A Teaching Model Application in the Course of Information Security
Автор: Chunyan Qiu, Wei Zhao, Jianhua Jiang, Jialing Han
Журнал: International Journal of Education and Management Engineering(IJEME) @ijeme
Статья в выпуске: 1 vol.3, 2013 года.
Бесплатный доступ
With the rapid development of economy, information Security is becoming more and more important for any modern organization in recent years. Therefore, How to teach information security is a challenge to universities. This paper aims to apply schema theory to information security curriculum. The teaching result shows that there is a significant difference in final exam and practice exam between the proposed model and a regular teaching model.
Information security, schema theory, computer teaching
Короткий адрес: https://sciup.org/15013799
IDR: 15013799
Текст научной статьи A Teaching Model Application in the Course of Information Security
-
A. Purpose and requirements of information security teaching
Information security [4] in general covers a wide range of technology. The purpose of information security teaching in university of finance and economics is to make students master of information security technology and method in practical application. Characteristics of information security curriculum are listed as follows.
-
1) Information security is a multidisciplinary technology. It involves computer, communication, mathematics, cryptography etc. Therefore, students must understand these related disciplines.
-
2) Practice of information security is the key to teaching of information security.
-
3) It is necessary for students to master some computer software to analyze the various potential safety problems of computer system and select appropriate techniques to tackle and solve these problems.
-
4) It is important for student to set up the ability of independent study new technology.
These characteristics of information security curriculum above are very important in the information security teaching and schema theory application.
-
B. Introduction of Schema Theory
A schema is a structural unit. In schema theory this units is an internal data structure in the memory that organizes an individual‘s similar experiences. It is used to recognize similar and discriminate dissimilar new experiences [5].
Schemata can be seen as the organized background knowledge. To get a comprehensive understanding of schema, characteristics of schema [6] as follow.
-
1) Schemata change moment by moment as information is received.
-
2) Schemas may embed and overlap. Each schema is embedded in other schemata and itself contains subschema.
-
3) Schemata are always organized meaningfully, can be added to, and, as an individual gains experience, develop to include more variables and more specificity.
-
4) They may also be reorganized when incoming data reveals a need to restructure the concept.
-
3. Teaching model application based on schema theory
In this paper, application of schema theory has four essential stages: schemata collection stage, teaching process stage, practice process stage and schemata reorganization. The relationship of these four stages can be seen in fig.1.
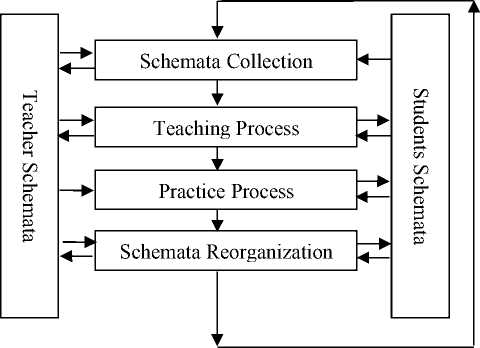
Figure 1. Mode of Information Security Teaching based on Schema Theory
These four phases are introduced in detail as follows.
-
A. Schemata Collection
Background knowledge will be of primary importance for students, and schema-based pre-learning activities should be used for activating and constructing such background knowledge. The main task in this stage is to collect students’ schemata related information security. To complete the task we have taken some methods listed as bellow.
Firstly, we can make a quiz on background knowledge in order to collect students’ schemata. The teacher analysis the test result for guiding the information teaching. This test only be used the first stage. Secondly, the teacher can test student learning effect by asking some questions about the last class teaching content, this test will be made for the second stage. Thirdly, the teacher analyzes students’ experiment report for the last class.
After finishing the above content, the teacher can collect much information about students’ schema to complete the future information security teaching.
-
B. Teaching Process
General knowledge and generic concepts are important to teach. A large proportion of student difficulties are insufficient general knowledge, especially in cross-disciplinary curriculum. So In this stage, teachers mainly teach basic knowledge and use the result of schema collection stage to guide teaching process. As we know prior knowledge is essential for the comprehension of new information, teacher either needs to help students build the prerequisite knowledge, or remind them of what they already know before introducing new material. Students feel internal conflict if they are trying to assimilate schemata which contradict their previous suppositions, teachers need to understand and help students build schemata and make connections between the old and the new.
-
C. Practice Process
Practice plays an important role in information security curriculum. Practice can improve students' skills and innovating ability and enhance student's understanding to theory knowledge. Teacher gives experimental aims, requirements and contents. Students apply what they have learnt to experiment and update their old schemata.
-
D. Schemata reorganization
-
4. Result Analysis
The main task in this stage is to reorganize their schemata. Therefore teachers can organize the student to carry on the discussion after students complete their experiment. We started with a discussion of the problem: why are computers not secure? And what they have learned by this experiment? This led naturally to a discussion of policy and mechanism, and general design principles and so on. This discussion inspires students to discover, query, think and propose solutions based on problems presented and theories learnt. In this way, schemata related with new information are activated.
After accomplishing the discussion above, students have to well complete experiment reports which can active student’s knowledge system. Experiment content includes four aspects: (1) Experiment purpose and requirements, (2) Experiment process, (3) Experiment results, (4) Experiences.
After completing the above process, students will reorganize their own schemata by themselves. Then, the next circle, which is from the first stage to the last, is started. These four stages are depicted as Fig.1.
From Fig.1, we know that students construct their schemata in teaching process stage, practice process stage, and schemata reorganization stages step by step, while the teacher collects students’ schemata in schemata collection stage, teaching process stage and schemata reorganization stages. The teacher can help students to construct their new schemata in teaching and practice stages. These four stages are a circle followed one by another. Students’ schemata construct and renew their own schemata in this circle, while the teacher gets students’ schemata information and try his best to renew students’ schemata.
In order to analyze the teaching effect of information security curriculum based on schema theory, this paper makes an experiment on students in information management and system major in Jilin University of finance and economics. Information security curriculum was arranged in the sixth semester.
Students are classified randomly into two classes. Each class has 34 students, none of whom have studied the information security technique before. These two classes are marked with class y1 and class y2. The teaching of class y1 is a traditional teaching model, while class y2 with schema theory applied. These two classes are taught by the same teacher, and all the students are randomly combination into two classes, if the teaching effect is significant different in final exam or experiment exam it must be because of different teaching models.
We apply schema theory in information security teaching in one term and analysis teaching effects which is shown in figures (Fig.2, Fig.3, Table I , Table II and TableШ). To better evaluate students’ learning results based on schema theory, on one hand we evaluate the exam scores of class y2, on the other hand evaluate the experiment scores of class y2.
-
A. Statistic analysis of Experiment scores
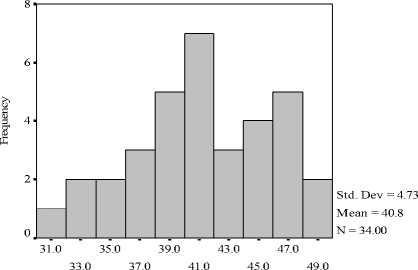
Experiment Scores
Figure 2. Histogram of Experiment Scores
The experiment full marks are 50 points. Most of student’s experiment scores between 30 and 48 in Fig.2. The mean of experiments’ scores is 40.8, and the standard deviation is 4.73. It shown that the application of schema theory in information security teaching works well in experiments and stimulate students' interest.
-
B. Statistic analysis of final examination Scores
After a semester, we made a final exam. The results are shown in Fig. 3. From Fig.3, the mean of final examination scores is 81.0, and the standard deviation is 7.80. The students’ examination scores spread from 60 to 96. Data results show that most of students have mastered the basic knowledge of information security. These 34 students’ scores are confirmed to normal distribution. All in all, the application of schema theory in information security teaching
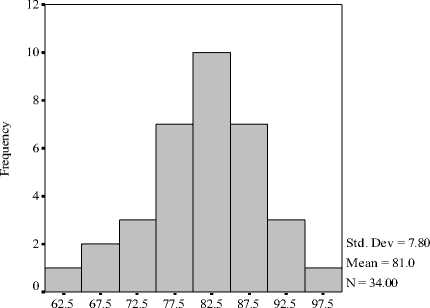
Exam Scores
Figure 3. Histogram of Final Examination Scores
-
C. Relationships between experiment Scores and exam Scores
In order to illustrate the relationships between experiments and final examination, Pearson correlation is given in Table I .
table i. Pearson Correlation of Exam scores and experiment scores
Correlations
|
Exam Score |
Experiment Score |
||
|
Exam Score |
Pearson Correlation |
1 |
.976** |
|
Sig. (2tailed) |
. |
.000 |
|
|
N |
34 |
34 |
|
|
Experiment |
Pearson |
.976** |
1 |
|
Score |
Correlation |
||
|
Sig. (2tailed) |
.000 |
. |
|
|
N |
34 |
34 |
|
**.Correlation is significant at the 0.01 level (2-tailed).
We adapt Pearson correlation analysis and get the correlation coefficient of 0.976 which represents an extremely strong relationship between them. That is to say, the students who get a higher score in experiment get a higher score in final exam, and vice versa. In a word, there is not a completely linear correlation between them.
The following sections discuss the most typical form of t-test that compares the means of two independent random samples class y1 and class y2. They are independent in the sense that they are drawn from different populations and each element of one sample is not paired (linked to) with its corresponding element of the other sample.
The typical null hypothesis of the independent sample t-test is that the mean difference of the two groups is zero [7]. The exam score and experiment score are considered as responsible variables to validate whether there is a significant difference between these two classes. We choose the scores of final exam to test the teaching effect. An independent t-Test assuming equal variances is applied, and the analyzed result is given in the table II.
As in all statistical tests, the basic criterion for statistical significance is a "2-tailed significance" less than 0.05. Where the level of significance (α) is 0.05.
The 0.00075 probability in table II is clearly less than 0.05 so the difference is statistically significant (t = 3.53479, df= 66, p<0.05). The mean of final exam by class y2 was significantly more than that by class y1.
table ii. T-TEST: TWO SAMPLES ASSUMING EQUAL VARIANCE FOR Exam Score
|
class y1 |
class y2 |
|
|
Mean |
73.85294 |
80.97059 |
|
Variance |
78.73529 |
59.12032 |
|
Observations |
34 |
34 |
|
df |
66 |
|
|
t Stat |
-3.53479 |
|
|
P(T<=t) two-tail |
0.00075 |
|
|
t Critical two-tail |
1.99656 |
To evaluate the practice teaching effect, a practice exam is performed. The scores of these two classes are analyzed in table Ш .
table iii. T-TEST: TWO SAMPLES ASSUMING EQUAL VARIANCE FOR Experiment Score
|
y1 |
y2 |
|
|
Mean |
38.14706 |
40.82353 |
|
Variance |
30.91711 |
17.84670 |
|
Observations |
34 |
34 |
|
df |
66 |
|
|
t Stat |
-2.23487 |
|
|
P(T<=t) two-tail |
0.02882 |
|
|
t Critical two-tail |
1.99656 |
From Table Ш , the 0.02882 probability is clearly less than 0.05 so the difference is statistically significant (t = 2.23487, df = 66, p<0.05). The mean of practice exam by class y2 was significantly more than that by class y1.
From table II and table Ш, they all show that using the schema theory teaching methods is significantly different with a traditional teaching model. Schema theory applied into information security teaching has achieved good teaching effect.
-
5. Conclusion and Future Work
This paper mainly discusses the application of schema theory in information security teaching. Using the schema theory, we can improve student's learning interest and get a better teaching effect. However, the above about schema theory can't explain that how students process and understand the meaning of information and how construct their own schemata. In fact, it is very difficult for the teacher to get correct schemata from students in schemata collection stage. So how to avoid getting wrong schemata is a challenge task. We find that students’ experiments and examination capacities are asymmetric in the final teaching effect, so we must make students more realize theory and practice are equally important for the future teaching.
Список литературы A Teaching Model Application in the Course of Information Security
- F. C. Bartlett, “Remembering,” Cambridge: Cambridge University Press. 1932.
- D. E. Rumelhart and A. Ortony, “The representation of knowledge and memory,” In R.C. Anderson, R. J. Spiro, and W. E. Montague(Eds.), Schooling and the acquisition of knowledge. Hillsdale, NJ: Erlbaum. 1977.
- M. W. Eysenck, M. T. Keane. “Cognitive Psychology: A Student‟sHandbook,” London: Longman Group Limited. 1985.
- M. E. Whitman and H. J. Mattord, “Designing and teaching information security curriculum,'‟ in Proceedings of the 1st annual Conference on Information Security Curriculum Development Kennesaw, Georgia: ACM, 2004.
- S. P. Marshall. “Schemas in problem solving,” Cambridge: Cambridge University press. 1995.
- Walker, A. Glenn. “Common Statistical Methods for Clinical Research with SAS Examples.” Cary,NC: SAS Institute. 2002
- Bluman, G. “Allan Elementary Statistics: A Step by Step Approach, A Brief Version“. 4th ed. New York: McGraw Hill. 2008.


