book 'De Materia Medica', section 2.82 according to the Salamanca Manuscript.
Musk is also rare archaism in Spanish. The name originates from the Greek μόσχος 'moskhos' or 'Moschi moschiferi'. Musk is a substance from a musk deer's glands with a strong smell. The substance was used in the medieval period as a perfume fixative and was known since the ancient times, but it was also used as a treatment. For example, Peter Schöffer described musk and its properties in his book (Schöffer, 1485), as well as Konrad von Megenberg in 'Liber de natura rerum'. (Megenberg, 13481350) Reportedly, musk components have anti-inflammatory and antihistamine activity (Evans, 1989).
It is worth discussing these facts revealed by the results of the uncoded text of the Voynich manuscript, especially to mention that the words have not been encrypted at all, only the letter 's' in the word 'mus (go)' and the letter 'm' in the word 'mel' were corrupted.
There are a lot of medieval botanical manuscripts, where other authors tried to hide the very names of plants. Especially Medieval manuscripts that were written for Alchemical proposes. 'Il giardino magico degli alchimisti' by Vera Segre Rutz (Segre Rutz, 2000) is about the alchemical herbals’ tradition and in particular about the alchemical herbal manuscript from Biblioteca Universitaria, MS Aldini 211. It is written in Vulgar Latin and describes almost fifty plants that cannot be identified with certainty. Obviously, some names of 13 plants seem to be corruptions of known names e.g. 'Antolla' for 'Anthyllis', 'Ariola' for 'Oriola'. 23 plant names are strongly corrupted for e.g. 'Metries' for 'Myrtus', 'Rigogola' for 'Galega'.
Manuscript Number is 'ljs419' Italy, of XV century is a typical of the medieval Apuleius herbal. But it has corrupted botanical names of plant on 71r folia. As well as the name of plant 'Pepeko' 24r, that is probably is one of the species of peony in real. | P E O N I O |. In reason, on the next folia there is another kind of peony: 24v: 'Peonia'.
4.1 The results of the Voynich manuscript marginalia with the names of the months
The most exceptional are the marginalia that were written by someone who could decipher and read the Voynich Manuscript. The most important thing is to determine the language that was used in the marginalia, but scholars to this day cannot even read the uncoded text.
For example, there have been several attempts to solve the problem of the names of months in the horoscope cycle that, according to results of my research, symbolize represented periods of months in alchemical processes for the transmutation of metals (Gladyseva, 2019).
It is important, that prof. James Westfall Thompson and prof. John Matthews Manly declared that Voynich Manuscript was written in Spanish and had influence of the Raymond Lull works. (Nill, 1936) But in real the Voynich manuscript had a very profound influence on the works of pseudo-Llull, Arnaldo de Vilanova (1240–1311), as well as Johannes de Rupescissa (between 1302 and 1310–1366) (Gladyseva, 2019).
The closest to deciphering the entire Voynich Manuscript was Dr. Erwin Panofsky, he was thinking that the Voynich Manuscript is Spanish, possibly from the south near Spain, and had the Jewish Kabbala influence. In his 1932 comments on the names of the months, he could read:
<'For example, April is written "April". "October is "Octembre" (or "Octember", I forget which), which certainly suggests some form of Spanish, rather than Latin or French ... '> (Panofsky, 1932).
But later in 'Military cryptanalysts: Panofsky's responses of 1954' Panofsky erroneously changed his opinion and claimed that the names of the months were written in ' provincial French ' (Panofsky, 1954).
Historically, there has been great confusion in the correct reading of the names of the months. The problem of reason was in erroneous conclusions. For e.g. in the failed determination of the language, the scholars always using several languages: a few months translation from Spanish, a few months from Catalan, French or Occitan and a few months from Italian as in the work of Gerard Cheshire, from the University of Bristol (Cheshire, 2019).
But reasonably, it is to suggest that someone who wrote the marginalia of the names of the months wrote them in the same language.
According to my research of the Voynich manuscript, the names of the months were written in Galician-Portuguese, which is also known as medieval Galician, particularly in Galician variety (Gladyseva, 2019).
v
70v (part)

fig.3 : Copyright © 2019 Yale University. All Rights Reserved
The marginalia: març(o) (Gladyseva, 2019) in medieval Galician (Galician-Portuguese) (Lorenzo, 1977), derived from the Latin mārtius, March. It is possible that it is written in Catalan or Occitan: Catalan -Març; Occitan - Març.Pisces, the two fish.
v
70v (part)

✓ 71r

fig.5: Copyright © 2019 Yale University. All Rights Reserved.
The marginalia: 'April' (Gladyseva, 2019) in medieval Galician (Galician-Portuguese), derived from lat. APRĪLEM, April. It may be written in Catalan. Aries, the goat.
✓ 71v (Left)

The marginalia: 'may (o)' (Gladyseva, 2019) in medieval Galician (Galician-Portuguese) (Mettmann, 1972), derived from lat. Māius, May. Taurus, the bull.
✓
71v (Medium)
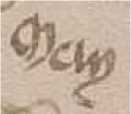
The marginalia: 'may (o)' (Gladyseva, 2019) in medieval Galician (Galician-Portuguese) (Mettmann, 1972), derived from lat. Māius, May. Taurus, the bull.
v
72r (Right).
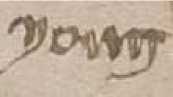
The marginalia: 'juny (o)' (Gladyseva, 2019) in medieval Galician (Galician-Portuguese), derived from lat. IŪNĬUS (Lorenzo, 1968), derivado del lat. IŪNĬUS, June. It is possible that it is written in Catalan 'juny'.Gemini, the twins.
v 72r

fig.9: Copyright © 2019 Yale University. All Rights Reserved
The marginalia: 'jullio' (Gladyseva, 2019) in medieval Galician (Galician-Portuguese) (Barreiro, 1995), derived from lat. JŪLĬUS, July. Cancer, two crabs.
v
72v (part, Left)

But in medieval Galician (Galician-Portuguese) is the name of Cesar Augusto, therefore, the word 'aug (o) st (o)' is also possible. The name of Emperor Octavio Augusto, derived from the month of August lat. AUGŬSTUS (Lorenzo, 1977).
v
72v (part, Right).

The marginalia: 'setembro' or 'setenbre' (Gladyseva, 2019) in medieval Galician (Galician-Portuguese), September. It is possible that it is written in Catalan 'setembre'. Virgo, the virgin. 'Setembro' is according to 'Sobre cronologia do vocabulário galego-português' (Lorenzo, 1968) y 'setenbre' is according to 'La traducción gallega de la Crónica General y de la Crónica de Castilla. Vol. II (Glosario) ' (Lorenzo, 1977). It is possible that it is written in Catalan 'setembre'. Virgo, the virgin.
v
72v (part)

The marginalia: 'Octubro', 'Outubre' or 'Oitubro' (Gladyseva, 2019) in medieval Galician (Galician-Portuguese) (Lorenzo, 1968), derived from lat. Octōber, October. It is possible that it is written in Catalan as 'October'.Libra, the balance.
v 73r

The marginalia: 'novẽbro', 'nove(m)bre' o 'noue(n)bre' (Gladyseva, 2019) in medieval Galician (Galician-Portuguese) (Lorenzo, 1977), derived from lat. NŎVĔMBER, November. It is possible that it is written in Catalan as 'nove(m)bre'.Scorpio, the scorpion.
Galician-Portuguese, which is also known as 'medieval Galician', in reality consisted of the two linguistic varieties that only differed in minor dialect phenomena (Queixas Zas, 2001).
Galicia belonged to the Kingdom of León, so it influenced medieval language. According to R. Lorenzo in the Galician variety it is possible that there was 'novembro' as in the Portuguese variety, but better known is 'novembre' (Lorenzo, 1977).
v 73v

The marginalia: 'dezembro' o 'dezenbre' (Gladyseva, 2019) in medieval Galician (Galician-Portuguese) (Lorenzo, 1968), derived from lat. december, December. Sagittarius.
Obviously the pages of Capricorn and Aquarius are missing in the Voynich Manuscript.
Some of the names of the months exist in Catalan or other Romance languages, but all the names of the months exist only in medieval Galician according to the results of the study.
4.2 The results of marginalia on the folia 17r of the Voynich manuscript
Scholars even cannot read the very important sentence, the marginalia on the folio 17 r of the Voynich Manuscript. The importance is in the language in which it was written, indicating that someone not only deciphered the Voynich manuscript, read it freely, but also used it for alchemical proposals. (Gladyseva, 2019) The marginalia is a tip for using another plant than in the description (Gladyseva, 2019):
'| better foreigner to use plant vrittanicum/brittanicum|'
The language is medieval Galician language or possibly Old Aragonese. The Aragonese expanded to the territories of the Kingdom of Aragon from the twelfth to the sixteenth centuries.These Aragonese words are the same as those of medieval Galician. Eg the word 'mellor' from which a short sentence begins.But additional research results indicate that the Voynich manuscript was written in medieval Galician (Gladyseva, 2019).
| better foreigner to use plant vrittanicum |
| me l l [i]or all(e)a[r] hus[ar] heru[a] vrittanicum |

-
1. mellor (Gladyseva, 2019) - medieval Galician as well as Old
-
2. allea - 'ajeno, ajena' (Gladyseva, 2019), derrived from lat. ALIĒNUS -'foreigner, foreigner', from lat. ALIENS (Lorenzo, 1977).
-
3. husar - 'usar (Gladyseva, 2019), soler, tener costumbre, obrar, ejercitar', de *ŪSĀRE (Lorenzo, 1977), to use.
-
3.1 Or possible another meaning 'huus' - indefinite article: un, una; a, an (Parker, 1958).
-
-
4. herua, erua 'hierba, veneno’ (Gladyseva, 2019), del lat. HĔRBA -hierba (Lorenzo, 1977), herb.
-
5. vrittanica – 'vrittanicum' herb.
Aragonese.
On the folia 17r , on the right corner of the Voynich manuscript, it is very easy to see another flower - ‘brittanica’ that is mentioned in the marginalia.
Herba 'brittanica' was a very frequent plant in medieval botanical manuscripts. For e.g. the manuscript of Pseudo-Apuleius MMW, 10 D 7 fol. 56v. from the National Library of the Netherlands.


fig.16, folia 17 r, MS 408 Copyright ©
fig.17 MMW, 10 D 7 fol. 56v, © Koninklijke Bibliotheek National Library of the Netherlands.
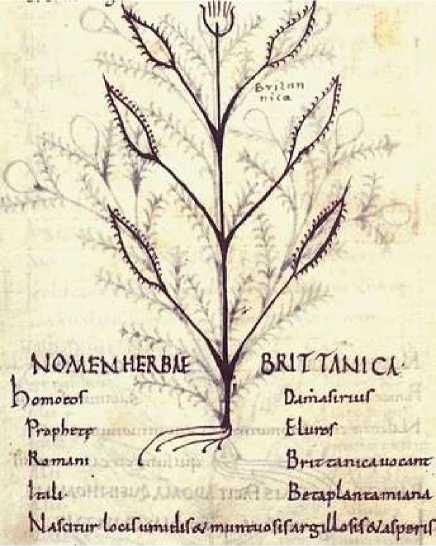
fig.18 Pseudo-Apuleius MMW, 10 D 7 fol. 56v. © Koninklijke Bibliotheek National Library of the Netherlands
5. Conclusion
The linguistic analysis of this article leads to the following conclusions.
The study of the Voynich manuscript marginalia have incredible results. The Voynich Manuscript marginalia on the folio 66r provide a complete description and a translation of the medieval Galician language.
It underlines the results of my dissertation and found clear support for the medieval Galician that was used in the Voynich manuscript.
That proves once again the fairness of my innovative research results such as the analysis of the morphology of the structure of words, the analysis of the syntax of sentence structures, the semantics of words, the lexicology of words. For many centuries, scholars who attempted to decipher the Voynich manuscript thought that an 'o' symbol is a zero or a coded symbol, but in reality it is a singular masculine definite article of medieval Galician that is identified in the Voynich manuscript with other articles, which were not encrypted at all. Singular Feminine: a. Plural Masculine: os. Plural Feminine: as. Such definite articles exist in Old Aragonese as well. Especially, the vernacular names of plants, which exist even in Galician in the present as well.
The language of the other marginalia, particularly on the folio 17 r of the Voynich Manuscript, is medieval Galician, but possibly also Aragonese, due to the word 'mellor', which is the same in both languages. But the other words are written in medieval Galego according to the results of the study.
In addition to the translation of the names of the months’ marginalia, the language in which it was written in a medieval Galician is also determined. This information is important to understand who could read the Voynich manuscript in medieval times.
The linguistic analysis yields the definitive results of the decipherment and the translation of the entire text of the Voynich Manuscript from the medieval Galician.
Список литературы Voynich manuscript - Analysis of the codification algorithm with the encryption methods known in the medieval time and results of the marginalies that were not encrypted
- Bacon, Roger.(1270). 'Epistola Fratris Rog. Baconis, de secretis operibus artis et naturae et null magitate' (‘The Message of the Monk Roger Bacon on the secret actions of art and nature and the Nobility of Magic’).
- Barreiro, M. C. (1995). A documentación notarial do concello de Noia (ss. XIV-XVI). [Glosario, 155-456]. Universidade de Santiago de Compostela.
- Cheshire, G. Ed. (2017). 'Linguistic missing links: instruction in decrypting, translating and transliterating the only document known to use both proto-Romance language and proto-Italic symbols for its writing system. Science Survey 1, (1-47.October 11, 2017).
- Cheshire, G. Ed. (2018). 'Linguistically dating and locating the origin of Manuscript MS408' University of Bristol. Science Survey 2. (January 12th, 2018, 1-36).
- Cheshire, G. Ed. (2019). Plant Series, No. 2. Manuscript MS408. Science Survey, October 2019. doi: https://doi.org/10.1080/02639904.2019.1599566
- Cheshire, G. Ed. (2019). The Language and Writing System of MS408“ (Voynich) Explained . Journal Romance Studies Volume 37, (2019, Apr 29 - Issue 1, 30-67).
- Evans, W. (1989). 'Trease and Evans 'Pharmacognosy'. 13th ed. Oxford, England: The Alden Press.
- Ferreiro, M. (2001). Gramática Histórica Galega, 2 vols. [2nd ed.]. Santiago de Compostela: Laiovento.
- Gladyseva, A. (2019). Criptografía de Tehillim. Vilnius: Gladyseva.
- Gladyseva, A. (2019). Deciphering of the WHOLE text of the Voynich Manuscript by Alisa Gladyseva". Vilnius: isbn 978-609-475-419-7.
- Gladyseva, A. (2019). Un sistema criptográfico basado en la sustitución homofónica en el poema hermético De rerum natura de Titus Lucretius Carus (99 a. C. - 55 a. C.). Vilnius: Gladyseva.
- Herman, J. (2000). Vulgar Latin. (R. Translated by Wright, Trans.) University Park: Pennsylvania State University Press.
- Hernández Gómez, S. (2010). Análisis de textos cifrados de los siglos xvi y xvii. https://e-archivo.uc3m.es/bitstream/handle/10016/11110/PFC_Sara_Gomez_Hernandez.pdf
- Lorenzo, R. (1968). Sobre cronologia do vocabulário galego-português. Vigo: Galaxia.
- Lorenzo, R. (1977). La traducción gallega de la Crónica General y de la Crónica de Castilla. Vol. II (Glosario). Ourense: Instituto de Estudios Orensanos Padre Feijóo.
- Megenberg, v. K. (1348-1350). Liber de natura rerum.
- Mettmann, W. M. (1972). Cantigas de Santa María de Afonso X, o Sábio. Vol. IV (Glossário). Coimbra: Universidade.
- Nill, A. (1936). With a note, listing the letter’s contents: “C) me my work on cipher ms.”.
- Panofsky, E. (1932). 'Panofsky’s comments of 1932'.
- Panofsky, E. (1954). Panofsky's responses of 1954. Military cryptanalysts.
- Parker, K. M. (1958). Vocabulario de la Crónica Troyana. . Salamanca : Universidad.
- Polybius. [146 a.C](1922). The Histories X.45.6. http://penelope.uchicago.edu/Thayer/E/Roman/Texts/Polybius/10*.html#45.6
- Queixas Zas, M. (2001). Historia xeral da literatura galega. Vigo: A nosa terra. p. 14. ISBN 978-84-95350-79-4.
- Rugg, G. (2004). The mystery of the Voynich Manuscript. Scientific American.
- Rutz, V. S. (2000). Il giardino magico degli alchimisti: un erbario illustrato trecentesco della Biblioteca universitaria di Pavia e la sua tradizione. Il polifilo.
- Schöffer, P. (1485). Gart der Gesundheit. (Hortus sanitatis). Mainz.
- Simonetta, C. (1474). Cipher-Breaking Rules Augusto Buonafalce Rules for Decrypting Enciphered Documents Without a Key. Pavia.
- Souto Cabo, J. A. ( 2008). Documentos galego-portugueses dos séculos XII e XIII. A Coruña: Universidade da Coruña.


