Analysis of methods for assessing threats in the field of data storage
Автор: Kureichik V.M., Pirozhkov S.S., Sakharova O.N., Kamyshev K.V., Kamenskaya E.N., Deberdeev M.P.
Журнал: Cardiometry @cardiometry
Рубрика: Report
Статья в выпуске: 27, 2023 года.
Бесплатный доступ
At present, in the conditions of the active development of the information society, when information is the main means of production, special attention is paid to the methods and means of organizing its protection and storage. A large number of developments, both software and physical, are devoted to this issue. Cybersecurity is becoming more and more necessary every day and, as a result, popular, as a result of which a large number of specialists with a basic education in the field of information security graduate every year. In addition, an extensive regulatory framework has been developed that regulates the procedure and principles for protecting and storing data. Thus, we can talk about the existence of an entire industry aimed at maintaining and improving information security. Besides, it is proved herein that there is a need to develop a method for quantitative assessment of the security of stored data.
Cybersecurity, threats, data, storage
Короткий адрес: https://sciup.org/148326343
IDR: 148326343 | DOI: 10.18137/cardiometry.2023.27/161163
Текст научной статьи Analysis of methods for assessing threats in the field of data storage
Imprint
Viktor M. Kureichik, Sergey S. Pirozhkov*, Olga N. Sakharova, Konstantin V. Kamyshev, Elena N. Kamenskaya. Analysis of methods for assessing threats in the field of data storage. Car-diometry; Issue No. 27; May 2023; p. 161-163; DOI: 10.18137/car-diometry.2023.27/161163; Available from:
Today, no branch of activity can exist in isolation from information technology. Any organization, even if its activities are not directly related to IT technologies, seeks to organize long-term storage and protec- tion of information related to the results of professional activities. If at small enterprises for organizing the protection and storage of information they are guided by existing technical means, then for enterprises of the defense industry complex of the Russian Federation, machine-building, aircraft building and other industries, only technical means are not enough, and there is a whole range of legal documentation that regulates the procedure for organizing data protection and storage (given examples).
To analyze the threat assessment in the field of data storage, a study was conducted on the basis of statistical data obtained by questioning more than 40 information security subjects, among which were small businesses that do not work with state secrets or information labeled “Secret”, medical institutions that strictly comply with Federal Law No. 152 “On the Protection of Personal Data”, as well as defense industry enterprises. The distribution of enterprises participating in the study is shown in Figure 1.
The following questions were used as the main questions of the questionnaire:
-
1. Industry of your organization.
-
2. Do you use information technology in your work?
-
3. Do you have to store data.
-
4. Are you engaged in protection of the stored data?
-
5. Assess the level of protection of stored data.
-
6. Assess the top storage threats in your organization.
-
7. Give examples of top storage threats in your organization that are not listed but are important to you.
The survey was conducted among experts who have the necessary qualifications in information technology. In addition, the survey was anonymous for enterprises, which made it possible to make the results of the study more accurate.
The analysis of the conducted research allowed to obtain the following results.
To the question “Do you use information technology in your work?”, all respondents answered “yes”, which is quite logical, since in the conditions of modern realities, human life is almost impossible without the use of information technology.
To the question “Do you have to store data?”, all survey participants also answered “yes”, which is completely obvious, since any work with information almost always implies its storage.
The share of participation of organizations in the study
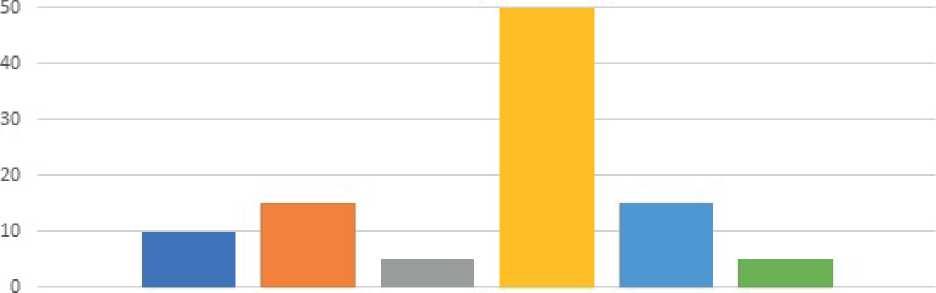
■ Education ■ Medical institutions
■ Large industries ■ Small industries
■ ГГ ■ Defense industry
Figure 1. The share of participation of organizations in the study
However, not everyone gave a positive answer to the question “Do you protect stored data?”: 5% of respondents do not think about the need to protect stored data.
To the question “Assess the level of protection of stored data” 95% of survey participants (who organize the protection of stored data) answered “Good” -68.5% or “Satisfactory” - 28.35%. 3.15% of the respondents answered “Sufficient”. All answers to this question are purely qualitative, since it is currently not possible to quantify the level of protection. A qualitative assessment does not give a complete picture of the level of data protection, but only allows one to subjectively assume that survey participants are satisfied with the means of protection used. Nevertheless, it is possible to objectively assess how protected a system is from threats only using a quantitative assessment.
To assess possible threats in the field of data storage, a classification list of threats associated with the lack of physical space on storage media, the possible lack of access to stored information and the possible destruction or distortion of information was proposed. An analysis of respondents’ answers showed that different threats are critical for different organizations. So for IT companies, the threats associated with the possible lack of space for storing information and access to it are critical, while the threat of destruction or distortion of information is not significant, in view 162 | Cardiometry | Issue 27. May 2023
of the well-developed data protection policy. For educational institutions, the threats of lack of space on media are not critical, while the threats of lack of access and deletion or distortion of information can lead to a disruption of the educational process. For medical institutions, the threats associated with the possible lack of space for storing information and the possible deletion or distortion of data turned out to be critical, and possible problems of access to information are not significant. Among small and large enterprises, as well as defense industry enterprises, ensuring protection against all types of threats is significant.
In the last question, survey participants were asked to give an example of threats that were not included in the proposed classification list, but protection against them would be important. All respondents put a dash in the corresponding column, which will allow us to conclude that the proposed classification of threats in the field of data storage is sufficient for further research.
After analyzing the data among respondents who answered yes to the question about “Protection of stored data”, additional testing was carried out in order to quantify the likelihood of threats to their organizations. As a result, 5% of the respondents gave a quantitative answer based on the assessment of threats on a scale from 0 to 10 points, which in turn is a qualitative rather than quantitative analysis. And 95% of the respondents could not give at least some quantitative assessment due to the lack of an appropriate methodology.
Thus, the conducted research on the basis of statistical data allowed us to obtain the following results. In almost all areas of activity, people actively use information technology, store various data. The majority is engaged in the organization of protection of the stored data. However, none of the survey participants could quantify the level of protection of stored data. Obviously, it is a quantitative assessment, in contrast to a qualitative one, that makes it possible to obtain objective data on the level of protection of any information system from possible threats. Therefore, there is a need to develop a method for quantitative assessment of the security of stored data.
Список литературы Analysis of methods for assessing threats in the field of data storage
- Abrarov RD. Information security in computer networks. Young Researcher. 2016; 9.5 (113.5):10-2. [in Russian].
- Alekseeva MS. Threats to the security of local computer networks. Young Researcher. 2014; 18 (77): 212-3. [in Russian].
- Varlataya SK, Shakhanova MV. Protection of information processes in computer networks. Training and Methodology. Moscow: Prospect, 2015. 216p. [in Russian].
- Information and psychological security: basic concepts / G.M. Zarakovskiy, G.L. Smolyan. Psychology and security of organizations/ Ed. by A. V. Brushlinsky and V. E. Lepsky. Moscow, 1997. [in Russian].
- Kureichik VM, Pirozhkov SS. Review: Big data storage issues. Proceedings of the International Scientific and Technical Congress "Intelligent Systems and Information Technologies 2020". 2020; 1: 420-6. [in Russian].
- Kureichik VM, Pirozhkov SS, Sakharova ON. Threats in the field of data storage. Engineering Journal of Don. 2021. No.7. [in Russian].
- Olifer VG, Olifer NA. Computer networks. Principles, technologies, protocols. St. Petersburg: Piter, 2020. 1008 p. [in Russian].
- A Taxonomy of DDoSW Attacks and DDoS Defense Mechanism - UCLA CSD Thechnical Report no. 020018. URL: lasr.cs.u cla.edu/ddos/ucla_tech_report_020018.pdf.
- Zhdanova IV, Bykov DV. Options for building a system for protecting electronic documents from copying. Engineering Journal of Don, 2012, No.2. [in Russian].
- Panov RI. Modern methods of information protection on the example of a Russian device. Modern Problems of Science and Education. 2015, No.2. [in Russian].


