Modeling of threats in the sphere of medical data storage
Автор: Sergey S. Pirozhkov, Olga N. Sakharova, Konstantin K. Kamyshev, Viktor M. Kureichik, Ilya M. Borodyansky
Журнал: Cardiometry @cardiometry
Рубрика: Short report
Статья в выпуске: 20, 2021 года.
Бесплатный доступ
In medical institutions of various levels, a large amount of data is stored in electronic form, to ensure the safety of which are presented with special requirements. Ensuring the safety of the storage of medical data should begin with an analysis of existing threats. This article provides a model of threats in the area of data storage, which includes the following components: comunicative, spatial and destructive threat. It is shown that, to date, communicative and spatial threats have minor rates, which can be neglected. The destructive threat is considered in more detail, its components are described. Recommendations for the development of medical data storage systems are given.
Data storage, Recommender system, Medical records, Database
Короткий адрес: https://sciup.org/148322450
IDR: 148322450 | DOI: 10.18137/cardiometry.2021.20.190193
Текст научной статьи Modeling of threats in the sphere of medical data storage
Imprint
Sergey S. Pirozhkov, Olga N. Sakharova, Konstantin K. Kamyshev*, Viktor M. Kureichik, Ilya M. Borodyansky. Modeling of threats in the sphere of medical data storage. Cardiometry; Issue 20; November 2021; p. 190-193; DOI: 10.18137/cardiome-try.2021.20.190193; Available from: issues/no20-november-2021/modeling-threats
Nowadays, in medical institutions a large amount of data is stored in electronic form. Most often, medical data on the patient includes: age, gender, anthropometric data, information on past and chronic diseases, the current diagnosis, the plan for further therapy, etc., which are obtained from professional medical workers. Thus, there are special requirements for storing medical data.
Ensuring the safety of the storage of medical data should begin with an analysis of existing threats. In accordance with [3], three types of storage threats are distinguished: communicative, spatial and destruc- 190 | Cardiometry | Issue 20. November 2021
tive, which can be presented in the form of the following mathematical model:
U= c*UP+ b*UK+ a*UD, where U is the total probability of a threat in the storage area,
UP is the probability of a spatial threat,
UK the probability of communicative threats, UD the probability of a destructive threat, a, b, c - specific weight ratios of types of threats.
The proposed mathematical model of threat in the storage area is applicable for information systems of various levels that may include both one PC in a private medical office and a computer local network of a large medical institution.
The total probability of a threat in the storage area will be in the interval of boundary values from 0 to 1. However, the boundary values can only be achieved in the limit, these values are not achievable in real life. The zero threat can only be in the absence of an information system to which a mathematical model of threats is applied. A value of the total probability of threats in the sphere of data storage equal to 1 means that the information system at the time of the assessment is no longer workable.
Specific weight coefficients are determined based on the analysis of statistical data obtained as a result of collecting information on the number of incidents according to the types of threats during a predetermined significant period of time. For medical institutions significant period of time can be set from the moment the organization of data storage in electronic form. Obviously, the sum of the specific weight coefficient values should be equal to 1 or 100%:
a+b+c=1 (or 100%).
This approach to the boundary conditions of the mathematical model of the occurrence of threats in the storage area will allow the total probability to remain in the specified limits.
The spatial threat is a threat of the repository overflow due to the constantly growing volume of the data being stored. The probability of occurrence of the spatial threat is determined by the availability of free space on the disks of medical institutions and the volume of stored data.
Communicative threat represents the lack of access to stored data. The probability of the communicative threat is determined based on the statistical analysis of the reliability of lines and communications devices.
To date, there is no uniform centralized medical data storage system, which would have had information about the state of health of the country’s population and to which access from any medical institution would be organized. Since all medical data is stored locally in separate medical institutions, the communicative and spatial threats are very insignificant in view of the fact that they are localized within each individual institution. In addition to minor rates of probabilities of the spatial and communicative threats occurrence, the values of the specific weight coefficients are also insignificant. As a result, the total probability of a threat in the storage area of medical data is reduced to determine the likelihood of a destructive threat, since the communicative and spatial threat can be neglected.
Destructive threat arises due to external influence on the data, resulting in a partial or complete loss of information.
In accordance with [3] destructive threat includes the following types of threats: software, virus, encryption, hacker’s, physical and user’s, they all can be presented in a graphical model.
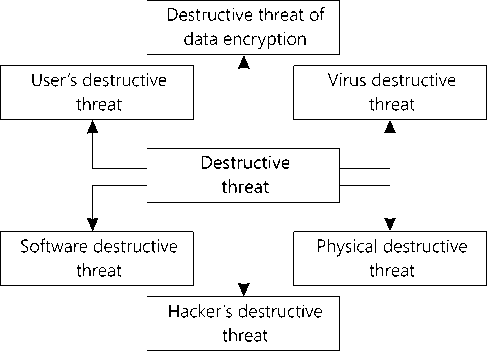
Figure 1. Destructive threat types
The probability of a destructive threat may also be presented in the form of a mathematical model:
Uд = as*UDs+ av*UDv+ ac*UDc + ahc*UDhc + + ahw*UDhw+ au*UDu, where UDs is a software destructive threat, UDv is a virus destructive threat, UDc is a destructive threat of data encryption, UDhc is a hacker’s destructive threat, UDhw is a physical destructive threat, UDu is a user’s destructive threat, as , av , ac , ahc , ahw , au – specific weight coefficients of a destructive threat component.
In turn, the probability of the occurrence of a destructive threat also lies in the range from 0 to 1, but cannot reach the boundary conditions in real life. This is explained by the fact that the 0 meaning implies the complete absence of stored data, and the value equal to 1 indicates that at the time of the assessment, the data is destroyed due to the occurrence of destructive threat.
Specific weight coefficients of the destructive threats components are determined based on a statistical analysis of incidents for the selected significant period of time. It is also evident that to meet the boundary conditions for the destructive threat probability the sum of values of components specific weight coefficients must be equal to 1, or 100%:
as+ av+ ac+ ahc+ ahw+ au= 1 (or 100%)
The software destructive threat arises due to a malfunction of a medical information system or a program that leads to damage or complete data deletion, as a result of which it becomes impossible to work with information.
Failures in the work of a medical information system or a program may occur as a result of a disconnection of electricity, failure of any physical component of the computer system as a whole, errors or deficiency of software developers. As a result, occurs any failure in the data processing, which leads to distortion or loss of data.
Virus destructive threat arises as a result of penetration into a computer system of a virus or malicious program, which can both cause damage or delete files from a hard disk and change data in it.
The destructive threat of data encryption is a kind of a virus destructive threat, since it has the same ways to penetrate the computer system of a medical institution. However, in relation to health facilities the destructive data encryption is highlighted as a particular type of threat, as data not deleted or corrupted there, but encrypted for subsequent commercial sale of decryption algorithms, which actually is a financial cyber crime.
For virus destructive threat and destructive data encryption threat, we can enumerate the following paths of infecting:
-
a) connecting an external information storage device (when the virus penetrates the system when connected to a computer external storage devices);
-
b) connecting to the Internet (when the virus enters the device through the downloaded infected file, visiting the infected site, opening a letter with a virus in email).
Hacker’s destructive threat is a deliberate penetration into a computer system with the aim of illegal information downloading, as well as damage, distortion or complete data deletion. In accordance with the Federal Law No. 152 «On Protection of Personal Data», a separate task is to ensure the protection of personal data stored in the databases of medical institutions. Therefore, great attention should be paid to protection from hacker attacks.
The physical destructive threat is a threat to the failure of the internal storage device and any component of the computer whose disruption can lead to the failure of the internal storage device, as a result of which the partial or complete loss of medical data occurs.
User’s destructive threat arises due to an error of a user or operator, as a result of which the data is deleted or distorted due to inattention, incorrectly accepted solutions or targeted action of the attacker.
To eliminate the user’s threat is possible only at 100% process automation. However, it is impossible to perform it 100%, since at the initial stage, even for an existing automated system, the initial data is still set by the user and completely eliminate the user’s actions is impossible. In case if at the stage of data input occurs uncorrected unnoticed or just minor error, then during subsequent processing of the data may be a critical situation which can lead to errors in the work of medical personnel (e.g., wrong prescription medications and others). Thus, it can be concluded that the qualification of the user, which works with medical data should be high enough.
Conventionally, the user’s destructive threat can be divided into the following types:
-
1. Data input error occurs as a result of casual typo when entering data. Due to any circumstances, the operator does not notice the error and continues entering. In this case, a purely human factor is triggered, which cannot be completely eliminated.
-
2. The interpretation error occurs as a result of an incorrect understanding by the operator of the information he receives for input. Quite often, the operator has an insufficient conceptual apparatus or a terminological dictionary, as a result of which the information entered is distorted by the operator unconsciously.
-
3. The deliberate input of incorrect data arises as a result of the targeted desire of the operator to distort the reliable information introduced into the system. It is possible to exclude this threat by checking the reliability of the employee at the employment stage of the organization’s internal security or personnel service. In addition, it is impossible to exclude the deliberate input of distorted or incorrect data in order to cause harm to patients or for obtaining own economic benefits.
-
4. Intentional theft or removal of data typically occurs as a result of self-serving purposes. This threat is eliminated by backing up information on protected storage devices.
-
5. Unintentional data deletion occurs as a result of the erroneous actions of the operator. Incorrect user’s actions, leading to accidental removal of any amount of information, are a consequence of the human factor.
These incidents can be avoided due to the training and systematic certification procedures for operator in order to form the unified concept of identifying medical information.
Today, the destructive threat is the greatest danger to storing medical data, since it is difficult to predict enough. The occurrence of spatial threats with a regular systemic analysis of methods for storing medical data can be foreseen. Communicative threats do not lead to loss of medical data, but only temporarily restrict access to them. At the same time, to predict the user’s behavior, the system failure, unauthorized penetration and failure of the equipment is almost impossible. Anti-virus software also does not give a hundred% guarantee of data security. However, properly organized backup of medical data allows you to minimize the consequences of the arising destructive threats.
Thus, there exists a need to create a unified centralized information system for the storage of medical data, in which the organization of protection against destructive threats will have a complex systematic nature. To collect all medical information on the patient in one place, it is proposed to create personal electronic health cards (PEHC) The PEHC data can be integrated into medical recommender systems (MRSs). Based on the analysis of information on the patient, MRS will send data to the user interface, the data most suitable for a particular patient, which will solve the problem of the cold start, one of the most common reasons for reducing the relevance of recommendations and, accordingly, the quality of the recommender systems.
It should also be taken nto account that when organizing a single centralized storage of medical data, integrated with one or more medical recommender systems, it is necessary to provide access to the repository to all employees of medical institutions according to their profile of activities, which in turn sharply increases the rates of communicative and spatial threats.
Conflict of interest
None declared.
Author contributions
The authors read the ICMJE criteria for authorship and approved the final manuscript.
Список литературы Modeling of threats in the sphere of medical data storage
- Kurechik VM, Pirogkov SS. Overview: Problems of Storage of Large Data. Proceedings of the International Scientific and Technical Congress “Intellectual Systems and Information Technologies 2020”.2020;1:420-6. [in Russian]
- Konstantin V. Kamyshev, Viktor M. Kureichik, Ilya M. Borodyanskiy. Review of the recommender systems application in cardiology. Cardiometry; Issue 16; May 2020; p.97-105; DOI: 10.12710/cardiometry.2020.16.97105
- Kureichik VM, Sakharova ON, Pirozhkov SS. Threats in the storage of data // Engineering Journal of Don. 2021;7. URL: http://www.ivdon.ru/uploads/article/pdf/IVD_60__6_kureichik_sakharova_pirozhkov.pdf_d70c5b810a.pdf [in Russian]
- A Taxonomy of DDoSW Attacks and DDoS Defense Mechanism – UCLA CSD Thechnical Report no. 020018. URL: lasr.cs.u cla.edu/ddos/ucla_tech_report_020018.pdf
- Zhdanova IV, Bykov DV. Options for building an electronic document protection system from copying. Engineering Journal of Don. 2012. No. 2 URL: ivdon.ru/ru/magazine/archive/n2y2012/825 [in Russian]
- Panov RI. Modern methods of information protection on the example of a Russian device. Modern problems of science and education, 2015, № 2-2.;URL: http://science-education.ru/ru/article/view?id=23134 [in Russian]
- Zhdanova IV, Bykov DV. Options for building an electronic document protection system from copying. Engineering Journal of Don. 2012. No. 2. URL: ivdon.ru/ru/magazine/archive/n2y2012/825 [in Russian]
- Panov RI. Modern methods of information protection on the example of a Russian device. Modern problems of science and education. 2015;2-2. URL: http://science-education.ru/ru/article/view?id=23134 [in Russian]
- Enikeeva LA, Stelmashonok EV, Stelmashonok VL. Modeling of information protection system of business processes infrastructure on an industrial plant. International business management. 2016;3:315-9.
- Mingaleva Z, Mirskikh I. Small innovative enterprise: the problems of protection of commercial confidential information and know-how. Middle east journal of scientific research, 2013;13:97-101.
- Onyigwang OJ, Shestak Y, Oksiuk A. Information protection of data processing center against cyber attacks. Proceedings of the 2016 IEEE 1st international conference on data stream mining and processing, DSMP 2016. 2016. p.397-400


